Abstract
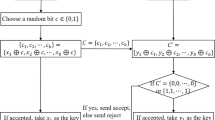
Recently, Tian et al. proposed a multi-user quantum private query protocol. The protocol realizes the function of n users querying the database at the same time, which can well protect the privacy of users and databases, and has high efficiency of implementation. Unfortunately, it has security vulnerability in the process of sending quantum sequences. Based on this vulnerability, we propose a man-in-the-middle attack on multi-user quantum private query protocol. Firstly, this paper reviews the multi-user quantum private query protocol. Secondly, the implementation steps of multi-user private query protocol are reviewed concisely. Finally, we pointed that in the protocol, Eve, the eavesdropper, can pretend to be Bob and the identity of the user to obtain the key of query data and steal the database information without being discovered. Through analysis, we find that man in the middle attack is feasible.



Similar content being viewed by others
References
Gertner, Y., Ishai, Y., Kushilevitz, E., Malkin, T.: Protecting data privacy in private information retrieval schemes. J. Comput. Syst. Sci. 60, 592–629 (2000)
Diep, D.N., Nagata, K., Wong, R.: Continuous-variable quantum computing and its applications to cryptography. Int. J. Theor. Phys. 59, 3184–3188 (2020)
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett. 100, 230502 (2008)
Ben-Or, M., Horodecki, M., Leung, D.W., Mayers, D., Oppenheim, J.: The universal composable security of quantum key distribution. Lect. Notes Comput. Sci. 3378, 386–406 (2005)
Jakobi, M., Simon, C., Gisin, N., Bancal, J.D., Branciard, C., Walenta, N., Zbinden, H.: Practical private database queries based on a quantum-key- distribution protocol. Phys. Rev. A. 83, 022301 (2011)
Gao, F., Liu, B., Wen, Q.Y.: Flexible quantum private queries based on quantum key distribution. Opt. Express. 20(16), 17411–17420 (2012)
Yang, Y.G., Zhang, M.O., Yang, R.: Private database queries using one quantum state. Quantum Inf. Process. 14, 1017–1024 (2015)
Zhu, H., Wang, X., Chen, C.M., Kumari, S.: Two novel semi-quantum-reflection protocols applied in connected vehicle systems with blockchain. Comput. Electr. Eng. 86, 106714 (2020)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A. 79(3), 032341 (2009)
Pei, T.R., Meng, X.L., Wei, C.Y., Gao, F., Tian, S.J., Deng, Q.Y.: Practical quantum private query of blocks based on the two-dimensional QKD system. Quantum Inf. Process. 18, 240 (2019)
Chang, Y., Zhang, S.B., Wan, G.G., Yan, L.L., Zhang, Y., Li, X.Y.: Practical two-way QKD-based quantum private query with better performance in user privacy. Int. J. Theor. Phys. 58, 2069–2080 (2019)
Ma, H.Y., Xu, P.A., Shao, C.H., Chen, L.B., Li, J.X., Pan, Q.: Quantum private query based on stable error correcting code in the case of noise. Int. J. Theor. Phys. 58, 4241–4248 (2019)
Xiao, H., Huang, W.H., Zhou, M.: An efficient quantum private query protocol based on Oracle and Grover iteration. Int. J. Theor. Phys. 58, 3025–3035 (2019)
Ye, T.Y., Li, H.K., Hu, J.L.: Multi-user quantum private query protocol. Int. J. Theor. Phys. 59, 2867–2874 (2020). https://doi.org/10.1007/s10773-020-04546-6
Akram, M.A., Ghaffar, Z., Mahmood, K., Kumari, S., Agarwal, K., Chen, C.M.: An anonymous authenticated key-agreement scheme for multi-server infrastructure Human-centric. Comput. Inf. Sci. 10(1), 1–18 (2020)
Wu, T.Y., Lee, Z., Obaidat, M.S., Kumari, S., Kumar, S., Chen, C.M.: An authenticated key exchange protocol for multi-server architecture in 5G networks. IEEE Access. 8, 28096–28108 (2020)
Acknowledgements
This work was supported by the Liaoning Provincial Natural Science Foundation of China (Grant No. 2019-MS-286), and Basic Scientific Research Project of Liaoning Provincial Department of Education (Grant No. LJC202007), and Shenyang Jianzhu University’s educational science research project in 2019.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhu, D., Wang, L. & Zhu, H. Cryptanalysis of Multi-User Quantum Private Query Protocol. Int J Theor Phys 60, 284–292 (2021). https://doi.org/10.1007/s10773-020-04691-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04691-y