当前位置:
X-MOL 学术
›
Trans. Emerg. Telecommun. Technol.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
Artificial bee colony method for identifying eavesdropper in terrestrial cellular networks
Transactions on Emerging Telecommunications Technologies ( IF 2.5 ) Pub Date : 2020-04-07 , DOI: 10.1002/ett.3941 D. Udaya Suriya Rajkumar 1 , P. Sunil Gavaskar 2 , Fadi Al-Turjman 3 , R. Sathiyaraj 4 , Balamurugan Balusamy 5
Transactions on Emerging Telecommunications Technologies ( IF 2.5 ) Pub Date : 2020-04-07 , DOI: 10.1002/ett.3941 D. Udaya Suriya Rajkumar 1 , P. Sunil Gavaskar 2 , Fadi Al-Turjman 3 , R. Sathiyaraj 4 , Balamurugan Balusamy 5
Affiliation
|
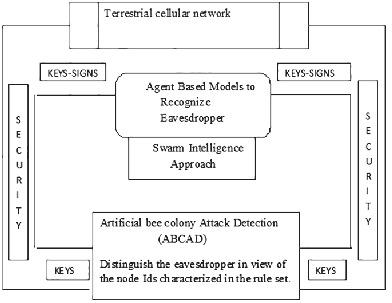
Nowadays, with the extensive variety of uses of the terrestrial cellular network, the security requirement for these networks is expanding enormously. Although these networks have faced various attacks, the eavesdropper is the most remarkable one. In this attack, once in a while, the foe node postures itself as a bogus base station (BS) and obtains information from achieving the main BS or changes the obtained information. In this article, a well-organized swarm intelligence approach is proposed within the context of agent-based models to recognize eavesdroppers, and artificial bee colony attack detection can distinguish the eavesdropper with regard to the node IDs characterized in the rule_set. The nodes that create a caution on distinguishing an intruder are assembled collectively. To recognize the intruder, a voting method is projected. Artificial bee colony Boolean sign generation is projected, which is distributed to the cautioned nodes in the grouping, the keys for sign the expect list to consent on the intruder. The proposed techniques recognize the aberrant relations without producing false positives and limit the capacity in the nodes of the terrestrial network, in contrast with Intrusion Detection Architecture, for the identification of eavesdroppers.
中文翻译:

一种识别地面蜂窝网络窃听者的人工蜂群方法
如今,随着地面蜂窝网络的广泛使用,对这些网络的安全要求正在急剧扩大。尽管这些网络面临各种攻击,但窃听者是最引人注目的一种。在这种攻击中,有时,敌方节点将自己伪装成一个虚假的基站(BS),并从实现主 BS 中获取信息或更改获取的信息。在本文中,在基于代理的模型的上下文中提出了一种组织良好的群体智能方法来识别窃听者,人工蜂群攻击检测可以根据规则集中表征的节点 ID 来区分窃听者。在区分入侵者时创建警告的节点被集合在一起。为了识别入侵者,投影了一种投票方法。人工蜂群布尔标志生成被投影,分发到分组中被警告的节点,用于签署期望列表以同意入侵者的密钥。 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 与入侵检测架构相比,所提出的技术在不产生误报的情况下识别异常关系并限制陆地网络节点的容量,以识别窃听者。
更新日期:2020-04-07
中文翻译:

一种识别地面蜂窝网络窃听者的人工蜂群方法
如今,随着地面蜂窝网络的广泛使用,对这些网络的安全要求正在急剧扩大。尽管这些网络面临各种攻击,但窃听者是最引人注目的一种。在这种攻击中,有时,敌方节点将自己伪装成一个虚假的基站(BS),并从实现主 BS 中获取信息或更改获取的信息。在本文中,在基于代理的模型的上下文中提出了一种组织良好的群体智能方法来识别窃听者,人工蜂群攻击检测可以根据规则集中表征的节点 ID 来区分窃听者。在区分入侵者时创建警告的节点被集合在一起。为了识别入侵者,投影了一种投票方法。人工蜂群布尔标志生成被投影,分发到分组中被警告的节点,用于签署期望列表以同意入侵者的密钥。 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 与入侵检测架构相比,所提出的技术在不产生误报的情况下识别异常关系并限制陆地网络节点的容量,以识别窃听者。











































 京公网安备 11010802027423号
京公网安备 11010802027423号