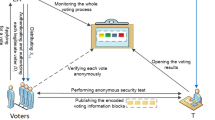
Abstract
Remarkable theoretical and experimental achievements of quantum technology have convincingly shown that a flourishing quantum age is coming. The threat of quantum attacks posed to the classical cryptographic protocols, whose security lies on the computational complexity of difficult problems, is ever more severe. As a particular voting and typical daily activity, the anonymous veto has already been further studied in classical cryptography. In this paper, a novel quantum anonymous veto protocol with information-theoretic security is proposed. Benefited from the entanglement of GHZ states and quantum nonlocality, our protocol satisfies some desirable properties of reliability, privacy, verifiability, tracelessness, and fairness. Compared to the properties of classical protocols, tracelessness is a unique property in quantum anonymous veto protocol. Using the online analog quantum computer of IBM Corporation placed on the cloud, we make an experimental test of anonymous veto for four voters. Any harmful attempt of cheating from the semi-honest certificate authority center, malicious voters, and external eavesdroppers will be detected by honest participants based on the fantastic quantum world. This work to voting theory helps elucidate how quantum mechanics can be harnessed for secure strategic advantage.





Similar content being viewed by others
References
Boneh, D., Golle, P.: Almost entirely correct mixing with applications to voting. In: Proceedings of 9th ACM Conference. Computer Communications Security, p. 6877, Washington (2002)
Clarkson, M.R., Chong, S., Myers, A.C.: Toward a secure voting system. In: Proceedings of 2008 IEEE Symposium on Security and Privacy, p. 354368, Oakland (2008)
Vaccaro, J.A., Spring, J., Chefles, A.: Quantum protocols for anonymous voting and surveying. Phys. Rev. A 75(1), 012333 (2007)
Horoshko, D., Kilin, S.: Quantum anonymous voting with anonymity check. Phys. Lett. A 375(8), 1172–1175 (2011)
Wang, Q.L., Yu, C.H., Gao, F., Qi, H.Y., Wen, Q.Y.: Self-tallying quantum anonymous voting. Phys. Rev. A 94(2), 022333 (2016)
Bradlyn, B., Elcoro, L., Cano, J., Vergniory, M.G., Wang, Z.J., Felser, C., Aroyo, M.I., Bernevig, B.A.: Topological quantum chemistry. Nature 547, 298305 (2017)
Lambert, N., Chen, Y., Cheng, Y., Li, C.M., Chen, G.Y., Nori, F.: Quantum biology. Nat. Phys. 9, 1018 (2013)
Liu, J., Zhang, X.L., Hu, B., Lu, Q., Liu, D.J., Dong, C.Q., Yang, Y.P.: Formation mechanism of HCN and NH3 during indole pyrolysis: a theoretical DFT study. J. Energy Inst. 93(2), 649–657 (2020)
Zrazhevskiy, P., Gao, X.: Multifunctional quantum dots for personalized medicine. Nano Today 4(5), 414–428 (2009)
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computer, System Signal Process, p. 175179, Bangalore (1984)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 20502056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441444 (2000)
Lucamarini, M., Dynes, J.F., Frohlich, B., Yuan, Z.L., Shields, A.J.: Security bounds for efficient decoy-state quantum key distribution. IEEE J. Set. Top. Quant. 21(3), 6601468 (2015)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 18241829 (1999)
Yang, Y.G., Wen, Q.Y., Zhang, X.: Multiparty simultaneous quantum identity authentication with secret sharing. Sci. China G Phys. Mech. Astron. 51(3), 321327 (2008)
Jia, H.Y., Wen, Q.Y., Gao, F., Qin, S.J., Guo, F.Z.: Dynamic quantum secret sharing. Phys. Lett. A 376(10), 1035–1041 (2012)
Christandl, M., Wehner, S.: Quantum Anonymous Transmissions. In Advances in Cryptology: ASIACRYPT 2005, pp. 217–235, Berlin, Heidelberg (2005)
Menicucci, N.C., Baragiola, B.Q., Demarie, T.F., Brennen, G.K.: Anonymous broadcasting of classical information with a continuous-variable topological quantum code. Phys. Rev. A 97(3), 032345 (2018)
Gao, F., Qin, S.J., Huang, W., Wen, Q.Y.: Quantum private query: a new kind of practical quantum cryptographic protocols. Sci. China G Phys. Mech. Astron. 62(7), 070301 (2019)
Wei, C.Y., Cai, X.Q., Liu, B., Wang, T.Y., Gao, F.: A generic construction of quantum-oblivious-key-transfer-based private query with ideal database security and zero failure. IEEE Trans. Comput. 67(1), 2–8 (2018)
Wang, Q.L., Li, Y.C., Yu, C.H., He, H., Zhang, K.J.: Quantum anonymous ranking and selection with verifiability. Quantum Inf. Process 19, 166 (2020). https://doi.org/10.1007/s11128-020-02664-y
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with \(n\)-level entangled statesg. Quantum Inf. Proc. 13(11), 23752389 (2014)
Wang, Q.L., Yu, C.H., Li, Y.C., Liu, J.S., Shi, R.H., Zhou, Y.Q.: Authenticated Quantum Sortition and Application in “Picking at Random Problems”. In IEEE Communications Letters, https://doi.org/10.1109/LCOMM.2020.3025319
Xu, F.H., Curty, M., Qi, B., Lo, H.K.: Measurement-device-independent quantum cryptography. IEEE J. Set. Top. Quantum 21(3), 6601111 (2015)
Mihara, T.: Quantum identification schemes with entanglements. Phys. Rev. A 65(6), 052326 (2002)
Hillery, M., Ziman, M., Buzek, V., Bieliková, M.: Towards quantum-based privacy and voting. Phys. Lett. A 349(1), 75–81 (2006)
Bonanome, M., Buzek, V., Hillery, M., Ziman, M.: Toward protocols for quantum-ensured privacy and secure voting. Phys. Rev. A 84(2), 022331 (2011)
Jiang, L., He, G.Q., Nie, D., Xiong, J., Zeng, G.H.: Quantum anonymous voting for continuous variables. Phys. Rev. A 85(4), 042309 (2012)
Xue, P., Zhang, X.: A simple quantum voting scheme with multi-qubit entanglement. Sci. Rep. 7(1), 7586 (2017)
Wang, S.L., Zhang, S., Wang, Q., Shi, R.H.: Fault-tolerant quantum anonymous voting protocol. Int. J. Theor. Phys. 58(3), 1008–1016 (2019)
The IBM Quantum Experience. http://www.research.ibm.com/quantum
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65(3), 032302 (2002)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: A simple participant attack on the brádler-dušek protocol. Phys. Rev. A 7(4), 329–334 (2007)
Lin, S., Gao, F., Guo, F.Z., Wen, Q.Y., Zhu, F.C.: Comment on “multiparty quantum secret sharing of classical messages based on entanglement swapping”. Phys. Rev. A 76(3), 036301 (2007)
Ramij, R., Guruprasad, K.: GHZ correlation provides secure Anonymous Veto Protocol. arXiv:quant-ph/1507.00592v2
Acknowledgements
This work was supported by NSFC (Grant No. 61801126), Open project of Chinese Academy of Sciences Key Laboratory of Quantum Information, University of Science and Technology of China (Grant No. KQI201902), the Fundamental Research Funds for the Central Universities (2020MS014), Beijing Excellent Talents Training Funding Project (Grant No. 201800002685XG356), Research and Application of Key Technologies for Open Source Software Security Monitoring (Grant No. SGFJXT00YJJS1800074), NSFC (Grant No. 61772001, 61901030), the Beijing Natural Science Foundation (Grant No. 4194088), the National Postdoctoral Program for Innovative Talent (Grant No. BX20180042), and the China Postdoctoral Science Foundation (Grant No. 2018M640070).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, Q., Li, Y., Yu, C. et al. Quantum-based anonymity and secure veto. Quantum Inf Process 20, 85 (2021). https://doi.org/10.1007/s11128-021-03022-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-021-03022-2