当前位置:
X-MOL 学术
›
Int. J. Commun. Syst.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
Optimal DBN‐based distributed attack detection model for Internet of Things
International Journal of Communication Systems ( IF 1.7 ) Pub Date : 2020-09-01 , DOI: 10.1002/dac.4595 Meenigi Ramesh Babu 1 , Kalludi Narasimhaiah Veena 1
International Journal of Communication Systems ( IF 1.7 ) Pub Date : 2020-09-01 , DOI: 10.1002/dac.4595 Meenigi Ramesh Babu 1 , Kalludi Narasimhaiah Veena 1
Affiliation
|
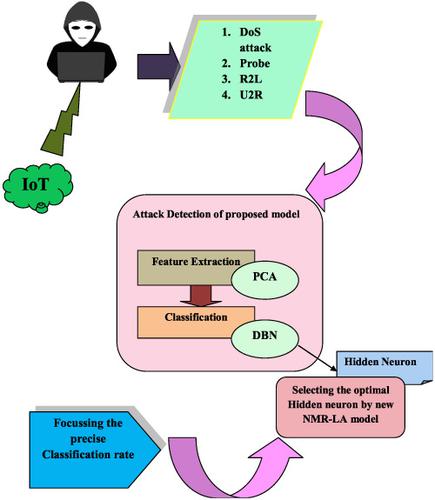
This paper introduces a new detection mechanism for defending the cyberspace with a new logic that aiding the concept of deep learning. The process involves two phases, namely, feature extraction and classification. The initial phase is the feature extraction, in which the features are extracted from the given input data by the renowned principal component analysis (PCA). Subsequently, the extracted features are subjected to the classification phase, where the deep belief network (DBN) model is used. The DBN model classifies the presence of attacks like denial of service (DoS), probe, R2L, and U2R. In order to make the performance more excellent, this paper diverts the strategy to a new concept termed “Optimization Concept.” Here, the hidden neuron of DBN is optimally selected by a new algorithm termed novel mutation rate‐based lion algorithm (NMR‐LA), which is the modified model of lion algorithm (LA). The performance of proposed algorithm NMR‐LA is compared over the conventional models in terms of both positive and negative measures like accuracy, sensitivity, specificity, precision, negative predictive value (NPV), F1 score and Mathews correlation coefficient (MCC), false‐positive rate (FPR), false‐negative rate (FNR), and false‐discovery rate (FDR) and proves the betterments of proposed work.
中文翻译:

最佳的基于DBN的物联网分布式攻击检测模型
本文介绍了一种新的检测机制,该机制以一种有助于深度学习概念的新逻辑来捍卫网络空间。该过程涉及两个阶段,即特征提取和分类。初始阶段是特征提取,其中通过著名的主成分分析(PCA)从给定的输入数据中提取特征。随后,对提取的特征进行分类阶段,在此阶段使用深度置信网络(DBN)模型。DBN模型将攻击的存在分类,例如拒绝服务(DoS),探测,R2L和U2R。为了使性能更好,本文将策略转移到一个称为“优化概念”的新概念。这里,DBN的隐藏神经元是通过一种称为新型基于突变率的狮子算法(NMR-LA)的新算法进行最佳选择的,该算法是狮子算法(LA)的改进模型。相对于常规模型,在准确性和敏感性,特异性,精密度,阴性预测值(NPV),F1得分和Mathews相关系数(MCC),错误-阳性率(FPR),假阴性率(FNR)和错误发现率(FDR),证明了拟议工作的改进。
更新日期:2020-10-16
中文翻译:

最佳的基于DBN的物联网分布式攻击检测模型
本文介绍了一种新的检测机制,该机制以一种有助于深度学习概念的新逻辑来捍卫网络空间。该过程涉及两个阶段,即特征提取和分类。初始阶段是特征提取,其中通过著名的主成分分析(PCA)从给定的输入数据中提取特征。随后,对提取的特征进行分类阶段,在此阶段使用深度置信网络(DBN)模型。DBN模型将攻击的存在分类,例如拒绝服务(DoS),探测,R2L和U2R。为了使性能更好,本文将策略转移到一个称为“优化概念”的新概念。这里,DBN的隐藏神经元是通过一种称为新型基于突变率的狮子算法(NMR-LA)的新算法进行最佳选择的,该算法是狮子算法(LA)的改进模型。相对于常规模型,在准确性和敏感性,特异性,精密度,阴性预测值(NPV),F1得分和Mathews相关系数(MCC),错误-阳性率(FPR),假阴性率(FNR)和错误发现率(FDR),证明了拟议工作的改进。











































 京公网安备 11010802027423号
京公网安备 11010802027423号