Abstract
Internet of things (IoT) devices lead to innovation trends in financial services. Real-world IoT applications certainly further the surge in new financial product design. In the insurance industry, companies can utilise data collected from all types of IoT-connected devices to more effectively determine premiums and provide better insurance products, known as IoT insurance. However, this has a downside: insurance companies might underestimate the possible cyber risks involved in these IoT insurance products. This study examines the potential cyber risks arising from the application of IoT devices-linked insurance. We consider the cyber risks in insurance product valuation and estimate the possible increase in cyber risk cost as more data are sourced from IoT devices. Our results contribute to IoT devices-linked health insurance development and improvement in related cyber risk management.



Similar content being viewed by others
Notes
Following Eling and Loperfido (2017), we use the same modelling strategy on U.S. data breach data.
We set the location parameter = 0 in this study, which assumes the entire sample follows GPD.
We assume a portfolio of insurance policies including different numbers of policyholders at different ages.
The quantile value of the lower left panel is calculated using an interpolation approach. We use the package ‘psych’ in R statistical software for the procedure.
Eling and Loperfido (2017) also apply this transformation method for loss amount estimation.
We use the R package “QTLRel” and “SpatialExtremes” to produce Q–Q plots for lognormal and GPD, respectively.
Unfortunately, these data are not publicly available. Most public data lack a categorised total.
The estimation indicates that the proportion of health insurance policy is for the whole insurance market. We divide by the number of health insurance policyholders in the U.S. The total written health insurance premiums are USD 867.5 billion. Also, the summations of the premiums of written health insurance, life insurance and non-life insurance are USD 670.1 billion, USD 546.8 billion and USD 830.3 billion, respectively. Hence, \(p_{1} = 867.5/\left( {670.1 + 546.8 + 830.3} \right) \cong 0.424.\) The total number of health insurance policyholders in the U.S. is 217.007 million. Thus, the discount rate in this study is \(p = 0.424 *\left( {1000/217007000} \right) \cong 0.00001954\).
In Taiwan, health insurance companies offer 5% to 10% premium discounts for such IoT health insurance, corresponding to the different levels of steps walked daily. We also provide sensitivity analysis in the numerical results.
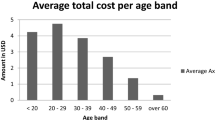
This assumption is based on the fact that IoT health insurance in Taiwan is primarily sold to people between the ages of 20 and 50.
GPD distribution is highly skewed, and therefore extreme values may occur; this may affect the sample average. Although our simulation is valid using an ordinary average, we suggest using a trimmed average for robust comparison if the ordinary average is unstable.
Health insurance premium is decided by the actuarial equivalence principle, including 10% loading for risk diversity.
For IoT security protection, see the website: https://www.trendmicro.com/us/iot-security/.
References
AIG. 2018. Getting hacked: IoT and beyond. https://www.aig.com/content/dam/aig/america-canada/us/documents/innovative-tech/getting-hacked-iot-and-beyond.pdf. Accessed 15 Nov 2019.
Anchen, J. 2017. Cyber: Getting to grips with a complex risk. Swiss Re Sigma 1: 1–38. https://www.swissre.com/institute/research/sigma-research/sigma-2017-01.html. Accessed 11 July 2019.
Auer, M. 2008. Operationelles risikomanagement bei finanzinstituten: Risiken identifizieren, analysieren und steuern. Weinheim: Wiley-VCH.
Biener, C., M. Eling, and J.H. Wirfs. 2015. Insurability of cyber risk: An empirical analysis. The Geneva Papers on Risk and Insurance-Issues and Practice 40 (1): 131–158.
Bruschi, D., L. Martignoni, and M. Monga. 2007. Code normalization for self-mutating malware. IEEE Security and Privacy 5 (2): 46–54.
Bouveret, A. 2018. Cyber risk for the financial sector: A framework for quantitative assessment. IMF working papers series. DC: International Monetary Fund.
Dey, N., A.S. Ashour, and C. Bhatt. 2017. Internet of things driven connected healthcare. In Internet of things and big data technologies for next generation healthcare, studies in big data, vol. 23, ed. C. Bhatt, N. Dey, and A. Ashour. Cham: Springer.
Dutang, C. 2015. Standard statistical inference. In Computational actuarial science with R, ed. A. Charpentler, 75–125. Boca Raton: CRC Press.
Eling, M., and K. Jung. 2018. Copula approaches for modeling cross-sectional dependence of data breach losses. Insurance: Mathematics and Economics 82: 167–180.
Eling, M., and M. Lehmann. 2018. The impact of digitalization on the insurance value chain and the insurability of risks. The Geneva Papers on Risk and Insurance-Issues and Practice 43 (3): 359–396.
Eling, M., and N. Loperfido. 2017. Data breaches: Goodness of fit, pricing, and risk measurement. Insurance: Mathematics and Economics 75: 126–136.
Eling, M., and J. Wirfs. 2019. What are the actual costs of cyber risk events? European Journal of Operational Research 272 (3): 1109–1119.
Forbes. 2019. Confirmed: 2 billion records exposed in massive smart home device breach. https://www.forbes.com/sites/daveywinder/2019/07/02/confirmed-2-billion-records-exposed-in-massive-smart-home-device-breach/#14317f93411c. Accessed 22 Nov 2019.
Gatzert, N., and A. Kolb. 2013. Risk measurement and management of operational risk in insurance companies from an enterprise perspective. Journal of Risk and Insurance 81 (3): 683–708.
Gatzert, N., J.T. Schmit, and A. Kolb. 2016. Assessing the risks of insuring reputation risk. Journal of Risk and Insurance 83 (3): 641–679.
Gilleland, E., and C. Ribatet. 2015. Reinsurance and extremal events. In Computational actuarial science with R, ed. A. Charpentler, 257–286. Boca Raton: CRC Press.
Gubbi, J., R. Buyya, S. Marusic, and M. Palaniswami. 2013. Internet of things (IoT): A vision, architectural elements, and future directions. Future Generation Computer Systems 29 (7): 1645–1660.
Hajoary, P.K., and K.B. Akhilesh. 2020. Role of government in tackling cyber security threat. In Smart technologies, ed. K. Akhilesh and D. Möller. Singapore: Springer.
Hall, S. 2017. The growing impact of wearable technology. Center for Insurance Policy and Research Study Newsletter. https://www.naic.org/cipr_newsletter_archive/vol23_wearable.pdf. Accessed 4 Aug 2019.
Insurance Information Institute. 2019. 2019 insurance fact book. New York: Insurance Information Institute.
Jacobs, J. 2014. Analyzing ponemon cost of data breach. https://datadrivensecurity.info/blog/posts/2014/Dec/ponemon/. Accessed 11 July 2019.
Karapiperis, D., A. Obersteadt, A. Brandenburg, S. Castagna, B. Birnbaum, A. Greenberg, and R. Harbage. 2015. Usage-based insurance and vehicle telematics: Insurance market and regulatory implications. Washington: Center for Insurance Policy and Research Study, NAIC Press.
Kaserer, C., and C. Klein. 2019. Systemic risk in financial markets: How systemically important are insurers. Journal of Risk and Insurance. 1: 2. https://doi.org/10.1111/jori.12236.
Kopp, E., L. Kaffenberger, and C. Wilson. 2017. Cyber risk, market failures, and financial stability. IMF working papers Series. DC: International Monetary Fund.
Madakam, S., R. Ramaswamy, and S. Tripathi. 2015. Internet of TStandard statistical inferencehings (IoT): A literature review. Journal of Computer and Communications 3 (5): 164–173.
McNeil, A.J. 1997. Estimating the tails of loss severity distributions using extreme value theory. ASTIN Bulletin: The Journal of the IAA 27 (1): 117–137.
National Association of Insurance Commissioners (NAIC). 2019. Internet of Thing (IOT). https://www.naic.org/cipr_topics/topic_internet_of_things.htm. Accessed 4 Aug 2019.
Otto, P.N., A.I. Antón, and D.L. Baumer. 2007. The choicepoint dilemma: How data brokers should handle the privacy of personal information. IEEE Security and Privacy 5 (5): 15–23.
PwC. 2016. This wearable technology survey: Wearables in the workplace. https://www.pwc.co.za/en/assets/pdf/wearables-in-the-workplace.pdf. Accessed 4 Aug 2019.
Radanliev, P., D.C. De Roure, R. Nicolescu, M. Huth, R.M. Montalvo, S. Cannady, and P. Burnap. 2018. Future developments in cyber risk assessment for the internet of things. Computers in Industry 102: 14–22.
Romanosky, S. 2016. Examining the costs and causes of cyber incidents. Journal of Cybersecurity 2 (2): 121–135.
Staib, D., M. Puttaiah, and O. Tschekassin. 2019. World insurance: the great pivot east continues. Swiss Re Sigma 3, 1-45. https://www.swissre.com/dam/jcr:b8010432-3697-4a97-ad8b-6cb6c0aece33/sigma3_2019_en.pdf. Accessed 11 July 2019.
Stone, T. 2018. Protecting connected transportation networks. Network Security 2018 (12): 8–10.
Villegas, A.M., A.L. Medaglia, and L.F. Zuluaga. 2012. Computing bounds on the expected payoff of alternative risk transfer products. Insurance: Mathematics and Economics 51 (2): 271–281.
World Economic Forum. 2019. Global risks Report 2019. Geneva: World Economic Forum.
Yang, S.Y., C.W. Wang, and H.C. Huang. 2016. The valuation of lifetime health insurance policies with limited coverage. Journal of Risk and Insurance 83 (3): 777–800.
Ziegeldorf, J.H., O.G. Morchon, and K. Wehrle. 2014. Privacy in the internet of things: Threats and challenges. Security and Communication Networks 7 (12): 2728–2742.
Acknowledgements
We are extremely grateful to the two anonymous reviewers and the editor for their insightful and valuable comments and suggestions. The authors would also like to express their sincere gratitude to the Ministry of Science and Technology for the financial support of the research (MOST-107-2410-H-035 -052 -MY2).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The authors would like to express their sincere gratitude to the Ministry of Science and Technology for the financial support.
Appendix: Data description of several cyber risk cases in the PRC database
Appendix: Data description of several cyber risk cases in the PRC database
-
1.
Cyber Breach Date: 10-Mar-2010
Thrivent Financial for Lutherans, Minneapolis, experienced a break-in at one of its offices in Pennsylvania. A laptop computer was among the items stolen. The laptop had safeguards to protect sensitive information, including strong password protection and encryption. But Thrivent Financial says the information stored on the laptop may be at risk. The information on the laptop was personal information, including names, addresses, Social Security numbers and health information.
-
2.
Cyber Breach Date: 05-Feb-2015
Anthem, the second largest health insurance company operating under Anthem Blue Cross, Anthem Blue Cross and Blue Shield Amerigroup and Healthlink has suffered a massive data breach. The company announced that they have been the victim of a “very sophisticated external cyber attack” on their system. The information compromised includes names, birthdays, medical ID’s, Social Security Numbers, street addresses, e-mail addresses, employment and income information. Over the next several weeks, those who were affected will be receiving some form of identity theft protection. For those members with questions regarding the breach, the company has set up a toll-free line at 1-877-263-79951-877-263-7995 FREE. More Information: For the statement by Anthem’s CEO Joseph R. Swedish and the dedicated website created for customer information, click here.
Additional Information: As further investigations are pursued regarding the Anthem breach, research by Brian Krebs and others show that the hacking began as early as April 2014 and is pointing to the Chinese hacker group known as “Deep Panda”.? At the time, Anthem was called Wellpoint, and upon further investigation Krebs “discovered a series of connected domain names that appear to imitate actual WellPoint sites, including we11point.com and myhr.we11point.com.” Because these sites were constructed almost 10 months prior, the question has now been raised as to why it took the company such a long time to uncover the hacking.
-
3.
Cyber Breach Date: 26-Jan-2016
Centene, a St. Louis-based payer, is searching for six missing hard drives that contain protected health information of approximately 950,000 individuals. The six hard drives contain information of individuals who received laboratory services from 2009 to 2015, including names, addresses, birth dates, Social Security numbers, member ID number and health information. There is no financial or payment information stored on the hard drives, according to the payer. Centene noticed the hard drives were missing when they were unaccounted for in an inventory of IT assets. The hard drives were part of a data project that used laboratory results to improve health outcomes. The payer does not believe the information has been inappropriately used but has launched an ongoing search “out of abundance of caution and in transparency,” according to a media notice.
Rights and permissions
About this article
Cite this article
Leong, YY., Chen, YC. Cyber risk cost and management in IoT devices-linked health insurance. Geneva Pap Risk Insur Issues Pract 45, 737–759 (2020). https://doi.org/10.1057/s41288-020-00169-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1057/s41288-020-00169-4