当前位置:
X-MOL 学术
›
Int. J. Commun. Syst.
›
论文详情
Our official English website, www.x-mol.net, welcomes your
feedback! (Note: you will need to create a separate account there.)
Design and performance analysis of an efficient single flow IP traceback technique in the AS level
International Journal of Communication Systems ( IF 1.7 ) Pub Date : 2020-03-10 , DOI: 10.1002/dac.4382 Morteza Arjmandpanah-Kalat 1 , Dariush Abbasinezhad-Mood 1 , Hamid-Reza Mahrooghi 1 , Sobhan Aliabadi 1
International Journal of Communication Systems ( IF 1.7 ) Pub Date : 2020-03-10 , DOI: 10.1002/dac.4382 Morteza Arjmandpanah-Kalat 1 , Dariush Abbasinezhad-Mood 1 , Hamid-Reza Mahrooghi 1 , Sobhan Aliabadi 1
Affiliation
|
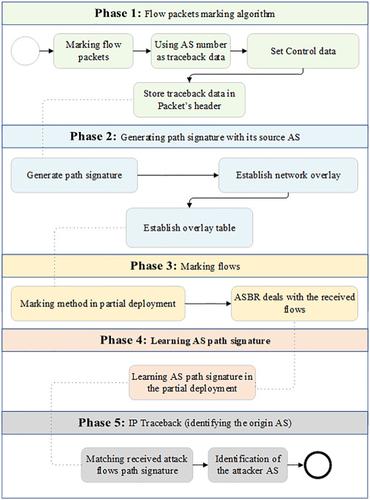
Network security is a major challenge for big and small companies. The Internet topology is vulnerable to Distributed Denial of Service (DDoS) attacks as it provides an opportunity to an attacker to send a large volume of traffic to a victim, which can limit its Internet availability. The main problem in the prevention of the DDoS attack, also known as the flooding attack, is how to find the source of traffic flooding. This is because the spoofed source Internet protocol (IP) address of packets is not affected on its routing. As a result, IP traceback techniques are proposed to find the source of attack and in general, to find the source of any packet. Doing so, the IP traceback techniques can help us to prevent the Denial of Service (DoS) and DDoS attacks. In this paper, we propose an efficient Single Flow IP Traceback (SFT) technique in the Autonomous System (AS) level. Furthermore, a path signature generation algorithm is presented for detecting and filtering the spoofed traffic. Our solution assumes a secure Border Gateway Protocol (BGP)‐routing infrastructure for exchanging authenticated messages in order to learn the path signatures, and it uses a marking algorithm in the flow level for transmission of the traceback messages. Because in our technique less bits are required to mark the IP header packet, the required storage space for any unique path to the victim is significantly decreased. Compared with the other existing techniques, the obtained results demonstrate that our technique has the least marking rate, overhead processing on the middle nodes, and destination's computational cost while offering the highest accuracy in tracebacking attack.
中文翻译:

AS级高效单流IP追溯技术的设计和性能分析
网络安全是大小公司的主要挑战。Internet拓扑易遭受分布式拒绝服务(DDoS)攻击,因为它为攻击者提供了向受害者发送大量流量的机会,这可能会限制Internet的可用性。防止DDoS攻击(也称为泛洪攻击)的主要问题是如何找到流量泛洪的来源。这是因为数据包的欺骗源Internet协议(IP)地址在其路由上不受影响。结果,提出了IP追溯技术来查找攻击源,并且通常可以找到任何数据包的源。这样做,IP追溯技术可以帮助我们防止拒绝服务(DoS)和DDoS攻击。在本文中,我们提出了一种在自治系统(AS)级别上有效的单流IP回溯(SFT)技术。此外,提出了一种路径签名生成算法,用于检测和过滤欺骗的流量。我们的解决方案假设使用安全的边界网关协议(BGP)路由基础结构来交换经过身份验证的消息,以学习路径签名,并且在流级别中使用标记算法来传输回溯消息。因为在我们的技术中,标记IP标头数据包所需的比特更少,所以显着减少了到受害者的任何唯一路径所需的存储空间。与其他现有技术相比,获得的结果表明我们的技术具有最低的标记率,中间节点的开销处理以及目标
更新日期:2020-03-10
中文翻译:

AS级高效单流IP追溯技术的设计和性能分析
网络安全是大小公司的主要挑战。Internet拓扑易遭受分布式拒绝服务(DDoS)攻击,因为它为攻击者提供了向受害者发送大量流量的机会,这可能会限制Internet的可用性。防止DDoS攻击(也称为泛洪攻击)的主要问题是如何找到流量泛洪的来源。这是因为数据包的欺骗源Internet协议(IP)地址在其路由上不受影响。结果,提出了IP追溯技术来查找攻击源,并且通常可以找到任何数据包的源。这样做,IP追溯技术可以帮助我们防止拒绝服务(DoS)和DDoS攻击。在本文中,我们提出了一种在自治系统(AS)级别上有效的单流IP回溯(SFT)技术。此外,提出了一种路径签名生成算法,用于检测和过滤欺骗的流量。我们的解决方案假设使用安全的边界网关协议(BGP)路由基础结构来交换经过身份验证的消息,以学习路径签名,并且在流级别中使用标记算法来传输回溯消息。因为在我们的技术中,标记IP标头数据包所需的比特更少,所以显着减少了到受害者的任何唯一路径所需的存储空间。与其他现有技术相比,获得的结果表明我们的技术具有最低的标记率,中间节点的开销处理以及目标











































 京公网安备 11010802027423号
京公网安备 11010802027423号