当前位置:
X-MOL 学术
›
Comput. Secur.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
FGMC-HADS: Fuzzy Gaussian Mixture-based Correntropy Models for detecting Zero-day Attacks from Linux Systems
Computers & Security ( IF 4.8 ) Pub Date : 2020-09-01 , DOI: 10.1016/j.cose.2020.101906 Waqas Haider , Nour Moustafa , Marwa Keshk , Amanda Fernandez , Kim-Kwang Raymond Choo , Abdul Wahab
Computers & Security ( IF 4.8 ) Pub Date : 2020-09-01 , DOI: 10.1016/j.cose.2020.101906 Waqas Haider , Nour Moustafa , Marwa Keshk , Amanda Fernandez , Kim-Kwang Raymond Choo , Abdul Wahab
|
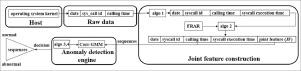
Abstract As existing system calls-based Host Anomaly Detection Systems (HADSs) exclude hidden patterns that can reside in the elapsed times of system calls with respect to the lifecycle of a kernel-calling process, they lack precision in the construction of behavioral regions for assisting in reliably protecting hosts against modern unknown attacks. In this paper, a HADS, the so-called Fuzzy Gaussian Mixture-based Correntropy (FGMC-HADS), based on the fuzzy rough set attribute reduction (FRAR) method, Gaussian mixture model (GMM) and Correntropy mechanism, is proposed. FGMC-HADS comprises two novel modules: (1) the FRAR method is applied to combine system calls’ identifiers and elapsed times to construct relevant hidden patterns; and (2) the GMM and Correntropy approaches is an anomaly detection technique, the so-called ’Corr-GMM’, developed to fuse multivariate features and recognize unknown anomalous activities, respectively. The posterior probabilities of the GMM are used as input to the Correntropy model to determine the time-series interdependencies of host activities, and then the Corr-GMM constructs legitimate boundaries as a threshold for discovering abnormal behaviors. The proposed FGMC-HADS is trained and validated using the datasets of NGIDS-DS, KDD-98 and new ToN_IoT of Linux data. The experimental results indicate that the proposed FGMC-HADS a reliable defense layer for Linux-based hosts against unknown attacks compared with other compelling HIDS techniques.
中文翻译:

FGMC-HADS:用于检测 Linux 系统零日攻击的基于模糊高斯混合的相关熵模型
摘要 由于现有的基于系统调用的主机异常检测系统 (HADS) 排除了可能存在于系统调用相对于内核调用过程的生命周期的经过时间中的隐藏模式,因此它们在构建行为区域以协助可靠地保护主机免受现代未知攻击。在本文中,基于模糊粗糙集属性约简(FRAR)方法、高斯混合模型(GMM)和相关熵机制,提出了一种HADS,即所谓的基于模糊高斯混合的相关熵(FGMC-HADS)。FGMC-HADS包括两个新颖的模块:(1)应用FRAR方法结合系统调用的标识符和经过的时间来构建相关的隐藏模式;(2) GMM 和 Correntropy 方法是一种异常检测技术,即所谓的“Corr-GMM”,分别用于融合多元特征和识别未知异常活动。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。
更新日期:2020-09-01
中文翻译:

FGMC-HADS:用于检测 Linux 系统零日攻击的基于模糊高斯混合的相关熵模型
摘要 由于现有的基于系统调用的主机异常检测系统 (HADS) 排除了可能存在于系统调用相对于内核调用过程的生命周期的经过时间中的隐藏模式,因此它们在构建行为区域以协助可靠地保护主机免受现代未知攻击。在本文中,基于模糊粗糙集属性约简(FRAR)方法、高斯混合模型(GMM)和相关熵机制,提出了一种HADS,即所谓的基于模糊高斯混合的相关熵(FGMC-HADS)。FGMC-HADS包括两个新颖的模块:(1)应用FRAR方法结合系统调用的标识符和经过的时间来构建相关的隐藏模式;(2) GMM 和 Correntropy 方法是一种异常检测技术,即所谓的“Corr-GMM”,分别用于融合多元特征和识别未知异常活动。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。GMM 的后验概率作为 Correntropy 模型的输入来确定宿主活动的时间序列相互依赖性,然后 Corr-GMM 构建合法边界作为发现异常行为的阈值。提议的 FGMC-HADS 使用 NGIDS-DS、KDD-98 和 Linux 数据的新 ToN_IoT 数据集进行训练和验证。实验结果表明,与其他引人注目的 HIDS 技术相比,所提出的 FGMC-HADS 是基于 Linux 的主机抵御未知攻击的可靠防御层。











































 京公网安备 11010802027423号
京公网安备 11010802027423号