Applied Soft Computing ( IF 7.2 ) Pub Date : 2021-02-15 , DOI: 10.1016/j.asoc.2021.107175 Sajjad Dadkhah , Farzaneh Shoeleh , Mohammad Mehdi Yadollahi , Xichen Zhang , Ali A. Ghorbani
|
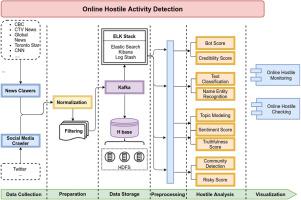
Over recent years, the development of online social media has dramatically changed the way people connect and share information. It is undeniable that social platform has promoted the quickest type of spread for fake stories. Almost all the current online fact-checking sources and researches are concentrating on the validating political content and context. The proposed system in this paper provides a complete visual data analytics methods to assist users in achieving a comprehensive understanding of malicious activities at multiple levels such as adversary’s behavior, victim’s behavior, content, and context level. In this paper, we investigate a variety of datasets from different aspects such as role, vulnerabilities, influential level, and distribution pattern. The proposed method in this paper focuses on automatic fake/hostile activity detection by utilizing a variety of machine learning (ML) techniques, deep learning models, natural language processes (NLP), and social network analysis (SNA) techniques. Different auxiliary models, such as bot detection, user credibility, and text readability, are deployed to generate additional influential features. The classification performance of ten different machine learning algorithms using a variety of well-known datasets is evaluated by utilizing 10-fold cross-validation.
中文翻译:

实时敌对活动分析与检测系统
近年来,在线社交媒体的发展极大地改变了人们联系和共享信息的方式。不可否认的是,社交平台已经促进了假新闻传播的最快类型。当前,几乎所有在线事实检查来源和研究都集中在验证政治内容和背景上。本文中提出的系统提供了完整的可视数据分析方法,以帮助用户全面了解恶意行为的多个层次,例如对手的行为,受害者的行为,内容和上下文级别。在本文中,我们从角色,漏洞,影响程度和分布模式等不同方面研究了各种数据集。本文提出的方法致力于通过利用各种机器学习(ML)技术,深度学习模型,自然语言过程(NLP)和社交网络分析(SNA)技术来自动进行假冒/敌对活动检测。部署了各种不同的辅助模型,例如漫游器检测,用户可信度和文本可读性,以生成其他有影响力的功能。通过利用10倍交叉验证,评估了使用各种众所周知的数据集的十种不同机器学习算法的分类性能。部署以生成其他有影响力的功能。通过利用10倍交叉验证,评估了使用各种众所周知的数据集的十种不同机器学习算法的分类性能。部署以生成其他有影响力的功能。通过利用10倍交叉验证,评估了使用各种众所周知的数据集的十种不同机器学习算法的分类性能。











































 京公网安备 11010802027423号
京公网安备 11010802027423号