Abstract
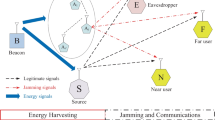
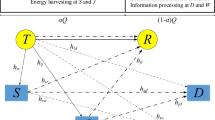
Spectrum sharing (SS) and energy harvesting (EH) basically improve spectrum-and-energy efficiencies required by modern communications systems. Nonetheless, most publications have focused on the linear (L) EH model which did not characterize practically non-linearities of EH circuits. Moreover, SS induces secondary receivers to suffer primary interference (PI) and facilitates eavesdroppers to overhear legitimate data. To secure communications in energy harvesting spectrum sharing networks (EHSSNs), this paper proposes a full-duplex (FD) secondary destination which not only receives legitimate signal but also jams signal reception of the eavesdropper. Joint effects of non-linear (NL) EH, PI, and FD destination-assisted jamming on security-and-reliability performances of EHSSNs are first analyzed in terms of outage and intercept probabilities that are then endorsed by Monte-Carlo simulations. Next, the proposed analysis is exploited to achieve the asymptotic analysis and the security-and-reliability analysis for two baseline EHSSNs (half-duplex (HD) destination and L EH). Finally, numerous results demonstrate joint effects of NL EH, PI, and FD destination on data security and communication reliability by comparing three EHSSNs: (i) L EH and FD destination; (ii) NL EH and FD destination; (iii) NL EH and HD destination. Notably, the proposed communications scheme with the FD destination is more secure than the baseline scheme with the HD destination. In addition, the reliability of the communications scheme with the NL EH is inferior to that with the L EH but the data security of the former is better than the latter. Additionally, the security-reliability trade-off exists for all the considered communications schemes. Moreover, the PI enhances the security but degrades the reliability. Furthermore, the time fraction for EH can be optimized to attain the best security-reliability trade-off.







Similar content being viewed by others
Notes
Raut et al. [11], Liu et al. [12], Kazmi et al. [4], Shanin et al. [30], Bayat et al. [31], Wang et al. [32], Ma et al. [33], Zhu et al. [34], Agrawal et al. [35], Shi et al. [36], and Dinh-Thuan et al. [37] studied non-spectrum sharing networks with NL EH and hence, such references should not be further surveyed.
Wang et al. [42] proposed the jamming signal as a pseudo-random sequence whose seed of this sequence generator at \(\text{D}\) can be embedded in a short secret key, which is shared merely with \(\text{R}\), not with \(\text{E}\).
References
Tashman, D. H., & Hamouda, W. (2021). Physical-layer security on maximal ratio combining for SIMO cognitive radio networks over cascaded \(\kappa -\mu \) fading channels. IEEE Transactions on Cognitive Communications and Networking, 7(4), 1244–1252.
Yadav, S., & Gurjar, D. S. (2021). Secrecy performance of SIMO underlay cognitive radio networks over \(\alpha -\mu \) fading channels. IEEE Access, 9, 62616–62629.
Ho-Van, K., Sofotasios, P. C., Muhaidat, S., Cotton, S. L., Yoo, S. K., Brychkov, Y. A., Dobre, O. A., & Valkama, M. (2021). Security improvement for energy harvesting based overlay cognitive networks with jamming-assisted full-duplex destinations. IEEE Transactions on Vehicular Technology, 70(11), 12232–12237.
Kazmi, S. A. A., & Coleri, S. (2020). Optimization of full-duplex relaying system with non-Linear energy harvester. IEEE Access, 8, 201566–201576.
Ji, B., Li, Y., Cao, D., Li, C., Mumtaz, S., & Wang, D. (2020). Secrecy performance analysis of UAV assisted relay transmission for cognitive network With energy harvesting. IEEE Transactions on Vehicular Technology, 69(7), 7404–7415.
Xu, Y., Xie, H., Liang, C., & Yu, F. R. (2021). Robust secure energy efficiency optimization in SWIPT-aided heterogeneous networks with a non-linear energy harvesting model. IEEE IoT Journal, 8(19), 14908–14919.
Gautam, S., Lagunas, E., Chatzinotas, S., & Ottersten, B. (2019). Relay selection and resource allocation for SWIPT in multi-user OFDMA systems. IEEE Transactions on Wireless Communications, 18(5), 2493–2508.
Xu, X., Özçelikkale, A., McKelvey, T., & Viberg, M. (2017). Simultaneous information and power transfer under a non-linear RF energy harvesting model. In Proc. (pp. 179–184). IEEE ICC.
Clerckx, B. (2018). Wireless information and power transfer: nonlinearity, waveform design, and rate-energy tradeoff. IEEE Transactions on Signal Processing, 66(4), 847–862.
Babaei, M., Aygölü, Ü., Basaran, M., & Durak-Ata, L. (2020). BER performance of full-duplex cognitive radio network With nonlinear energy harvesting. IEEE Transactions on Green Communications and Networking, 4(2), 448–460.
Raut, P., Sharma, P. K., Tsiftsis, T. A., & Zou, Y. (2020). Power-time splitting-based non-linear energy harvesting in FD short-packet communications. IEEE Transactions on Vehicular Technology, 69(8), 9146–9151.
Liu, Y., Ye, Y., Ding, H., Gao, F., & Yang, H. (2020). Outage performance analysis for SWIPT-based incremental cooperative NOMA networks with non-linear harvester. IEEE Communications Letters, 24(2), 287–291.
Lu, G., Shi, L., & Ye, Y. (2018). Maximum throughput of TS/PS scheme in an AF relaying network with non-linear energy harvester. IEEE Access, 6, 26617–26625.
Sadique, J. J., Ullah, S. E., Islam, M. R., Raad, R., Kouzani, A. Z., & Mahmud, M. P. (2021). Transceiver design for full-duplex UAV based zero-padded OFDM system with physical layer security. IEEE Access, 9, 59432–59445.
Ho-Van, K., & Do-Dac, T. (2021). Overlay networks with jamming and energy harvesting: security analysis. Arabian Journal for Science and Engineering, 46, 9713–9724.
Yang, H., Xia, X., Li, J., Zhu, P., & You, X. (2022). Joint transceiver design for network-assisted full-duplex systems with SWIPT. IEEE Systems Journal, 16(1), 1206–1216.
Thakur, A., Kumar, A., Gupta, N., & Chatterjee, P. (2022). Secrecy analysis of reconfigurable underlay cognitive radio networks with SWIPT and imperfect CSI. IEEE Transactions on Network Science and Engineering, 9(1), 89–97.
Yan, P., Zou, Y., & Zhu, J. (2018). Energy-aware multiuser scheduling for physical-layer security in energy-harvesting underlay cognitive radio systems. IEEE Transactions on Vehicular Technology, 67(3), 2084–2096.
Wang, X., Na, Z., Lam, K. Y., Liu, X., Gao, Z., Li, F., & Wang, L. (2019). Energy efficiency optimization for NOMA-based cognitive radio with energy harvesting. IEEE Access, 7, 139172–139180.
Ge, L., Chen, G., Zhang, Y., Tang, J., Wang, J., & Chambers, J. A. (2020). Performance analysis for multihop cognitive radio networks with energy harvesting by using stochastic geometry. IEEE IoT Journal, 7(2), 1154–1163.
Bouabdellah, M., El Bouanani, F., Sofotasios, P. C., Muhaidat, S., Da Costa, D. B., Mezher, K., Ben-Azza, H., & Karagiannidis, G. K. (2019). Cooperative energy harvesting cognitive radio networks with spectrum sharing and security constraints. IEEE Access, 7, 173329–173343.
Wang, D., Zhou, F., & Leung, V. C. (2020). Primary privacy preserving with joint wireless power and information transfer for cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 6(2), 683–693.
Shi, H., Cai, Y., Chen, D., Hu, J., Yang, W., & Yang, W. (2019). Physical layer security in an untrusted energy harvesting relay network. IEEE Access, 7, 24819–24828.
Ho-Van, K., & Do-Dac, T. (2020). Security performance of underlay cognitive relaying networks with energy harvesting. Wireless Personal Communications, 110(2), 829–846.
Ho-Van, K., & Do-Dac, T. (2020). Security enhancement for energy harvesting cognitive networks with relay selection. Wireless Communications and Mobile Computing, 2020, 1–13.
Zhao, W., She, R., & Bao, H. (2019). Security energy efficiency maximization for two-way relay assisted cognitive radio NOMA network with self-interference harvesting. IEEE Access, 7, 74401–74411.
Su, R., Wang, Y., & Sun, R. (2019). Secure cooperative transmission in cognitive AF relay systems with destination-aided jamming and energy harvesting. In Proc. (pp. 1–5). IEEE PIMRC.
Xu, M., Jing, T., Fan, X., Wen, Y., & Huo, Y. (2018). Secure transmission solutions in energy harvesting enabled cooperative cognitive radio networks. In Proc. (pp. 1–6). IEEE WCNC.
Su, R., Wang, Y., & Sun, R. (2018). Destination-assisted jamming for physical-layer security in SWIPT cognitive radio systems. In Proc. (pp. 1–6). IEEE WCNC.
Shanin, N., Cottatellucci, L., & Schober, R. (2021). Markov decision process based design of SWIPT systems: Non-linear EH circuits, memory, and impedance mismatch. IEEE Transactions on Communications, 69(2), 1259–1274.
Bayat, S., Khalili, A., & Han, Z. (2020). Resource allocation for MC MISO-NOMA SWIPT-enabled HetNets with non-linear energy harvesting. IEEE Access, 8, 192270–192281.
Wang, D., et al. (2020). Performance analysis and resource allocations for a WPCN With a new nonlinear energy harvester model. IEEE OJ-CS, 1, 1403–1424.
Ma, G., Xu, J., Liu, Y. F., & Moghadam, M. R. V. (2021). Time-division energy beamforming for multiuser wireless power transfer with non-linear energy harvesting. IEEE Wireless Communications Letters, 10(1), 53–57.
Zhu, Z., Wang, N., Hao, W., Wang, Z., & Lee, I. (2021). Robust beamforming designs in secure MIMO SWIPT IoT networks with a non-linear channel model. IEEE IoT Journal, 8(3), 1702–1715.
Agrawal, K., Flanagan, M. F., & Prakriya, S. (2020). NOMA with battery-assisted energy harvesting full-duplex relay. IEEE Transactions on Vehicular Technology, 69(11), 13952–13957.
Shi, L., Cheng, W., Ye, Y., Zhang, H., & Hu, R. Q. (2018). Heterogeneous power-splitting based two-way DF relaying with non-linear energy harvesting. In Proc. (pp. 1–7). IEEE GLOBECOM.
Do, D. T., Le, C. B., & Le, A. T. (2020). Joint of full-duplex relay, non-linear energy harvesting and multiple access in performance improvement of cell-edge user in heterogeneous networks. Wireless Networks, 26(8), 6253–6266.
Wang, D., & Men, S. (2018). Secure energy efficiency for NOMA based cognitive radio networks with nonlinear energy harvesting. IEEE Access, 6, 62707–62716.
Ni, L., Da, X., Hu, H., Zhang, M., & Cumanan, K. (2020). Outage constrained robust secrecy energy efficiency maximization for EH cognitive radio networks. IEEE Wireless Communications Letters, 9(3), 363–366.
Solanki, S., Upadhyay, P. K., Da Costa, D. B., Ding, H., & Moualeu, J. M. (2020). Performance analysis of piece-wise linear model of energy harvesting-based multiuser overlay spectrum sharing networks. IEEE OJ-CS, 1, 1820–1836.
Hakimi, A., Mohammadi, M., Mobini, Z., & Ding, Z. (2020). Full-duplex non-orthogonal multiple access cooperative spectrum-sharing networks with non-linear energy harvesting. IEEE Transactions on Vehicular Technology, 69(10), 10925–10936.
Wang, F., & Zhang, X. (2020). Secure resource allocation for polarization-based non-linear energy harvesting over 5G cooperative CRNs. IEEE Wireless Communications Letters (accepted). https://ieeexplore.ieee.org/document/9212400/.
Maji, P., Roy, S. D., & Kundu, S. (2019). Physical layer security with non-linear energy harvesting relay. In Proc. (pp. 1–6). IEEE ICCCNT.
Bharadia, D., McMilin, E., & Katti, S. (2013). Full duplex radios. In Proc. ACM SIGCOMM, HongKong (pp. 375–386).
Li, M., Huang, Y., Yin, H., Wang, Y., & Cai, C. (2019). Improving the security and spectrum efficiency in overlay cognitive full-duplex wireless networks. IEEE Access, 7, 68359–68372.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series and products (6th ed.). Academic Press.
Abramowitz, M., & Stegun, I. A. (1972). Handbook of mathematical functions with formulas, graphs, and mathematical tables (10th ed.). U.S. Government Printing Office.
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2019.318. We acknowledge Ho Chi Minh City University of Technology (HCMUT), VNU-HCM for supporting this study.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix A: Proof for the PDF of \(P_s\) in (28)
Appendix A: Proof for the PDF of \(P_s\) in (28)
To obtain the PDF of \(P_s\), one firstly needs the CDF of \(P_s\). Plugging (10) into the definition of the CDF results in
The \(\mathcal{P}_2\) term can be rewritten in terms of the CDF of \(g_{ps}\) as
Given \(\hat{P}_s\) in (1), the \(\mathcal{P}_1\) term is further decomposed as
To complete the derivation of (53), three cases should be considered as follows:
Case 1: \(x \le {A_s}{P_l}\)
This case simplifies (53) as
Case 2: \({A_s}{P_l} < x \le {A_s}{P_u}\)
This case simplifies (53) as
Case 3: \(x > {A_s}{P_u}\)
This case simplifies (53) as
Plugging \({{\mathcal{P}}_1}\) and \({{\mathcal{P}}_2}\) into (51), one obtains the CDF of \(P_s\) as
The derivative of \({F_{P_s}}\left( x \right) \), which is simplified as (28), is the PDF of \(P_s\), completing the proof.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Joint effects of non-linear energy harvesting, primary interference, and full-duplex destination-assisted jamming on spectrum sharing networks. Wireless Netw 29, 221–234 (2023). https://doi.org/10.1007/s11276-022-03119-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-03119-1