Abstract
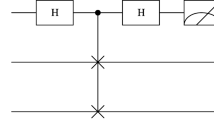
Recently, Lang put forward for the first time a quantum gate-based quantum private comparison (QPC) protocol (Int J Theor Phys, 59(2020)833) which uses the quantum controlled-not gates to implement comparison instead of classical exclusive-or computations. It was claimed that this quantum gate-based QPC protocol is secure against both the outside attack and the participant attack. However, in this paper, it is pointed out that this protocol cannot resist a special measurement attack from the third party (TP) and the disturbance attack from an outside attacker. The corresponding improvements are further suggested to remedy these security loopholes.
Similar content being viewed by others
References
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42, 055305 (2009)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1561–1565 (2010)
Yang, Y.G., Xia, J., Jia, X., Shi, L., Zhang, H.: New quantum private comparison protocol without entanglement. Int J Quantum Inf. 10, 1250065 (2012)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12, 1077–1088 (2013)
Ji, Z.X., Ye, T.Y.: Multi-party quantum private comparison based on the entanglement swapping ofd-level cat states and d-level bell states. Quantum Inf. Process. 16(7), 177 (2017)
Ye, T.Y., Ji, Z.X.: Multi-user quantum private comparison with scattered preparation and one-way convergent transmission of quantum states. Sci. China Phys. Mech. Astron. 60(9), 090312 (2017)
Ye, C.Q., Ye, T.Y.: Multi-party quantum private comparison of size relation withd-level single-particle states. Quantum Inf. Process. 17(10), 252 (2018)
Lang, Y.F.: Quantum gate-based quantum private comparison. Int. J. Theor. Phys. 59, 833–840 (2020)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5), 1049 (2005)
Li, C.Y., Li, X.H., Deng, F.G., Zhou, P., Liang, Y.J., Zhou, H.Y.: Efficient quantum cryptography network without entanglement and quantum memory. Chin. Phys. Lett. 23(11), 2896 (2006)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semi-honest third party. Quantum Inf. Process. 12, 877–885 (2013)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ming-Yi, D. Cryptanalysis and Improvement of Quantum Gate-Based Quantum Private Comparison. Int J Theor Phys 60, 195–199 (2021). https://doi.org/10.1007/s10773-020-04675-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04675-y