Abstract
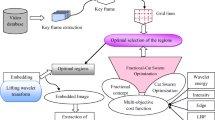
In this paper, an effective method named Exponential Fractional-Cat Swarm Optimization (Exponential Fractional-CSO) along with multi-objective cost function is proposed. The proposed method is designed by integrating the CSO with the fractional concept based on the Exponential parameters. Initially, an input video is selected from the database from which frames are generated. Key frames are chosen among the frames using the contourlet transform and Structural Similarity Index Measure (SSIM). Regions are formed on the selected key frames through the help of grid lines. Once the regions are formed, optimal regions are ascertained with the help of the proposed optimization algorithm along with multi-objective cost functions to hide the secret data. During the embedding process, the secret data is hidden in the optimal region using the lifting wavelet transform (LWT). The embedded video is then transmitted through the network to reach its intended receiver. The experimental results reveal that the proposed Exponential Fractional-CSO obtained a maximal correlation of 0.9931 by considering the frames, maximal Peak Signal-to-Noise Ratio (PSNR) of 89.70 dB and MSE of 0.00006 respectively. Hence, the proposed method shows greater effectiveness of hiding the secret data in the video sequence along with data security.






Similar content being viewed by others
References
Bahrami M, Bozorg-Haddad O, Chu X (2018) Cat swarm optimization (CSO) algorithm. In: Bozorg-Haddad O (ed) Advanced optimization by nature-inspired algorithms. Springer Singapore, Singapore, pp 9–18
Banharnsakun A (2018) Artificial bee colony approach for enhancing LSB based image steganography. Multimed Tools Appl 77:27491–27504. https://doi.org/10.1007/s11042-018-5933-5
Bhaladhare PR, Jinwala DC (2014) A clustering approach for the l -diversity model in privacy preserving data mining using fractional calculus-bacterial foraging optimization algorithm. Adv Comput Eng 2014:1–12. https://doi.org/10.1155/2014/396529
Chan PW, Lyu MR, Chin RT (2005) A novel scheme for hybrid digital video watermarking: approach, evaluation and experimentation. IEEE Trans Circuits Syst Video Technol 15:1638–1649. https://doi.org/10.1109/TCSVT.2005.856932
Chandel B, Jain DS (2016) Video steganography: a survey. 7
Feng Y, Wang G-G, Deb S et al (2017) Solving 0–1 knapsack problem by a novel binary monarch butterfly optimization. Neural Comput & Applic 28:1619–1634. https://doi.org/10.1007/s00521-015-2135-1
Goldberg DE, HOLLAND JH (1998) Genetic algorithms and machine learning. Kluwer Academic Publishers
Gurunathan K, Rajagopalan SP (2020) A stegano - visual cryptography technique for multimedia security. Multimed Tools Appl 79:3893–3911. https://doi.org/10.1007/s11042-019-7471-1
Hussain M, Wahab AWA, Idris YIB et al (2018) Image steganography in spatial domain: A survey. Signal Processing: Image Communication 65:46–66. https://doi.org/10.1016/j.image.2018.03.012
Jalali A, Farsi H (2019) A new steganography algorithm based on video sparse representation. Multimed Tools Appl. https://doi.org/10.1007/s11042-019-08233-5
Karaboga D, Basturk B (2007) A powerful and efficient algorithm for numerical function optimization: artificial bee colony (ABC) algorithm. J Glob Optim 39:459–471. https://doi.org/10.1007/s10898-007-9149-x
Kennedy J, Eberhart R (1995) Particle swarm optimization. In: paper presented at the proceeding of the IEEE international conference on neural networks, Perth, Australia, 27 November–1 December
Khadam U, Iqbal MM, Alruily M et al (2020) Text data security and privacy in the internet of things: threats, challenges, and future directions. Wirel. Commun. Mob. Comput. 2020:1–15. https://doi.org/10.1155/2020/7105625
Li Y, Wang H-X (2019) Robust H.264/AVC video watermarking without intra distortion drift. Multimed Tools Appl 78:8535–8557. https://doi.org/10.1007/s11042-018-6942-0
Liu S, Xu D (2020) A robust steganography method for HEVC based on secret sharing. Cogn. Syst. Res. 59:207–220. https://doi.org/10.1016/j.cogsys.2019.09.008
Liu Y, Li Z, Ma X (2012) Reversible data hiding scheme based On H.264/AVC without distortion drift. JSW 7:1059–1065. https://doi.org/10.4304/jsw.7.5.1059-1065
Liu S, Bai W, Liu G et al (2018) Parallel fractal compression method for big video data. Complexity 2018:1–16. https://doi.org/10.1155/2018/2016976
Miri A, Faez K (2017) Adaptive image steganography based on transform domain via genetic algorithm. Optik 145:158–168. https://doi.org/10.1016/j.ijleo.2017.07.043
Montes de Oca MA, Stutzle T, Birattari M, Dorigo M (2009) Frankenstein’s PSO: a composite particle swarm optimization algorithm. IEEE Trans Evol Computat 13:1120–1132. https://doi.org/10.1109/TEVC.2009.2021465
Moon SK, Raut RD (2013) Analysis of secured video steganography using computer forensics technique for enhance data security. In: 2013 IEEE Second International Conference on Image Information Processing (ICIIP-2013). IEEE, Shimla, India, pp 660–665
Noda H, Furuta T, Niimi M, Kawaguchi E (2004) Application of BPCS steganography to wavelet compressed video. In: 2004 International Conference on Image Processing, 2004. ICIP ‘04. IEEE, Singapore, pp 2147–2150
Noorkami M, Mersereau RM (2007) A framework for robust watermarking of H.264-encoded video with controllable detection performance. IEEE Trans Inform Forensic Secur 2:14–23. https://doi.org/10.1109/TIFS.2006.890306
Pradhan PM, Panda G (2012) Solving multiobjective problems using cat swarm optimization. Expert Syst. Appl. 39:2956–2964. https://doi.org/10.1016/j.eswa.2011.08.157
Shanableh T (2012) Data hiding in MPEG video files using multivariate regression and flexible macroblock ordering. IEEE Trans Inform Forensic Secur 7:455–464. https://doi.org/10.1109/TIFS.2011.2177087
Song GH, Liu H (2020) An improved high capacity and efficient data hiding scheme for 3d videos without distortion drift. IEEE Access 8:143464–143478. https://doi.org/10.1109/ACCESS.2020.3013033
Stanescu D, Stratulat M, Ciubotaru B et al (2007) Embedding data in video stream using steganography. In: 2007 4th International Symposium on Applied Computational Intelligence and Informatics. IEEE, Timisoara, Romania, pp 241–244
Suresh M, Sam IS (2020) Optimal wavelet transform using Oppositional Grey Wolf Optimization for video steganography. Multimed Tools Appl. https://doi.org/10.1007/s11042-020-09330-6
Suresh M, Shatheesh Sam I (2018) High secure video steganography based on shuffling of data on Least significant DCT coefficients. In: 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS). IEEE, Madurai, India, pp 877–882
Suresh M, Shatheesh Sam I (2020) Optimized interesting region identification for video steganography using Fractional Grey Wolf Optimization along with multi-objective cost function. Journal of King Saud University - Computer and Information Sciences S1319157820304456. https://doi.org/10.1016/j.jksuci.2020.08.007
Tew Y, Wong K (2014) An Overview of Information Hiding in H.264/AVC Compressed Video. IEEE Trans Circuits Syst Video Technol 24:305–319. https://doi.org/10.1109/TCSVT.2013.2276710
Tsai Y-S, Tsai P (2011) Adaptive data hiding for vector quantization images based on overlapping codeword clustering. Inf. Sci. 181:3188–3198. https://doi.org/10.1016/j.ins.2011.03.017
Video Watermarking using DWT - File Exchange - MATLAB Central. https://in.mathworks.com/matlabcentral/fileexchange/52225. Accessed 24 Mar 2020
Wagdarikar AMU, Senapati RK (2019) Design and development of a multiobjective cost function for robust video watermarking using wavelet transform. J Intell Syst 28:873–891. https://doi.org/10.1515/jisys-2017-0264
Wang W, Farid H (2009) Exposing digital forgeries in video by detecting double quantization. In: Proceedings of the 11th ACM workshop on Multimedia and security - MM&Sec ‘09. ACM Press. USA, Princeton, New Jersey, p 39
Wang J, Jia X, Kang X, Shi Y-Q (2019) A Cover Selection HEVC Video Steganography Based on Intra Prediction Mode. IEEE Access 7:119393–119402. https://doi.org/10.1109/ACCESS.2019.2936614
Xiph.org :: Derf’s Test Media Collection. https://media.xiph.org/video/derf/. Accessed 24 Mar 2020
Xue Y, Zhou J, Zeng H et al (2019) An adaptive steganographic scheme for H.264/AVC video with distortion optimization. Signal Process. Image Commun. 76:22–30. https://doi.org/10.1016/j.image.2019.04.012
Yang H, Kot AC (2004) Text document authentication by integrating inter character and word spaces watermarking. 2004 IEEE International Conference on Multimedia and Expo (ICME) (IEEE Cat. No.04TH8763). IEEE, Taipei, Taiwan:955–958
Younus ZS, Younus GT (2019) Video Steganography Using Knight Tour Algorithm and LSB Method for Encrypted Data. J. Intell. Syst. 29:1216–1225. https://doi.org/10.1515/jisys-2018-0225
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Suresh, M., Sam, I.S. Exponential fractional cat swarm optimization for video steganography. Multimed Tools Appl 80, 13253–13270 (2021). https://doi.org/10.1007/s11042-020-10395-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10395-6