Abstract
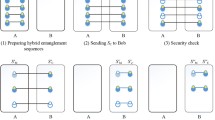
Quantum identity authentication key agreement (QIAKA) protocols are designed to allow two nodes to establish a secure secret key when they require few resources, such as a few shared secret bits, and it is technologically feasible. However, the existing studies have two main flaws: they divided quantum identity authentication and key agreement into two realms to research, not integrated them. On the other side, the existing quantum identity authentication has many safety loopholes with inefficiency. In this paper, we firstly devise a quantum identity authentication key agreement protocol without entanglement to improve the efficiency and wipe out any node to know the session key expect the involved parties. In our proposed protocol, through revising the mode and parameters, both the security and efficiency are improved greatly. Furthermore, the short shared secret key is dynamic change at the end of the proposed protocol. Compared with the related literature recently, our proposed scheme can not only own high efficiency and unique functionality, but is also robust to various attacks and the security proof is suitable for the single-state QIAKA protocol.

Similar content being viewed by others
References
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Grover, L.K.: Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 79(2), 325 (1997)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers Systems and Signal Processing, Bangalore, India, pp. 175–179 (1984)
Zeng, G., Zhang, W.: Identity verification in quantum key distribution. Phys. Rev. A 61, 022303 (2000)
Sasaki, T., Yamamoto, Y., Koashi, M.: Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509, 475 (2014)
Hwang, T., Lee, K.C., Li, C.M.: Provably secure three-party authenticated quantum key distribution protocols. IEEE Trans. Dependable Secure Comput. 4(1), 71 (2007)
Guan, D.J., Wang, Y.-J., Zhuang, E.S.: A practical protocol for three-party authenticated quantum key distribution. Quantum Inf. Process. 13, 2355–2374 (2014)
Cao, G., Chen, C., Jiang, M.: A scalable and flexible multi-user semi-quantum secret sharing. In: ICTCE 2018 Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering, pp. 28–32 (2018)
Clancy, T.C., McGwier, R.W.: TUTORIAL: Post-Quantum Cryptography and 5G Security, May 15–17, 2019. ACM. ISBN 978-1-4503-6726-4/19/05. https://doi.org/10.1145/3317549.3324882
Prousalis, K., Konofaos, N.: Improving the sequence alignment method by quantum multi-pattern recognition. In: Proceeding SETN ‘18, Proceedings of the 10th Hellenic Conference on Artificial Intelligence, No. 50, July 09–12 (2018)
Mandal, K., Fan, X., Gong, G.: Warbler: a lightweight pseudorandom number generator for EPC C1 GEN2 tags. Cryptol. Inf. Secur. 2, 73–84 (2012)
Jannati, H., Ardeshir-Larijani, E.: Detecting relay attacks on RFID communication systems using quantum bits. Quantum Inf. Process. 15(11), 1–13 (2016)
Tsai, M.F., Chilamkurti, N., Shieh, C.K.: An adaptive packet and block length forward error correction for video streaming over wireless networks. Wirel. Pers. Commun. 56(3), 435–446 (2011)
Zhang, P., Aungskunsiri, K., Martinlopez, E., Wabnig, J., Lobino, M., Nock, R.W., et al.: Reference-frame-independent quantum-key-distribution server with a telecom tether for an on-chip client. Phys. Rev. Lett. 112(13), 1153–1165 (2014)
Choi, C.: Google and NASA launch quantum computing AI lab. MIT Technology Review (May 16, 2013)
Linn, A.: The future is quantum: Microsoft releases free preview of quantum development kit. (Dec. 11, 2017). https://bit.ly/2C3fxv3//
Brooks, M.: Quantum computers buyers’ guide: Buy one today. New Scientist (Oct. 15, 2014)
Cusumano, M.A.: The business of quantum computing. Commun. ACM 61(10), 20–22 (2018)
Curty, M., Santos, D.J.: Quantum authentication of classical messages. Phys. Rev. A 64, 062309 (2001)
Wang, S., Yin, Z.Q., Chen, W., He, D.Y., Song, X.T., Li, H.W., Zhang, L.J., Zhou, Z., Guo, G.C., Han, Z.F.: Experimental demonstration of a quantum key distribution without signal disturbance monitoring. Nat. Photonics 9, 832–836 (2015)
Stucki, D., Gisin, N., Guinnard, O., Ribordy, G., Zbinden, H.: Quantum key distribution over 67 km with a plug and play system. New J. Phys. 4, 41 (2002)
Xu, G., Chen, X., Dou, Z., et al.: A novel protocol for multiparty quantum key management. Quantum Inf. Process. 14, 2959–2980 (2015)
Shen, D.S., Ma, W.P., Wang, L.L.: Two-party quantum key agreement with four-qubit cluster states. Quantum Inf. Process. 13, 2313–2324 (2014)
Min, S.Q., Chen, H.Y., Gong, L.H.: Novel multi-party quantum key agreement protocol with G-Like states and Bell states. Int. J. Theor. Phys. 57, 1811–1822 (2018)
Gang, X., Xiu-Bo, C., Zhao, D., et al.: Novel criteria for deterministic remote state preparation via the entangled six-qubit state. Entropy 18(7), 267 (2016)
Hong, C.H., Heo, J., Jang, J.G., Kwon, D.: Quantum identity authentication with single photon. Quantum Inf. Process. 16(10), 236 (2017)
Schwinger, J.: Unitary operator bases. Proc. Natl. Acad. Sci. U. S. A. 46(4), 570 (1960)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Modern Phys. 74, 145–190 (2002)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299, 802–803 (1992)
Bresson, E., Chevassut, O., Pointcheval, D., Quisquater, J.-J.: Provably authenticated group Diffie–Hellman key exchange. In: Proceedings of Eighth ACM Conference Computer and Communications Security, pp. 255–264 (2001)
Lin, J., Hwang, T.: New circular quantum secret sharing for remote agents. Quantum Inf. Process. 12(1), 685–697 (2013)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85, 5633–5638 (2000)
Zha, X., Yuan, C., Zhang, Y.: Generalized criterion for a maximally multi-qubit entangled state. Laser Phys. Lett. 10, 045201 (2013)
Borras, A., Plastino, A.R., Batle, J.: Multiqubit systems: highly entangled states and entanglement distribution. J. Phys. A Math. Theor. 40, 13407 (2007)
Acknowledgements
This work was supported by the Liaoning Provincial Natural Science Foundation of China (Grant No. 2019-MS-286) and Basic Scientific Research Project of Liaoning Provincial Department of Education (2020).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhu, H., Wang, L. & Zhang, Y. An efficient quantum identity authentication key agreement protocol without entanglement. Quantum Inf Process 19, 381 (2020). https://doi.org/10.1007/s11128-020-02887-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02887-z