Abstract
The use of background checks has become more prevalent and is perceived as having crucial importance in hiring in the private sector, given the extent of employee crimes. In examining this phenomenon, security and administration scholars have promoted the general security necessity of such checks but have only focused on the application of legal and constitutional provisions relevant to the background check process. As a result, the security field has overlooked the theoretical bases for background checks and the theories addressing how background checks should be conducted. To address this gap, this article presents a qualitative meta-analysis of the theoretical literature from a variety of academic fields and identifies four overarching themes important for understanding background checks as a tool for hiring. Then, as an illustration, the article examines how well the regulation of background checks in the U.S. financial sector reflects theoretical findings, exposing critical gaps between research and practice. Thus, this analysis provides security practitioners with important guidance in how to effectively use background checks as a crime prevention tool.
Similar content being viewed by others
Notes
In their most recent report, their 10th edition, ACFE analyzed 2,690 cases across 120 countries. The cases analyzed in their study were chosen from the results of a survey the organization sends to members. While this study has methodological limitations, it is the largest known comprehensive study on occupational crime conducted on a regular basis.
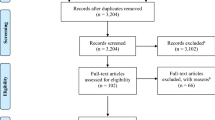
As explained further in the methods section below, the population of research literature examined was narrowed to include literature where background checks were discussed and also at least one theoretical perspective was mentioned.
All the theories that the researchers encountered are included here. No theory was included or excluded based on the numbers of mentions in articles.
The FDIC published proposed rules in the Federal Register in December 2019, and public comments were invited to be submitted through February 2020. Currently, the FDIC Board of Directors are considering the comments and how to proceed with the proposed amendments.
References
Albarracin, D., B.T. Johnson, M. Fishbein, and P.A. Muellerleile. 2001. Theories of reasoned action and planned behavior as models of condom use: A meta-analysis. Psychological Bulletin 127 (1): 142–161.
Arjoon, S. 2006. Striking a balance between rules and principles-based approaches for effective governance: A risks-based approach. Journal of Business Ethics 68 (1): 53–82.
Association of Certified Fraud Examiners (ACFE). 2002–2018. Report to the Nations. ACFE.com.
Atkinson, P. 2017. Thinking ethnographically. Sage.
Atkinson, D.V., and K. Lockwood. 2015. The benefits of ban the box: A case study of Durham, NC. Social Coalition for Social Justice.
Backman, C. 2012. Mandatory criminal record checks in Sweden: Scandals and function creep. Surveillance and Society 10 (3/4): 276–291.
Beach, L.R., and T.R. Mitchell. 1987. Image theory: Principles, goals and plans in decision making. Acta Psychologica 66 (3): 201–220.
Beach, L.R., B. Smith, J. Lundell, and T.R. Mitchell. 1988. Image theory: Descriptive sufficiency of a simple rule for the compatibility test. Journal of Behavioral Decision Making 1: 17–28.
Berkelaar, B.L. 2014. Cybervetting, online information, and personnel selection: New transparency expectations and the emergence of a digital social contract. Management Communication Quarterly 28 (4): 479–506.
Blumstein, A., and K. Nakamura. 2009. Redemption in the presence of widespread criminal background checks. Criminology 47 (2): 327–359.
Brody, R.G. 2010. Beyond the basic background check: Hiring the. Management Research Review 33 (3): 210–223.
Brody, R.G., F.S. Perri, and H.J. Van Buren. 2015. Further beyond the basic background check: Predicting future unethical behavior. Business and Society Review 120 (4): 549–576.
Burgemeestre, B., J. Hulstijn, and Y.H. Tan. 2009. Rule-based versus principle-based regulatory compliance. In JURIX: 37–46.
Bushway, S., P. Nieuwbeerta, and A. Blokland. 2011. The predictive value of criminal background checks: Do age and criminal history affect time to redemption. Criminology 9 (1): 27–60.
Calder, J.D. 1987. New Corporate Security: The autumn of crime control and the spring of fairness and due process. Journal of Contemporary Criminal Justice 3 (4): 1–34.
Clozel, L. 2019. Small time crimes a dealbreaker for banking jobs. The Wall Street Journal.https://www.wsj.com/articles/small-time-crimes-a-dealbreaker-for-banking-jobs-11555851720.
Cohen, L., and M. Felson. 1979. Social change and crime rate trends: A routine activity approach. American Sociological Review 44 (4): 588–608.
Cornelius, C.V., C.J. Lynch, and R. Gore. 2017. Aging out of crime: Exploring the relationship between age and crime with agent-based modeling. Agent-Directed Simulation Symposium, Article No. 3, Virginia Beach.
Cozzetto, D.A., and T.B. Pedeliski. 1996. Privacy and the workplace. Review of Public Personnel Administration, Spring: 21–31.
Creed, T.L. 2008. Negligent hiring and criminal rehabilitation: Employing ex-convicts, yet avoiding liability. Thomas L. Rev. 20: 183–204.
Cummings, A., T. Lewellen, D. McIntire, A.P. Moore, and R. Trzeciak. 2012. Insider threat study: Illicit cyber activity involving fraud in the U.S. financial services sector, CERT Program, Carnegie Mellon.
Denver, M., G. Siwach, and S. Bushway. 2017. A new look at the employment and recidivism relationship through the lens of a criminal background check. Criminology 55 (1): 74–204.
Desio, P. An overview of the organizational guidelines, [Undated]. Deputy General Counsel, United States Sentencing Commission.
Donaldson, T., and T.W. Dunfee. 1994. Toward a unified conception of business ethics: Integrative social contracts theory. Academy of Management Review 19 (2): 252–264.
EEOC (Equal Employment Opportunity Commission) and FTC (Federal Trade Commission) [Undated]. Background checks: What employers need to know.https://www.eeoc.gov/eeoc/publications/upload/eeoc_ftc_background_checks_employers.pdf.
Evans, L. 2007. Monitoring technology in the American workplace: Would adopting English privacy standards better balance employee privacy and productivity? Cal. Law Review 95: 1115–1150.
Fales, A. 2012. Background check: Wells Fargo employee fired. Channel 13 WHO Tv. https://whotv.com/2012/05/10/background-check-wells-fargo-employee-fired/.
FDIC. 2014. Law, Regulations, Related Acts, Section 19 Penalty for Unauthorized Participation by Convicted Individual. https://www.fdic.gov/regulations/laws/rules/1000-2100.html.
FDIC. 2018. Your complete guide to Section 19.https://www.fdic.gov/regulations/applications/resources/brochure-section-19.pdf.
Feeley, K.M. 2012. Hiring sexters to teach children: Creating predictable and flexible standards for negligent hiring in schools. NML Rev. 42: 83–130.
Federal Register. FDIC incorporation of existing statement of policy regarding requests for participation in the affairs of an insured depository institution by convicted individuals. Proposed Rules. Vol. 84, No. 241.
Federal Trade Commission (FTC). 2006. Financial institutions and customer information: Complying with the Safeguards Rule.https://www.ftc.gov/tips-advice/business-center/guidance/financial-institutions-customer-information-complying.
Financial Crime Enforcement Network’s (FinCEN) Know Your Customer requirements. 2016. Federal Register, Vol. 81, No. 91.
Gerlach, E. 2006. The background check balancing act: Protecting applicants with criminal convictions while encouraging criminal background checks in hiring. U.PA. Journal of Labor and Employment Law 8 (4): 981–1000.
Greenfield, W.M. 2004. Attention to people and principles is key to corporate governance and ethics. New York: Wiley.
Harris, P.M., and K.S. Keller. 2005. Ex-offenders need not apply: The criminal background check in hiring decisions. Journal of Contemporary Criminal Justice 21 (1): 6–30.
Heimer, M. 2019. Why JPMorgan Chase wants to give more former criminals a second chance. Fortune, 21 October. Retrieved September 14, 2020, from https://fortune.com/2019/10/21/jpmorgan-chase-ban-the-box-hiring/.
Heltman, J. 2019. FDIC plan would make it easier for banks to hire ex-cons. American Banker.https://www.americanbanker.com/news/fdic-plan-would-make-it-easier-for-banks-to-hire-ex-cons.
Holtzer, H.J., S. Raphael, and M.A. Stoll. 2006. Perceived criminality, criminal background checks and the racial hiring practices of employers. The Journal of Law & Economics 49 (2): 451–480.
Hoon, C. 2013. Meta-synthesis or qualitative case studies. Organizational Research Methods 76 (4): 522–556.
Huberman, A.M., and M.B. Miles. 2009. The qualitative researcher's companion. Thousand Oaks: Sage Publ.
Jaccard, J., and G. Wood. 1988. The effects of incomplete information on the formation of attitudes toward behavioral alternatives. Journal of Personality and Social Psychology 54 (4): 580–591.
Johnson, R.D. 1987. Making judgments when information is missing: Inferences, biases and framing effects. Acta Psychologica 66 (1): 69–82.
Johnson, R.D., and I.P. Levin. 1985. More than meets the eye: The effect of missing information on purchase evaluations. Journal of Consumer Research 12 (2): 69–177.
J.P.Morgan Chase & Co. 2019. Reducing Barriers to Employment in the Banking Industry for Qualified Individuals with Criminal Records. https://www.jpmorganchase.com/corporate/Corporate-Responsibility/document/hiring-reform.pdf.
Kuhn, K.M. 2013. What we overlook: Background checks and their implications for discrimination. Industrial and Organizational Psychology 6 (4): 419–423.
Laub, J.H., and R.J. Sampson. 1993. Turning points in the life course: Why change matters in the study of crime. Criminology 31 (3): 301–325.
Lee, M.A. 2017. Do criminal background checks in hiring punish? Washington University Jurisprudence Review 9: 27–352.
Levashina, J., and J. Campion. 2009. Expected practices in background checking: Review of the human resource management literature. Employee Responsibilities and Rights Journal 21: 231–249.
Lichtblau, E. 2016. U.S. to curb queries on criminal histories of government job seekers. The New York Times. https://www.nytimes.com/2016/04/29/us/politics/criminal-history-job-applicants-prisoners-background-check.html.
Lipman, I. 1988. Personnel selection in the private security industry: More than a resume. The Annals of the American Academy of Political and Social Science 498: 83–90.
Mael, F.A. 1991. A conceptual rationale for the domain and attributes of biodata items. Personnel Psychology 44 (4): 763–792.
Mael, F.A., and B.E. Ashforth. 1995. Loyal from day one: Biodata, organizational identification, and turnover among newcomers. Personnel Psychology 48 (2): 309–333.
Martin, K. 2012. Diminished or just different? A factorial vignette study of privacy as a social contract. Journal of Business Ethics 111: 519–539.
Martin, M., and J. French. 2013. Collections and crime: The case of Citibank in Indonesia. Journal of Business Cases and Applications 7: 1.
Maurer, R. 2017. Know before you hire: 2017 employment screening trends. The Society for Human Resource Management.https://www.shrm.org/resourcesandtools/hr-topics/talent-acquisition/pages/2017-employment-screening-trends.aspx.
Merton, R.K. 1936. The unanticipated consequences of purposive social action. American Sociological Review 1 (6): 894–904.
Millard, E. 2007. Online background checks: As social networking sites grow, so does the ability of employers to discriminate. ABA Journal 93 (1): 37.
Mullaney, T. 2018. Why companies are turning to ex-cons to fill slots for workers. CNBC.https://www.cnbc.com/2018/09/18/why-companies-are-turning-to-ex-cons-to-fill-slots-for-workers.html.
Mulvaney, E. 2018. Wells Fargo lawfully fired employees over background checks, appeals court says. Think Advisor.
Mumford, M.D., and W.A. Owens. 1987. Methodology review: Principles, procedures, and findings in the application of background data measures. Applied Psychological Measurement 11 (1): 1–31.
Mumford, M.D., and G.S. Stokes. 1991. Developmental determinants of individual action: Theory and practice in the application of background data. The Handbook of Industrial and Organizational Psychology 2: 1–78.
Mumford, M.D., G.S. Stokes, and W.A. Owens. 1990. Patterns of life history: The ecology of human individuality. Hillsdale: Lawrence Erlbaum Associates.
Patriot Act of 2001, Pub. L. No. 107-56.
Petersen, Ian B. 2015. Toward true fair chance hiring: Balancing stakeholder interests and reality in regulating criminal background checks. Texas Law Review 94 (1): 176–203.
Piquero, A.R. 2008. Taking stock of developmental trajectories of criminal activity over the life course. In The long view of crime: A synthesis of longitudinal research, ed. A.M. Liberman, 23–78. New York: Springer.
Ponemon Institute. 2015. Cost of cybercrime study: Global.
Prenzler, T., and R. Sarre. 2008. Developing a risk profile and model regulatory system for the security industry. Security Journal 21 (4): 264–277.
Proctor, T. 2005. Family ties in the making of modern intelligence. Journal of Social History 39 (2): 451–466.
Rigakos, G.S., R.C. Davis, C. Ortiz, A. Blunt, and J. Broz. 2009. Soft targets? A national survey of the preparedness of large retail malls to prevent and respond to terrorist attacks after 9/11. Security Journal 22 (4): 286–301.
Rodriguez, M.N., and B. Avery. 2017. Ban the Box. National Employment Law Project.
Ross, A.S., 2012. Under federal law, banks crack down on employees who were jailed, no matter how minor their mistake. San Francisco Chronicle, 31 August. Retrieved September 14, 2020, from https://www.pressreader.com/usa/san-francisco-chronicle-late-edition/20120831/281556583001955.
Roth, P.L., P. Bobko, C.H. Van Iddekinge, and J. Thatcher. 2016. Social media in employee selection decisions: A research agenda for unchartered territory. Journal of Management 42 (1): 269–298.
Sandelowski, M. 2004. Qualitative meta-analysis. In The SAGE encyclopedia of social science research methods, vol. 3, ed. M. Lewis-Beck, A. Bryman, and T.F. Laio, 892. Thousand Oaks: Sage Publications.
Schoeff, M. 2015. SEC approves FINRA background check rule. Investment News.
Seidl, C., and S. Traub. 1998. A new test of image theory. Organizational Behavior and Human Decision Processes 75 (2): 93–116.
Smith, J.J. 2014. Banning the box but keeping the discrimination: Disparate impact and employers’ overreliance on criminal background checks. Harvard Civil Rights-Civil Liberties Law Review 49: 197–228.
Smith, C., and D. Brooks. 2013. Security science: The theory and practice of security. Amsterdam: Elsevier.
Solinas-Saunders, M., and M.J. Stacer. 2015. An analysis of ‘ban the box’ policies through the prism of Merton’s theory of unintended consequences of purposive social action. Critical Sociology 41 (7–8): 1187–1198.
Stohl, C., M. Etter, S. Banghart, and D. Woo. 2017. Social media policies: Implications for contemporary notions of corporate social responsibility. Journal of Business Ethics 142 (3): 413–436.
Strahilevitz, K.J. 2010. Reunifying privacy law. California Law Review 98 (6): 2007–2048.
Tajfel, H. 1978. The achievement of group differentiation. In Differentiation between social groups: Studies in the social psychology of intergroup relations, ed. H. Tajfel, 77–98. London: Academic Press.
Tufts, S.H., W.S. Jacobson, and M.S. Stevens. 2015. Status update: Social media and local government human resource practices. Review of Public Personnel Administration 35 (2): 193–207.
Valeau, P.J. 2015. Stages and pathways of development of nonprofit organizations: An integrative model. VOLUNTAS: International Journal of Voluntary and Nonprofit Organizations 26 (5): 1894–1919.
Wang, X., D. Mears, and W.D. Bales. 2010. Race-specific employment contexts and recidivism. Criminology 48 (4): 1171–1211.
Weiman, D.F. 2007. Barriers to prisoners' reentry into the labor market and the social costs of recidivism. Social Research 74 (2): 575–611.
Weissert, E.P. 2016. Get out of jail free? Preventing employment discrimination against people with criminal records using ban the box laws. University of Pennsylvania Law Review 164: 1529–1555.
Young, N.C.J., and G.N. Powell. 2015. Hiring ex-offenders: A theoretical model. Human Resource Management Review 25 (3): 298–312.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Binns, C.A., Kempf, R.J. Background checks: the theories behind the process. Secur J 34, 776–801 (2021). https://doi.org/10.1057/s41284-020-00260-4
Published:
Issue Date:
DOI: https://doi.org/10.1057/s41284-020-00260-4