Abstract
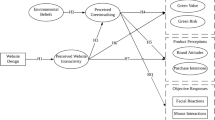
Food fraud is a widespread problem that involves the act of defrauding consumers for economic gain. Food fraud incidents pose a considerable threat to the economic stability of agri-food industry as well as the health and welfare of consumers. With the increasing use of online grocery shopping, the Internet has facilitated deceptive and fraudulent practices by criminals. Using a sample of U.S. consumers, the current study explores the applicability of routine activities theory in the context of food fraud. The findings show that online routine activities, online target suitability, exposure to food ads, and perceived risk are significantly linked to food fraud victimization. Our study demonstrates that the routine activities theory is a useful framework to understand the vulnerabilities associated with food fraud. Implications for research and policy are discussed.

Similar content being viewed by others
References
Aung, M.M., and Y.S. Chang. 2014. Traceability in a food supply chain: Safety and quality perspectives. Food Control 39: 172–184.
Barlass, T. 2015. 'Child aged 10 dies after drinking coconut drink as importer admits label charges', The Sydney Morning Herald, 4 October, Retrieved from https://www.smh.com.au/healthcare/child-aged-10-dies-after-drinking-coconut-milk-as-importer-admits-label-charges-20150925-gjvakb.html
BBC News. 2010. 'China dairy products found tainted with melamine', BBC News, 9 July, Retrieved from https://www.bbc.com/news/10565838
Berinsky, A.J., G.A. Huber, and G.S. Lenz. 2012. Evaluating online labor markets for experimental research: Amazon. com’s Mechanical Turk. Political Analysis 20: 351–368.
Bilge, L., T. Strufe, D. Balzarotti, and E. Kirda. 2009. All your contacts are belong to us: automated identity theft attacks on social networks. Proceedings of the 18th International Conference on World Wide Web; 20–24 April, Madrid, Spain, pp. 551–560.
Bimbo, F., A. Bonanno, and R. Viscecchia. 2019. An empirical framework to study food labelling fraud: An application to the Italian extra-virgin olive oil market. Australian Journal of Agricultural and Resource Economics 63: 701–725.
Brenner, L., T. Meyll, O. Stolper, and A. Walter. 2020. Consumer fraud victimization and financial well-being. Journal of Economic Psychology 76: 102243.
Brooks, S., C.T. Elliott, M. Spence, C. Walsh, and M. Dean. 2017. Four years post-horsegate: An update of measures and actions put in place following the horsemeat incident of 2013. NPJ Science of Food 1: 1–7.
Buhrmester, M., T. Kwang, and S.D. Gosling. 2011. Amazon’s Mechanical Turk: A new source of inexpensive, yet high-quality, data? Perspectives on Psychological Science 6: 3–5.
Charlebois, S., A. Schwab, R. Henn, and C.W. Huck. 2016. Food fraud: An exploratory study for measuring consumer perception towards mislabeled food products and influence on self-authentication intentions. Trends in Food Science and Technology 50: 211–218.
Charlebois, S., M. Juhasz, L. Foti, and S. Chamberlain. 2017. Food fraud and risk perception: Awareness in Canada and projected trust on risk-mitigating agents. Journal of International Food and Agribusiness Marketing 29: 260–277.
Cohen, L.E., and M. Felson. 1979. Social change and crime rate trends: A routine activity approach. American Sociological Review 44: 588–608.
Conway, J. 2018a. Online grocery shopping among households in the U.S. 2017, by age. Statista. Retrieved from https://www.statista.com/statistics/754619/online-grocery-shopping-by-age/
Conway, J. 2018b. U.S. online grocery sales 2018–2023. Statista. Retrieved from https://www.statista.com/statistics/293707/us-online-grocery-sales/
Coupe, T., and L. Blake. 2006. Daylight and darkness targeting strategies and the risks of being seen at residential burglaries. Criminology 44: 431–464.
Cowburn, G., and A. Boxer. 2007. Magazines for children and young people and the links to Internet food marketing: A review of the extent and type of food advertising. Public Health Nutrition 10: 1024–1031.
Crossey, S. 2017. 5 problems facing the global food supply chain. Retrieved from https://foodsafetytech.com/column/5-problems-facing-global-food-supply-chain/
Decernis. 2019. Food Fraud Database. Retrieved from https://decernis.com/solutions/food-fraud-database/
Deliema, M., D. Shadel, and K. Pak. 2020. Profiling victims of investment fraud: Mindsets and risky behaviors. Journal of Consumer Research 46: 904–914.
Drew, J.M., and L. Farrell. 2018. Online victimization risk and self-protective strategies: Developing police-led cyber fraud prevention programs. Police Practice and Research 19: 537–549.
Eck, J.E., and R.V. Clarke. 2003. Classifying common police problems: A routine activity approach. Crime Prevention Studies 16: 7–40.
Elferink, M., and F. Schierhorn. 2016. 'Global demand for food is rising. Can we meet it? ', Harvard Business Review, 7 April, Retrieved from https://hbr.org/2016/04/global-demand-for-food-is-rising-can-we-meet-it
Esteki, M., J. Regueiro, and J. Simal-Gandara. 2019. Tackling fraudsters with global strategies to expose fraud in the food chain. Comprehensive Reviews in Food Science and Food Safety 18: 425–440.
EUIPO. 2016. Infringement of protected Geographical Indications for wine, spirits, agricultural products and foodstuffs in the European Union. Retrieved from https://euipo.europa.eu/tunnel-web/secure/webdav/guest/document_library/observatory/documents/Geographical_indications_report/geographical_indications_report_en.pdf
Europol. 2018. Operation Opson VII Analysis Report. Retrieved from https://www.europol.europa.eu/publications-documents/operation-opson-vii-analysis-report
FAO. 2018. Overview of food fraud in the fisheries sector. Retrieved from http://www.fao.org/3/i8791en/I8791EN.pdf
Farrand, B. 2018. Combatting physical threats posed via digital means: the European Commission’s developing approach to the sale of counterfeit goods on the Internet. European Politics and Society 19: 338–354.
FDA. 2009. Economically motivated adulteration; Public meeting; Request for comment, Docket No. FDA-2009-N-0166. Federal Register 15497.
Felt, A.P., M. Finifter, E. Chin, S. Hanna, and D. Wagner. 2011. A survey of mobile malware in the wild. Proceedings of the 1st ACM workshop on Security and Privacy in Smartphones and Mobile Devices; 17–21 October, Chicago, IL, pp. 3–14.
Fenoff, R., and J. Spink. 2017. Food fraud and food fraud detection technologies. In The Routledge Handbook of Technology, Crime and Justice, ed. M.R. McGuire and T.J. Holt, 295–309. New York: Taylor and Francis.
Ferraro, K.F. 1995. Fear of Crime: Interpreting Victimization Risk. Albany, NY: SUNY Press.
Fisher, B.S., F.T. Cullen, and M.G. Turner. 2002. Being pursued: Stalking victimization in a national study of college women. Criminology and Public Policy 1: 257–308.
Fogel, J., and E. Nehmad. 2009. Internet social network communities: Risk taking, trust, and privacy concerns. Computers in Human Behavior 25: 153–160.
Frankel, E. N., R. J. Mailer, S. C. Wang, C. F. Shoemaker, J. X. Guinard, J. D. Flynn, and N. D. Sturzenberger. 2011. Report: Evaluation of extra-virgin olive oil sold in California. UC-Davis Olive Center. Retrieved from https://olivecenter.ucdavis.edu/media/files/report041211finalreduced.pdf
GAO. 2020. Food safety: High risk issue. Retrieved from https://www.gao.gov/key_issues/food_safety/issue_summary#t=0
GFSI. 2018. Tackling Food Fraud through Food Safety Management Systems. Retrieved from https://mygfsi.com/wp-content/uploads/2019/09/Food-Fraud-GFSI-Technical-Document.pdf
Goodman, J.K., C.E. Cryder, and A. Cheema. 2013. Data collection in a flat world: The strengths and weaknesses of Mechanical Turk samples. Journal of Behavioral Decision Making 26: 213–224.
Granitto, Y. 2015. 'Police Uncover 7,000-Ton Olive Oil Fraud in Italy', 3 December, Olive Oil Times, Retrieved from https://www.oliveoiltimes.com/business/police-uncover-7000-ton-olive-oil-fraud-in-italy/49929
Grocery Manufacturers Association. 2010. Consumer product fraud: deterrence and detection. Retrieved from http://www.gmaonline.org/downloads/wygwam/consumerproductfraud.pdf
Halford, J.C., J. Gillespie, V. Brown, E.E. Pontin, and T.M. Dovey. 2004. Effect of television advertisements for foods on food consumption in children. Appetite 42: 221–225.
Hayashi, Y. 2019. 'Scammers Find More Opportunities on Internet Marketplaces', The Wall Street Journal, 29 September, Retrieved from https://www.wsj.com/articles/scammers-find-easy-prey-on-internet-marketplaces-11569784198
Holden, C.J., T. Dennie, and A.D. Hicks. 2013. Assessing the reliability of the M5–120 on Amazon’s mechanical Turk. Computers in Human Behavior 29: 1749–1754.
Holt, T.J., and A.M. Bossler. 2008. Examining the applicability of lifestyle-routine activities theory for cybercrime victimization. Deviant Behavior 30: 1–25.
Holt, T.J., and M.G. Turner. 2012. Examining risks and protective factors of on-line identity theft. Deviant Behavior 33: 308–323.
Holt, T.J., and A.M. Bossler. 2013. Examining the relationship between routine activities and malware infection indicators. Journal of Contemporary Criminal Justice 29: 420–436.
Holtfreter, K., M.D. Reisig, and T.C. Pratt. 2008. Low self-control, routine activities, and fraud victimization. Criminology 46: 189–220.
Holtfreter, K., M.D. Reisig, T.C. Pratt, and R.E. Holtfreter. 2015. Risky remote purchasing and identity theft victimization among older Internet users. Psychology, Crime and Law 21: 681–698.
Hong, E., S.Y. Lee, J.Y. Jeong, J.M. Park, B.H. Kim, K. Kwon, and H.S. Chun. 2017. Modern analytical methods for the detection of food fraud and adulteration by food category. Journal of the Science of Food and Agriculture 97: 3877–3896.
International Food Information Council. 2020. Consumer perceptions of food fraud. Retrieved from https://foodinsight.org/wp-content/uploads/2020/02/Food-Fraud-Research.pdf
Johnson, R. 2014. Food Fraud and Economically Motivated Adulteration of Food and Food Ingredients. (CRS Report No. R43358) Retrieved from https://fas.org/sgp/crs/misc/R43358.pdf
Jouvenal, J. 2018. 'Seafood mogul pleads guilty to selling 'distressed' meat as Chesapeake blue crab', The Washington Post, 26 September, Retrieved from https://www.washingtonpost.com/local/public-safety/crab-fakes-seafood-mogul-pleads-guilty-to-selling-distressed-meat-as-fresh-chesapeake-blue-crab/2018/09/26/d739629e-c0e3-11e8-be77-516336a26305_story.html
Kemps, E., M. Tiggemann, and S. Hollitt. 2014. Exposure to television food advertising primes food-related cognitions and triggers motivation to eat. Psychology and Health 29: 1192–1205.
Kennedy, L.W., and D.R. Forde. 1990. Routine activities and crime: An analysis of victimization in Canada. Criminology 28: 137–152.
Khaksar, R., T. Carlson, D.W. Schaffner, M. Ghorashi, D. Best, S. Jandhyala, J. Traverso, and S. Amini. 2015. Unmasking seafood mislabeling in U.S. markets: DNA barcoding as a unique technology for food authentication and quality control. Food Control 56: 71–76.
Kigerl, A. 2012. Routine activity theory and the determinants of high cybercrime countries. Social Science Computer Review 30: 470–486.
Leukfeldt, E.R., and M. Yar. 2016. Applying routine activity theory to cybercrime: A theoretical and empirical analysis. Deviant Behavior 37: 263–280.
Levay, K.E., J. Freese, and J.N. Druckman. 2016. The demographic and political composition of Mechanical Turk samples. Sage Open 6: 1–17.
Lord, N., J. Spencer, J. Albanese, and C.F. Elizondo. 2017. In pursuit of food system integrity: The situational prevention of food fraud enterprise. European Journal on Criminal Policy and Research 23: 483–501.
Manning, L., and J.M. Soon. 2016. Food safety, food fraud, and food defense: A fast evolving literature. Journal of Food Science 81: R823–R834.
Messner, S.F., and J.R. Blau. 1987. Routine leisure activities and rates of crime: A macro-level analysis. Social Forces 65: 1035–1052.
Mooney, P. 2015. 'The Story Behind China's Tainted Milk Scandal Company feared going public with information as thousands of children were sickened', U.S. News & World Report, 9 October, Retrieved from https://www.usnews.com/news/world/articles/2008/10/09/the-story-behind-chinas-tainted-milk-scandal
Navarro, J.N., and J.L. Jasinski. 2012. Going cyber: Using routine activities theory to predict cyberbullying experiences. Sociological Spectrum 32: 81–94.
Newman, G.R., and R.V. Clarke. 2003. Superhighway Robbery: Preventing Ecommerce Crime. Cullompton: Willan Press.
Ngo, F.T., and R. Paternoster. 2011. Cybercrime Victimization: An examination of Individual and Situational level factors. International Journal of Cyber Criminology 5: 773–793.
Packaged Facts. 2019. Global Food E-commerce. Retrieved from https://www.packagedfacts.com/Global-Food-Commerce-12393622/
Paek, S.Y., and M.K. Nalla. 2015. The relationship between receiving phishing attempt and identity theft victimization in South Korea. International Journal of Law, Crime and Justice 43: 626–642.
Pratt, T.C., K. Holtfreter, and M.D. Reisig. 2010. Routine online activity and internet fraud targeting: Extending the generality of routine activity theory. Journal of Research in Crime and Delinquency 47: 267–296.
PwC and SSAFE. 2016. Food fraud vulnerability assessment: Free online tool helps food companies fight fraud to protect consumers. Retrieved from https://www.pwc.com/vn/en/publications/2016/food_fraud_vulnerability_assessment.pdf
Reisig, M.D., and K. Holtfreter. 2013. Shopping fraud victimization among the elderly. Journal of Financial Crime 20: 324–337.
Reisig, M.D., T.C. Pratt, and K. Holtfreter. 2009. Perceived risk of internet theft victimization: Examining the effects of social vulnerability and financial impulsivity. Criminal Justice and Behavior 36: 369–384.
Reyns, B.W. 2013. Online routines and identity theft victimization: Further expanding routine activity theory beyond direct-contact offenses. Journal of Research in Crime and Delinquency 50: 216–238.
Reyns, B.W. 2015. A routine activity perspective on online victimization: Results from the Canadian General Social Survey. Journal of Financial Crime 22: 396–411.
Reyns, B.W., and B. Henson. 2016. The thief with a thousand faces and the victim with none: Identifying determinants for online identity theft victimization with routine activity theory. International Journal of Offender Therapy and Comparative Criminology 60: 1119–1139.
Reyns, B.W., B. Henson, and B.S. Fisher. 2011. Being pursued online: Applying cyberlifestyle-routine activities theory to cyberstalking victimization. Criminal Justice and Behavior 38: 1149–1169.
Reyns, B.W., and R. Randa. 2019. No honor among thieves: personal and peer deviance as explanations of online identity fraud victimization Security Journal, 1–16.
Robson, K., M. Dean, S. Brooks, S. Haughey, and C. Elliott. 2020. A 20-year analysis of reported food fraud in the global beef supply chain. Food Control 116: 107310.
Sampson, R.J., and J.D. Wooldredge. 1987. Linking the micro-and macro-level dimensions of lifestyle-routine activity and opportunity models of predatory victimization. Journal of Quantitative Criminology 3: 371–393.
Schreck, C.J., R.A. Wright, and J.M. Miller. 2002. A study of individual and situational antecedents of violent victimization. Justice Quarterly 19: 159–180.
Scully, M., M. Wakefield, P. Niven, K. Chapman, D. Crawford, I.S. Pratt, L.A. Baur, V. Flood, B. Morley, and NaSSDA Study Team. 2012. Association between food marketing exposure and adolescents’ food choices and eating behaviors. Appetite 58: 1–5.
Shears, P. 2010. Food fraud—A current issue but an old problem. British Food Journal 112: 198–213.
Silic, M., and A. Back. 2016. The dark side of social networking sites: Understanding phishing risks. Computers in Human Behavior 60: 35–43.
Soon, J.M., and L. Manning. 2019. Developing anti-counterfeiting measures: The role of smart packaging. Food Research International 123: 135–143.
Soon, J.M., L. Manning, and R. Smith. 2019. Advancing understanding of pinch-points and crime prevention in the food supply chain. Crime Prevention and Community Safety 21: 42–60.
Spink, J., P.V. Hegarty, N.D. Fortin, C.T. Elliott, and D.C. Moyer. 2019. The application of public policy theory to the emerging food fraud risk: Next steps. Trends in Food Science & Technology 85: 116–128.
Spink, J., and D.C. Moyer. 2011. Defining the public health threat of food fraud. Journal of Food Science 76: R157–R163.
Spink, J., D.L. Ortega, C. Chen, and F. Wu. 2017. Food fraud prevention shifts the food risk focus to vulnerability. Trends in Food Science and Technology 62: 215–220.
Tewksbury, R., E.E. Mustaine, and K.M. Stengel. 2008. Examining rates of sexual offenses from a routine activities perspective. Victims and Offenders 3: 75–85.
Tibola, C.S., S.A. da Silva, A.A. Dossa, and D.I. Patrício. 2018. Economically motivated food fraud and adulteration in Brazil: Incidents and alternatives to minimize occurrence. Journal of Food Science 83 (8): 2028–2038.
Tillyer, M.S., and J.E. Eck. 2009. Routine activities. In 21st Century Criminology: A Reference Handbook, ed. J.M. Miller, 279–287. Thousand Oaks, CA: Sage.
USDA. 2019. Organic Market Overview. United States Department of Agriculture Economic Research Service. Retrieved from https://www.ers.usda.gov/topics/natural-resources-environment/organic-agriculture/organic-market-overview/
Van Ruth, S.M., W. Huisman, and P.A. Luning. 2017. Food fraud vulnerability and its key factors. Trends in Food Science and Technology 67: 70–75.
Van Wilsem, J. 2011. ‘Bought it, but never got it’ assessing risk factors for online consumer fraud victimization. European Sociological Review 29: 168–178.
Warner, K., W. Roberts, P. Mustain, B. Lowell and M. Swain. 2019. Casting a Wider Net: More Action Needed to Stop Seafood Fraud in the United States. Retrieved from https://usa.oceana.org/blog/oceana-study-finds-seafood-fraud-nationwide
Weinberg, J.D., J. Freese, and D. McElhattan. 2014. Comparing data characteristics and results of an online factorial survey between a population-based and a crowdsource-recruited sample. Sociological Science 1: 292–331.
Wiecha, J.L., K.E. Peterson, D.S. Ludwig, J. Kim, A. Sobol, and S.L. Gortmaker. 2006. When children eat what they watch: Impact of television viewing on dietary intake in youth. Archives of Pediatrics & Adolescent Medicine 160: 436–442.
Woolfe, M., and S. Primrose. 2004. Food forensics: Using DNA technology to combat misdescription and fraud. Trends in Biotechnology 22: 222–226.
Yar, M. 2005. The novelty of ‘Cybercrime’ an assessment in light of routine activity theory. European Journal of Criminology 2: 407–427.
Yiannas, F. 2018. A new era of food transparency powered by blockchain. Innovations: Technology Governance, Globalization 12: 46–56.
Zhang, W., and J. Xue. 2016. Economically motivated food fraud and adulteration in China: An analysis based on 1553 media reports. Food Control 67: 192–198.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Have you ever purchased any food-related product via the Internet or online vendors that was misrepresented or falsely labeled in the past 12 months? (yes/no/unsure).
What is your age? (below 18 / 18 to 24 / 25 to 34 / 35 to 44 / 45 to 54 / 55 to 64 / 65 and above).
What is your biological sex? (female / male).
What is your race / ethnicity? (Hispanic or Latino / Black or African-American / Asian-American / American Indian / White or Caucasian / Native Hawaiian or Pacific Islander / Other).
Which of the following best describes your level of education? (some high school / High school diploma or equivalent / some college / bachelor’s degree / master’s degree / doctorate or professional degree).
Which of the following best describes your annual household income? (less than $10,000 / $10,000 to $24,999 / $25,000 to $49,999 / $50,000 to $99,999 / $100,000 and greater).
What is your status of employment? (employed full-time / employed part-time / unemployed / unemployed / student / retired / self-employed / unable to work).
What is your marital status? (single / married / in a domestic partnership / divorced / widowed).
Do you purchase foods regularly using online vendors (e.g., Amazon, eBay, Walmart)? (yes / no).
If you think about the past 12 months, how often do you spend performing the following activities (online banking, online shopping, online forums, social networking sites, chatting apps) while online or using your computer-mediated communication (e.g., personal computer, laptop, tablets, smart phone)? (always / often / sometimes/rarely/never).
Have you ever created a profile or account using online vendor websites (e.g., Amazon, eBay, Walmart)? (yes / no).
If you answered yes, please respond to the following question.
-
Do you allow anyone to view your profile(s) or account(s)? (yes / no)
-
Do you include information about your interests on your profile(s) or account(s)? (yes / no)
-
Do you spend time personalizing your profile page(s) or account(s)? (yes / no)
-
Do you use your real name on your profile page(s) or account(s)? (yes / no)
-
Do you have your own profile page or account with an online vendor (e.g., Amazon) for purchasing food products or supplements? (yes / no)
During the past 6 months, how often have you spent time viewing traditional sources of media (e.g., radio, television, magazines, newspapers, TV) related to food or nutrition related products or supplements? (always / often / sometimes / rarely / never).
During the past 6 months, how often have you spent time viewing online sources of media (e.g., Twitter, Facebook, YouTube, Instagram, Linkedln) related to food or nutrition related products or supplements? (always / often / sometimes / rarely / never).
How likely or unlikely do you think you will be a victim of food fraud in the following year? (very likely / fairly likely / fairly unlikely / very unlikely).
Rights and permissions
About this article
Cite this article
Lee, B., Fenoff, R. & Spink, J. Routine activities theory and food fraud victimization. Secur J 35, 506–530 (2022). https://doi.org/10.1057/s41284-021-00287-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1057/s41284-021-00287-1