当前位置:
X-MOL 学术
›
Comput. Electr. Eng.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
Optimized neural network model for attack detection in LTE network
Computers & Electrical Engineering ( IF 4.0 ) Pub Date : 2020-12-01 , DOI: 10.1016/j.compeleceng.2020.106879 K. Krishna Jyothi , Shilpa Chaudhari
Computers & Electrical Engineering ( IF 4.0 ) Pub Date : 2020-12-01 , DOI: 10.1016/j.compeleceng.2020.106879 K. Krishna Jyothi , Shilpa Chaudhari
|
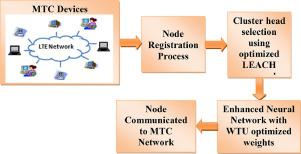
Abstract Machine-type communication (MTC) senses our environment througfh connecting millions of devices to one another, and becomes an enabler for context-aware and ubiquitous computing services. Still, there has been no research managing the network lifetime for these MTC devices due to a lack of authentication requirements and attack detection. Thus, this research work intends to develop an efficient attack detection model for MTC. Since the previous work on MTC based Long Term Evaluation(LTE) model had only authenticated the MTC devices via clustering, security is a critical issue that is focused on the current research work. Here, the attack detection is undergone by introducing an enhanced Neural Network (NN) model, where the authenticated nodes, as well as cluster Head (CH) from elliptic curve cryptography (ECC), are detected for attacks. In case of the presence of attack, the enhanced NN introduces a penalty as one and prohibits those nodes from taking part in MTC communication. As a novelty, here the training of enhanced NN is accomplished via a new optimization algorithm referred to Whale with Tri-level Update (WTU). Moreover, the security requirement is fulfilled by fixing the objectives like confidentiality and repudiation on data transmission. The efficiency of the proposed attack detection model is proved and a comparative evaluation will be accomplished in terms of certain security analysis.
中文翻译:

LTE网络攻击检测的优化神经网络模型
摘要 机器类型通信 (MTC) 通过将数百万台设备相互连接来感知我们的环境,并成为上下文感知和无处不在的计算服务的推动者。尽管如此,由于缺乏身份验证要求和攻击检测,还没有研究管理这些 MTC 设备的网络生命周期。因此,这项研究工作旨在为 MTC 开发一种有效的攻击检测模型。由于之前基于 MTC 的长期评估 (LTE) 模型的工作仅通过集群对 MTC 设备进行身份验证,因此安全性是当前研究工作关注的关键问题。在这里,通过引入增强型神经网络 (NN) 模型来进行攻击检测,其中检测到经过身份验证的节点以及椭圆曲线加密 (ECC) 中的簇头 (CH) 是否存在攻击。在存在攻击的情况下,增强型 NN 引入惩罚为 1 并禁止这些节点参与 MTC 通信。作为一个新颖之处,这里增强 NN 的训练是通过一种新的优化算法来完成的,该算法称为 Whale with Tri-level Update (WTU)。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。
更新日期:2020-12-01
中文翻译:

LTE网络攻击检测的优化神经网络模型
摘要 机器类型通信 (MTC) 通过将数百万台设备相互连接来感知我们的环境,并成为上下文感知和无处不在的计算服务的推动者。尽管如此,由于缺乏身份验证要求和攻击检测,还没有研究管理这些 MTC 设备的网络生命周期。因此,这项研究工作旨在为 MTC 开发一种有效的攻击检测模型。由于之前基于 MTC 的长期评估 (LTE) 模型的工作仅通过集群对 MTC 设备进行身份验证,因此安全性是当前研究工作关注的关键问题。在这里,通过引入增强型神经网络 (NN) 模型来进行攻击检测,其中检测到经过身份验证的节点以及椭圆曲线加密 (ECC) 中的簇头 (CH) 是否存在攻击。在存在攻击的情况下,增强型 NN 引入惩罚为 1 并禁止这些节点参与 MTC 通信。作为一个新颖之处,这里增强 NN 的训练是通过一种新的优化算法来完成的,该算法称为 Whale with Tri-level Update (WTU)。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。此外,通过确定数据传输的机密性和否认等目标来满足安全要求。证明了所提出的攻击检测模型的有效性,并在一定的安全分析方面进行了比较评估。











































 京公网安备 11010802027423号
京公网安备 11010802027423号