当前位置:
X-MOL 学术
›
Trans. Emerg. Telecommun. Technol.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
Edge-based blockchain enabled anomaly detection for insider attack prevention in Internet of Things
Transactions on Emerging Telecommunications Technologies ( IF 3.6 ) Pub Date : 2020-11-17 , DOI: 10.1002/ett.4158 Yusuf Muhammad Tukur 1, 2 , Dhavalkumar Thakker 1 , Irfan‐Ullah Awan 1
Transactions on Emerging Telecommunications Technologies ( IF 3.6 ) Pub Date : 2020-11-17 , DOI: 10.1002/ett.4158 Yusuf Muhammad Tukur 1, 2 , Dhavalkumar Thakker 1 , Irfan‐Ullah Awan 1
Affiliation
|
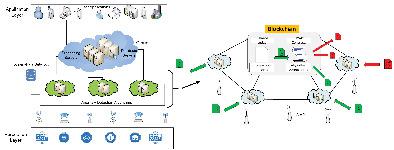
Internet of Things (IoT) platforms are responsible for overall data processing in the IoT System. This ranges from analytics and big data processing to gathering all sensor data over time to analyze and produce long-term trends. However, this comes with prohibitively high demand for resources such as memory, computing power and bandwidth, which the highly resource constrained IoT devices lack to send data to the platforms to achieve efficient operations. This results in poor availability and risk of data loss due to single point of failure should the cloud platforms suffer attacks. The integrity of the data can also be compromised by an insider, such as a malicious system administrator, without leaving traces of their actions. To address these issues, we propose in this work an edge-based blockchain enabled anomaly detection technique to prevent insider attacks in IoT. The technique first employs the power of edge computing to reduce the latency and bandwidth requirements by taking processing closer to the IoT nodes, hence improving availability, and avoiding single point of failure. It then leverages some aspect of sequence-based anomaly detection, while integrating distributed edge with blockchain that offers smart contracts to perform detection and correction of abnormalities in incoming sensor data. Evaluation of our technique using real IoT system datasets showed that the technique remarkably achieved the intended purpose, while ensuring integrity and availability of the data which is critical to IoT success.
中文翻译:

基于边缘的区块链启用异常检测以防止物联网中的内部攻击
物联网 (IoT) 平台负责物联网系统中的整体数据处理。这范围从分析和大数据处理到随时间收集所有传感器数据以分析和产生长期趋势。然而,这伴随着对内存、计算能力和带宽等资源的过高需求,资源高度受限的物联网设备缺乏将数据发送到平台以实现高效运营的能力。如果云平台遭受攻击,这会导致可用性差和由于单点故障而导致数据丢失的风险。数据的完整性也可能被内部人员(例如恶意系统管理员)破坏,而不会留下他们的行为痕迹。为了解决这些问题,我们在这项工作中提出了一种基于边缘的区块链启用异常检测技术,以防止物联网中的内部攻击。该技术首先利用边缘计算的能力,通过使处理更靠近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。该技术首先利用边缘计算的能力,通过使处理更靠近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。该技术首先利用边缘计算的能力,通过使处理更接近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。
更新日期:2020-11-17
中文翻译:

基于边缘的区块链启用异常检测以防止物联网中的内部攻击
物联网 (IoT) 平台负责物联网系统中的整体数据处理。这范围从分析和大数据处理到随时间收集所有传感器数据以分析和产生长期趋势。然而,这伴随着对内存、计算能力和带宽等资源的过高需求,资源高度受限的物联网设备缺乏将数据发送到平台以实现高效运营的能力。如果云平台遭受攻击,这会导致可用性差和由于单点故障而导致数据丢失的风险。数据的完整性也可能被内部人员(例如恶意系统管理员)破坏,而不会留下他们的行为痕迹。为了解决这些问题,我们在这项工作中提出了一种基于边缘的区块链启用异常检测技术,以防止物联网中的内部攻击。该技术首先利用边缘计算的能力,通过使处理更靠近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。该技术首先利用边缘计算的能力,通过使处理更靠近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。该技术首先利用边缘计算的能力,通过使处理更接近物联网节点来减少延迟和带宽要求,从而提高可用性并避免单点故障。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。然后利用基于序列的异常检测的某些方面,同时将分布式边缘与提供智能合约的区块链集成,以检测和纠正传入传感器数据中的异常。使用真实物联网系统数据集对我们的技术进行评估表明,该技术显着实现了预期目的,同时确保了对物联网成功至关重要的数据的完整性和可用性。



























 京公网安备 11010802027423号
京公网安备 11010802027423号