Abstract
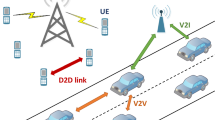
Automotive cyber physical systems (CPSs) are ever more utilizing wireless technology for V2X communication as a potential way out for challenges regarding collision detection, wire strap up troubles and collision avoidance. However, security is constrained as a result of the energy and performance limitations of modern wireless systems. Accordingly, the need for efficient secret key generation and management mechanism for secured communication among computationally weak wireless devices has motivated the introduction of new authentication protocols. Recently, there has been a great interest in physical layer based secret key generation schemes by utilizing channel reciprocity. Consequently, it is observed that the sequence generated by two communicating parties contain mismatched bits which need to be reconciled by exchanging information over a public channel. This can be an immense security threat as it may let an adversary attain and recover segments of the key in known channel conditions. We proposed Hopper-Blum based physical layer (HB-PL) authentication scheme in which an enhanced physical layer key generation method integrates the Hopper-Blum (HB) authentication protocol. The information collected from the shared channel is used as secret keys for the HB protocol and the mismatched bits are used as the induced noise for learning parity with noise (LPN) problem. The proposed scheme aims to provide a way out for bit reconciliation process without leakage of information over a public channel. Moreover, HB protocol is computationally efficient and simple which helps to reduce the number of exchange messages during the authentication process. We have performed several experiments which show that our proposed design can generate secret keys with improved security strength and high performance in comparison to the current authentication techniques. Our scheme requires less than 55 exchange messages to achieve more than 95% of correct authentication.
Similar content being viewed by others
References
Gao Z, Chen D, Cai S, Wu H C. Optdynlim: an optimal algorithm for the one-dimensional RSU deployment problem with nonuniform profit density. IEEE Transactions on Industrial Informatics, 2018, 15(2): 1052–1061
Gao Z, Chen D, Cai S, Wu H C. Optimal and greedy algorithms for the one-dimensional RSU deployment problem with new model. IEEE Transactions on Vehicular Technology, 2018, 67(8): 7643–7657
Qiu J, Du L, Zhang D, Su S, Tian Z. Nei-tte: intelligent traffic time estimation based on fine-grained time derivation of road segments for smart city. IEEE Transactions on Industrial Informatics, 2019, 16(4): 2659–2666
Tian Z, Shi W, Wang Y, Zhu C, Du X, Su S, Sun Y, Guizani N. Realtime lateral movement detection based on evidence reasoning network for edge computing environment. IEEE Transactions on Industrial Informatics, 2019, 15(7): 4285–4294
Tian Z, Su S, Shi W, Du X, Guizani M, Yu X. A data-driven method for future internet route decision modeling. Future Generation Computer Systems, 2019, 95: 212–220
Lin C, Rao L, Giusto P, D’Ambrosio J, Sangiovanni-Vincentelli A L. Efficient wire routing and wire sizing for weight minimization of automotive systems. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2015, 34(11): 1730–1741
Dar K, Bakhouya M, Gaber J, Wack M, Lorenz P. Wireless communication technologies for its applications [topics in automotive networking]. IEEE Communications Magazine, 2010, 48(5): 156–162
ElBatt T, Saraydar C, Ames M, Talty T. Potential for intra-vehicle wireless automotive sensor networks. In: Proceedings of IEEE Sarnoff Symposium. 2006, 1–4
Wang S, Yao N, Gong N, Gao Z. A trigger-based pseudonym exchange scheme for location privacy preserving in vanets. Peer-to-Peer Networking and Applications, 2018, 11(3): 548–560
Li M, Sun Y, Lu H, Maharjan S, Tian Z. Deep reinforcement learning for partially observable data poisoning attack in crowdsensing systems. IEEE Internet of Things Journal, 2020, 7(7): 6266–6278
Tian Z, Luo C, Qiu J, Du X, Guizani M. A distributed deep learning system for web attack detection on edge devices. IEEE Transactions on Industrial Informatics, 2020, 16(3): 1963–1971
Tian Z, Gao X, Su S, Qiu J. Vcash: a novel reputation framework for identifying denial of traffic service in internet of connected vehicles. IEEE Internet of Things Journal, 2019, 7(5): 3901–3909
Tan Q, Gao Y, Shi J, Wang X, Fang B, Tian Z. Toward a comprehensive insight into the eclipse attacks of tor hidden services. IEEE Internet of Things Journal, 2018, 6(2): 1584–1593
Shen C, Li Y, Chen Y, Guan X, Maxion R A. Performance analysis of multi-motion sensor behavior for active smartphone authentication. IEEE Transactions on Information Forensics and Security, 2017, 13(1): 48–62
Shen C, Chen Y, Guan X, Maxion R. Pattern-growth based mining mouse-interaction behavior for an active user authentication system. IEEE Transactions on Dependable and Secure Computing, 2020, 17(2): 335–349
Smolyakov A D, Sulimov A I, Karpov A V, Sherstyukov O N. Experimental verification of possibility of secret encryption keys distribution with a phase method in a multipath environment. In: Proceedings of International Siberian Conference on Control and Communications. 2013, 1–5
Jegatheesan A, Sonikha P. Secure and efficient key sharing scheme for manet using a symmetric approach. In: Proceedings of International Conference on Emerging Trends and Innovations In Engineering and Technological Research. 2018, 1–7
Zhan F, Yao N, Gao Z, Lu Z, Chen B. Efficient key generation leveraging channel reciprocity and balanced gray code. Wireless Networks, 2019, 25(2): 611–624
Qiu J, Tian Z, Du C, Zuo Q, Su S, Fang B. A survey on access control in the age of internet of things. IEEE Internet of Things Journal, 2020, 7(6): 4682–4696
Jiang X, Yang S, Huang P, Zeng G. High-speed reconciliation for cvqkd based on spatially coupled ldpc codes. IEEE Photonics Journal, 2018, 10(4): 1–10
Sayeed A, Perrig A. Secure wireless communications: secret keys through multipath. In: Proceedings of IEEE International Conference on Acoustics, Speech and Signal Processing. 2008, 3013–3016
Liu Y, Draper S C, Sayeed A M. Secret key generation through OFDM multipath channel. In: Proceedings of the 45th Annual Conference on Information Sciences and Systems. 2011, 1–6
Hassan A A, Stark W E, Hershey J E, Chennakeshu S. Cryptographic key agreement for mobile radio. Digital Signal Processing, 1996, 6(4): 207–212
Azimi-Sadjadi B, Kiayias A, Mercado A, Yener B. Robust key generation from signal envelopes in wireless networks. In: Proceedings of the 14th ACM Conference on Computer and Communications Security. 2007, 401–410
Mathur S, Trappe W, Mandayam N, Ye C, Reznik A. Radio-telepathy: extracting a secret key from an unauthenticated wireless channel. In: Proceedings of the 14th ACM International Conference on Mobile Computing and Networking. 2008, 128–139
Premnath S N, Jana S, Croft J, Gowda P L, Clark M, Kasera S K, Patwari N, Krishnamurthy S V. Secret key extraction from wireless signal strength in real environments. IEEE Transactions on Mobile Computing, 2013, 12(5): 917–930
Panhwar M A, Deng Z, Khuhro S A, Hakro D N. Distance based energy optimization through improved fitness function of genetic algorithm in wireless sensor network. Studies in Informatics and Control, 2018, 27(4): 461–468
Lv S, Lu X, Lu Z, Wang X, Wang N, Sun L. Zero reconciliation secret key extraction in mimo backscatter wireless systems. In: Proceedings of IEEE International Conference on Communications. 2016, 1–6
Wang Q, Su H, Ren K, Kim K. Fast and scalable secret key generation exploiting channel phase randomness in wireless networks. In: Proceedings of IEEE INFOCOM. 2011, 1422–1430
Patwari N, Croft J, Jana S, Kasera S K. High-rate uncorrelated bit extraction for shared secret key generation from channel measurements. IEEE Transactions on Mobile Computing, 2010, 9(1): 17–30
Zeng K, Wu D, Chan A, Mohapatra P. Exploiting multiple-antenna diversity for shared secret key generation in wireless networks. In: Proceedings of IEEE INFOCOM. 2010, 1–9
Ren K, Su H, Wang Q. Secret key generation exploiting channel characteristics in wireless communications. IEEE Wireless Communications, 2011, 18(4): 6–12
Pacher C, Grabenweger P, Martinez-Mateo J, Martin V. An information reconciliation protocol for secret-key agreement with small leakage. In: Proceedings of IEEE International Symposium on Information Theory. 2015, 730–734
Brassard G, Salvail L. Secret-key reconciliation by public discussion. In: Proceedings of Workshop on the Theory and Application of of Cryptographic Techniques. 1993, 410–423
Martinez-Mateo J, Pacher C, Peev M, Ciurana A, Martin V. Demystifying the information reconciliation protocol cascade. Quantum Information and Computation, 2015, 15(5&6): 0453–0477
Toyran M. A study on information reconciliation problem in quantum key distribution. In: Proceedings of the 24th Signal Processing and Communication Application Conference. 2016, 157–160
Zhang M, Shen C, Wu Z G, Zhang D. Dissipative filtering for switched fuzzy systems with missing measurements. IEEE Transactions on Cybernetics, 2019, 50(5): 1931–1940
Juels A, Weis S A. Authenticating pervasive devices with human protocols. In: Proceedings of Annual International Cryptology Conference. 2005, 293–308
Hopper N J, Blum M. Secure human identification protocols. In: Proceedings of International Conference on the Theory and Application of Cryptology and Information Security. 2001, 52–66
Blum A, Furst M, Kearns M, Lipton R J. Cryptographic primitives based on hard learning problems. In: Proceedings of Annual International Cryptology Conference. 1993, 278–291
Guo Q, Johansson T, Lindahl C. A new algorithm for solving ring-lpn with a reducible polynomial. IEEE Transactions on Information Theory, 2015, 61(11): 6204–6212
Bringer J, Chabanne H, Dottax E. HB++: a lightweight authentication protocol secure against some attacks. In: Proceedings of the 2nd International Workshop on Security, Privacy and Trust in Pervasive and Ubiquitous Computing. 2006, 28–33
Piramuthu S. HB and related lightweight authentication protocols for secure RFID tag/reader authentication title. In: Proceedings of CollECTeR Europe. 2006, 238–239
Piramuthu S, Tu Y. Modified HB authentication protocol. In: Proceedings of Western European Workshop on Research in Cryptology. 2007, 41–42
Munilla J, Peinado A. HB-MP: a further step in the HB-family of lightweight authentication protocols. Computer Networks, 2007, 51(9): 2262–2267
Leng X, Mayes K, Markantonakis K. HB-MP+ protocol: an improvement on the HB-MP protocol. In: Proceedings of IEEE International Conference on RFID. 2008, 118–124
Rizomiliotis P. HB-MAC: improving the random-hb# authentication protocol. In: Proceedings of International Conference on Trust, Privacy and Security in Digital Business. 2009, 159–168
Abyaneh M R S. On the security of non-linear HB (NLHB) protocol against passive attack. In: Proceedings of IEEE/IFIP International Conference on Embedded and Ubiquitous Computing. 2010, 523–528
Bosley C, Haralambiev K, Nicolosi A. HBN: an HB-like protocol secure against man-in-the-middle attacks. IACR Cryptology ePrint Archive. 2011, 349–350
Rizomiliotis P, Gritzalis S. GHB#: a provably secure HB-like lightweight authentication protocol. In: Proceedings of International Conference on Applied Cryptography and Network Security. 2012, 489–506
Lin Z, Song J S. An improvement in HB-family lightweight authentication protocols for practical use of RFID system. Journal of Advances in Computer Networks, 2013, 1(1): 61–65
Ka A K. hHB: a harder HB+ protocol. In: Proceedings of the 12th International Joint Conference on e-Business and Telecommunications. 2015, 163–169
Blum A, Kalai A, Wasserman H. Noise-tolerant learning, the parity problem, and the statistical query model. Journal of the ACM (JACM), 2003, 50(4): 506–519
Regev O. On lattices, learning with errors, random linear codes, and cryptography. Journal of the ACM (JACM), 2009, 56(6): 33–34
Acknowledgements
This work was supported by the Shandong Provincial Key Research and Development Program of China (2018CXGC0701), the National Natural Science Foundation of China (NSFC) (Grant No. 61972050), and the foundation of State Key Laboratory of Network and Switching Technology, Beijing University of Posts and Telecommunications (SKLNST-2018-1-11).
Author information
Authors and Affiliations
Corresponding author
Additional information
Ahmer Khan Jadoon received his Bachelor degree from COMSATS Institute of Information Technology, Pakistan in 2010 and the MS degree in Information and Communication Engineering from University of Electronic Science and Technology of China (UESTC). He is currently a PhD student in School of Computer Science at Beijing University of Posts and Telecommunications, China. His current research interest includes information security, vehicular security and light-weight Cryptography.
Jing Li received the BS degree from Inner Mongol Normal University in 2010, the MS degree from Shanxi Normal University, China in 2013 and PhD degree in Beijing University of Posts and Telecommunications, China. Currently, she works at Guangzhou University, China. Her research interests include cloud computing, applied cryptography and privacy-preserving, etc.
Licheng Wang received the BS degree from Northwest Normal University, China in 1995, the MS degree from Nanjing University, China in 2001, and the PhD degree from Shanghai Jiao Tong University, China in 2007. He is an associate professor in Beijing University of Posts and Telecommunications, China. His current research interests include modern cryptography, network security, trust management, etc.
Electronic Supplementary Material
Rights and permissions
About this article
Cite this article
Jadoon, A.K., Li, J. & Wang, L. Physical layer authentication for automotive cyber physical systems based on modified HB protocol. Front. Comput. Sci. 15, 153809 (2021). https://doi.org/10.1007/s11704-020-0010-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11704-020-0010-4