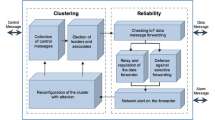
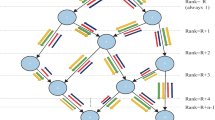
Abstract
Internet of things (IoT) is renowned for being a massive revolution led by business leaders and researchers. Routing protocol for low-power and lossy network (RPL) is a standardized protocol that serves the routing need of the IPv6-based low-power and lossy networks, which are the significant enablers of the IoT technology. Despite its many outstanding features, RPL offers very low protection against different routing attacks. In this respect, we mainly emphasize on the sybil attack. Specifically, we focus on three different types of sybil attack on a realistic smart home network topology. Considering the involvement of resource-constraint devices, we propose and evaluate a novel decentralized countermeasure against these attacks. The proposed countermeasure is based on a hybrid approach that involves the use of the geographical location of the nodes and a trust value-based parent selection procedure. Along with this, we use specially configured monitoring nodes that are responsible for the detection of the malicious attacker node(s). Further, we use RPL’s multi-instance property to integrate the proposed decentralized architecture into the exiting RPL protocol. We implement the proposed countermeasure in Cooja, the Contiki operating system-based network simulator. The results obtained through our experiments validate the practicality of the proposed countermeasure.




















Similar content being viewed by others
References
Watteyne T, Molinaro A, Richichi MG, Dohler M (2010) From MANET to IETF roll standardization: a paradigm shift in WSN routing protocols. IEEE Commun Surv Tutor 13(4):688–707
Bang AO, Ramteke PL (2013) MANET: history, challenges and applications. Int J Appl Innov Eng Manag (IJAIEM) 2(9):249–251
Airehrour D, Gutierrez J, Ray SK (2016) Secure routing for internet of things: a survey. J Netw Comput Appl 66:198–213
“Internet of things (IoT)—the future of IoT miniguide: the burgeoning IoT market continues, 2019. [Online]. https://www.cisco.com/c/en/us/solutions/internet-of-things/future-of-iot.html
Shirer M, MacGillivray C (2019) The growth in connected IoT devices is expected to generate 79.4 ZB of data in 2025, according to a new IDC forecast
Raoof A, Matrawy A, Lung C-H (2018) Routing attacks and mitigation methods for RPL-based internet of things. IEEE Commun Surv Tutor 21(2):1582–1606
Hwang YH (2015) IoT security & privacy: threats and challenges, In: Proceedings of the 1st ACM workshop on IoT privacy, trust, and security, p 1
Patra L, Rao UP (2016) Internet of things—architecture, applications, security and other major challenges. In: 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom). IEEE, pp 1201–1206
Winter T, Thubert P, Brandt A, Hui JW, Kelsey R, Levis P, Pister K, Struik R, Vasseur J-P, Alexander RK (2012) RPL: IPv6 routing protocol for low-power and lossy networks
Kharrufa H, Al-Kashoash HA, Kemp AH (2019) RPL-based routing protocols in IoT applications: a review. IEEE Sens J 19(15):5952–5967
Ghaleb B, Al-Dubai A, Ekonomou E, Qasem M, Romdhani I, Mackenzie L (2018) Addressing the DAO insider attack in RPL’s internet of things networks. IEEE Commun Lett 23(1):68–71
Tahir Y, Yang S, McCann J (2017) BRPL: backpressure RPL for high-throughput and mobile IoTs. IEEE Trans Mobile Comput 17(1):29–43
Pongle P, Chavan G (2015) A survey: attacks on RPL and 6LoWPAN in IoT. In: International Conference on Pervasive Computing (ICPC). IEEE 2015, pp 1–6
Le A, Loo J, Luo Y, Lasebae A (2013) The impacts of internal threats towards routing protocol for low power and lossy network performance. In: 2013 IEEE Symposium on Computers and Communications (ISCC). IEEE, pp 000789–000794
Zhang K, Liang X, Lu R, Shen X (2014) Sybil attacks and their defenses in the internet of things. IEEE Internet Things J 1(5):372–383
Hui TK, Sherratt RS, Sánchez DD (2017) Major requirements for building smart homes in smart cities based on internet of things technologies. Future Gener Comput Syst 76:358–369
Machado K, Rosário D, Cerqueira E, Loureiro AA, Neto A, De Souza JN (2013) A routing protocol based on energy and link quality for internet of things applications. Sensors 13(2):1942–1964
Giusto D, Iera A, Morabito G, Atzori L (2010) The internet of things: 20th Tyrrhenian workshop on digital communications. Springer, Berlin
Airehrour D, Gutierrez JA, Ray SK (2019) Sectrust-RPL: a secure trust-aware RPL routing protocol for internet of things. Future Gener Comput Syst 93:860–876
Kaliyar P, Jaballah WB, Conti M, Lal C (2020) LiDL: localization with early detection of sybil and wormhole attacks in IoT networks. Comput Secur. 94:101849
Levis P, Clausen T, Hui J, Gnawali O, Ko J (2011) The trickle algorithm, Internet Engineering Task Force, RFC6206
Kim H-S, Ko J, Culler DE, Paek J (2017) Challenging the IPV6 routing protocol for low-power and lossy networks (RPL): a survey. IEEE Commun Surv Tutor 19(4):2502–2525
Evangelista D, Mezghani F, Nogueira M, Santos A (2016) Evaluation of sybil attack detection approaches in the internet of things content dissemination. In: Wireless days (WD). IEEE 2016, pp 1–6
Jan MA, Nanda P, He X, Liu RP (2018) A sybil attack detection scheme for a forest wildfire monitoring application. Future Gener Comput Syst 80:613–626
Yao Y, Xiao B, Yang G, Hu Y, Wang L, Zhou X (2019) Power control identification: a novel sybil attack detection scheme in VANETs using RSSI. IEEE J Sel Areas Commun 37(11):2588–2602
Al-Qurishi M, Alrubaian M, Rahman SMM, Alamri A, Hassan MM (2018) A prediction system of sybil attack in social network using deep-regression model. Future Gener Comput Syst 87:743–753
Ayaida M, Messai N, Najeh S, Ndjore KB (2019) A macroscopic traffic model-based approach for sybil attack detection in VANETs. Ad Hoc Netw 90:101845
Vasudeva A, Sood M (2018) Survey on sybil attack defense mechanisms in wireless ad hoc networks. J Netw Comput Appl 120:78–118
Lu Y, Da Xu L (2018) Internet of things (IoT) cybersecurity research: a review of current research topics. IEEE Internet Things J 6(2):2103–2115
Raza S, Wallgren L, Voigt T (2013) SVELTE: real-time intrusion detection in the internet of things. Ad hoc Netw 11(8):2661–2674
Medjek F, Tandjaoui D, Abdmeziem MR, Djedjig N (2015) Analytical evaluation of the impacts of sybil attacks against RPL under mobility. In: 12th international symposium on programming and systems (ISPS). IEEE 2015, pp 1–9
Medjek F, Tandjaoui D, Romdhani I, Djedjig N (2017) Performance evaluation of RPL protocol under mobile sybil attacks. IEEE Trustcom/BigDataSE/ICESS. IEEE 2017:1049–1055
Medjek F, Tandjaoui D, Romdhani I, Djedjig N (2017) A trust-based intrusion detection system for mobile RPL based networks, In: 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData). IEEE, pp 735–742
Nikam A, Ambawade D (2018) Opinion metric based intrusion detection mechanism for RPL protocol in IoT. In: 3rd International Conference for Convergence in Technology (I2CT). IEEE 2018, pp 1–6
Conti M, Kaliyar P, Rabbani MM, Ranise S (2018) SPLIT: a secure and scalable RPL routing protocol for internet of things. In: 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob). IEEE, pp 1–8
Thulasiraman P, Wang Y (2019) A lightweight trust-based security architecture for RPL in mobile IoT networks. In: 16th IEEE Annual Consumer Communications & Networking Conference (CCNC). IEEE 2019, pp 1–6
Hashemi SY, Aliee FS (2019) Dynamic and comprehensive trust model for IoT and its integration into RPL. J Supercomput 75(7):3555–3584
Tandon A, Srivastava P (2019) Trust-based enhanced secure routing against rank and sybil attacks in IoT. In: 2019 Twelfth International Conference on Contemporary Computing (IC3). IEEE, pp 1–7
Murali S, Jamalipour A (2019) A lightweight intrusion detection for sybil attack under mobile RPL in the internet of things. IEEE Internet Things J 7(1):379–388
Pu C (2020) Sybil attack in RPL-based internet of things: analysis and defenses. IEEE Internet Things J 7(6):4937–4949
Gnawali O, Levis P (2012) The minimum rank with hysteresis objective function, RFC 6719
Preiss T, Sherburne M, Marchany R, Tront J (2014) Implementing dynamic address changes in contikios. In: International Conference on Information Society (i-Society 2014). IEEE, pp 222–227
Dunkels A, Gronvall B, Voigt T (2004) Contiki-a lightweight and flexible operating system for tiny networked sensors, In: 29th annual IEEE International Conference on Local Computer Networks. IEEE, pp 455–462
Österlind F, Dunkels A, Eriksson J, Finne N, Voigt T (2006) Cross-level sensor network simulation with cooja. In: First IEEE international workshop on practical issues in building sensor network applications (SenseApp 2006)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Bang, A.O., Rao, U.P. A novel decentralized security architecture against sybil attack in RPL-based IoT networks: a focus on smart home use case. J Supercomput 77, 13703–13738 (2021). https://doi.org/10.1007/s11227-021-03816-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-03816-2