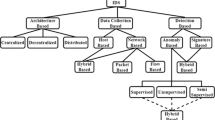
Abstract
With the increase in the usage of the Internet, a large amount of information is exchanged between different communicating devices. The data should be communicated securely between the communicating devices and therefore, network security is one of the dominant research areas for the current network scenario. Intrusion detection systems (IDSs) are therefore widely used along with other security mechanisms such as firewall and access control. Many research ideas have been proposed pertaining to the IDS using machine learning (ML) techniques, deep learning (DL) techniques, and swarm and evolutionary algorithms (SWEVO). These methods have been tested on the datasets such as DARPA, KDD CUP 99, and NSL-KDD using network features to classify attack types. This paper surveys the intrusion detection problem by considering algorithms from areas such as ML, DL, and SWEVO. The survey is a representative research work carried out in the field of IDS from the year 2008 to 2020. The paper focuses on the methods that have incorporated feature selection in their models for performance evaluation. The paper also discusses the different datasets of IDS and a detailed description of recent dataset CIC IDS-2017. The paper presents applications of IDS with challenges and potential future research directions. The study presented, can serve as a pedestal for research communities and novice researchers in the field of network security for understanding and developing efficient IDS models.















Similar content being viewed by others
Notes
DARPA https://www.ll.mit.edu/r-d/datasets Last accessed: 24, August, 2020.
KDD CUP 99
https://www.kdd.org/kdd-cup/view/kdd-cup-1999/Data Last accessed: 24, August, 2020.
NSL-KDD https://www.unb.ca/cic/datasets/nsl.html Last accessed: 24, August, 2020.
DEFCON https://www.defcon.org/html/links/dc-torrent.html Last accessed: 24, August, 2020.
CAIDA https://www.caida.org/data/about/downloads/ Last accessed: 24, August, 2020.
LBNL https://powerdata.lbl.gov/download.html Last accessed: 24, August, 2020.
CDX http://www.fit.vutbr.cz/~ihomoliak/asnm/ASNM-CDX-2009.html Last accessed: 24, August, 2020.
Kyoto https://www.takakura.com/Kyoto_data/ Last accessed: 24, August, 2020.
Twente https://www.utwente.nl/en/eemcs/ps/research/dataset/ Last accessed: 24, August, 2020.
UMASS http://traces.cs.umass.edu/index.php/Network/Network Last accessed: 24, August, 2020.
ISCX2012 https://www.unb.ca/cic/datasets/ids.html Last accessed: 24, August, 2020.
ADFA https://www.unsw.adfa.edu.au/unsw-canberra-cyber/cybersecurity/ADFA-IDS-Datasets/ Last accessed: 24, August, 2020.
UNSW-NB15 https://www.unsw.adfa.edu.au/unsw-canberra-cyber/cybersecurity/ADFA-NB15-Datasets/ Last accessed: 24, August, 2020.
CIC-IDS-2017 https://www.unb.ca/cic/datasets/ids-2017.html Last accessed: 24, August, 2020.
Abbreviations
- DNN:
-
Deep Neural Network
- DBN:
-
Deep Belief Network
- SDN:
-
Software Defined Network
- HAST-IDS:
-
Hierarchical Spatial-Temporal features-based Intrusion Detection System
- LSTM:
-
Long Short Term Memory
- CAIDA:
-
Center for Applied Internet Data Analysis
- IRC:
-
Internet Relay Chat
- MAE:
-
Mean Absolute Error
- MSE:
-
Mean Squared Error
- ARI:
-
Adjusted Rand Index
- MI:
-
Mutual Information
- AMI:
-
Adjusted Mutual Information
- NMI:
-
Normalized Mutual Information
- FMI:
-
Fowlkes Mallows scores
- SMS:
-
Short Message Service
- CSAIL:
-
Computer Science and Artificial Intelligence Laboratory
- DDoS:
-
Distributed Denail of Service
- R2L:
-
Remote to Local
- RFE:
-
Recursive Feature Elimination
- U2R:
-
User to Root
- DoS:
-
Denial of Service
- ELM:
-
Extreme Learning Machine
- FP:
-
False Positive
- TP:
-
True Positive
- FN:
-
False Negative
- TN:
-
True Negative
- NSA:
-
Negative Selection Algorithm
- AIS:
-
Artificial Immune System
- SNS:
-
Self-NonSelf
- RSKFCM:
-
Robust Spatial Kernel Fuzzy C-Means
- EM:
-
Expectation Maximization
- SMO:
-
Sequential Minimal Optimization
- PAM:
-
Partition Around Mediods
- CLARA:
-
Clustering Large Applications
- LMDRT:
-
Logarithmic Marginal Density Ration Transformation
- DT:
-
Decision Tree
- IG:
-
Information Gain
- SVM:
-
Support Vector Machine
- FAR:
-
False Alram Rate
- DR:
-
Detection Rate
- ROC:
-
Receiver Operating Characteristics
- MLP:
-
Multi-Layer Percepton
- ANN:
-
Artificial Neural Network
- PCA:
-
Principal Component Analysis
- CC:
-
Correlation Coefficient
- SA:
-
Simulated Annealing
- CFS:
-
Correlation Feature Selection
- FVBRM:
-
Feature Vitality Based Reduction Method
- KDD:
-
Knowledge Discovery Database
- LS-SVM:
-
Least Square-Support Vector Machine
- EMFFS:
-
Ensemble Multi-Filter Feature Selection
- RBF:
-
Radial Basis Function
- TPR:
-
True Positive Rate
- FPR:
-
False Positive Rate
- MIFS:
-
Mutual Information Feature Selection
- FMIFS:
-
Flexible Mutual Information based Feature Selection
- FLCFS:
-
Flexible Linear Correlation based Feature Selection
- TASVM:
-
Triangle Area Support Vector Machine
- k-NN:
-
k Nearest Neighbour
- BPN:
-
Back Propogation Network
- NB:
-
Naïve Bayes
- KMC:
-
K-Means Clustering
- CANN:
-
Cluster Centers and Nearest Neighbours
- SOM:
-
Self Organizing Maps
- MOPF:
-
Modified Optimum Path Forest
- DPC:
-
Density Peak Clustering
- RNN:
-
Recurrent Neural Network
- CPE:
-
Cost Per Example
- RBNN:
-
Radial Basis Neural Network
- FFNN:
-
Feed Forward Neural Network
- GRNN:
-
Generalized Regression Neural Network
- PNN:
-
Probabilistic Neural Network
- GRU-RNN:
-
Gated Recurrent Unit-Recurrent Neural Network
- RBM:
-
Restricted Boltzmann Machine
- PE:
-
Portable Executable
- CNN:
-
Convolutional Neural Network
- ISCX:
-
Information Security Center of Excellence
- GA:
-
Genetic Algorithm
- PSO:
-
Particle Swarm Optimization
- GNP:
-
Genetic Network Programming
- LR:
-
Logistic Regression
- HG-GA:
-
HyperGraph-Genetic Algorithm
- GSA:
-
Genetic Selection Algorithm
- ER:
-
Error Rate
- CFO:
-
Cuttle Fish Optimization
- AR:
-
Accuracy Rate
- KPCA:
-
Kernel-Principal Component Analysis
- CART:
-
Classification and Regression Tree
- BA:
-
Bat Algorithm
- ACO:
-
Ant Colony Optimization
- LUS:
-
Local Unimodal Sampling
- WMA:
-
Weighted Majority Algorithm
- WMN:
-
Wireless Mesh Network
- IDS:
-
Intrusion Detection System
- ML:
-
Machine Learning
- DL:
-
Deep Learning
- MLDL:
-
Machine Learning and Deep Learning
- SWEVO:
-
Swarm and Evolutionary Algorithm
- NIST:
-
National Institute of Standards and Technology
- OWASP:
-
Open Web Application Security Project
- IoT:
-
Internet of Things
- BoT-IoT:
-
Botnet-Internet of Things
- ELM:
-
Extreme Learning Machine
References
Aburomman AA, Reaz MBI (2016) A novel SVM-kNN-PSO ensemble method for intrusion detection system. Appl Soft Comput 38:360–372
Aghdam MH, Kabiri P (2016) Feature selection for intrusion detection system using ant colony optimization. IJ Netw Secur 18(3):420–432
Agrawal S, Agrawal J (2015) Survey on anomaly detection using data mining techniques. Procedia Comput Sci 60:708–713
Ahmad AB Iftikhar and, Alghamdi AS (2009) Application of artificial neural network in detection of probing attacks. In: IEEE symposium on industrial electronics and applications, 2009. ISIEA 2009, vol 2. IEEE, pp 557–562
Ahmad I, Basheri M, Iqbal MJ, Rahim A (2018) Performance comparison of support vector machine, random forest, and extreme learning machine for intrusion detection. IEEE Access 6:33789–33795
Ahmed M, Mahmood AN, Hu J (2016) A survey of network anomaly detection techniques. J Netw Comput Appl 60:19–31
Ahmim A, Maglaras L, Ferrag MA, Derdour M, Janicke H (2019) A novel hierarchical intrusion detection system based on decision tree and rules-based models. In: 2019 15th international conference on distributed computing in sensor systems (DCOSS). IEEE, pp 228–233
Akinyelu AA, Adewumi AO (2014) Classification of phishing email using random forest machine learning technique. J Appl Math 2014:1–6
Al-Emadi S, Al-Mohannadi A, Al-Senaid F (2020) Using deep learning techniques for network intrusion detection. In: 2020 IEEE international conference on informatics, IoT, and enabling technologies (ICIoT). IEEE, pp 171–176
Al-Janabi STF, Saeed HA (2011) A neural network based anomaly intrusion detection system. In: Developments in E-systems engineering (DeSE), 2011. IEEE, pp 221–226
Alelyani S, Tang J, Liu H (2018) Feature selection for clustering: a review. In: Data clustering. Chapman and Hall/CRC, pp 29–60
Alhaj TA, Siraj MM, Zainal A, Elshoush HT, Elhaj F (2016) Feature selection using information gain for improved structural-based alert correlation. PLoS ONE 11(11):e0166017
Ali MH, Al Mohammed BAD, Ismail A, Zolkipli MF (2018a) A new intrusion detection system based on fast learning network and particle swarm optimization. IEEE Access 6:20255–20261
Ali MH, Fadlizolkipi M, Firdaus A, Khidzir NZ (2018b) A hybrid particle swarm optimization-extreme learning machine approach for intrusion detection system. In: 2018 IEEE student conference on research and development (SCOReD). IEEE, pp 1–4
Aljawarneh S, Aldwairi M, Yassein MB (2018) Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci 25:152–160
Ambikavathi C, Srivatsa SK et al (2020) Predictor selection and attack classification using random forest for intrusion detection. J Sci Ind Res (JSIR) 79(05):365–368
Ambusaidi MA, He X, Nanda P (2015) Unsupervised feature selection method for intrusion detection system. In: 2015 IEEE Trustcom/BigDataSE/ISPA, IEEE, vol 1, pp 295–301
Ambusaidi MA, He X, Nanda P, Tan Z (2016) Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Trans Comput 65(10):2986–2998
Amiri F, Yousefi MR, Lucas C, Shakery A, Yazdani N (2011) Mutual information-based feature selection for intrusion detection systems. J Netw Comput Appl 34(4):1184–1199
Ampah NK, Akujuobi CM, Sadiku MN, Alam S (2011) An intrusion detection technique based on continuous binary communication channels. Int J Secure Netw 6(2–3):174–180
Anwar S, Mohamad Zain J, Zolkipli MF, Inayat Z, Khan S, Anthony B, Chang V (2017) From intrusion detection to an intrusion response system: fundamentals, requirements, and future directions. Algorithms 10(2):39
Aslahi-Shahri B, Rahmani R, Chizari M, Maralani A, Eslami M, Golkar M, Ebrahimi A (2016) A hybrid method consisting of GA and SVM for intrusion detection system. Neural Comput Appl 27(6):1669–1676
Bajtoš T, Gajdoš A, Kleinová L, Lučivjanská K, Sokol P (2018) Network intrusion detection with threat agent profiling. Security and Communication Networks (2018)
Barbhuiya FA, Bansal G, Kumar N, Biswas S, Nandi S (2013) Detection of neighbor discovery protocol based attacks in ipv6 network. Netw Sci 2(3–4):91–113
Barrett M (2018) Framework for improving critical infrastructure cybersecurity. Technical Report, National Institute of Standards and Technology, Gaithersburg, MD, USA
Basnet R, Mukkamala S, Sung AH (2008) Detection of phishing attacks: a machine learning approach. In: Soft computing applications in industry. Springer, pp 373–383
Bennasar M, Hicks Y, Setchi R (2015) Feature selection using joint mutual information maximisation. Expert Syst Appl 42(22):8520–8532
Bhati BS, Rai C (2020) Analysis of support vector machine-based intrusion detection techniques. Arab J Sci Eng 45(4):2371–2383
Bhuyan MH, Bhattacharyya DK, Kalita JK (2014) Network anomaly detection: methods, systems and tools. IEEE Commun Surv Tutor 16(1):303–336
Blum A, Wardman B, Solorio T, Warner G (2010) Lexical feature based phishing url detection using online learning. In: Proceedings of the 3rd ACM workshop on artificial intelligence and security. ACM, pp 54–60
Bollinger J, Enright B, Valites M (2015) Crafting the InfoSec playbook: security monitoring and incident response master plan. O’Reilly Media Inc, Newton
Bostani H, Sheikhan M (2017) Modification of supervised OPF-based intrusion detection systems using unsupervised learning and social network concept. Pattern Recogn 62:56–72
Brown C, Cowperthwaite A, Hijazi A, Somayaji A (2009) Analysis of the 1999 Darpa/Lincoln laboratory IDs evaluation data with netadhict. In: IEEE symposium on computational intelligence for security and defense applications (2009), CISDA 2009. IEEE, pp 1–7
Buczak AL, Guven E (2016) A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun Surv Tutor 18(2):1153–1176
Bujlow T, Riaz T, Pedersen JM (2012) A method for classification of network traffic based on C5. 0 Machine Learning Algorithm. In: 2012 international conference on computing, networking and communications (ICNC). IEEE, pp 237–241
Callado A, Kamienski C, Szabó G, Gero BP, Kelner J, Fernandes S, Sadok D (2009) A survey on internet traffic identification. IEEE Commun Surv Tutor 11(3):37–52
Canzanese R, Mancoridis S, Kam M, (2015) System call-based detection of malicious processes. In: IEEE international conference on software quality, reliability and security. IEEE, pp 119–124
Carneiro G (2010) NS-3: Network simulator 3. In: UTM Lab Meeting April, vol 20, pp 4–5
Carrasquilla U (2010) Benchmarking algorithms for detecting anomalies in large datasets. MeasureIT, Nov pp 1–16
Casey E (2011) Digital evidence and computer crime: forensic science, computers, and the internet. Academic Press, London
Chae Hs, Jo Bo, Choi SH, Park Tk (2013) Feature selection for intrusion detection using NSL-KDD. In: Recent advances in computer science, pp 184–187
Chakraborty A, Bhattacharjee S, Marsden JR, Shankar R, Katz ES, Vallee WL Jr (2018) Predictive models to measure the impact of fiber-optic broadband speeds on local towns and communities. Telematics Inform 35(5):1408–1420
Chandala V, Banerjee A, Kumar V (2009) Anomaly detection: a survey. University of Minnesota, ACM Computing Surveys
Chandra A, Khatri SK, Simon R (2019) Filter-based attribute selection approach for intrusion detection using k-means clustering and sequential minimal optimization technique. In: 2019 Amity international conference on artificial intelligence (AICAI). IEEE, pp 740–745
Chaudhari K, Thakkar A (2019a) A comprehensive survey on travel recommender systems. Arch Comput Methods Eng 27:1–27
Chaudhari K, Thakkar A (2019b) Survey on handwriting-based personality trait identification. Expert Syst Appl 124:282–308
Chaudhari K, Thakkar A (2019c) Travelling salesman problem: an empirical comparison between ACO, PSO, ABC, FA and GA. In: Emerging research in computing, information, communication and applications. Springer, pp 397–405
Chebrolu S, Abraham A, Thomas JP (2005) Feature deduction and ensemble design of intrusion detection systems. Comput Secur 24(4):295–307
Chen L, Yan Z, Zhang W, Kantola R (2015) Trusms: a trustworthy SMS spam control system based on trust management. Fut Gener Comput Syst 49:77–93
Chen J, Qi X, Chen L, Chen F, Cheng G (2020) Quantum-inspired ant lion optimized hybrid k-means for cluster analysis and intrusion detection. Knowl Based Syst 203:106167
Chitrakar R, Huang C (2012) Anomaly based intrusion detection using hybrid learning approach of combining k-medoids clustering and naive bayes classification. In: 2012 8th international conference on wireless communications, networking and mobile computing (WiCOM). IEEE, pp 1–5
Choi SS, Cha SH, Tappert CC (2010) A survey of binary similarity and distance measures. J Syst Cybern Inform 8(1):43–48
Chou TS, Yen KK, Luo J (2008) Network intrusion detection design using feature selection of soft computing paradigms. Int J Comput Intell 4(3):196–208
Creech G, Hu J (2013) Generation of a new IDS test dataset: time to retire the KDD collection. In: Wireless communications and networking conference (WCNC). IEEE, pp 4487–4492
Daş R, Karabade A, Tuna G (2015) Common network attack types and defense mechanisms. In: 2015 23nd signal processing and communications applications conference (SIU). IEEE, pp 2658–2661
Dasgupta D (2012) Artificial immune systems and their applications. Springer, Berlin
Dash M, Koot PW (2009) Feature selection for clustering. In: Encyclopedia of database systems. Springer, pp 1119–1125
Dembczynski K, Jachnik A, Kotlowski W, Waegeman W, Hüllermeier E (2013) Optimizing the f-measure in multi-label classification: plug-in rule approach versus structured loss minimization. In: International conference on machine learning, pp 1130–1138
Deshpande P, Sharma SC, Peddoju SK, Junaid S (2018) HIDS: a host based intrusion detection system for cloud computing environment. Int J Syst Assur Eng Manag 9(3):567–576
Devaraju S, Ramakrishnan S (2014) Performance comparison for intrusion detection system using neural network with KDD dataset. ICTACT J Soft Comput 4(3):106167
Dewa Z, Maglaras LA (2016) Data mining and intrusion detection systems. Int J Adv Comput Sci Appl 7(1):62–71
Doak J (1992) CSE-92-18-an evaluation of feature selection methods and their application to computer security
Duarte V, Farruca N (2010) Using libpcap for monitoring distributed applications. In: 2010 international conference on high performance computing and simulation. IEEE, pp 92–97
Duch W, Winiarski T, Biesiada J, Kachel A (2003) Feature selection and ranking filters. In: International conference on artificial neural networks (ICANN) and international conference on neural information processing (ICONIP), Citeseer, vol 251, p 254
Dutta V, Choraś M, Pawlicki M, Kozik R (2020) Hybrid model for improving the classification effectiveness of network intrusion detection. In: Proceedings of the 13th international conference on computational intelligence in security for information systems (CISIS 2020), Burgos, Spain, pp 18–20
Dy JG, Brodley CE (2000) Feature subset selection and order identification for unsupervised learning. In: ICML, Citeseer, pp 247–254
Eesa AS, Orman Z, Brifcani AMA (2015) A novel feature-selection approach based on the cuttlefish optimization algorithm for intrusion detection systems. Expert Syst Appl 42(5):2670–2679
Elhag S, Fernández A, Alshomrani S, Herrera F (2019) Evolutionary fuzzy systems: a case study for intrusion detection systems. In: Evolutionary and swarm intelligence algorithms. Springer, pp 169–190
Elmasry W, Akbulut A, Zaim AH (2020) Evolving deep learning architectures for network intrusion detection using a double pso metaheuristic. Comput Netw 168:107042
Elsherif A et al. (2018) Automatic intrusion detection system using deep recurrent neural network paradigm. J Inf Secur Cybercrimes Res 1(1):21–31
Emary E, Zawbaa HM, Ghany KKA, Hassanien AE, Parv B (2015) Firefly optimization algorithm for feature selection. In: Proceedings of the 7th Balkan conference on informatics conference. ACM, p 26
Enache AC, Sgârciu V (2015) An improved bat algorithm driven by support vector machines for intrusion detection. In: International joint conference. Springer, pp 41–51
Farid DM, Harbi N, Rahman MZ (2010) Combining naive bayes and decision tree for adaptive intrusion detection. arXiv preprint arXiv:10054496
Farnaaz N, Jabbar M (2016) Random forest modeling for network intrusion detection system. Procedia Comput Sci 89:213–217
Fausett LV et al (1994) Fundamentals of neural networks: architectures, algorithms, and applications, vol 3. Prentice-Hall, Englewood Cliffs
Fleuret F (2004) Fast binary feature selection with conditional mutual information. J Mach Learn Res 5(Nov):1531–1555
Fowlkes EB, Mallows CL (1983) A method for comparing two hierarchical clusterings. J Am Stat Assoc 78(383):553–569
Fries TP (2008) A fuzzy-genetic approach to network intrusion detection. In: Proceedings of the 10th annual conference companion on Genetic and evolutionary computation. ACM, pp 2141–2146
Gamal M, Abbas H, Sadek R (2020) Hybrid approach for improving intrusion detection based on deep learning and machine learning techniques. In: Joint European-US workshop on applications of invariance in computer vision. Springer, pp 225–236
Ganapathy S, Kulothungan K, Muthurajkumar S, Vijayalakshmi M, Yogesh P, Kannan A (2013) Intelligent feature selection and classification techniques for intrusion detection in networks: a survey. EURASIP J Wirel Commun Netw 1:271
Gao HH, Yang HH, Wang XY (2005) Ant colony optimization based network intrusion feature selection and detection. In: Proceedings of 2005 international conference on machine learning and cybernetics, vol 6, 2005. IEEE, pp 3871–3875
Gharib A, Sharafaldin I, Lashkari AH, Ghorbani AA (2016) An evaluation framework for intrusion detection dataset. In: 2016 international conference on information science and security (ICISS). IEEE, pp 1–6
Ghosh J, Kumar D, Tripathi R (2020) Features extraction for network intrusion detection using genetic algorithm (GA). In: Modern approaches in machine learning and cognitive science: a walkthrough. Springer, pp 13–25
Goeschel K (2016) Reducing false positives in intrusion detection systems using data-mining techniques utilizing support vector machines, decision trees, and naive Bayes for off-line analysis. In: SoutheastCon 2016. IEEE, pp 1–6
Grzonka D, Jakobik A, Kołodziej J, Pllana S (2018) Using a multi-agent system and artificial intelligence for monitoring and improving the cloud performance and security. Future Gener Comput Syst 86:1106–1117
Gupta B, Agrawal DP, Yamaguchi S (2016a) Handbook of research on modern cryptographic solutions for computer and cyber security. IGI Global, Hershey
Gupta S, Chaudhari BS, Chakrabarty B (2016b) Vulnerable network analysis using war driving and security intelligence. In: 2016 international conference on inventive computation technologies (ICICT), vol 3. IEEE, pp 1–5
Gurung S, Ghose MK, Subedi A (2019) Deep learning approach on network intrusion detection system using NSL-KDD dataset. Int J Comput Netw Inf Secur (IJCNIS) 11(3):8–14
Halkidi M, Batistakis Y, Vazirgiannis M (2001) On clustering validation techniques. J Intell Inf Syst 17(2–3):107–145
Hamamoto AH, Carvalho LF, Sampaio LDH, Abrão T, Proença ML Jr (2018) Network anomaly detection system using genetic algorithm and fuzzy logic. Expert Syst Appl 92:390–402
Hamed T, Ernst JB, Kremer SC (2018) A survey and taxonomy of classifiers of intrusion detection systems. In: Computer and network security essentials. Springer, pp 21–39
Harish B, Kumar SA (2017) Anomaly based intrusion detection using modified fuzzy clustering. IJIMAI 4(6):54–59
Hassan MM, Gumaei A, Alsanad A, Alrubaian M, Fortino G (2020) A hybrid deep learning model for efficient intrusion detection in big data environment. Inf Sci 513:386–396
Heck RH, Thomas S, Tabata L (2013) Multilevel modeling of categorical outcomes using IBM SPSS. Routledge, London
Henriques J, Caldeira F, Cruz T, Simões P (2020) Combining k-means and xgboost models for anomaly detection using log datasets. Electronics 9(7):1164
Hindy H, Atkinson R, Tachtatzis C, Colin JN, Bayne E, Bellekens X (2020) Towards an effective zero-day attack detection using outlier-based deep learning techniques. arXiv preprint arXiv:200615344
Hodge V, Austin J (2004) A survey of outlier detection methodologies. Artif Intell Rev 22(2):85–126
Hodo E, Bellekens X, Hamilton A, Tachtatzis C, Atkinson R (2017) Shallow and deep networks intrusion detection system: a taxonomy and survey. arXiv preprint arXiv:170102145
Hoque MS, Mukit M, Bikas M, Naser A et al. (2012) An implementation of intrusion detection system using genetic algorithm. arXiv preprint arXiv:12041336
Hosseini S, Zade BMH (2020) New hybrid method for attack detection using combination of evolutionary algorithms, SVM, and ANN. Comput Netw 173:107168
Hu W, Hu W, Maybank S (2008) Adaboost-based algorithm for network intrusion detection. IEEE Trans Syst Man Cybern Part B Cybern 38(2):577–583
Igbe O, Darwish I, Saadawi T (2016) Distributed network intrusion detection systems: an artificial immune system approach. In: 2016 IEEE first international conference on connected health: applications, systems and engineering technologies (CHASE). IEEE, pp 101–106
Ikram ST, Cherukuri AK (2016) Improving accuracy of intrusion detection model using PCA and optimized SVM. J Comput Inf Technol 24(2):133–148
Imamverdiyev Y, Abdullayeva F (2018) Deep learning method for denial of service attack detection based on restricted Boltzmann machine. Big Data 6(2):159–169
Inayat Z, Gani A, Anuar NB, Khan MK, Anwar S (2016) Intrusion response systems: foundations, design, and challenges. J Netw Comput Appl 62:53–74
Index CVN (2017) Global mobile data traffic forecast update, 2016–2021 white paper. Cisco, San Jose
Islam R, Abawajy J (2013) A multi-tier phishing detection and filtering approach. J Netw Comput Appl 36(1):324–335
Javaid A, Niyaz Q, Sun W, Alam M (2016) A deep learning approach for network intrusion detection system. In: Proceedings of the 9th EAI international conference on bio-inspired information and communications technologies (formerly BIONETICS), ICST (Institute for Computer Sciences, and Social-Informatics), pp 21–26
John GH, Kohavi R, Pfleger K (1994) Irrelevant features and the subset selection problem. In: Machine learning proceedings. Elsevier, pp 121–129
Jović A, Brkić K, Bogunović N (2015) A review of feature selection methods with applications. In: 2015 38th international convention on information and communication technology, electronics and microelectronics (MIPRO). IEEE, pp 1200–1205
Kabir E, Hu J, Wang H, Zhuo G (2018) A novel statistical technique for intrusion detection systems. Future Gener Comput Syst 79:303–318
Kabir MM, Shahjahan M, Murase K (2012) A new hybrid ant colony optimization algorithm for feature selection. Expert Syst Appl 39(3):3747–3763
Kabir MR, Onik AR, Samad T (2017) A network intrusion detection framework based on Bayesian network using wrapper approach. Int J Comput Appl 166(4):13–17
Kalita DJ, Singh VP, Kumar V (2020) SVM hyper-parameters optimization using multi-PSO for intrusion detection. In: Social networking and computational intelligence. Springer, pp 227–241
Kamisiński A, Fung C (2015) Flowmon: detecting malicious switches in software-defined networks. In: Proceedings of the 2015 workshop on automated decision making for active cyber defense. ACM, pp 39–45
Kannan A, Maguire GQ, Sharma A, Schoo P (2012) Genetic algorithm based feature selection algorithm for effective intrusion detection in cloud networks. In: 2012 IEEE 12th international conference on data mining workshops (ICDMW). IEEE, pp 416–423
Kelleher JD, Mac Namee B, D’arcy A, (2015) Fundamentals of machine learning for predictive data analytics: algorithms, worked examples, and case studies. MIT Press, Cambridge
Khammassi C, Krichen S (2017) A GA-LR wrapper approach for feature selection in network intrusion detection. Comput Secur 70:255–277
Khan S, Gani A, Wahab AWA, Singh PK (2018) Feature selection of denial-of-service attacks using entropy and granular computing. Ara J Sci Eng 43(2):499–508
Khraisat A, Gondal I, Vamplew P, Kamruzzaman J, Alazab A (2020) Hybrid intrusion detection system based on the stacking ensemble of c5 decision tree classifier and one class support vector machine. Electronics 9(1):173
Kim J, Kim H (2015) Applying recurrent neural network to intrusion detection with hessian free optimization. In: International workshop on information security applications. Springer, pp 357–369
Kim TY, Cho SB (2018) Web traffic anomaly detection using C-LSTM neural networks. Expert Syst Appl 106:66–76
Knight W (2018) MIT technology review. Serious quantum computers are finally here What are we going to do with them
Kolari P, Java A, Finin T, Oates T, Joshi A, et al. (2006) Detecting spam blogs: a machine learning approach. In: Proceedings of the national conference on artificial intelligence, vol 21. MIT Press, Cambridge, p 1351
Kondaiah R, Sathyanarayana B (2018) Trust based genetic neuro-fuzzy system for intrusion detection and self adaptive firefly integrated particle swarm optimization algorithm for secure routing in manet. Int J Appl Eng Res 13(8):5722–5735
Krishnaveni S, Vigneshwar P, Kishore S, Jothi B, Sivamohan S (2020) Anomaly-based intrusion detection system using support vector machine. In: Artificial intelligence and evolutionary computations in engineering systems. Springer, pp 723–731
Kuang F, Xu W, Zhang S (2014) A novel hybrid KPCA and SVM with GA model for intrusion detection. Appl Soft Comput 18:178–184
Kumar G (2020) An improved ensemble approach for effective intrusion detection. J Supercomput 76(1):275–291
Kumar K, Batth JS (2016) Network intrusion detection with feature selection techniques using machine-learning algorithms. Int J Comput Appl 150(12):1–13
Kumar GR, Mangathayaru N, Narasimha G (2015) An improved k-means clustering algorithm for intrusion detection using Gaussian function. In: Proceedings of the the international conference on engineering & MIS 2015. ACM, p 69
Landress AD (2016) A hybrid approach to reducing the false positive rate in unsupervised machine learning intrusion detection. In: SoutheastCon 2016. IEEE, pp 1–6
Lashkari AH, Draper-Gil G, Mamun MSI, Ghorbani AA (2017) Characterization of tor traffic using time based features. In: ICISSP, pp 253–262
Lever J, Krzywinski M, Altman N (2016) Points of significance: model selection and overfitting
Li Y, Wang JL, Tian ZH, Lu TB, Young C (2009) Building lightweight intrusion detection system using wrapper-based feature selection mechanisms. Comput Secur 28(6):466–475
Li J, Liu Y, Gu L (2010) DDoS attack detection based on neural network. In: 2010 2nd international symposium on aware computing (ISAC). IEEE, pp 196–199
Li WS, Bai XM, Duan LZ, Zhang X (2011) Intrusion Detection based on ant colony algorithm of Fuzzy clustering. In: 2011 international conference on computer science and network technology (ICCSNT), vol 3. IEEE, pp 1642–1645
Li L, Zhang H, Peng H, Yang Y (2018) Nearest neighbors based density peaks approach to intrusion detection. Chaos Solitons Fractals 110:33–40
Li W, Tug S, Meng W, Wang Y (2019) Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener Comput Syst 96:481–489
Lin SW, Ying KC, Lee CY, Lee ZJ (2012) An intelligent algorithm with feature selection and decision rules applied to anomaly intrusion detection. Appl Soft Comput 12(10):3285–3290
Lin WC, Ke SW, Tsai CF (2015) CANN: an intrusion detection system based on combining cluster centers and nearest neighbors. Knowl-Based Syst 78:13–21
Liu H, Motoda H (2012) Feature selection for knowledge discovery and data mining, vol 454. Springer, Berlin
Liu Y, Liang S, Fang W, Zhou Z, Hu R, Zhou H, Hou J, Wang Y (2020) A hybrid feature selection algorithm combining information gain and genetic search for intrusion detection. J. Phys. Conf. Ser. 1601:032048
Lohiya R, Thakkar A (2020) Application domains, evaluation datasets, and research challenges of IoT: a systematic review. IEEE Internet Things J
Lohiya R, Thakkar A (In press) Intrusion detection using deep neural network with antirectifier layer. In: International conference on applied soft computing and communication networks (ACN’20), ISBN 978-981-33-6173-7\_7
Lv L, Wang W, Zhang Z, Liu X (2020) A novel intrusion detection system based on an optimal hybrid kernel extreme learning machine. Knowl Based Syst 105648
Mabu S, Chen C, Lu N, Shimada K, Hirasawa K (2011) An intrusion-detection model based on fuzzy class-association-rule mining using genetic network programming. IEEE Trans Syst Man Cybern Part C Appl Rev 41(1):130–139
Mandal N, Jadhav S (2016) A survey on network security tools for open source. In: 2016 IEEE international conference on current trends in advanced computing (ICCTAC). IEEE, pp 1–6
McHugh J (2000) Testing intrusion detection systems: a critique of the 1998 and 1999 Darpa intrusion detection system evaluations as performed by Lincoln laboratory. ACM Trans Inf Syst Secur (TISSEC) 3(4):262–294
McHugh ML (2012) Interrater reliability: the kappa statistic. Biochemia medica: Biochemia medica 22(3):276–282
Meftah S, Rachidi T, Assem N (2019) Network based intrusion detection using the UNSW-NB15 dataset. Int J Comput Digit Syst 8(5):478–487
Mehra P (2012) A brief study and comparison of snort and bro open source network intrusion detection systems. Int J Adv Res Comput Commun Eng 1(6):383–386
Migliavacca M, Papagiannis I, Eyers DM, Shand B, Bacon J, Pietzuch P (2010) DEFCON: high-performance event processing with information security. In: Proceedings of the 2010 USENIX conference on USENIX annual technical conference, USENIX Association, pp 1–1
Mitra P, Murthy C, Pal SK (2002) Unsupervised feature selection using feature similarity. IEEE Trans Pattern Anal Mach Intell 24(3):301–312
Moustafa N, Slay J (2015) UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In: 2015 military communications and information systems conference (MilCIS), IEEE, pp 1–6
Muda Z, Yassin W, Sulaiman M, Udzir N (2016) K-means clustering and Naive Bayes classification for intrusion detection. J IT Asia 4(1):13–25
Mukherjee S, Sharma N (2012) Intrusion detection using Naive Bayes classifier with feature reduction. Procedia Technol 4:119–128
Mungra D, Agrawal A, Thakkar A (2020) A voting-based sentiment classification model. In: Intelligent communication, control and devices. Springer, pp 551–558
Muniyandi AP, Rajeswari R, Rajaram R (2012) Network anomaly detection by cascading k-Means clustering and C4. 5 decision tree algorithm. Procedia Eng 30:174–182
Napiah MN, Idris MYIB, Ramli R, Ahmedy I (2018) Compression header analyzer intrusion detection system (CHA-IDS) for 6LoWPAN communication protocol. IEEE Access 6:16623–16638
Naseer S, Saleem Y, Khalid S, Bashir MK, Han J, Iqbal MM, Han K (2018) Enhanced network anomaly detection based on deep neural networks. IEEE Access 6:48231–48246
Nechaev B, Allman M, Paxson V, Gurtov A (2004) Lawrence Berkeley National Laboratory (LBNL)/ICSI enterprise tracing project. LBNL/ICSI, Berkeley
Nehinbe JO (2009) A simple method for improving intrusion detections in corporate networks. In: International conference on information security and digital forensics. Springer, pp 111–122
Nehinbe JO (2011) A critical evaluation of datasets for investigating IDSs and IPSs researches. In: 2011 IEEE 10th international conference on cybernetic intelligent systems (CIS). IEEE, pp 92–97
Nguyen TT, Armitage G (2008) A survey of techniques for internet traffic classification using machine learning. IEEE Commun Surv Tutor 10(4):56–76
Ni X, He D, Chan S, Ahmad F (2016) Network anomaly detection using unsupervised feature selection and density peak clustering. In: International conference on applied cryptography and network security. Springer, pp 212–227
Nigam K, McCallum AK, Thrun S, Mitchell T (2000) Text classification from labeled and unlabeled documents using EM. Mach Learn 39(2–3):103–134
Nisioti A, Mylonas A, Yoo PD, Katos V (2018) From intrusion detection to attacker attribution: a comprehensive survey of unsupervised methods. IEEE Commun Surv Tutor 20(4):3369–3388
Niu Z, Shi S, Sun J, He X (2011) A survey of outlier detection methodologies and their applications. In: International conference on artificial intelligence and computational intelligence. Springer, pp 380–387
Norouzian MR, Merati S (2011) Classifying attacks in a network intrusion detection system based on artificial neural networks. In: 2011 13th international conference on advanced communication technology (ICACT). IEEE, pp 868–873
Novaković J (2016) Toward optimal feature selection using ranking methods and classification algorithms. Yugoslav J Oper Res 21(1):119–135
Obermeyer Z, Emanuel EJ (2016) Predicting the future-big data, machine learning, and clinical medicine. New Engl J Med 375(13):1216
OpenDNS L (2016) PhishTank: an anti-phishing site. https://www.phishtank.com
Osanaiye O, Cai H, Choo KKR, Dehghantanha A, Xu Z, Dlodlo M (2016) Ensemble-based multi-filter feature selection method for DDoS detection in cloud computing. EURASIP J Wirel Commun Netw 1:130
Panda M, Abraham A, Patra MR (2010) Discriminative multinomial Naive Bayes for network intrusion detection. In: 2010 sixth international conference on information assurance and security (IAS). IEEE, pp 5–10
Pandya R, Pandya J (2015) C5.0 algorithm to improved decision tree with feature selection and reduced error pruning. Int J Comput Appl 117(16):18–21
Pareek P, Thakkar A (2021) A survey on video-based human action recognition: recent updates, datasets, challenges, and applications. Artif Intell Rev 54(3):2259–2322
Patel C, Patel R, Thakkar A (2012a) Object detection and segmentation using local and global property. Int J Comput Sci Res Appl 2(02):02–10
Patel R, Patel CI, Thakkar A (2012b) Aggregate features approach for texture analysis. In: 2012 Nirma University international conference on engineering (NUiCONE). IEEE, pp 1–5
Patgiri R, Varshney U, Akutota T, Kunde R (2018) An investigation on intrusion detection system using machine learning. In: 2018 IEEE symposium series on computational intelligence (SSCI). IEEE, pp 1684–1691
Peddabachigari S, Abraham A, Grosan C, Thomas J (2007) Modeling intrusion detection system using hybrid intelligent systems. J Netw Comput Appl 30(1):114–132
Peng H, Long F, Ding C (2005) Feature selection based on mutual information criteria of max-dependency, max-relevance, and min-redundancy. IEEE Trans Pattern Anal Mach Intell 27(8):1226–1238
Peng J, Choo KKR, Ashman H (2016) User profiling in intrusion detection: a review. J Netw Comput Appl 72:14–27
Potluri S, Henry NF, Diedrich C (2017) Evaluation of hybrid deep learning techniques for ensuring security in networked control systems. In: 2017 22nd IEEE international conference on emerging technologies and factory automation (ETFA). IEEE, pp 1–8
Prusty S, Levine BN, Liberatore M (2011) Forensic investigation of the OneSwarm anonymous filesharing system. In: Proceedings of the 18th ACM conference on Computer and communications security. ACM, pp 201–214
Rais HM, Mehmood T (2018) Dynamic ant colony system with three level update feature selection for intrusion detection. IJ Netw Secur 20(1):184–192
Rajagopal S, Kundapur PP, Hareesha KS (2020) A stacking ensemble for network intrusion detection using heterogeneous datasets. Secur Commun Netw 2020:1–9
Rajput D, Thakkar A (2019) A survey on different network intrusion detection systems and countermeasure. In: Emerging research in computing, information, communication and applications. Springer, pp 497–506
Raman MG, Somu N, Kirthivasan K, Liscano R, Sriram VS (2017) An efficient intrusion detection system based on hypergraph-genetic algorithm for parameter optimization and feature selection in support vector machine. Knowl-Based Syst 134:1–12
Ranshous S, Shen S, Koutra D, Harenberg S, Faloutsos C, Samatova NF (2015) Anomaly detection in dynamic networks: a survey. Wiley Interdiscip Rev Comput Stat 7(3):223–247
Riquelme N, Von Lücken C, Baran B (2015) Performance metrics in multi-objective optimization. In: 2015 Latin American computing conference (CLEI). IEEE, pp 1–11
Rousseeuw PJ (1987) Silhouettes: a graphical aid to the interpretation and validation of cluster analysis. J Comput Appl Math 20:53–65
Sabahi F, Movaghar A (2008) Intrusion detection: a survey. In: 3rd International Conference on Systems and Networks Communications, 2008. ICSNC’08. IEEE, pp 23–26
Saeys Y, Inza I, Larrañaga P (2007) A review of feature selection techniques in bioinformatics. Bioinformatics 23(19):2507–2517
Sahu S, Mehtre BM (2015) Network intrusion detection system using J48 Decision Tree. In: 2015 international conference on advances in computing, communications and informatics (ICACCI). IEEE, pp 2023–2026
Sánchez-Maroño N, Alonso-Betanzos A, Tombilla-Sanromán M (2007) Filter methods for feature selection–a comparative study. In: International conference on intelligent data engineering and automated learning. Springer, pp 178–187
Sangkatsanee P, Wattanapongsakorn N, Charnsripinyo C (2011) Practical real-time intrusion detection using machine learning approaches. Comput Commun 34(18):2227–2235
Sangster B, O’Connor T, Cook T, Fanelli R, Dean E, Morrell C, Conti GJ (2009) Toward instrumenting network warfare competitions to generate labeled datasets. In: CSET
Sarvari S, Sani NFM, Hanapi ZM, Abdullah MT (2020) An efficient anomaly intrusion detection method with feature selection and evolutionary neural network. IEEE Access 8:70651–70663
Sato M, Yamaki H, Takakura H (2012) Unknown attacks detection using feature extraction from anomaly-based ids alerts. In: 2012 IEEE/IPSJ 12th international symposium on applications and the internet (SAINT). IEEE, pp 273–277
Schneier B, Kelsey J (1999) Secure audit logs to support computer forensics. ACM Trans Inf Syst Secur (TISSEC) 2(2):159–176
Shah SAR, Issac B (2018) Performance comparison of intrusion detection systems and application of machine learning to snort system. Future Gener Comput Syst 80:157–170
Sharafaldin I, Lashkari AH, Ghorbani AA (2018) Toward generating a new intrusion detection dataset and intrusion traffic characterization. In: ICISSP, pp 108–116
Sharbaf M (2018) Artificial intelligence and cybersecurity. Bus Strategy Artif Intell Econ 5
Sharma R, Rajvaidya H, Pareek P, Thakkar A (2019) A comparative study of machine learning techniques for emotion recognition. In: Emerging research in computing, information, communication and applications. Springer, pp 459–464
Sheen S, Rajesh R (2008) Network intrusion detection using feature selection and Decision tree classifier. In: TENCON 2008—2008 IEEE Region 10 conference. IEEE, pp 1–4
Sheikhan M, Jadidi Z, Farrokhi A (2012) Intrusion detection using reduced-size RNN based on feature grouping. Neural Comput Appl 21(6):1185–1190
Sheth N, Yong L, Callon R, Black D (2015) Juniper networks
Shiravi A, Shiravi H, Tavallaee M, Ghorbani AA (2012) Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput Secur 31(3):357–374
Shirazi HM (2009) Anomaly intrusion detection system using information theory, K-NN and KMC algorithms. Aust J Basic Appl Sci 3(3):2581–2597
Snapp SR, Brentano J, Dias G, Goan TL, Heberlein LT, Ho CL, Levitt KN (2017) DIDS (distributed intrusion detection system)-motivation, architecture, and an early prototype
Soheily-Khah S, Marteau PF, Béchet N (2018) Intrusion detection in network systems through hybrid supervised and unsupervised machine learning process: a case study on the ISCX dataset. In: 2018 1st international conference on data intelligence and security (ICDIS). IEEE, pp 219–226
Sommer P (1999) Intrusion detection systems as evidence. Comput Netw 31(23–24):2477–2487
Song J, Alves-Foss J (2016) The DARPA cyber grand challenge: a competitor’s perspective, part 2. IEEE Secur Priv 14(1):76–81
Song J, Takakura H, Okabe Y, Eto M, Inoue D, Nakao K (2011) Statistical analysis of honeypot data and building of Kyoto 2006+ dataset for NIDS evaluation. In: Proceedings of the first workshop on building analysis datasets and gathering experience returns for security. ACM, pp 29–36
Song Q, Ni J, Wang G (2013) A fast clustering-based feature subset selection algorithm for high-dimensional data. IEEE Trans Knowl Data Eng 25(1):1–14
Sperotto A, Sadre R, Van Vliet F, Pras A (2009) A labeled data set for flow-based intrusion detection. In: International workshop on IP operations and management. Springer, pp 39–50
Sperotto A, Schaffrath G, Sadre R, Morariu C, Pras A, Stiller B (2010) An overview of IP flow-based intrusion detection. IEEE Commun Surv Tutor 12(3):343–356
Søhoel H, Jaatun MG, Boyd C (2018) OWASP Top 10-Do Startups Care? In: 2018 international conference on cyber security and protection of digital services (Cyber Security). IEEE, pp 1–8
Srinivas J, Das AK, Kumar N (2019) Government regulations in cyber security: framework, standards and recommendations. Future Gener Comput Syst 92:178–188
Su MY (2011) Using clustering to improve the KNN-based classifiers for online anomaly network traffic identification. J Netw Comput Appl 34(2):722–730
Subba B, Biswas S, Karmakar S (2016) Enhancing performance of anomaly based intrusion detection systems through dimensionality reduction using principal component analysis. In: 2016 IEEE international conference on advanced networks and telecommunications systems (ANTS). IEEE, pp 1–6
Sung AH, Mukkamala S (2004) The feature selection and intrusion detection problems. In: Annual Asian computing science conference. Springer, pp 468–482
Suresh M, Anitha R (2011) Evaluating machine learning algorithms for detecting DDoS attacks. In: International conference on network security and applications. Springer, pp 441–452
Susilo B, Sari RF (2020) Intrusion detection in IoT networks using deep learning algorithm. Information 11(5):279
Talavera L (2005) An evaluation of filter and wrapper methods for feature selection in categorical clustering. In: International symposium on intelligent data analysis. Springer, pp 440–451
Tama BA, Rhee KH (2015) A combination of PSO-based feature selection and tree-based classifiers ensemble for intrusion detection systems. In: Advances in computer science and ubiquitous computing. Springer, pp 489–495
Tang P, Jiang Ra, Zhao M (2010) Feature selection and design of intrusion detection system based on k-means and triangle area support vector machine. In: Second international conference on future networks, 2010. ICFN’10. IEEE, pp 144–148
Tang TA, Mhamdi L, McLernon D, Zaidi SAR, Ghogho M (2018) Deep recurrent neural network for intrusion detection in SDN-based networks. In: 2018 4th IEEE conference on network softwarization and workshops (NetSoft). IEEE, pp 202–206
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In: IEEE symposium on computational intelligence for security and defense applications (2009), CISDA 2009. IEEE, pp 1–6
Thakkar A, Chaudhari K (2020a) A comprehensive survey on portfolio optimization, stock price and trend prediction using particle swarm optimization. Arch Comput Methods Eng 28(4):2133-–2164
Thakkar A, Chaudhari K (2020b) Crest: cross-reference to exchange-based stock trend prediction using long short-term memory. Procedia Comput Sci 167:616–625
Thakkar A, Chaudhari K (2020c) Predicting stock trend using an integrated term frequency-inverse document frequency-based feature weight matrix with neural networks. Appl Soft Comput. https://doi.org/10.1016/j.asoc.2020.106684
Thakkar A, Chaudhari K (2021) Fusion in stock market prediction: a decade survey on the necessity, recent developments, and potential future directions. Inf Fusion 65:95–107
Thakkar A, Kotecha K (2011) Bio-inspired based optimized algorithm for cluster head election using RSSI and LQI. Int J Comput Sci 1(02):19–29
Thakkar A, Lohiya R (2020a) A review of the advancement in intrusion detection datasets. Procedia Comput Sci 167:636–645
Thakkar A, Lohiya R (2020b) Role of swarm and evolutionary algorithms for intrusion detection system: a survey. In: Swarm and evolutionary computation, p 100631
Thakkar A, Lohiya R (2021a) Attack classification using feature selection techniques: a comparative study. J. Ambient Intell Human Comput 12(1):1249–1266
Thakkar A, Lohiya R (2021b) A review on machine learning and deep learning perspectives of ids for IoT: recent updates, security issues, and challenges. Arch Comput Methods Eng 28(4):3211–3243
Thakkar A, Jivani N, Padasumbiya J, Patel CI (2013) A new hybrid method for face recognition. In: 2013 Nirma University international conference on engineering (NUiCONE). IEEE, pp 1–9
Thakkar A, Mungra D, Agrawal A (2020) Sentiment analysis: an empirical comparison between various training algorithms for artificial neural network. Int J Innov Comput Appl 11(1):9–29
Thaseen IS, Kumar CA (2014) Intrusion detection model using fusion of PCA and optimized SVM. In: 2014 international conference on contemporary computing and informatics (IC3I). IEEE, pp 879–884
Thaseen IS, Kumar CA (2017) Intrusion detection model using fusion of chi-square feature selection and multi class SVM. J King Saud Univ Comput Inf Sci 29(4):462–472
Tian J, Gu H (2010) Anomaly detection combining one-class SVMs and particle swarm optimization algorithms. Nonlinear Dyn 61(1–2):303–310
Tsoumakas G, Katakis I, Vlahavas I (2010) Data mining and knowledge discovery handbook. Mining multi-label data
Udd R, Asplund M, Nadjm-Tehrani S, Kazemtabrizi M, Ekstedt M (2016) Exploiting bro for intrusion detection in a SCADA system. In: Proceedings of the 2nd ACM international workshop on cyber-physical system security. ACM, pp 44–51
Umer MF, Sher M, Bi Y (2017) Flow-based intrusion detection: techniques and challenges. Comput Secur 70:238–254
Vardhini KK, Sitamahalakshmi T (2017) Enhanced intrusion detection system using data reduction: an ant colony optimization approach. Int J Appl Eng Res 12(9):1844–1847
Vasilomanolakis E, Karuppayah S, Mühlhäuser M, Fischer M (2015) Taxonomy and survey of collaborative intrusion detection. ACM Comput Surv (CSUR) 47(4):55
Veeramachaneni K, Arnaldo I, Korrapati V, Bassias C, Li K (2016) AI 2: training a big data machine to defend. In: 2016 IEEE 2nd international conference on big data security on cloud (BigDataSecurity), IEEE international conference on high performance and smart computing (HPSC), and IEEE international conference on intelligent data and security (IDS). IEEE, pp 49–54
Verma P, Anwar S, Khan S, Mane SB (2018) Network intrusion detection using clustering and gradient boosting. 2018 9th international conference on computing, communication and networking technologies (ICCCNT). IEEE, pp 1–7
Vidal JM, Monge MAS, Monterrubio SMM (2020) Anomaly-based intrusion detection: adapting to present and forthcoming communication environments. In: Handbook of research on machine and deep learning applications for cyber security. IGI Global, pp 195–218
Vijayanand R, Devaraj D, Kannapiran B (2018) Intrusion detection system for wireless mesh network using multiple support vector machine classifiers with genetic-algorithm-based feature selection. Comput Secur 77:304–314
Vinh NX, Epps J, Bailey J (2010) Information theoretic measures for clusterings comparison: variants, properties, normalization and correction for chance. J Mach Learn Res 11(Oct):2837–2854
Wang AH (2010) Detecting spam bots in online social networking sites: a machine learning approach. In: IFIP annual conference on data and applications security and privacy. Springer, pp 335–342
Wang G, Hao J, Ma J, Huang L (2010) A new approach to intrusion detection using Artificial Neural Networks and fuzzy clustering. Expert Syst Appl 37(9):6225–6232
Wang H, Gu J, Wang S (2017) An effective intrusion detection framework based on SVM with feature augmentation. Knowl-Based Syst 136:130–139
Wang J, Hong X, Ren Rr, Li Th (2009) A real-time intrusion detection system based on PSO-SVM. In: Proceedings. The 2009 international workshop on information security and application (IWISA 2009), Citeseer, p 319
Wang SS, Yan KQ, Wang SC, Liu CW (2011) An integrated intrusion detection system for cluster-based wireless sensor networks. Expert Syst Appl 38(12):15234–15243
Wang W, Sheng Y, Wang J, Zeng X, Ye X, Huang Y, Zhu M (2018) HAST-IDS: learning hierarchical spatial-temporal features using deep neural networks to improve intrusion detection. IEEE Access 6:1792–1806
Wedde HF, Lehnhoff S, van Bonn B, Bay Z, Becker S, Böttcher S, Brunner C, Büscher A, Fürst T, Lazarescu AM, et al. (2007) Highly dynamic and adaptive traffic congestion avoidance in real-time inspired by honey bee behavior. In: Mobilität und Echtzeit, Springer, pp 21–31
Woland A, Santuka V, Harris M, Sanbower J (2018) Integrated security technologies and solutions-volume I: Cisco security solutions for advanced threat protection with next generation firewall, intrusion prevention, AMP, and content security. Cisco Press
Xie M, Hu J (2013) Evaluating host-based anomaly detection systems: a preliminary analysis of ADFA-LD. In: 2013 6th international congress on image and signal processing (CISP), vol 3. IEEE, pp 1711–1716
Xie M, Hu J, Slay J (2014) Evaluating host-based anomaly detection systems: application of the one-class SVM algorithm to ADFA-LD. In: 2014 11th international conference on fuzzy systems and knowledge discovery (FSKD). IEEE, pp 978–982
Xie Y, Feng D, Tan Z, Zhou J (2016) Unifying intrusion detection and forensic analysis via provenance awareness. Future Gener Comput Syst 61:26–36
Xin Y, Kong L, Liu Z, Chen Y, Li Y, Zhu H, Gao M, Hou H, Wang C (2018) Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 6:35365–35381
Xu C, Zhang Q, Li J, Zhao X (2008) A bee swarm genetic algorithm for the optimization of DNA encoding. In: 3rd international conference on innovative computing information and control, 2008. ICICIC’08. IEEE, pp 35–35
Xu C, Shen J, Du X, Zhang F (2018) An intrusion detection system using a deep neural network with gated recurrent units. IEEE Access 6:48697–48707
Xu J, Han D, Li KC, Jiang H (2020) A k-means algorithm based on characteristics of density applied to network intrusion detection. Comput Sci Inf Syst 00:14–14
Yang Z, Algesheimer R, Tessone CJ (2016) A comparative analysis of community detection algorithms on artificial networks. Sci Rep 6:30750
Yassin W, Udzir NI, Muda Z, Sulaiman MN, et al. (2013) Anomaly-based intrusion detection through k-means clustering and Naives Bayes classification. In: Proceedings of 4th international conference on computing and informatics, ICOCI, vol 49, pp 298–303
Yihunie F, Abdelfattah E, Regmi A (2019) Applying machine learning to anomaly-based intrusion detection systems. In: 2019 IEEE Long Island systems, applications and technology conference (LISAT). IEEE, pp 1–5
Yin C, Zhu Y, Fei J, He X (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5:21954–21961
Zhang J, Zulkernine M, Haque A (2008) Random-forests-based network intrusion detection systems. IEEE Trans Syst Man Cybern Part C Appl Rev 38(5):649–659
Zhang W, Yang Q, Geng Y (2009) A survey of anomaly detection methods in networks. In: International symposium on computer network and multimedia technology (2009), CNMT 2009. IEEE, pp 1–3
Zhou H (2018) Malware detection with neural network using combined features. In: China cyber security annual conference. Springer, pp 96–106
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Thakkar, A., Lohiya, R. A survey on intrusion detection system: feature selection, model, performance measures, application perspective, challenges, and future research directions. Artif Intell Rev 55, 453–563 (2022). https://doi.org/10.1007/s10462-021-10037-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10462-021-10037-9