Abstract
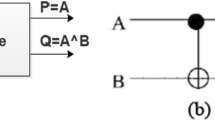
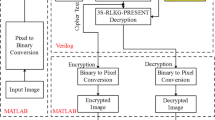
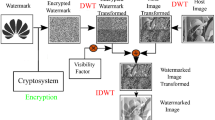
The reversible computation is the process of designing the architecture with reversible logic gates (RLG) and applicable for optical computing, digital signal processing, nanotechnologies and low-power circuits. In this study, integer wavelet transform (IWT) compression technique is applied to the input image to compress the pixel value. The utilization of the IWT is used to improve the quality of the image in terms of peak signal-to-noise ratio (PSNR) and structural similarity index matrix (SSIM). In addition, different types of RLGs are used to perform the encryption and decryption of the images. A random number is generated using the Lorenz chaotic system (LCS) that contains three different stages and each stage is developed using arithmetic blocks. Here, an effective key value is generated from the input image values by connecting the LCS’s output with the heterogeneous key generation (HKG) module. The inverse IWT (IIWT) technique is used to retrieve the original data during execution of decryption operation. Application specific integrated circuit and field-programmable gate array (FPGA) performances are calculated for reversible logic cryptographic design (RLCD) IWT-HKG architecture. The results showed that it has achieved better performance compared to conventional methods. Moreover, security analyses such as avalanche effect, side channel attack and session key agreement are performed for the RLCD-IWT-HKG method. The RLCD-IWT-HKG method has achieved 89 LUTs, 52 flip flops and 31 slices for the Virtex 6 FPGA device. After retrieving the decrypted images, values of PSNR and SSIM are evaluated as 39.90 dB and 0.6874, respectively.


























Similar content being viewed by others
Data Availability
The datasets generated during the current study are not publicly available due to the usage of real-time images. In this research work, we have captured a real-time dataset using a DSLR camera. But, the real-time datasets are available from the corresponding author on reasonable request.
References
H.D. Azari, P.V. Joshi, An efficient implementation of present cipher model with 80 bit and 128 bit key over FPGA based hardware architecture. Int. J. Pure Appl. Math. 119, 1825–1832 (2018)
A.N. Bahar, M.M. Rahman, N.M. Nahid, M.K. Hassan, Energy dissipation dataset for reversible logic gates in quantum dot-cellular automata. Data Brief 10, 557–560 (2017)
M.K. Balajee, J.M. Gnanasekar, Evaluation of key dependent S-box based data security algorithm using hamming distance and balanced output. Tem J. 5, 67–75 (2016)
A. Balamanikandan, K. Krishnamoorthi, Low area ASIC implementation of LUT–CLA–QTL architecture for cryptography applications. Wireless Netw. 26(1–13), 2681–2693 (2020)
G. Bansod, A. Patil, S. Sutar, N. Pisharoty, An ultralightweight encryption design for security in pervasive computing, in Big Data Security on Cloud (BigDataSecurity). IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS) (2016), pp. 79–84
Z.H.A.O. Guosheng, W.A.N.G. Jian, Security analysis and enhanced design of a dynamic block cipher. China Commun. 13, 150–160 (2016)
E. Honarvarfard, M. Gamella, A. Poghossian, M.J. Schöning, E. Katz, An enzyme-based reversible controlled NOT (CNOT) logic gate operating on a semiconductor transducer. Appl. Mater. Today 9, 266–270 (2017)
S. Karunamurthi, V.K. Natarajan, VLSI implementation of reversible logic gates cryptography with LFSR key. Microprocess. Microsyst. 69, 68–78 (2019)
I. Koyuncu, A.T. Özcerit, The design and realization of a new high speed FPGA-based chaotic true random number generator. Comput. Electr. Eng. 58, 203–214 (2017)
B. Koziel, R. Azarderakhsh, M.M. Kermani, D. Jao, Post-quantum cryptography on FPGA based on isogenies on elliptic curves. IEEE Trans. Circuits Syst. I Regul. Pap. 64, 86–99 (2017)
B. Koziel, R. Azarderakhsh, M.M. Kermani, A high-performance and scalable hardware architecture for isogeny-based cryptography. IEEE Trans. Comput. 67, 1594–1609 (2018)
S. Kuchhal, R. Verma, Security design of DES using reversible logic. Int. J. Comput. Sci. Netw. Secur. 15, 81 (2015)
L. Li, B. Liu, H. Wang, QTL: a new ultra-lightweight block cipher. Microprocess. Microsyst. 45, 45–55 (2016)
G.S. Mahdi, A modification of TEA block cipher algorithm for data security (MTEA). Eng. Technol. J. 29, 822–832 (2011)
M.S. Mahindrakar, Evaluation of blowfish algorithm based on avalanche effect. Int. J. Innov. Eng. Technol. 4, 99–103 (2014)
S.T. Nadu, A block cipher algorithm to enhance the avalanche effect using dynamic key-dependent s-box and genetic operations. Int. J. Pure Appl. Math. 119, 399–418 (2018)
A.C. Nuthan, C. Nagaraj, V.B. Havyas, Implementation of data encryption standard using reversible gate logic. Int. J. Soft Comput. Eng. 3, 270–272 (2013)
S. Patranabis, D.B. Roy, A. Chakraborty, N. Nagar, A. Singh, D. Mukhopadhyay, S. Ghosh, Lightweight design-for-security strategies for combined countermeasures against side channel and fault analysis in IoT applications. J. Hardw. Syst. Secur. 3(2), 103–131 (2019)
K. Rajesh, G. Umamaheswara Reddy, FPGA implementation of encryption and decryption of a message using optimized reconfigurable reversible gate. Int. J. Innov. Eng. Technol. 8, 1654–1658 (2019)
P. Sarkar, Tweakable enciphering schemes using only the encryption function of a block cipher. Inf. Process. Lett. 111, 945–955 (2011)
M. Soeken, M. Roetteler, N. Wiebe, G. De Micheli, LUT-based hierarchical reversible logic synthesis. Comput. Aided Des. Integr. Circuits Syst. 38, 1675–1688 (2018)
N. Tara, H.M.H. Babu, L. Jamal, Power efficient optimum design of the reversible Plessey logic block of a field-programmable gate array. Sustain. Comput. Inf. Syst. 16, 76–92 (2017)
M. Zhang, X. Tong, Joint image encryption and compression scheme based on IWT and SPIHT. Opt. Lasers Eng. 90, 254–274 (2017)
H. Zodpe, A. Sapkal, An efficient AES implementation using FPGA with enhanced security features. J. King Saud Univ. Eng. Sci. 32, 115–122 (2018)
Funding
This study was not funded by any organization.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Saranya, K., Vijeyakumar, K. A Low Area FPGA Implementation of Reversible Gate Encryption with Heterogeneous Key Generation. Circuits Syst Signal Process 40, 3836–3865 (2021). https://doi.org/10.1007/s00034-021-01649-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-021-01649-1