npj Quantum Information ( IF 6.6 ) Pub Date : 2019-07-26 , DOI: 10.1038/s41534-019-0180-9 Margarida Pereira , Marcos Curty , Kiyoshi Tamaki
|
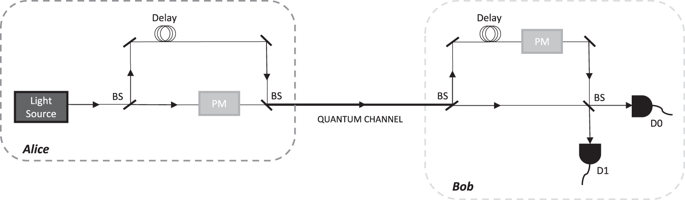
In theory, quantum key distribution (QKD) allows secure communications between two parties based on physical laws. However, most of the security proofs of QKD today make unrealistic assumptions and neglect many relevant device imperfections. As a result, they cannot guarantee the security of the practical implementations. Recently, the loss-tolerant protocol (K. Tamaki et al., Phys. Rev. A, 90, 052314, 2014) was proposed to make QKD robust against state preparation flaws. This protocol relies on the emission of qubit systems, which, unfortunately, is difficult to achieve in practice. In this work, we remove such qubit assumption and generalise the loss-tolerant protocol to accommodate multiple optical modes in the emitted signals. These multiple optical modes could arise, e.g., from Trojan horse attacks and/or device imperfections. Our security proof determines some dominant device parameter regimes needed for achieving secure communication and, therefore, it can serve as a guideline to characterise QKD transmitters. Furthermore, we compare our approach with that of H.-K. Lo et al. (Quantum Inf. Comput., 7, 431–458, 2007) and identify which method provides the highest secret key generation rate as a function of the device imperfections. Our work constitutes an important step towards the best practical and secure implementation for QKD.
中文翻译:

具有缺陷和泄漏源的量子密钥分发
从理论上讲,量子密钥分发(QKD)允许基于物理定律的两方之间进行安全通信。但是,当今QKD的大多数安全证明都做出了不切实际的假设,并忽略了许多相关的设备缺陷。结果,它们不能保证实际实施的安全性。最近,提出了一种容错协议(K. Tamaki等,Phys。Rev. A,90,052314,2014),以使QKD对状态准备缺陷具有鲁棒性。该协议依赖于量子比特系统的发射,不幸的是,这在实践中很难实现。在这项工作中,我们删除了这种量子位假设,并概括了容错协议,以在发射信号中适应多种光学模式。这些多种光学模式可能来自例如特洛伊木马攻击和/或设备缺陷。我们的安全证明确定了实现安全通信所需的一些主要设备参数方案,因此,它可以用作表征QKD发射机的指南。此外,我们将我们的方法与H.-K方法进行了比较。Lo等。(Quantum Inf。Comput。,第7卷,第431-458页,2007年),并确定哪种方法提供的最高密钥生成率取决于设备的缺陷。我们的工作是迈向QKD最佳实践和安全实施的重要一步。(2007年),并确定哪种方法可提供最高的秘密密钥生成率,具体取决于设备缺陷。我们的工作是迈向QKD最佳实践和安全实施的重要一步。(2007年),并确定哪种方法可提供最高的秘密密钥生成率,具体取决于设备缺陷。我们的工作是迈向QKD最佳实践和安全实施的重要一步。











































 京公网安备 11010802027423号
京公网安备 11010802027423号