Abstract
Motivated by today’s huge volume of data that needs to be handled in secrecy, there is a wish to develop not only fast and light but also reliably secure cryptosystems. Chaos allows for the creation of pseudo-random numbers (PRNs) by low-dimensional transformations that need to be applied only a small number of times. These two properties may translate into a chaos-based cryptosystem that is both fast (short running time) and light (little computational effort). What we propose here is an approach to generate PRNs—and consequently digital secret keys—that can serve as a seed for an enhanced chaos-based cryptosystem. We use low-dimensional chaotic maps to quickly generate PRNs that have little correlation, and then, we quickly (“fast”) enhance secrecy by several orders (“reliability”) with very little computational cost (“light”) by simply looking at the less significant digits of the initial chaotic trajectory. This paper demonstrates this idea with rigor, by showing that a transformation applied a small number of times to chaotic trajectories significantly increases its entropy and Lyapunov exponents, as a consequence of the smoothing out of the probability density towards a uniform distribution.
Similar content being viewed by others
1 Introduction
The secrecy in chaos-based cryptosystems relies on mathematical transformations that generate a trajectory whose correlation decays rapidly. The correlation of chaotic trajectories will always decay to zero after a sufficiently long time. This is due to the mixing property that allows nearby points to be quickly mapped anywhere in the transformation domain, and due to the sensibility to the initial condition chaotic transformations have. In fact, the speed of correlation decay and the sensibility to the initial conditions quantified by the Lyapunov exponent are intimately connected [1]. A chaotic system with a very large positive Lyapunov exponent is thus desirable for cryptography [2], since it allows for very rapid decay of correlations. Moreover, chaotic signals can be generated by low-powered, small area and simple integration as well as analog circuits operating in very large frequency bandwidths.
Cryptosystems need to perform heavy calculations. For example, chaos-based block ciphers [3,4,5] such as those that encrypt images, movies and audio employ a series of complex mathematical transformations over too many bits of information. If one wants a light cryptosystem that can be run in any portable devices or that can be considered even for massive streaming, the use of real numbers with higher precision should be avoided. To improve on the performance of chaos-based cryptosystems, the underlying chaotic transformation has been discretized by considering transformations operating on an integer domain. Discretization can preserve important ergodic properties as the mixing property and the sensibility to the initial conditions, but might also create spurious periodic cycles of low period [4, 6], which result in correlations weakening the security of cryptosystems that rely on these transformations. Even chaotic transformations (such as the Bernoulli shift map) acting on real numbers with finite resolution might create spurious periodic cycles due to numerical errors.
With recent advances, it is relatively easy today to perform numerical computation with arbitrary precision, and thus, current efficient cryptosystems can rely on maps with real arithmetics of higher precision. However, any meaningful encoding of the chaotic trajectory that allows decoding, such as those used to create a pseudo-random number (PRN) generator or binary secret keys, would be strongly correlated with the most significant digits of the trajectory. To create a stream cipher based on chaos [7], where a binary information stream is encoded by XOR transformation to a binary secret key created by encoding a chaotic trajectory, Gerard Vidal Cassanya [8] has proposed the use of the less significant digits of a trajectory obtained from a higher-dimensional chaotic system of ODEs to create the binary secret key. The idea of using the less significant digits of chaotic trajectories has appeared before in the work of Ref. [9]; however, it was in Ref. [8] (and other previous patent applications cited within) that less significant digits were taken by a transformation that this work claims to be optimal to support a fast, light and reliable cryptosystem.
Inspired by today’s huge volume of data that needs to be handled in secrecy, there is a desire to develop not only fast (quick run time) and light (little computational cost) but also reliable (highly entropic, sensitive to the initial conditions, low correlation) cryptosystems. An important aspect of a cryptosystem is its initialization. For example, one might employ a PRN to choose parameters. Secret keys, which can be created from PRNs, are also used to encrypt the information and represent a core operation in any cryptosystem. Any innovative invention that creates reliable PRNs or secret keys with optimized use of computational resources will contribute tremendously to a world that wants to communicate massive amounts of information, but securely. PRNs are not only important for secrecy in communication. It is also fundamental to the functioning of several autonomous machines, toys, and they are essential for several numerical algorithms. This work demonstrates that looking at the less significant digits of chaotic trajectories is indeed a pathway for the creation of fast, light and reliable PRNs.
The work of Ref. [10] has analyzed the dynamics and the statistical properties of the deep-zoom transformation to a chaotic trajectory, a transformation that takes up the less significant digits of a real number. This transformation applied to the logistic map regarded as the k-logistic map [10] was defined by the less significant digits located at k digits to the right of the decimal point. It was shown that a PRN based on the k-logistic map has strong properties regarding statistical randomness tests DIEHARD and NIST, and thus demonstrating from a statistical perspective that the k-logistic map can sustain secure cryptosystems. The k-logistic map takes advantage of not only having trajectory points with arbitrarily large precision, and thus within principle no detectable spurious cycle, but also on hiding the information about the most significant digits, which could reveal information about the algorithm behind the generation of the PRNs.
The interest in the present work is to understand how the deep-zoom transformation changes a particular map ergodic properties such as its space partition, density measure, Lyapunov exponent, Topological, and Shannon’s entropy. Our results, mostly illustrated by how the deep-zoom transformation operates into the Logistic map, are valid to generic 1D chaotic maps or a set of numbers generated by any other process. The deep-zoom transformation is a complementary operation to chaos-based cryptosystem: We first quickly generate a chaotic trajectory by a low-dimensional map, and then, we use the deep-zoom transformation to quickly and lightly enhance security. Our work thus proposes a pathway for the creation of a fast, light and reliable chaos-based cryptosystem.
Our first result is to demonstrate that the k-deep-zoom (k-DZ) transformation to a point x is mathematically equivalent to iterating for k times the decimal shift map (DSM) [11, 12]. This map is well known, and it is since decades considered to be a mathematical toy model to demonstrate how a shift into the less significant digits results in strong chaos. Despite its tremendous appeal due to the nice way this map deals with decimal digits, scientists working with encryption based on nonlinear transformations have focused their attention on other more known similar maps, such as the Bernoulli shift map [13] or the Baker’s map, instead of the DSM. The main difference is whereas the DSM operates by shifting the decimal numbers, Bernoulli shift and Baker’s map operate by shifting the binary sequence encoding the real numbers of the trajectory.
Then, we demonstrate that by applying the k-DZ transformation only once to generic chaotic trajectories, the mapped trajectories will approach a uniform invariant measure for a sufficiently large but in practice small k, thus requiring much less computational effort to create numbers with uniform statistics, a standard requirement for reliable PRNs. The convergence to the uniform invariant measure also dictates the convergence of the Lyapunov exponent (LE) to the topological and Shannon’s entropy of the mapped trajectories, indicating that the transformed points have achieved the largest sensibility to the initial conditions that is possible. Having a trajectory for which the level of chaos is the same as the level of entropy means that uncertainty about the past and the future is as large as one could wish for the particular chaotic map being considered. Moreover, all these quantities are linearly proportional to k, thus implying that randomness (higher entropy) and the sensibility to the initial conditions (large LE) can be trivially increased by the resolution with which a trajectory is observed, and not by increasing the dimension of a system or by considering higher-order iterates of the map onto itself, operations that would require computational resources.
Throughout this paper, we will show how this map amazing properties applied to any 1D chaotic systems with finite probability measure allows for a clear path to the creation of fast (quick run time, low number of iterations), light (little computational effort, low dimension) and reliable (uniform statistics, strongly sensitive to the initial conditions, high entropy) pseudo-random numbers or symbolic secret keys, thus supporting fast, light and reliable chaos-based cryptosystems.
Enhanced sensitivity to the initial conditions and increase in entropy is achieved as a consequence that the k-DZ transformation smooths out the probability density of an arbitrary initial distribution of numbers transforming it into a uniform distribution. Highly entropic numbers with high sensitive to the initial conditions give support to reliable cryptosystems. Chaotic maps can produce numbers faster than inbuilt pseudo-random number generators, thus giving support to a cryptosystem that is fast. Moreover, these maps (e.g., as the Logistic map) can be low-dimensional, which reduces further computational requirements, giving support to a cryptosystem that is light.
2 The k-deep-zoom (k-DZ) transformation, its equivalence to the Decimal shift map (DSM), and the logistic map
Given a 1D map f(x) defined in a domain [a, b] and producing an orbit \({\mathcal {O}}(x_0)=\{x_0, x_1,\ldots , x_t\}\) generated by the initial condition \(x_0\), with a given invariant density \(\rho (x)\) and probability measure \(\mu (x)\), such that for an interval \(\epsilon \in [a,b]\) we have that \(\mu (\epsilon )=\int _{x \in \epsilon }\rho (x)\mathrm{d}x\), the k-DZ transformation \(\phi _k(x)\) was defined in [10] by
where \(\lfloor \) \(\rfloor \) stands for the floor function. In Ref. [10], and motivated mostly for practical reasons, a parameter L was considered which set the number of less significant digits for the function \(\phi _{k}(x)\). Here, we drop this definition and assume that \(L \rightarrow \infty \), or is a large number.
This map can be analogously described by
The DSM map is defined by
and its k-folded version (the k-th iteration of D) which we represent by \(D^k\) is basically
which is exactly equal to Eq. (3). Thus, the k-fold DSM map is mathematically equal to the k-DZ transformation.
To illustrate the action of the DZ transformation, given the value \(x=0.3923481\), then \(\phi _{k=2}(x)= 0.23481.\)
2.1 The k-DZ transformation and other maps in literature
The idea of using a cryptosystem based on mod transformations that extract the less significant digits of real numbers generated by chaotic systems was to the best of our knowledge first proposed in Ref. [9]. Given a real number \(x_n\) generated by a chaotic system (discrete or continuous), this work has proposed cipher x by
with A and S representing arbitrary constants.
Equation (4) can be seen as a particular case of Eq. (6), but not of Eq. (3) because the k-DZ transformation introduces the extra parameter k.
Our work shows when this parameter can generate suitable PRNs. However, in the work of Ref. [9], only the case for \(A=10^7\) and \(S=256\) was studied, and without the rigour and deepness presented in the present work to study the ergodic and dynamic manifestations of these transformations. The choice of \(S=256\), which turns the map of Eq. (6) not equivalent to the DSM map, was made to organize the number \(R_n\) into a two-dimensional gray-scale image for further processing. This choice, however, is not optimal for the security of the encryption, measured in terms of entropy and sensibility to the initial conditions. The optimal choice, demonstrated further, is obtained for \(S=1\), as in Eqs. (3) or (5). The choice made of A as an arbitrary constant is also per se not always optimal to extract the less significant digits, unless this arbitrary constant is of the form \(A=10^k\), as in Eq. (3).
2.2 The Logistic map
The logistic map has been extensively studied over the past years [14]. Since it is a well-know system and that produces typical chaotic behavior [15], we focus the application of the k-DZ transformation to trajectory points being iterated by the logistic map for typical initial conditions and that produce chaotic sets when they are stable, which we refer as the k-logistic map, adopting previously defined terminology. Worth mentioning that the probability of finding a chaotic orbit for a randomly chosen parameter by any typical initial condition in the Logistic map is finite [16]. So randomly picked parameters (within the allowed domain) and randomly picked initial conditions will likely generated a chaotic attractor. It is described by
where \(x_t \in [0,1]\). In Eq. (7), \(x_t \in \mathfrak {R}\), and as such each trajectory point is assumed to have infinite precision. However, in practice, \(x_t\) has finite precision, but this does not prevent one from solving Eq. (7) by numerical means. The shadowing lemma [17] guarantees that numerical solutions of this map are stable even if trajectory points have a finite resolution, in the sense that the numerical trajectory will remain close to a true trajectory for a very long time, this time depending on the resolution of the trajectory considered.
3 Analysis
3.1 Phase space, partition, and topological entropy
Equation (2) is useful because it provides the key to calculate the location of the partition points, where the map becomes discontinuous. The points of discontinuities happen at the boundaries created by the mod function, so at multiples of \(10^{-k}\), more specifically at \(m10^{-k}\), for \(m \in {\mathbb {N}}\) and \(m \le 10^k\). There will be then \(10^k\) discontinuous intervals. Figure 1 shows the original logistic map with b=4 (\(k=0\), left panel), and the corresponding k-DZ transformation for \(k=1\) (second panel to the right), \(k=2\) (third panel to the right), and \(k=3\) (right-most panel).
The k-DZ transformation applied to the trajectory points of the Logistic map. From left to right panels, for \(k=0\), \(k=1\), \(k=2\), and \(k=3\) by using Eq. (3)
So, the set containing the points \(x^*\) where discontinuities appear can be obtained by solving the following equation:
We can define a topological entropy of the k-DZ transformation, which is an upper bound for the Shannon entropy, by the Boltzmann entropy of gas measuring the entropy of it in terms of the number of observable states. Here, we can define the states as being the fall of a trajectory point into an interval within the partition provided by Eq. (8). Regardless of the value of b, and actually regardless of which kind of 1D chaotic map is used, this number is given by the number of partition points of the k-DZ transformation and it is equal to \(10^k\), which is also the number of possible symbolic sequences that the k-logistic map produces. It is given by
It is useful to compare this result with the topological entropy of the original logistic map, defined in terms of the number of subintervals in its generating Markov partition, and equal to \(2^o\), where \(o \in {\mathbb {N}}\) is the order of the partition representing the resolution of the subintervals composing the partition (measuring \(~2^{-o}\) in length). That results in that \(H_T=o\ln {(2)}\). Here, we see an advantage of the use of the k-logistic map to produce efficient pseudo-random numbers in a light fashion, so without requiring too expensive computational resources. Assuming o and k to be of the same order, the topological entropy of the k-logistic map be \(\ln {(10)}/\ln {(2)}\) larger than that of the logistic map.
It is also worthwhile to compare the result in Eq. (9) with the topological entropy, \(H_T^{(S)}\), obtained by applying Eq. (6). Defining \(A=10^k\), we obtain that the topological entropy equals \(H_T^{(S)} = k \ln {(10)} - \ln {(S)}\) for Eq. (6). Thus, the entropy achieved in Eq. (9) for the k-DZ transformation in Eq. (3) can only be achieved by applying Eq. (6) to that same chaotic set if \(S=1\).
3.2 k-logistic map probability density
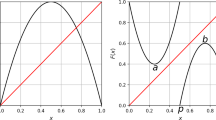
One of the most important characteristics of a good PRN generator is that successive output values of it, say \(u_0,u_1,u_2,\ldots \) are independent random variables from the uniform distribution over the interval [0, 1]. It was shown in [10] that as k increases the probability distribution of the map becomes more and more uniform. This is reproduced in Fig. 2, in terms of the histogram (frequency) analysis. As can be seen in this figure, for \(k=0\) (a) this distribution is not uniform as it is to be expected from the logistic map with b=4, with a high probability of finding points close to 1 and 0. As k grows with \(k=1\), \(k=2\), and \(k=3\), the distribution tends to become increasingly uniform, as can be observed in the Fig. 2b. In (c), we show a magnification of (b) for the region close to zero.
Frequency distribution curves for a the original logistic map, b the \(k-\)-logistic map with \(k=1\), \(k=2\) and \(k=3\) and parameter \(b=4\). The horizontal axis shows the \(x_t \in [0, 1]\) (500 bins), and the vertical axis shows the frequency of the \(10^4\) values discarding the first \(10^3\) transient values. The curves represent the mean and standard deviation (shaded error bar) for sequences generated over 100 random initial conditions. c The inset plot depicts a zoom on the windows \(x \in [0, 0.03]\) for these 4 plots
3.3 The natural invariant measure of the k-DZ transformation and its Shannon’s entropy
To calculate the asymptotic Lyapunov exponent of the k-DZ transformation, which is independent on the choice of the chaotic map, we notice that the k-DZ is piecewise linear, wherein each partition sub-interval the map has a constant derivative function. Arranging the values of \(x^*(i)\) in Eq. (8) in a ranking of crescent order and indicating it by, i.e., \(x^*(m) \equiv x^*_{i}\) such that \(x^*_{i+1}>x^*_{i}\), each partition subinterval comprises the interval
for \(i \in {\mathbb {N}}\) and \(i=[0,1, \ldots , 10^k-1]\).
The derivative of the piecewise-linear map for each sub-interval \(d_i\) can be calculated by
since \(\phi _k(d_i) = 1\), where \(| d_i |\) represents the length of the sub-partition \(d_i\).
The evolution of an arbitrary initial probability measure to a 1D nonlinear transformation is dictated by the Perron–Frobenius operator. For piecewise linear systems, the Perron–Frobenius operator can be cast in terms of a linear system of equations operating in each subinterval of the map partition. The k-DZ transformation takes as the initial measure generated by the nonlinear logistic map and then applies k times the DSM. If we assume that the measure in each subinterval of the k-DZ is uniform (which initially will be not) and we represent it by the component \([{\mathbf \mu }]_i\) of the vector \({\mathbf \mu }\) (\(i=\{1, \ldots ,n\}\)) with \(n= 10^{k}\), and we define the density in each interval as given by
an equation for the evolution of the non-normalized density at iteration t can be obtained [18].
where the square matrix \({{\mathcal {Z}}}\) with component \([{{\mathcal {Z}}}]_{ij}\) is the reciprocal of the absolute value of the slope of the map taking the measure from the interval j to the interval i and can be defined by a matrix with equal rows as
Equation (13) represents how the measure evolves concerning only 10\(^{k}\) intervals are valid if the measure and the density are uniform for every sub-partition \(d_i\) since it has been derived from the continuous Perron–Frobenius operator integrated over intervals where the measure was assumed to be constant. If the initial measure is not uniform for each subpartition interval, as it is the case since the initial measure was generated by the logistic map, we either should consider the continuous operator (effectively described by an infinite dimension matrix) or alternatively, we can adopt a much simpler strategy. We take Eq. (13) and study it in the limit, when \(t \rightarrow \infty \).
Defining the vector \({\mathbf {d}}=\{d_1,d_2,\ldots ,d_n\}\) and the diagonal matrix \(D={\mathbb {I}} {\mathbf {d}}\), the element \([]_{ij}\) of the matrix \(D{{\mathcal {Z}}}D^{-1}\) represents the percentage of the measure in the interval \(d_j\) that goes to the interval \(d_i\). The matrix \({{\mathcal {Z}}}\) has equal rows because the piecewise equivalent of the k-logistic map takes measure from each interval to all others with the same proportion in each of the intervals \(d_j\).
The k-logistic map state space. From left to right panels are shown \(k=0\), \(k=1\), \(\ldots \), \(k=7\) using parameter \(b = 4 \). The horizontal and vertical axes show the state space of \(x^k_t\) against \(\phi _k(f(x_t))\). Each orbit contains \(10^5\) points starting from random initial conditions
The k-logistic map state space. From left to right panels are shown \(k=0\), \(k=1\), \(\ldots \), \(k=7\) on region \(b \in [3.6, 4]\). The horizontal and vertical axes show the state space of \(x^k_t\) against \(\phi _k(f(x_t))\). Each orbit contains \(5\times 10^3\) points starting from random initial conditions
The equilibrium point of Eq. (13) is obtained when
which means that the time invariant density is a normalized eigenvector of \({{\mathcal {Z}}}\).
The matrix \({{\mathcal {Z}}}\) is a stochastic matrix, since it is a non-negative matrix and the sum of all elements in a row totals 1. This is easy to see since
The Perron–Frobenius theorem guarantees that a square stochastic matrix has a unique dominant real unitary eigenvalue, with all other eigenvalues smaller than 1. This means that the density of the k-DZ transformation in the limit of \(k \rightarrow \infty \) is natural (it is unique), regardless of the initial probability measure that is fed into the k-DZ transformation. The natural density can be recovered by proper normalization dividing \({\mathbf \rho ^*}\) by \(\sum _i [{\mathbf \rho ^*}]_id_i\) so that the physical natural density in each interval is given by
This is to guarantee that the density produces the natural measure by Eq. (12).
It is also easy to see that the unique unitary eigenvalue has associated with it a uniform eigenvector with all components equal to a constant value c: \({\mathbf \rho }^* = [c\, c\, c\, \ldots , c]^\mathrm{T}\), so the piecewise k-DZ transformation has a uniform density given by
This leads us to an invariant natural measure in each interval that equals the Lebesgue measure of the interval, and thus,
So, for sufficiently large k, it is to be expected that the k-logistic map will have a uniform natural invariant density, although the density of the logistic map is not uniform for each interval. In practice, this sufficiently large number is around k=4, when this map generates PRNs with all the good statistical characteristics for security [10]. Being invariant means that any initial probability measure will eventually evolve to the same invariant measure. Thus, the reliability of the security for the PRNs generated by the k-DZ transformation is substantially more dependable on the properties of the DSM, than on the statistical properties of the chaotic set of points being iterated by the k-DZ transformation, or also on the chaotic map considered to initially generate the chaotic trajectory to be fed into the k-DZ transformation. Since the invariant measure of the k-logistic map is constant (for sufficiently large k), this means that any encoding supported by the partition defined in Eq. (8) will produce equiprobable symbols, this rendering cryptanalysis based on frequency statistics to be inappropriate.
The asymptotic Shannon’s entropy of the k-DZ transformation is therefore equal to the topological entropy:
3.4 The Lyapunov exponent of the k-DZ transformation
The Lyapunov exponent (LE) of the k-DZ transformation can always be calculated regardless of the chaotic map being used as the generator of the initial measure. This is so because the map is piecewise linear with constant derivative everywhere (except the partition points). The Lyapunov exponent can be calculated by
where \(\mathrm{d}\mu =\rho (x)\, \mathrm{d}x\), represents the invariant measure of the k-DZ transformation.
The chaotic map has its own domain of validity. This domain must be normalized to fit within the domain of the k-DZ transformation. For the logistic map, the domain is [0, 1], the same as the domain of the k-DZ transformation. Therefore, its LE is equal to
So we see that for a sufficiently large k, the k-DZ transformation produces a LE that approaches the topological entropy which is also equal to Shannon’s entropy. A light cryptosystem that does not require much computational effort demands the use of transformations that can be as entropic as possible and with the largest as possible sensibility to the initial conditions (which implies in a quick decay of correlation).
When comparing the LE of the k-DZ transformation in Eq. (3) [result in Eq. (20)] with the LE of the transformation Eq. (6) (proposed in Ref. [9]), assuming \(A=10^k\), we notice that Eq. (6) can be equivalently written as:
which can be rewritten as:
where \(\Phi (x_n)=\frac{10^k}{S}x_n, \hbox { mod 1}\). Noticing that the LE of the function \(\Phi (x_n)\) is the same as the one obtained if \(\Phi (x_n)\) is multiplied by a constant, then the LE of Eq. (6) is equal to
Thus, the LE of Eq. (6) is only equal to the one of Eq. (3), if \(S=1\). As a result of Eq. (24), we have assumed that the speed of convergence of the probability density measure [19] of Eq. (6) is the same as the one of Eq. (3). This is to be expected since the second largest eigenvalue of the matrix \({{\mathcal {Z}}}\) regulating the evolution of the density measure for Eq. (3) is the same as the one for this matrix regulating the evolution of the density measure for Eq. (6), and both are equal to zero.
3.5 Enhancement of sensibility to the initial conditions of the k-logistic map
The LE of the k-DZ transformation does not depend on the choice of the chaotic map generating the measure. It is nevertheless interesting to understand how much chaos is enhanced by the application of the k-DZ transformation into a chaotic map. Considering this chaotic map to be the logistic map [Eq. (7)], we then want to understand how much chaos is enhanced if the DZ transformation with \(k=1\) is applied not to the trajectory points generated by the logistic map, but to the map itself. So we calculate the Lyapunov exponent of the map \(\phi _{k}(f(x_t))\), whose state space (\(\phi _{k}(f(x_t)) \times x_t\)) is shown in Fig. 3. Additionally, Fig. 4 shows a colored version of this previous picture for parameters in region \(b \in [3.6, 4]\).
This map is described by
Its LE can be calculated by
where \(\mathrm{d}\mu =\rho (x)\, \mathrm{d}x\) now represents the measure of the logistic map.
The first derivative of the map in Eq. (25) is
whereas its density for \(b=4\) is given by
Placing Eqs. (27) and (28) in Eq. (26) and integrating over the map domain (\(x \in [0,1]\)), we obtain that
since
So the first thing to notice is that the LE of the map in Eq. (25) is equal to the LE of the 1-logistic map plus the LE of the original logistic map for \(b=4\) (which is equal to \(\ln {(2)}\)). This tells us that when creating a cryptosystem based on a chaotic map, more entropy and sensibility to the initial conditions can be achieved by a simple inspection to the least k significant digits, instead of doing more iterations in the chaotic map generating the initial chaotic sequence.
This analysis can be easily extended to the logistic map operating under any parameter b that produces chaotic motion.
The Lyapunov exponent of the map in Eq. (25) can be calculated using the time approach by
which lead us to
and finally to
where \(\lambda _0(b)\) is just the Lyapunov exponent of the logistic map for the parameter b. Thus, here it is obvious that the gain for sensibility to the initial conditions is trivially achieved by just choosing a sufficiently large k.
4 Pseudo-random numbers and symbolic secret keys
The output of the k-DZ transformation \(\phi _k(x)\) generates real points in the unit interval. These points have a uniform invariant density, are highly entropic, and have high sensitivity to the initial conditions. Moreover, their security analysis was already analyzed in Ref. [10] (specifically, Tables II and III), showing high-quality pseudo-random numbers for \(k\ge 4\) through statistical randomness tests such as DIEHARD [20] and NIST [21]. These values have all the properties wished for a PRN.
Another strategy we can employ to generate PRNs and that directly renders the creation of digital secret keys is by means of the symbolic representation of the trajectory of the k-DZ transformation. Thus, a partition that is not the natural partition of the k-DZ transformation needs to be considered. This natural partition is given by \({\varvec{d}}\) whose borders are defined by Eq. (8). Then, for a given k, there will be \(10^k\) symbols for the natural partition. The point \(\phi _k(x_i) \in [d_i,d_{i+1}]\) is encoded by the i-th symbol of the alphabet (\(i=\{0,1,\ldots ,10^k-1\}\)), represented by \(s_i\). A transformed trajectory of length L represented by \(\{\phi _k(x_1), \phi _k(x_2), \ldots , \phi _k(x_L)\}\) will have the symbolic representation \({\varvec{s}} = \{s_1, s_2, \ldots , s_L\}\), where \(s_i \in [0,10^k-1]\). The vector \({\varvec{s}}\) fully represents the information about the location of the points \(x_i\) being mapped (within the resolution of the partition cells), and therefore should be avoided for the creation of the secret key. The partition to create a secret key should have a minimal number of intervals, for example a binary partition where \(\phi _k(x_i) < 0.5\) is encoded by ‘0’ and \(\phi _k(x_i) \ge 0.5\) is encoded by ‘1’. In this way, points within \(x_i \in [0,1]\) will be encoded with equal probabilities for ‘0’ and ‘1’.
5 Conclusions
Cryptography relies on the application of several transformations to eliminate all existing correlations between the message and its ciphered version. A preliminary requirement for achieving this relies on the use of highly entropic and non-correlated pseudo-random numbers. The sensitivity to the initial conditions property chaotic systems have is the key to this goal. The interest today is to be able to accomplish such a task for reliable encryption but by relying on transformations that require little computational effort (light) and quick running time (fast).
In this work, we characterize the properties of the so-called the k-Deep Zoom (k-DZ) to potentially support reliable cryptosystems that uses pseudo-random numbers or secret keys that were created fast and lightly. Besides the decimal shift map (DSM) is not conceptually equivalent to the k-DZ, we show that the k-DZ is mathematically equivalent to the DSM map iterated k times. More than that, we show that the k-fold DSM can be rewritten into a form completely equivalent to the k-DZ transformation. So all the good properties of the DSM map such as uniform statistics, high entropy, and sensibility to the initial conditions are inherited by the k-DZ. There is a semantic difference between both maps. Whereas the k-DZ transformation effectively represents an algorithm that simply extracts the less significant digits of a real number, the DSM is a map that transforms a point into another point. This semantic interpretation of the DZ-transformation can be in the future exploited for the creation of dedicated electronic chips operating at the hardware level that only work with less significant digits, thus potentially bringing the encryption process to the physical level. We show that the entropy and the Lyapunov exponent are linearly proportional to k. This means that the trivial and light task of peeking onto the sequence of less significant digits positioned k digits to the decimal floating-point is sufficient to drastically increase the entropy and therefore the uncertainty past and future numbers, at a minimal computational cost.
Several of the properties of the k-DZ transformation depend only on the map itself, not on the chaotic system being considered as the generator of the original trajectory being encoded, or any other set of numbers being generated by any other process (e.g., stochastic processes). Thus, one might wonder why to use the k-DZ transformation into a chaotic set of numbers after all? The reason is that chaotic trajectories have several advantages. They are easy to be generated and do not require the use of higher-dimensional systems, in both digital or analog domains, they require less algorithmic complexity, less-power electronics, less CPU dedication and can be generated at impressive large bandwidths. Chaos, however, is deterministic and correlation does decay quickly, but not as quickly as one would wish. The additional application of the k-DZ transformations to chaotic trajectories fast and lightly enhances the already existing wished properties of chaos to cryptography, a transformation that optimizes essential ingredients to a secure cryptosystem, but with minimal computational effort.
Our strategy to create pseudo-random numbers or secret keys requires the use of a chaotic system whose simulated trajectory is guaranteed to be chaotic for a long period, and that can be additionally generated using minimal computational resources. For this reason, the logistic map is a good candidate. The k-DZ transformation is then applied a single time to this stable chaotic trajectory. Our claim is that this strategy quickly generates secure and light PRNs. Another strategy to generate secure PRNs, which might increase the computational cost to some extent, was proposed in Ref. [13], where an approximate true trajectory of the Bernoulli map is calculated directly using real algebraic numbers. It would be interesting to study the performance of PRNs (in terms of speed, weight, and reliability) that are either generated by applying the k-Deep Zoom to the logistic map or by the true trajectory of the Bernoulli map.
We must conclude by reinforcing the idea that our main results do not require the use of the logistic map. Any other map could be used, for example we could use as the initial chaotic trajectory that serves as the input to the k-DZ transformation, one that is created by the intertwining logistic map (ILM) [22]. This map has attracted attention in the chaos-based crypto-community because it expands the key space, produces a density measure that seems to be uniform (yet to be demonstrated), and that could potentially have robust chaotic attractors (Ref. [23]) (yet to be demonstrated), systems that produce chaotic attractors that cannot be replaced by a periodic attractor by a parameter perturbation. However, its use to generate chaotic trajectories as the input data to our k-DZ transformation would need to be done with caution not to compromise our promise to the potential creation of a fast, light and reliable cryptosystem. The ILM is a three-dimensional map (higher-dimensional), with a trigonometric transformation (sinusoidal) (thus not light). The Lyapunov exponent of the ILM map remains below 0.5, whereas the Bernoulli shift map has as its Lyapunov exponent the value of \(\ln {(2)}\). It is worth mentioning that the Lyapunov exponent of the trajectory obtained from the one obtained from the k-DZ transformation applied to a trajectory of the logistic map is proportional to \(k \ln {(10)}\). Finally, to the best of our knowledge the results that the ILM produces a uniform density measure is not demonstrated, whereas in this work we rigorously demonstrated that any chaotic trajectory can be transformed by the k-DZ transformation in order to produce an invariant uniform distribution. Moreover, the approach to the invariant uniform distribution is rapidly, only requiring a single iteration of the k-DZ transformation.
References
Slipantschuk, J., Bandtlow, O.F., Just, W.: On the relation between Lyapunov exponents and exponential decay of correlations. J. Phys. A Math. Theor. 46(7), 75101 (2013)
Pisarchik, A.N., Zanin, M.: Chaotic map cryptography and security. Int. J. Comput. Res. 19(1), 49 (2012)
Fridrich, J.: Image encryption based on chaotic maps. In: 1997 IEEE International Conference on Systems, Man, and Cybernetics. Computational Cybernetics and Simulation, vol. 2, pp. 1105–1110. IEEE (1997)
Farajallah, M., El Assad, S., Deforges, O.: Fast and secure chaos-based cryptosystem for images. Int. J. Bifurc. Chaos 26(2), 1650021 (2016)
Zhang, W., Wong, K.W., Yu, H., Zhu, Z.L.: An image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Commun. Nonlinear Sci. Numer. Simul. 18(8), 2066 (2013)
Garasym, O., Taralova, I., Lozi, R.: New nonlinear CPRNG based on tent and logistic maps. In: Complex Systems and Networks, pp. 131–161. Springer (2016)
Vidal, G., Baptista, M.S., Mancini, H.: A fast and light stream cipher for smartphones. Eur. Phys. J. Spec. Top. 223(8), 1601 (2014)
Cassanya, G.V.: Method for generating a pseudorandom sequence, and method for coding or decoding a data stream. Method for generating a pseudorandom sequence, and method for coding or decoding a data stream. US Patent 9,654,289 (2017)
Lee, P.H., Pei, S.C., Chen, Y.Y.: Generating chaotic stream ciphers using chaotic systems. Chin. J. Phys. 41(6), 559 (2003)
Machicao, J., Bruno, O.M.: Improving the pseudo-randomness properties of chaotic maps using deep-zoom. Chaos Interdiscip. J. Nonlinear Sci. 27, 53116 (2017)
Graham, R.L., Knuth, D.E., Patashnik, O., Liu, S.: Concrete mathematics: a foundation for computer science. Comput. Phys. 3(5), 106 (1989)
Hilborn, R.C., et al.: Chaos and Nonlinear Dynamics: An Introduction for Scientists and Engineers. Oxford University Press on Demand (2000)
Saito, A., Yamaguchi, A.: Pseudorandom number generator based on the Bernoulli map on cubic algebraic integers. Chaos Interdiscip. J. Nonlinear Sci. 28(10), 103122 (2018)
May, R.M.: Simple mathematical models with very complicated dynamics. Nature 261(5560), 459 (1976)
Ott, E.: Chaos in Dynamical Systems. Cambridge University Press, Cambridge (2002)
Thunberg, H.: Periodicity versus chaos in one-dimensional dynamics. SIAM Rev. 43, 3 (2001)
Grebogi, C., Hammel, S.M., Yorke, J.A., Sauer, T.: Shadowing of physical trajectories in chaotic dynamics: containment and refinement. Phys. Rev. Lett. 65(13), 1527 (1990)
Alligood, K., Sauer, T., Yorke, J.: Chaos: An Introduction to Dynamical Systems. Textbooks in thematical Sciences. Springer, New York (2012)
Boyd, S., Diaconis, P., Parrilo, P., Xiao, L.: Fastest mixing Markov chain on graphs with symmetries. SIAM J. Optim. 20(2), 792 (2009)
Marsaglia, G.: The Marsaglia random number CDROM, with the DIEHARD battery of tests of randomness. http://www.stat.fsu.edu/pub/diehard (1998)
Rukhin, A., Soto, J., Nechvatal, J., Smid, M., Barker, E., Leigh, S., Levenson, M., Vangel, M., Banks, D., Heckert, A.: NIST Special Publication 800-22: a statistical test suite for random number generator for criptographic applications. Tech. rep, National Institute of Standards and Technology, Gaithersburg, MD, USA (2001)
Wang, X., Xu, D.: Image encryption using genetic operators and intertwining logistic map. Nonlinear Dyn. 78, 2975 (2014)
Banerjee, S., Yorke, J.A., Grebogi, C.: Robust chaos. Phys. Rev. Lett. 80, 3049 (1998)
Acknowledgements
J. M. acknowledges a scholarship from the National Council for Scientific and Technological Development (CNPq Grant #155957/2018-0) and the São Paulo Research Foundation (FAPESP #2020/03514-9). O. M. B. acknowledges support from CNPq (Grant #307897/2018-4) and FAPESP (Grant #16/18809-9).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Machicao, J., Bruno, O.M. & Baptista, M.S. Zooming into chaos as a pathway for the creation of a fast, light and reliable cryptosystem. Nonlinear Dyn 104, 753–764 (2021). https://doi.org/10.1007/s11071-021-06280-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-021-06280-y