Pervasive and Mobile Computing ( IF 3.0 ) Pub Date : 2020-06-18 , DOI: 10.1016/j.pmcj.2020.101211 Kyounggon Kim , Kiyoon Cho , Jihwan Lim , Young Ho Jung , Min Seok Sung , Seong Beom Kim , Huy Kang Kim
|
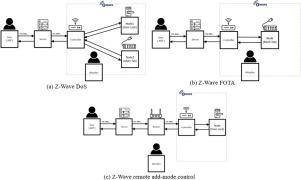
With the evolution of state-of-the-art applications and paradigms, the world is progressing toward smart cities. Smart homes are an important aspect of smart cities, wherein various mobile computing and network technologies are used. However, they are also susceptible to security threats that can cause serious issues related to privacy and safety. Z-Wave is a wireless technology primarily used in smart homes; however, its protocol has not been sufficiently investigated. In this study, we examined threat modeling for the Z-Wave protocol to determine the security issues and suggested attack scenarios in which we gained full control over the commercial products that implement Z-Wave. We analyzed the level 2 data flow diagram of actual products. The experimental results revealed that the major products that implement Z-Wave have several vulnerabilities.
A video demonstrating our experimental result can be found at https://youtu.be/sM-NlJexDPU.
中文翻译:

您的协议是什么:与Z-Wave协议相关的漏洞和安全威胁
随着最先进的应用程序和范例的发展,世界正朝着智慧城市发展。智能家居是智能城市的重要方面,其中使用了各种移动计算和网络技术。但是,它们也容易受到安全威胁的影响,可能导致与隐私和安全有关的严重问题。Z-Wave是一种主要用于智能家居的无线技术。但是,它的协议尚未得到充分研究。在本研究中,我们检查了Z-Wave协议的威胁模型以确定安全问题,并提出了攻击方案,在这些方案中我们获得了对实现Z-Wave的商业产品的完全控制。我们分析了实际产品的2级数据流程图。
可以在https://youtu.be/sM-NlJexDPU上找到演示我们实验结果的视频。











































 京公网安备 11010802027423号
京公网安备 11010802027423号