Abstract
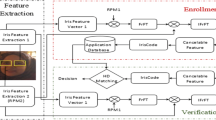
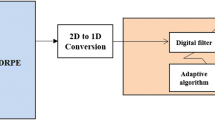
Biometric recognition approaches have overwhelmed major issues in traditional authentication systems. Privacy invasion and security are the needed features in the effective development of biometric recognition systems. Recently some biometric techniques have been suffered to hacking trails also. Hence there is a despairing need to propose a novel cancelable iris recognition scheme. The prime objective of this research is to create a transformed cancelable biometric template through an encryption function and a one-way transformation function. The random projection matrix is employed here to generate the first feature vector. Then an encrypted cancelable iris code is generated using Double Random Phase Encryption (DRPE) in the Fractional Fourier Transform (FFT) domain. The proposed framework utilizes both the left and right iris image of a person and generates a single cancelable iris template. This feature guarantees the privacy-preserving cancelable iris code generation for secure authentication. The experiment is carried on two state-of-art datasets CASIA Iris V4 and IITD iris to affirm the efficacy of the proposed methodology. The result analysis witnessed a promising accuracy of 99.59%, a recognition rate of 99.88% with a lower Equal Error Rate (ERR) of 0.46%. It has also been proved that the proposed approach is computationally efficient as it recognizes the iris code with less recognition time of 7 ms with a maximum true positive and true negative rate of 100%.









Similar content being viewed by others
References
Lakhno V (2018) Modeling of decision making procedure for the financing of cybersecurity means of cloud services by the medium of the bilinear multi-step quality game with several terminal surfaces. Bull Pol Acad Sci 64(4):467–472
Venugopalan S, Savvides M (2011) How to generate spoofed irises from an iris code template. IEEE Trans Inf Forensics Secur 6(2):385–395
Punithavathi P, Subbiah G (2017) Can cancellable biometrics preserve privacy? Biom Technol Today 2017(7):8–11
Gunjan VK, Prasad PS, Mukherjee S (2019). Biometric template protection scheme- cancelable biometrics. Proceedings of the international conference on Communications and cyber-physical engineering pp: 405–411
Rajasekar V, Premalatha J, Sathya K, An Efficient Signcryption Scheme for Secure Authentication using Hyper Elliptic Curve Cryptography and Keccak Hashing, International journal of Recent Technology and Engineering, Vol.8, pp: 1593–1598
Lai YL, Jin Z, Teoh J et al (2017) Cancelable iris template generation based on indexing first one hashing. Pattern Recogn 64:105–117
Randa F Soliman, Mohamed Amin, Fathi E Abd El-Samie (2018). A modified cancelable biometric scheme using random projection, https://doi.org/10.1007/s40745-018-0172-1
Soliman NF, Mohamed E, Magdi F, Abd El-Samie FE, AbdElnaby M (2017) Efficient iris localization and recognition. Optik 140:469–475
Rathgeb C, Breitinger F, Baier H, and Busch C (2015). Towards bloom filter-based indexing of iris biometric data. Proceedings of 15th IEEE international conference on biometrics, pp. 422–429
Tarek M, Ouda O, Hamza T (2017). Pre-image resistant cancelable biometrics scheme using a bidirectional memory model. International Journal of Network Security. Vo.19, No.4, pp: 498–506
An L, Chen X, Yang S, Bhanu B (2016) Sparse representation matching for person re-identification. Information Sciences, pp:74–89
Sandhya M, Prasad M (2017) Cancelable fingerprint cryptosystem using multiple spiral curves and fuzzy commitment scheme. Int J Pattern Recognit Artif Intell 31(4):14–32
Kumar D, Sastry M, Manikantan K (2016). Iris recognition using contrast enhancement and Spectrum-based feature extraction. International conference on emerging trends in engineering, technology, and science, pp. 1–7
Mohammed Hamzah Abed (2017). Iris recognition model based on Principal Component analysis and 2 level Haar wavelet transforms: Case study CUHK and UTIRIS iris databases. pp-485-500
Viriri S, Tapoma J (2017) Iris pattern recognition based on cumulative sums and majority vote methods. Int J Adv Robot Syst 14:172988141770393. https://doi.org/10.1177/1729881417703931
Rajasekar V, Premalatha J, Sathya K 2020 Enhanced Biometric Recognition for Secure Authentication Using Iris Preprocessing and Hyperelliptic Curve Cryptography Wireless Communications and Mobile Computing 2020 1–19
Saracevic M, Adamovic S, Bisevac E (2018) Applications of Catalan numbers and lattice path combinatorial problem in cryptography. Acta Polytech Hung 15(7):91–110
Velmurugan S, Selvarajan S (2018) A multimodal authentication for biometric recognition system using Hybridi fusion techniques. International Journal of Cluster Computing Springer US, ISSN1386-7857
Dwivedi R, Dey S, Singh R, Prasad A (2017) A privacy preserving cancelable iris template generation scheme using decimal encoding and lookup table mapping. Comput Secur 6:373–386
Evans N, Marcel S, Ross A, Teoh ABJ (2015) Biometrics security and privacy protection. IEEE Signal Process Mag 32(5):17–18
Refregier P, Javidi B (1995) Optical image encryption based on input plane and Fourier plane random encoding. Opt Lett 20:767–769
Taheri M, Mozaffari S (2013) Phase mask generation for DRPE method using Chaos theory and hash function. Optik 124:2363–2367
Oshi MJ, Shakher C, Singh K (2008) Color image encryption and decryption for twin images in the fractional Fourier domain. Opt Commun 281(23):5713–5720
CASIA V.4 Iris Image Database Version Three. Available: http://www.cbsr.ia.ac.cn
Ajay Kumar and Arun Passi (2008). Comparison and combination of iris matches for reliable personal identification. Proc. CVPR 2008, Anchorage, Alaska, pp 21–27
Drozdowski P, Garg S, Rathgeb C, Gomez-Barrcro M, Chang D, Busch C (2019) Privacy-preserving indexing of Iris-codeswith cancelable bloom filter-based search structures. In: European signal processing conference (EUSIPCO), vol 26. IEEE, pp 2360–2364
Wu SC, Chen PT, Swindlehurst AL, Hung PL (2018) Cancelable biometric recognition with ECGs: subspacebased approaches. IEEE Trans Inf Forensics Secur 14(5):1323–1336
Lee DH, Lee SH, Cho NI (2019) Cancelable biometrics using noise embedding. In: international conference on pattern recognition (ICPR), vol 24. IEEE, pp 3390–3395
Kumar N, Singh S, Kumar A (2018) Random permutation principal component analysis for cancelable biometric recognition. Appl Intell 48(9):2824–2836
Sudhakar T, Gavrilova M (2020) Cancelable biometrics using deep learning as a cloud service. IEEE Access 8:112932–112943. https://doi.org/10.1109/ACCESS.2020.3003869
Merabet F, Cherif A, Belkadi M, Blazy O, Conchon E, Sauveron D (2020) New efficient M2C and M2M mutual authentication protocols for IoT-based healthcare applications. Peer-to-Peer Netw Applic 13(2):439–474
Rajasekar V, Jayapaul P, Krishnamoorthi S (2019) Cryptanalysis and enhancement of multi factor remote user authentication scheme based on signcryption, Advances in Mathematics of Communications, https://doi.org/10.3934/amc.2020103
Rajasekar V, Premalatha J, Sathya K (2020) Multi-factor signcryption scheme for secure authentication using hyper elliptic curve cryptography and bio-hash function. Bull Pol Ac: Tech 68:4
Funding
The proposed research work was not funded by any organization.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that no conflict of interest exists.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rajasekar, V., Premalatha, J. & Sathya, K. Cancelable Iris template for secure authentication based on random projection and double random phase encoding. Peer-to-Peer Netw. Appl. 14, 747–762 (2021). https://doi.org/10.1007/s12083-020-01046-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-020-01046-6