Abstract
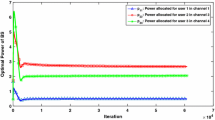
In this paper, jamming and anti-jamming in a time slotted orthogonal frequency division multiple access (OFDMA) are investigated. The users of the network cooperate to mitigate the jamming effect. Interactions among the network users and the jammer are modeled by a mixed integer non-cooperative generalized game which is a NP-hard problem. To relax the problem, a new algorithm is proposed based on channel state information (CSI) to determine the transmission channels and the partners of users in the network. To solve the proposed game, an optimization problem is solved for each player considering the best response of the other player. Another generalized game is proposed to model the cooperation among users of the network. The latter game is transformed to an equivalent Quasi Variational Inequality (QVI). Then, a new gradient based algorithm is proposed by utilizing the Karush-Kuhn-Tucker (KKT) conditions to find the solution of the equivalent QVI. Then, solving the latter game and substituting the best related response, the solution of the former generalized game is also obtained. The convergence of the proposed algorithms, and the uniqueness related to the solution of the both generalized games are proven. Finally, the simulation results confirm the effectiveness of the proposed approach.








Similar content being viewed by others
References
Zhao, N., Guo, J., Yu, F. R., Li, M., & Leung, V. C. M. (2017). Antijamming schemes for interference-alignment-based wireless networks. IEEE Transaction on Vehicular Technology, 66(2), 1271–1283.
Nadendla, V. S. S., Sharma, V., & Varshney, P. K. (2017). On strategic multi-antenna jamming in centralized detection networks. IEEE Signal Processing Letters, 24(2), 186–190.
Wei, S., Kannan, R., Chakravarthy, V., & Rangaswamy, M. (2012). CSI usage over parallel fading channels under jamming attacks: A game theory study. IEEE Transactions on Communications, 60(4), 1167–1175.
Altman, E., Avrachenkov, K., & Garnaev, A. (2007). A jamming game in wireless networks with transmission cost. Proceedings of Lecture Notes in Computer Science, 4465, 1–12.
Boyd, S., & Vandenberghe, L. (2004). Convex optimization. Cambridge, United Kingdom: Cambridge University Press.
Altman, E., Avrachenkovand, K., & Garnaev, A. (May 2009). Jamming in wireless networks: The case of several jammers. IEEE Conference on Game Theory of Networks, (pp 585–592).
Altman, E., Avrachenkov, K., & Garnaev, A. (2011). Jamming in wireless networks under uncertainty. Mobile Network Application, 16, 246–254.
Shafiee, S., & Ulukus, S. (2009). Mutual information games in multiuser channels with correlated jamming. IEEE Transactions on Information Theory, 55(10), 4598–4607.
Kashyap, A., Basar, T., & Srikant, R. (2004). Correlated jamming on MIMO gaussian fading channels. IEEE Transactions on Information Theory, 50(9), 2119–2123.
Yang, D., Xue, G., Zhang, J., Richa, A., & Fang, X. (2013). Coping with a smart jammer in wireless networks: A stackelberg game approach. IEEE Transaction on Wireless Communications, 12(8), 4038–4047.
Xiao, L., Chen, T., Liu, J., & Dai, H. (2015). Anti-jamming transmission stackelberg game with observation errors. IEEE Communication Letter, 19(6), 949–952.
Anand, S., Sengupta, S., & Chandramouli, R. (2010). An attack-defense game theoretic analysis of multi-band wireless covert timing networks. IEEE International Conference on Information and Communication, (1–9).
Oro, S. D., Galluccio, L., Morabito, G., Palazzo, S., Chen, L., & Martignon, F. (2015). Defeating jamming with the power of silence: A game-theoretic analysis. IEEE Transaction on Wireless Communications, 14(5), 2337–2352.
Fang, Zh, Song, T., & Li, T. (2015). Energy harvesting for two-way OFDM communications under hostile jamming. IEEE Signal Processing Letters, 22(4), 413–416.
Rezgui, G., Belmega, E. V., & Chorti, A. (2019). Mitigating jamming attacks using energy harvesting. IEEE Wireless Communications Letters, 8(1), 297–300.
Noori, H., & Sharafat, A. R. (2017). Proportional fairness in MC-CDMA networks in the presence of jammers: A game theoretic approach. Iranian Journal of Science and Technology, Transactions of Electrical Engineering Springer, 41(4), 267–282.
Pelechrinis, K., Koufogiannakis, Ch., & Krishnamurthy, S. V. (2009). Gaming the jammer: Is frequency hopping effective?. IEEE Conference on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, WiOPT, (pp 1–10).
Popper, Ch., Strasser, M., & Capkun, S. (2010). Anti-jamming broadcast communication using uncoordinated spread spectrum techniques. IEEE Journal on Selected Areas in Communications, 28(5), 703–715.
Li, H., & Han, Z. (2010). Dogfight in spectrum: Combating primary user emulation attacks in cognitive radio systems, Part I: Known channel statistics. IEEE Transactions on Wireless Communications, 9(11), 3566–3577.
Li, H., & Han, Z. (2011). Dogfight in spectrum: Combating primary user emulation attacks in cognitive radio systems, Part II: Unknown channel statistics. IEEE Transactions on Wireless Communications, 10(1), 274–283.
Zhu, Q., Li, H., Han, Z., & Basar, T. (2010). A stochastic game model for jamming in multi-channel cognitive radio systems. Proceedings of IEEE ICC, 2010, 1–6.
Chen, Ch., Song, M., Xin, Ch., & Backens, J. (2013). A game-theoretical anti-jamming scheme for cognitive radio networks. IEEE Network, 27(3), 22–27.
Wu, Y., Wang, B., Liu, K. J. R., & Clancy, T. C. (2012). Anti-jamming games in multi-channel cognitive radio networks. IEEE Journal on Selected Areas in Communications, 30(1), 4–15.
Hanawal, M. K., Abdel-Rahman, M. J., & Krunz, M. (2015). Joint adaptation of frequency hopping and transmission rate for anti-jamming wireless systems. IEEE Transaction on Mobile Computing, PP(99), 1–14.
Wang, B., Wu, Y., Liu, K. J. R., & Clancy, T. C. (2011). An anti-jamming stochastic game for cognitive radio networks. IEEE Journal on Selected Areas in Communications, 29(4), 877–889.
Noori, H., & Vilni, Saeed Sadeghi. (May 2019). Defense against intelligent jammer in cognitive wireless networks. 27th Iranian Conference on electrical engineering (ICEE2019), pp. xx – xx.
Xiao, L., Dai, H., & Ning, P. (2012). Jamming-resistant collaborative broadcast using uncoordinated frequency hopping. IEEE Transaction on Information Forensics and Security, 7(1), 297–309.
Zhang, L., Guan, Z., & Melodia, T. (2016). United against the enemy: Anti-jamming based on cross-layer cooperation in wireless networks. IEEE Transaction on Wireless Communications, 15(8), 5733–5747.
Hasna, M. O., & Alouini, M. S. (2003). End-to-end performance of transmission systems with relays over Rayleigh-fading channel. IEEE Transaction on Wireless Communication, 2(6), 1126–1131.
Korte, B., & Vygen, J. (2008). Combinatorial optimization: Theory and algorithms (2nd ed.). New York: Springer.
Mohnram, T. C., & Bhashyam, S. (2005). A sub-optimal joint subcarrier and power allocation algorithm for multiuser OFDM. IEEE Communication Letter, 9(8), 685–687.
Boyd, S., & Vandenberghe, L. (2004). Convex optimization. Cambridge: Cambridge University Press.
Facchinei, F., & Kanzow, C. (2007). Generalized nash equilibrium problems. 4OR, 5(3), 173–210.
Bertsekas, D. P., & Tsitsiklis, J. N. (2000). Gradient convergence in gradient methods with errors. Industrial and Applied Mathematics, 10(3), 627–642.
Ng, D. W. K., Lo, E., & Schober, R. (2012). Energy-efficient resource allocation in OFDMA systems with large numbers of base station antennas. IEEE Transaction Wireless Communication, 11(9), 3292–3304.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The authors are with the Department of Electrical Engineering, Vali-e-Asr University of Rafsanjan, Rafsanjan, Kerman, Iran.
Appendices
Appendix A: Proof of Theorem 1
Proof
To prove, the convexity of the utility function, and also, the convexity of the constraint should be proved.
Lemma 1
The objective function of problem (28) is a concave function of \((p_{i,1}^{k},p_{i,2}^{k})\).
Proof
The Hessian matrix of objective function in (28) is as:
which is negative definite, hence, the objective function of (28) is a concave function. \(\square \)
According to lemma 1, the utility function is convex. Also, since the constraint C1 is an affine function, it is also a convex function. Consequently, the problem (28) is a convex optimization problem. \(\square \)
Appendix B: Proof of Theorem 3
Proof
In the proposed scenario, the sets \(T_{i}\) are composed from the constraint \(\mathcal {C}2\). The sets are nonempty, closed and continuous. Since the constraint \(\mathcal {C}2\) is affine in terms of \(p_{i,1}^{k}\) and \(\alpha _{i}\), it is convex. Thus, the sets \(T_{i}\) satisfy the condition in the theorem 2. Additionally, for the utility function of players in the game \(\tilde{\mathcal {G}}\), we have:
Lemma 2
The objective function of problem (32) is a concave function of \((p_{i,1}^{k},\alpha _{i})\).
Proof
The Hessian matrix of (32) with respect to \((p_{i,1}^{k},\alpha _{i})\) is:
which is negative definite. Thus, the problem is concave. \(\square \)
Since the utility function of all players are convex, and Also, quasi-convex, the conditions of Theorem 2 are fulfilled. It leads that the generalized game \(\tilde{\mathcal {G}}\) has a generalized Nash equilibrium. \(\square \)
Appendix C: Proof of Theorem 5
Proof
To prove the convexity of the jammer problem, it is proven that the objective function and the constraint function are convex.
Lemma 3
The objective function of problem (21) is a convex function of \((j_{1}^{k},j_{2}^{k})\).
Proof
The Hessian of (21) with respect to \((j_{1}^{k},j_{2}^{k})\) is:
which is positive definite, hence, the objective function of (21) is a convex one. \(\square \)
Since the objective function of the jammer is convex, and the constraint \(\mathcal {C}3\) is affine, the jammer problem is a convex optimization problem. \(\square \)
Appendix D: Proof of Theorem 7
Proof
To prove the theorem, consider the following definition and theorem.
Definition 3
The gradient of f is Lipschitz continuous with parameter \(L > 0\) if [35]
Theorem 8
To solve (46), the gradient method converges when the utility functions satisfy the following conditions:
-
Utility function is convex and differentiable with its domain.
-
\(\nabla u_{i}\) is Lipschitz continuous with parameter \(L \ge 0\).
-
Optimal value is finite and attained.
Proof
Please refer to [34]. \(\square \)
Since the utility functions of both the users and the jammer are logarithmic functions, the related convexity and differentiability are clear. Additionally, the optimal value for both players are finite due to their power constraints and logarithmic form of the utility function. Therefore, if the gradient of utility function is Lipschitz continuous with parameter L, the proposed problem satisfies the above conditions. Thus, the convergence of the proposed algorithm is proven.
Based on Sect. 4, the utility function of all users of the network and the utility of the jammer are the sum of two logarithm functions that is as the logarithm of the product of arguments, which is a logarithm function. As it is proven in the lemma 4, the logarithm function is a gradient Lipschitz function. Note that, in the lemma 4, the proof holds when the argument of the logarithm is in \((1,\infty )\), which is satisfied here. Thus, the utility function of the players are gradient Lipschitz and the proposed algorithm converges. \(\square \)
Lemma 4
The logarithm function \(\log (x)\) is a gradient Lipschitz function.
Proof
Let \(d,f \in (1,\infty )\). Based on the mean value theorem, there is a point e such that:
Hence, we have:
Therefore, the gradient of the \(log(\cdot )\) is a Lipschitz function, and then, the \(log(\cdot )\) is a gradient Lipschitz function. \(\square \)
Rights and permissions
About this article
Cite this article
Noori, H., Gholizadeh, M.H. User cooperation to mitigate the jamming in OFDMA networks. Wireless Netw 27, 1215–1231 (2021). https://doi.org/10.1007/s11276-020-02519-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-020-02519-5