Physical Communication ( IF 2.2 ) Pub Date : 2022-09-26 , DOI: 10.1016/j.phycom.2022.101902 Ramesh Chand Meena , Surbhi Bhatia , Rutvij H. Jhaveri , Long Cheng , Ankit Kumar , Arwa Mashat
|
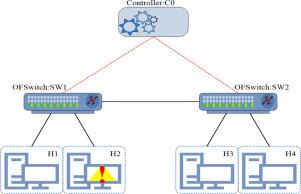
SDN (Software-Defined Networking) is a new technology that separates data and control planes; the main components of SDN are OFSwitches and Controller. The traffic flow is monitored by the SDN controller. Initially, OFSwitches lack security rules for packet handling. OFSwitch sends the packet to the controller for examination, creating control messages that favor the packet and establishing necessary flow entry. Host packets are sent to their destination, seeing only the destination host address and not the source host address. The attacker takes advantage of this situation and generates packets with forged source addresses in order to conceal his identity and perform various source address spoofed attacks such as Denial of Service (DoS), man in the middle (MiM), Distributed DoS (DDoS), and so on. This paper proposes a design for discovering hosts proactively, preparing HostTable, configuring flow entry during handshaking, and detecting and preventing source-forged attacks in Hybrid SDN. We called it HyPASS: Design of Hybrid-SDN Prevention of Source Spoofing Attacks with Host Discovery and Address Validation. We used Python for Mininet implementation and tested it on RYU and POX controllers. During the experiment, it identifies and drops 99.99% of packets with the forged source address.
中文翻译:

HyPASS:设计混合SDN,防止带有主机发现和地址验证的源欺骗攻击
SDN(Software-Defined Networking)是一种将数据平面和控制平面分离的新技术;SDN的主要组件是OFSwitches和Controller。流量由 SDN 控制器监控。最初,OFSwitch 缺乏数据包处理的安全规则。OFSwitch 将数据包发送到控制器进行检查,创建有利于数据包的控制消息并建立必要的流条目。主机数据包被发送到它们的目的地,只看到目标主机地址而不是源主机地址。攻击者利用这种情况,生成带有伪造源地址的数据包,以隐藏自己的身份,并执行各种源地址欺骗攻击,例如拒绝服务 (DoS)、中间人 (MiM)、分布式 DoS (DDoS)、等等。本文提出了一种在混合SDN中主动发现主机、准备HostTable、配置握手过程中的流表项以及检测和防止源伪造攻击的设计。我们将其称为 HyPASS:使用主机发现和地址验证来防止源欺骗攻击的混合 SDN 设计。我们使用 Python 实现 Mininet,并在 RYU 和 POX 控制器上对其进行了测试。在实验过程中,它识别并丢弃了 99.99% 的带有伪造源地址的数据包。



























 京公网安备 11010802027423号
京公网安备 11010802027423号