当前位置:
X-MOL 学术
›
Trans. Emerg. Telecommun. Technol.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
Anomaly‐based intrusion detection systems: The requirements, methods, measurements, and datasets
Transactions on Emerging Telecommunications Technologies ( IF 3.6 ) Pub Date : 2021-03-08 , DOI: 10.1002/ett.4240 Suzan Hajj 1 , Rayane El Sibai 2 , Jacques Bou Abdo 3 , Jacques Demerjian 4 , Abdallah Makhoul 1 , Christophe Guyeux 1
Transactions on Emerging Telecommunications Technologies ( IF 3.6 ) Pub Date : 2021-03-08 , DOI: 10.1002/ett.4240 Suzan Hajj 1 , Rayane El Sibai 2 , Jacques Bou Abdo 3 , Jacques Demerjian 4 , Abdallah Makhoul 1 , Christophe Guyeux 1
Affiliation
|
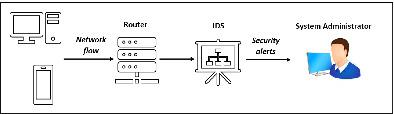
With the Internet's unprecedented growth and nations' reliance on computer networks, new cyber‐attacks are created every day as means for achieving financial gain, imposing political agendas, and developing cyberwarfare arsenals. Network security is thus acquiring increasing attention among researchers, practitioners, network architects, policy makers, and others. To defend organizations' networks from existing, foreseen, and future threats, intrusion detection systems (IDSs) are becoming a must. Existing surveys on anomaly‐based IDS (AIDS) focus on specific components such as detection mechanisms and lack many others. In contrast to existing surveys, this article covers the full scope needed by researchers and practitioners alike when studying AIDS. The scope ranges from the intrusion detection techniques to attacks forms and passing through the relevant attack features, most‐used datasets, challenges, and potential solutions. This article provides an exhaustive review of IDSs and discusses their requirements and performance metrics in deep. It presents a taxonomy of IDSs based on four criteria: information source, detection strategy, detection mode, and architecture. Then, in‐depth analysis and a comparison of network intrusion detection approaches based on anomaly detection techniques are given. The article also introduces a classification of computer network attacks, along with their different forms and the relevant network traffic features to detect them, as well as a summary of the popular datasets used by the researchers to evaluate the IDSs. Finally, the article highlights several research challenges and the possible solutions to deal with them.
中文翻译:

基于异常的入侵检测系统:需求,方法,度量和数据集
随着Internet的空前增长和各国对计算机网络的依赖,每天都会出现新的网络攻击,以此作为获取经济利益,强加政治议程和发展网络战武器库的手段。因此,网络安全越来越引起研究人员,从业人员,网络架构师,政策制定者等的关注。为了保护组织的网络免受现有,可预见的和未来的威胁,入侵检测系统(IDS)成为必须。现有的有关基于异常的IDS(AIDS)的调查都集中在特定的组件(例如检测机制)上,而缺少许多其他组件。与现有调查相反,本文涵盖了研究人员和从业人员在研究艾滋病时所需的全部范围。范围从入侵检测技术到攻击形式,以及贯穿相关的攻击功能,最常用的数据集,挑战和潜在解决方案。本文对IDS进行了详尽的回顾,并深入讨论了它们的要求和性能指标。它基于四个标准提出了IDS的分类标准:信息源,检测策略,检测模式和体系结构。然后,对基于异常检测技术的网络入侵检测方法进行了深入的分析和比较。本文还介绍了计算机网络攻击的分类,它们的不同形式以及检测它们的相关网络流量功能,以及研究人员用来评估IDS的流行数据集的摘要。最后,
更新日期:2021-04-05
中文翻译:

基于异常的入侵检测系统:需求,方法,度量和数据集
随着Internet的空前增长和各国对计算机网络的依赖,每天都会出现新的网络攻击,以此作为获取经济利益,强加政治议程和发展网络战武器库的手段。因此,网络安全越来越引起研究人员,从业人员,网络架构师,政策制定者等的关注。为了保护组织的网络免受现有,可预见的和未来的威胁,入侵检测系统(IDS)成为必须。现有的有关基于异常的IDS(AIDS)的调查都集中在特定的组件(例如检测机制)上,而缺少许多其他组件。与现有调查相反,本文涵盖了研究人员和从业人员在研究艾滋病时所需的全部范围。范围从入侵检测技术到攻击形式,以及贯穿相关的攻击功能,最常用的数据集,挑战和潜在解决方案。本文对IDS进行了详尽的回顾,并深入讨论了它们的要求和性能指标。它基于四个标准提出了IDS的分类标准:信息源,检测策略,检测模式和体系结构。然后,对基于异常检测技术的网络入侵检测方法进行了深入的分析和比较。本文还介绍了计算机网络攻击的分类,它们的不同形式以及检测它们的相关网络流量功能,以及研究人员用来评估IDS的流行数据集的摘要。最后,



























 京公网安备 11010802027423号
京公网安备 11010802027423号