Abstract
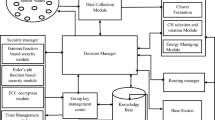
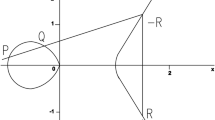
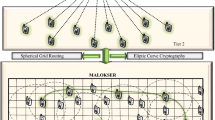
In this paper, we propose a new cryptosystem based on matrix translation and Elliptic curve cryptography for developing a secure routing algorithm to provide energy efficient and secured data communications in Wireless Sensor Networks. Moreover, the newly proposed techniques are implemented by decomposing the process into the key generation phase, encryption phase, cluster based secure routing phase and decryption phase. For this purpose, we introduce two new tables namely space reference table and String Position based ASCII value and Prime number generation Table. Here, the Space reference table is used to assign the values for the spaces that are occurring in the sentence before the encryption and decryption process. Next, it uses the String Position based ASCII value and Prime number generation Table developed in this work to convert the strings into numerical digits and to allocate the nearest prime number for the generated numerical digits. In addition, we propose two new algorithms namely ASCII AND PRIME NUMBER based Encryption/Decryption Algorithm and a Secure Routing Algorithm using cipher text conversion and distance vectors called Matrix Translation and Elliptic Curve based Cryptosystem for Secure Routing Algorithm for performing cluster based and energy efficient secure routing. The major advantages of the proposed secure routing system include the increase in security, packet delivery ratio and overall network performance and also decrease in energy consumption and delay. This work has been implemented using NS2 simulator and Java.





Similar content being viewed by others
References
Peng, C., Chen, J., Obaidat, M. S., Vijayakumar, P., & He, D. (2020). Efficient and provably secure multireceiver signcryption scheme for multicast communication in edge computing. IEEE Internet of Things Journal, 7, 6056–6068.
Siva, S., Sindhu, S., Geetha, S., & Kannan, A. (2012). Decision tree based light weight intrusion detection using a wrapper approach. Expert Systems with Applcations, 39(1), 129–141.
Kavin, B. P., Ganapathy, S., Kanimozhi, U., & Kannan, A. (2020). An enhanced security framework for secured data storage and communications in cloud using ECC, access control and LDSA. Wireless Personal Communications, 115(2), 1107–1135.
Thangaramya, K., Kulothungan, K., Logambigai, R., Selvi, M., Ganapathy, S., & Kannan, A. (2019). Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Computer Networks, 151, 211–223.
Kalidoss, T., Rajasekaran, L., Kanagasabai, K., Sannasi, G., & Kannan, A. (2020). QoS aware trust based routing algorithm for wireless sensor networks. Wireless Personal Communications, 110(4), 1637–1658.
Sethuraman, P., Tamizharasan, P. S., & Kannan, A. (2019). Fuzzy genetic elliptic curve diffie hellman algorithm for secured communication in networks. Wireless Personal Communications, 105(3), 993–1007.
Viswanathan, S., & Kannan, A. (2019). “Elliptic key cryptography with Beta Gamma functions for secure routing in wireless sensor networks.” Wireless Networks, 25, 4903–4914. https://doi.org/10.1007/s11276-019-02073-9.
Bartolini, S., & Giorgi, R. (2008). Effecticve of instruction-set extension on an embedded processor; A case study on elliptic curve cryptography over GF(2m). IEEE Transactions on Computers, 57(5), 672–685.
Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of Computation, 48(177), 203–209.
Lauter, K. (2004). The advantages of elliptic curve cryptography for wireless security. IEEE Wireless Communications, 11(1), 62–67.
Liu, Z., Huang, X., Hu, Z., Khan, M. K., Seo, H., & Zhou, L. (2017). On emerging family of elliptic curves to secure internet of things: ECC comes of age. IEEE Transactions on Dependable and Secure Computing, 14(3), 237–248.
de Dormale, G. M., & Quisquater, J. J. (2007). High-speed hardware implementations of elliptic curve cryptography: A survey. Journal of Systems Architecture, 53(2–3), 72–84.
Li, T., Liu, Z., Li, J., Jia, C., & Li, K. (2017). CDPS: Acryptographic data publishing system. Journal of Computer and System Sciences, 89, 80–91.
Elhoseny, M., Elminir, H., Riad, A., & Yuan, X. (2016). A secure data routing schema for WSN using elliptic curve cryptography and homomorphic encryption. Journal of King Saud University Computer and Information Sciences, 28, 262–275.
Heinzelman, W. R., Chandrakasan, A. P., & Balakrishnan, H. (2000), ‘Energy-efficient communication protocol for wireless microsensor networks’. Proceedings of IEEE 33rd annual Hawaii international conference on system sciences, vol. 2, pp. 1–10.
Heinzelman, W. R., & ChandrakasanBalakrishnan, A. P. H. (2002). An application specific protocol architecture for wireless sensor network. IEEE Transaction on Wireless Communication, 1(4), 660–670.
Younis, O., & Fahmy, S. (2004). HEED: A hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks. IEEE Transactions on Mobile Computing, 3(4), 366–379.
Abdalla, H., Hu, X., Wahaballa, A., Ali, A. A., Ramadan, M., & Qin, Z. (2017). Integrating the functional encryption and proxy re-cryptography to secure DRM scheme. Internation Journal of Network Security, 19(1), 27–38.
Kaaniche, N., & Laurent, M. (2017). Data security and privacy preservation in cloud storage environments based on cryptographic mechanisms. Computer Communications, 111, 120–141.
Kumar, S., Kumar, M., Budhiraja, R., Das, M. K., & Singh, S. (2018). A cryptographic model for better information security. Journal of Information Security and Applications, 43, 123–138.
Zhou, Q., Yang, G., & He, L. (2014). A secure enhanced data aggregation based on ECC in wireless sensor network. Sensor Journal, 14(4), 6701–6721.
Mykletun, E., Girao, J., Westhoff, D. (2006). “Public key based crypto schemes for data concealment in wireless sensor networks”, In: The IEEE international conference on communications, IEEE, Istanbul, pp. 2288–2295.
Rizk, R., & Alkady, Y. (2015). Two-phase hybrid cryptography algorithm for wireless sensor networks. Journal of Electrical Systems and Information Technology, 2, 296–313.
Shengmin, Xu., Yang, G., & Yi, Mu. (2019). Revocable attribute-based encryption with decryption key exposure resistance and ciphertext delegation. Information Sciences, 479, 116–134.
Qin, Bo., Qianhong, Wu., Zhang, L., Farràs, O., & Domingo-Ferrer, J. (2012). Provably secure threshold public-key encryption with adaptive security and short ciphertexts. Information Sciences, 210, 67–80.
Ge, Wu., Guo, F., & Susilo, W. (2019). Generalized public-key cryptography with tight security. Information Sciences, 504, 561–577.
Beiter, M., Mont, M. C., Chen, L., & Pearson, S. (2014). End-to-end policy based encryption techniques for multi-party data management. Computer Standards & Interfaces, 36, 689–703.
Ding, W., Yan, Z., & Deng, R. H. (2017). Encrypted data processing with Homomorphic Re-Encryption. Information Sciences, 409–410, 35–55.
Wang, X. A., Xhafa, F., Cai, W., Ma, J., & Wei, F. (2016). “Efficient privacy preserving predicate encryption with fine-grained searchable capability for Cloud storage.” Computers and Electrical Engineering, 56, 871–883.
Kavin, B. P., & Ganapathy, S. (2019). A secured storage and privacy- preserving model using CRT for providing security on cloud and IoT-based applications. Computer Networks, 151, 181–190.
Alqahtani, F., Al-Makhadmeh, Z., Tolba, A., & Said, O. (2020). TBM: A trust-based monitoring security scheme to improve the service authentication in the Internet of Things communications. Computer Communications, 150, 216–225.
Maitra, T., Obaidat, M. S., Giri, D., Dutta, S., & Dahal, K. (2019). “ElGamal cryptosystem-based secure authentication system for cloud-based IoT applications.” IET Networks, 8(5), 289–298.
Shen, M., Ma, B., Zhu, L., Du, X., & Xu, K. (2019). Secure phrase search for intelligent processing of encrypted data in cloud-based IoT. IEEE Internet of Things Journal, 6(2), 1998–2008.
Ma, M., He, D., Fan, S., & Feng, D. (2020). Certificateless searchable public key encryption scheme secure against keyword guessing attacks for smart healthcare. Journal of Information Security and Applications, 50, 1–9.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of Interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Pradeep, S., Muthurajkumar, S., Ganapathy, S. et al. A Matrix Translation and Elliptic Curve Based Cryptosystem for Secured Data Communications in WSNs. Wireless Pers Commun 119, 489–508 (2021). https://doi.org/10.1007/s11277-021-08221-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08221-9