Abstract
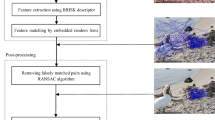
Copy-move (or copy-paste or cloning) is one of the most common image forgeries, wherein one or more region are copied and pasted within the same image. The motivations of such forgery include hiding an element in the image or emphasizing a particular object. Copy-move image forgery is more challenging to detect than other types, such as splicing and retouching. In recent years, keypoint based copy-move forgery detection, which extracts image keypoints and uses local visual features to identify duplicated regions, exhibits remarkable performance with respect to memory requirement and robustness against various attacks. However, these approaches usually have poor detection ability when copy-move forgeries only involve small or smooth regions. Moreover, they cannot always effectively deal with multiple copy-move forgeries. To tackle these challenges, we propose a robust and effective multiple copy-move forgeries detection and localization method through adaptive keypoint extraction, robust local feature representation, and offsets clustering based post-processing. Firstly, we develop a new image keypoint detector, named generic features from accelerated segment test, and extract adaptively the uniform distribution keypoints from the forged image by employing the adaptive-thresholding and non-maximum suppression. Then, we introduce fast quaternion polar complex exponential transform to describe the image keypoints compactly and distinctively, and utilize the KD tree based K-nearest neighbor matching to find possible correspondences. Finally, the falsely matched pairs are removed by employing the offsets information based candidate clustering, and the duplicated regions are localized using RANSAC and ZNCC algorithm. We conduct extensive experiments to evaluate the performance of the proposed approach, in which encouraging results validate the effectiveness of the proposed technique, especially for plain/multiple copy-move forgeries, in comparison with the state-of-the-art approaches recently proposed in the literature.





















Similar content being viewed by others
References
Sadeghi S, Dadkhah S, Jalab HA, Mazzola G (2018) State of the art in passive digital image forgery detection: copy-move image forgery. Pattern Anal Appl 21(2):291–306
Pan X, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inf Forens Secur 5(4):857–867
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G (2011) A sift-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans Inf Forens Secur 6(3):1099–1110
Silva E, Carvalho T, Ferreira A, Rocha A (2015) Going deeper into copy-move forgery detection: Exploring image telltales via multi-scale analysis and voting processes. J Vis Commun Image Represent 29:16–32
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forens Secur 10(3):507–518
Zandi M, Mahmoudi-Aznaveh A, Talebpou A (2016) Iterative copy-move forgery detection based on a new interest point detector. IEEE Trans Inf Forens Secur 11(11):2499–2512
Shivakumar BL, Baboo SS (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues (IJCSI) 8(4):199
Rosten E, Drummond T (2006) Machine learning for high-speed corner detection. European conference on computer vision (ECCV), Graz, Austria. Springer, Berlin
Li YN (2013) Quaternion polar harmonic transforms for color images. IEEE Signal Process Lett 20(8):803–806
Mahmood T, Mehmood Z, Shah M, Saba T (2018) A robust technique for copy-move forgery detection and localization in digital images via stationary wavelet and discrete cosine transform. J Vis Commun Image Represent 53:202–214
Muhammad G, Hussain M, Bebis G (2012) Passive copy move image forgery detection using undecimated dyadic wavelet transform. Digit Invest 9(1):49–57
Bravo-Solorio S, Nandi AK (2011) Exposing duplicated regions affected by reflection, rotation and scaling. In: 2011 IEEE international conference on acoustics, speech and signal processing (ICASSP), Prague, Czech Republic, 22–27
Hilal A, Hamzeh T, Chantaf S (2017) Copy-move forgery detection using principal component analysis and discrete cosine transform. 2017 sensors networks smart and emerging technologies (SENSET), Beirut, Lebanon, 12–14
Dixit R, Naskar R, Mishra S (2017) Blur-invariant copy-move forgery detection technique with improved detection accuracy utilising SWT-SVD. IET Image Proc 11(5):301–309
T. Mahmood, T. Nawaz, M. Shah, Z. Khan, R. Ashraf, H. A. Habib. Copy-move forgery detection technique based on DWT and Hu Moments. International Journal of Computer Science and Information Security (IJCSIS), 2016, 14(5).
J. Ouyang, Y. Liu, M. Liao. Robust copy-move forgery detection method using pyramid model and Zernike moments. Multimedia Tools and Applications, 2018, 1–19.
Pun CM, Chung JL (2018) A two-stage localization for copy-move forgery detection. Inf Sci 463:33–55
Warif NBA, Idris MYI, Wahab AWA, Salleh R (2019) CMF-iteMS: An automatic threshold selection for detection of copy-move forgery. Forensic Sci Int 295:83–99
Li L, Li S, Zhu H, Wu X (2014) Detecting copy-move forgery under affine transforms for image forensics. Comput Electr Eng 40(6):1951–1962
Emam M, Han Q, Niu X (2016) PCET based copy-move forgery detection in images under geometric transforms. Multimedia Tools and Applications 75(18):11513–11527
Yap PT, Jiang X, Kot AC (2010) Two-dimensional polar harmonic transforms for invariant image representation. IEEE Trans Pattern Anal Mach Intell 32(7):1259–1270
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copy–move forgery detection. IEEE Trans Inf Forensics Secur 10(11):2284–2297
Zhu Y, Shen X, Chen H (2016) Copy-move forgery detection based on scaled ORB. Multimedia Tools and Applications 75(6):3221–3233
Yang H, Qi S, Niu Y, Niu P, Wang X (2019) Copy-move forgery detection based on adaptive keypoints extraction and matching. Multimedia Tools and Applications 78(24):34585–34612
Y. Li, J. Zhou. Image copy-move forgery detection using hierarchical feature point matching. 2016 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA), Jeju, South Korea, 13–16, Dec. 2016.
Wang XY, Li S, Liu YN, Niu Y, Yang HY, Zhou ZL (2017) A new keypoint-based copy-move forgery detection for small smooth regions. Multimedia Tools and Applications 76(22):23353–23382
Jin G, Wan X (2017) An improved method for SIFT-based copy–move forgery detection using non-maximum value suppression and optimized J-Linkage. Signal Processing: Image Communication 57:113–125
Pun CM, Yuan XC, Bi XL (2015) Image forgery detection using adaptive over-segmentation and feature point matching. IEEE Trans Inf Forensics Secur 10(8):1705–1716
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Del Tongo L, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Processing: Image Communication 28(6):659–669
Li Y, Wang S, Tian Q, Ding X (2015) A survey of recent advances in visual feature detection. Neurocomputing 149:736–751
Rosten E, Porter R, Drummond T (2010) Faster and better: A machine learning approach to corner detection. IEEE Trans Pattern Anal Mach Intell 32(1):105–119
E. Mair, G. D. Hager, D. Burschka, M. Suppa, G. Hirzinger. Adaptive and generic corner detection based on the accelerated segment test. European Conference on Computer Vision (ECCV), Crete, Greece, 5–10, Sept. 2010.
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vision 60(2):91–110
Mainali P, Lafruit G, Yang Q, Geelen B, Van Gool L, Lauwereins R (2013) SIFER: scale-invariant feature detector with error resilience. Int J Comput Vision 104(2):172–197
Yang H, Qi S, Wang C, Yang S, Wang X (2020) Image analysis by Log-Polar Exponent-Fourier moments. Pattern Recogn 101:107177
Liao SX, Pawlak M (1998) On the accuracy of Zernike moments for image analysis. IEEE Trans Pattern Anal Mach Intell 20(12):1358–1364
C. H. Teh, R. T. Chin. On image analysis by the methods of moments. The Computer Society Conference on Computer Vision and Pattern Recognition (CVPR), Ann Arbor, MI, USA, 5–9, June 1988.
Xin Y, Liao S, Pawlak M (2007) Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recogn 40(12):3740–3752
Rakshit S, Ghosh A, Shankar BU (2007) Fast mean filtering technique (FMFT). Pattern Recogn 40(3):890–897
Li Y, Zhou J (2019) Fast and effective image copy-move forgery detection via hierarchical feature point matching. IEEE Trans Inf Forensics Secur 14(5):1307–1322
Funding
This work was supported by the National Natural Science Foundation of China under Grant Nos. 61472171 and 61701212.
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, Xy., Wang, C., Wang, L. et al. Robust and effective multiple copy-move forgeries detection and localization. Pattern Anal Applic 24, 1025–1046 (2021). https://doi.org/10.1007/s10044-021-00968-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10044-021-00968-y