当前位置:
X-MOL 学术
›
Int. Trans. Electr. Energy Syst.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
Privacy boundary determination of smart meter data using an artificial intelligence adversary
International Transactions on Electrical Energy Systems ( IF 1.9 ) Pub Date : 2021-07-14 , DOI: 10.1002/2050-7038.13020 Xiao‐Yu Zhang 1, 2 , Chris Watkins 2 , Clive Cheong Took 1 , Stefanie Kuenzel 1
International Transactions on Electrical Energy Systems ( IF 1.9 ) Pub Date : 2021-07-14 , DOI: 10.1002/2050-7038.13020 Xiao‐Yu Zhang 1, 2 , Chris Watkins 2 , Clive Cheong Took 1 , Stefanie Kuenzel 1
Affiliation
|
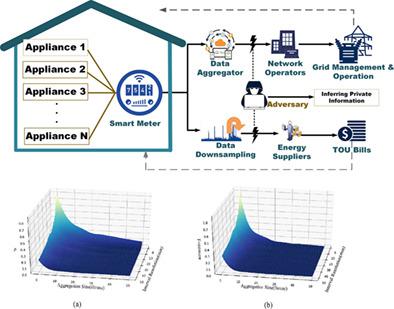
The roll-out of the new-generation smart meter with artificial intelligence (AI)-based data mining algorithms causes serious privacy issues for consumers. By detecting appliance usages, an adversary can easily monitor the behavior patterns of residents. In this paper, a privacy-preserving smart metering model is proposed; the system utilizes a data aggregator to aggregate the readings of neighboring smart meters and a data down-sampler to reduce the sensitive information in the load profiles. An AI-based adversary is introduced to simulate the adversarial process. Four state-of-the-art deep learning/machine learning algorithms (convolutional neural network–long short-term memory (CNN-LSTM), gated recurrent unit (GRU), k-nearest neighbors (KNN), and CNN are employed as data mining algorithms. By tuning the variables (aggregation size α and interval resolution σ), the detectability boundaries of particular appliances are evaluated. Based on the appliance detectability, a three-level privacy boundary (real-time surveillance, presence/absence detection, and complete protection) is obtained. The result shows that to achieve complete data protection, the aggregation size should exceed 40, and the interval resolution should exceed 8 hours.
中文翻译:

使用人工智能对手确定智能电表数据的隐私边界
采用基于人工智能 (AI) 的数据挖掘算法的新一代智能电表的推出给消费者带来了严重的隐私问题。通过检测设备使用情况,攻击者可以轻松监控居民的行为模式。本文提出了一种保护隐私的智能计量模型;该系统使用数据聚合器来聚合相邻智能电表的读数,并使用数据下采样器来减少负载配置文件中的敏感信息。引入了基于 AI 的对手来模拟对抗过程。四种最先进的深度学习/机器学习算法(卷积神经网络-长短期记忆(CNN-LSTM)、门控循环单元(GRU)、k-最近邻(KNN)和CNN被用作数据挖掘算法。通过调整变量(聚合大小α和间隔分辨率σ ),评估特定器具的可检测性边界。基于设备可检测性,获得三级隐私边界(实时监控、存在/不存在检测和完全保护)。结果表明,要实现完整的数据保护,聚合大小应超过40,间隔解析应超过8小时。
更新日期:2021-09-16
中文翻译:

使用人工智能对手确定智能电表数据的隐私边界
采用基于人工智能 (AI) 的数据挖掘算法的新一代智能电表的推出给消费者带来了严重的隐私问题。通过检测设备使用情况,攻击者可以轻松监控居民的行为模式。本文提出了一种保护隐私的智能计量模型;该系统使用数据聚合器来聚合相邻智能电表的读数,并使用数据下采样器来减少负载配置文件中的敏感信息。引入了基于 AI 的对手来模拟对抗过程。四种最先进的深度学习/机器学习算法(卷积神经网络-长短期记忆(CNN-LSTM)、门控循环单元(GRU)、k-最近邻(KNN)和CNN被用作数据挖掘算法。通过调整变量(聚合大小α和间隔分辨率σ ),评估特定器具的可检测性边界。基于设备可检测性,获得三级隐私边界(实时监控、存在/不存在检测和完全保护)。结果表明,要实现完整的数据保护,聚合大小应超过40,间隔解析应超过8小时。









































 京公网安备 11010802027423号
京公网安备 11010802027423号