Abstract
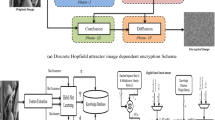
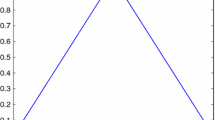
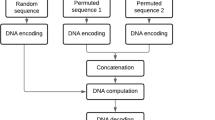
Multimedia data encryption is an ever-growing and challenging domain in the emerging digital world, with image encryption at the forefront to provide privacy for the user’s data. Image encryption aims to generate a stable noisy image irrespective of the input image. The current solution to this communication challenge is to use complex mathematics with a series of algorithms known as public-key cryptography. But the increasing power of computers and the ingenuity of hackers is open up more and more cracks in this mathematical armor. An ideal solution to this problem would provide provable information security, guaranteeing the safety of our personal information. In addition to it, the system must adapt itself to day to day miracles of the real world. Neural assisted techniques are the solutions to satisfy the above-said requirements. Hence, this paper proposes Hopfield neural attractor-assisted image encryption scheme in which combined tent maps are employed for the substitution process. Nowadays, a chosen-plaintext attack is a big challenge for encryption schemes. To resist the chosen plaintext attack, this scheme proposes the higher bitplane confusion using the tent map, which replaces the conventional diffusion process. Besides, the proposed scheme offers desire metrics such as the average correlation of 0.003, entropy as 7.99, and keyspace of 10184.











Similar content being viewed by others
References
Suri S, Vijay R (2019) A synchronous intertwining logistic map-DNA approach for color image encryption. J Ambient Intell Hum Comput 10:2277–2290. https://doi.org/10.1007/s12652-018-0825-0
Chidambaram N, Raj P, Thenmozhi K et al (2019) A cloud compatible DNA coded security solution for multimedia file sharing & storage. Multimed Tools Appl 78:33837–33863. https://doi.org/10.1007/s11042-019-08166-z
Sivaraman R, Rajagopalan S, Rayappan B, Bosco J, Rengarajan A (2020) ‘Ring oscillator as confusion–diffusion agent: a complete TRNG drove image security. IET Image Process 14:2987–2997. https://doi.org/10.1049/iet-ipr.2019.0168
Kalpana M, Ratnavelu K, Balasubramaniam P et al (2019) Double-key secure for N-1-N sound record data (SRD) by the drive-response of BAM NNs. Neural Process Lett 50:2925–2944. https://doi.org/10.1007/s11063-019-10067-z
N. I. of S. and Technology (2001) Specification for the Advanced Encryption Standard (AES)—FIPS PUB 197, pp 1–47. https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf
Silva-garcía VM, Flores-carapia R, Rentería-márquez C, Luna-benoso B (2018) Substitution box generation using Chaos: an image encryption application. Appl Math Comput 332:123–135
Praveenkumar P, Amirtharajan R, Thenmozhi K, Rayappan JBB (2017) Fusion of confusion and diffusion: a novel image encryption approach. Telecommun Syst 65:65–78
Li G, Wang L (2019) Double chaotic image encryption algorithm based on optimal sequence solution and fractional transform. Vis Comput 35:1267–1277. https://doi.org/10.1007/s00371-018-1574-y
Kumari M, Gupta S, Sardana P (2017) A survey of image encryption algorithms. 3D Res 8(4):1–35
Wang C, Zhang X, Zheng Z (2017) An efficient image encryption algorithm based on a novel chaotic map. Multimed Tools Appl 76(22):24251–24280
Sengul D (2016) A new data hiding method based on chaos embedded genetic algorithm for color image. Artif Intell Rev 46:129–143
Chandrasekaran J, Thiruvengadam SJ (2017) A hybrid chaotic and number theoretic approach for securing DICOM images. Secur Commun Netw 2017:1–12
Wu J, Liao X, Yang B (2018) Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process 142:292–300
Dhall S, Pal SK, Sharma K (2018) Cryptanalysis of image encryption scheme based on a new 1D chaotic system. Signal Process 146:22–32
Wang H, Xiao D, Chen X, Huang H (2018) Cryptanalysis and enhancements of image encryption using combination of the 1D chaotic map. Signal Process 144:444–452
Özkaynak F, Özer AB (2016) Cryptanalysis of a new image encryption algorithm based on chaos. Optik (Stuttg) 127(13):5190–5192
Lakshmi C, Thenmozhi K, Rayappan JBB, Amirtharajan R (2018) Encryption and watermark-treated medical image against hacking disease—an immune convention in spatial and frequency domains. Comput Methods Progr Biomed 159:11–21
Hopfield J (1984) Neurons with graded response have collective computational properties like those of two-state neurons. Proc Natl Acad Sci USA 81:3088–3092
Lakshmi C, Thenmozhi K, Rayappan JBB, Amirtharajan R (2019) Hopfield attractor-trusted neural network: an attack-resistant image encryption. Neural Comput Appl 32:11477–11489
Wang XY, Li ZM (2019) A color image encryption algorithm based on Hopfield chaotic neural network. Opt Lasers Eng 115:107–118
Li Q, Yang X-S, Yang F (2005) Hyperchaos in Hopfield-type neural networks. Neurocomputing 67:275–280
Hopfield JJ (1982) Neural networks and physical systems with emergent collective computational abilities (associative memory/parallel processing/categorization/content-addressable memory/fail-soft devices). Biophysics (Oxf) 79:2554–2558
Gao T, Gu Q, Emmanuel S (2009) A novel image authentication scheme based on hyper-chaotic cell neural network. Chaos, Solitons Fractals 42(1):548–553
Huang Y, Yang X-S (2006) Hyperchaos and bifurcation in a new class of four-dimensional Hopfield neural networks. Neurocomputing 69(13):1787–1795
Kassem A, Hassan HAH, Harkouss Y, Assaf R (2013) Efficient neural chaotic generator for image encryption. Digit Signal Process 25:266–274
Bigdeli N, Farid Y, Afshar K (2012) A robust hybrid method for image encryption based on Hopfield neural network. Comput Electr Eng 38(2):356–369
Yu W, Cao J (2006) Cryptography based on delayed chaotic neural networks. Phys Lett Sect A Gen At Solid State Phys 356(4–5):333–338
Fu C et al (2013) An efficient and secure medical image protection scheme based on chaotic map. Comput Biol Med 43(8):1000–1010. https://doi.org/10.1016/j.compbiomed.2013.05.005
El Assad S, Farajallah M (2016) A new chaos-based image encryption system. Signal Process Image Commun 41:144–157
Zhang Y (2018) The unified image encryption algorithm based on chaos and cubic S-Box. Inf Sci (NY) 450:361–377. https://doi.org/10.1016/j.ins.2018.03.055
Li Q, Yang XS, Yang F (2005) Hyperchaos in Hopfield-type neural networks. Neurocomputing 67(1–4 SUPPL.):275–280
Wu Y, Zhou Y, Saveriades G, Agaian S, Noonan JP, Natarajan P (2013) Local Shanon entropy measure with statistical tests for image randomness. Inf Sci (NY) 222:323–342
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber J Multidiscip J Sci Technol J Sel Areas Telecommun 1:31–38
Xue H, Du J, Li S, Ma W (2018) Region of interest encryption for color images based on a hyperchaotic system with three positive Lyapunov exponets. Opt Laser Technol 106:506–516
Diaconu A-V (2016) Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf Sci 355–356:314–327. https://doi.org/10.1016/j.ins.2015.10.027
Khan AH, Cao X, Li S, Katsikis VN, Liao L (2020) BAS-ADAM: an ADAM based approach to improve the performance of beetle antennae search optimizer. IEEE/CAA J Autom Sin 7(2):461–471. https://doi.org/10.1109/JAS.2020.1003048
Khan AH et al (2020) Optimal portfolio management for engineering problems using nonconvex cardinality constraint: a computing perspective. IEEE Access 8:57437–57450. https://doi.org/10.1109/ACCESS.2020.2982195
Li Z, Li S (2020) Saturated PI control for nonlinear system with provable convergence: an optimization perspective. IEEE Trans Circuits Syst II Express Briefs 1:5. https://doi.org/10.1109/tcsii.2020.3007879
Li Z, Zuo W, Li S (2020) Zeroing dynamics method for motion control of industrial upper-limb exoskeleton system with minimal potential energy modulation. Measurement 163:107964
Li Z, Li C, Li S, Cao X (2020) A fault-tolerant method for motion planning of industrial redundant manipulator. IEEE Trans Ind Inform 16(12):7469–7478. https://doi.org/10.1109/TII.2019.2957186
Acknowledgements
The authors thank the Department of Science and Technology, New Delhi for the FIST funding (SR/FST/ET-II/2018/221). Also, the authors wish to thank the Intrusion Detection Lab at School of Electrical and Electronics Engineering, SASTRA Deemed University for providing infrastructural support to carry out this research work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lakshmi, C., Thenmozhi, K., Venkatesan, C. et al. Mutated Cleavages of Images for Stealth Disclosure: A Hopfield Neural Network Attractor (HNNA) Approach. Neural Process Lett 53, 907–928 (2021). https://doi.org/10.1007/s11063-020-10412-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11063-020-10412-7