Abstract
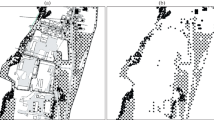
The case of analysis of associatively protected cartographic scenes is considered. Protection of objects and their coordinates is achieved masking binary matrices of their code symbols. The set of inverse mask matrices is the recognition key. This allows such protection to be attributed to associative steganography. A message is considered to be unconditionally steadfast if it is statistically indistinguishable from a random sequence. Therefore, the study of its steadfastness is carried out using statistical tests of randomness NIST. If a pseudo-random sequence successfully passes the test of all 15 tests, then it is considered random (‘‘white’’). If there is a failure at least on one test, then it is considered ‘‘black’’. But in the case of the application of the basic masking algorithm, this cannot help the disclosure of the stegomessage. The effect of masking redundancy introduced with the aim of improving noise immunity on the durability of mapping objects to the effects of various attacks is considered. It is established that associative steganography retains the property of provable (computational) stability in this case as well. Recommendations for its use to protect the text characteristics of objects are given.




Similar content being viewed by others
REFERENCES
V. A. Raikhlin, I. S. Vershinin, R. F. Gibadullin, and S. V. Pystogov, ‘‘Reliable recognition of masked binary matrices. Connection to information security in map systems,’’ Lobachevskii J. Math. 34, 319–325 (2013).
V. A. Raikhlin, I. S. Vershinin, R. F. Gibadullin, and S. V. Pystogov, ‘‘Reliable recognition of masked cartographic scenes during transmission over the network,’’ in Proceedings of the IEEE 2016 International Siberian Conference on Control and Communications SIBCON, May 2016. https://doi.org/10.1109/ICIEAM.2018.8728629
V. A. Raikhlin, I. S. Vershinin, and R. F. Gibadullin, ‘‘The elements of associative steganography theory,’’ Mosc. Univ. Comput. Math. Cybern. 43, 40–46 (2019).
C. E. Shannon, ‘‘Communication theory of secrecy systems,’’ Bell Syst. Tech. J. 28, 656–715 (1949).
R. O. Duda and P. E. Hart, Pattern Classification and Scene Analysis (Wiley, New York, 1973).
M. Matsumoto, M. Saito, H. Haramoto, and T. Nishimura, ‘‘Pseudorandom number generation: impossibility and compromise,’’ J. Univ. Comput. Sci. 12, 672–690 (2006).
D. A. Ker, ‘‘A capacity result for batch steganography,’’ IEEE Signal Process. Lett. 14 (8D), 525–528 (2007).
L. Bassham, A. Rukhin, J. Soto, J. Nechvatal, M. Smid, E. Barker, S. Leigh, M. Levenson, M. Vangel, D. Banks, N. Heckert, and J. Dray, ‘‘A statistical test suite for random and pseudorandom number generators for cryptographic applications,’’ (2010). https://doi.org/10.6028/NIST.SP.800-22r1a
U. Maurer, ‘‘A universal statistical test for random bit generators,’’ J. Cryptol. 5, 89–105 (1992).
J. K. M. Sadique and Uz Zaman, R. Ghosh, ‘‘Review on fifteen statistical tests proposed by NIST,’’ J. Theor. Phys. Cryptogr. 1, 18–31 (2012).
K. Gyarmati, ‘‘On a pseudorandom property of binary sequences,’’ Ramanujan J., No. 8, 289–302 (2004).
I. S. Vershinin, ‘‘Elaboration of the criterion of redundancy of noise-resistant information hiding within associative steganography,’’ Inform. Secur. 19, 511–514 (2016).
E. S. Wentzel, Probability Theory, Textbook for Universities, 6th ed. (Imported, Moscow, 1987).
V. A. Raikhlin, I. S. Vershinin, R. S. Minyazev, and R. F. Gibadullin, Constructive Modeling of Computer Science Systems, 6th ed. (Nauka, Kazan, 2016) [in Russian].
A. P. Alferov, A. Yu. Zubov, A. S. Kuzmin, and A. V. Cheremushkin, Basics of Cryptography, Textbook, 2nd ed. (Helios ARV, Moscow, 2002) [in Russian].
S. V. Pystogov, DBMS MapCluster. https://github.com/pystogov/MapCluster. Accessed 2019.
Author information
Authors and Affiliations
Corresponding authors
Additional information
(Submitted by F. M. Ablaev)
Appendices
NIST TEST SUMMARY
No. | Statistical test | Test statistics c(S) | Detectable defect |
|---|---|---|---|
1 | Frequency (monobit) test | Normalized absolute sum of sequence element values | Too many zeros or ones in the sequence |
2 | Frequency test inside unit | Measure of matching observed number of units inside block with theoretically expected | Localized deviations of frequency of occurrence of units in block from the ideal value of 1/2 |
3 | Check cumulative sums | Maximum deviation of the accumulated amount of elements in a sequence from an initial reference point | Large value of ones or zeros at the beginning or end of a binary sequence |
4 | Series check | Total number of series for entire length of sequence | Too fast or too slow reversal during sequence generation |
5 | Check maximum length of series in block | Measure matching observed value of maximum length of single series with theoretically expected value | Deviation from theoretical distribution of maximum lengths of series of units |
6 | Checking rank of binary matrix | Measure matching observed value of different order of ranks from theoretically expected | Deviation of empirical law of value distribution of matrix ranks from theoretical, which indicates dependence of characters in the sequence |
7 | Spectral test based on the discrete Fourier transform | Normalized difference between the observed and expected number of frequency components that exceed 95% threshold level | Identification of periodic components (trends) in binary sequence |
8 | Check overlapping patterns | Measure of matching the observed number of overlapping patterns in sequence with the theoretical value | Large number of m-bit series of units in the sequence |
9 | Maurer’s universal test | Sum of logarithm of distance between l-bit patterns | Sequence compressibility |
10 | Entropy test | Measure matching observed value of entropy source with the theoretically expected for random source | Uneven distribution of m-bit words in sequence (regularity of source properties) |
11 | Checking random deviations | Measure matching observed number of visits random walk in predetermined state inside loop with theoretically expected | Deviation from theoretical law of distribution of visits to particular state by random walk |
12 | Check random deviations (option) | Total number of visits to given state by random walk | Deviation from theoretical expected total number of visits in case of random walk to given state |
13 | Sequential test | Measure matching observed number of all variants encountered m-bit patterns with theoretically expected | Uneven distribution of m-bit words in sequence |
14 | Checking non-overlapping patterns | Measure matching observed number of non-periodic patterns in sequence with theoretical value | Large number of specified non-periodic patterns in the sequence |
15 | Linear complexity check | Measure matching observed number of events is appearance of fixed length equivalent linear recurrence register for given block with theoretically expected | Deviation of empirical distribution of lengths of equivalent linear recurrent registers for a sequence of fixed length from theoretical distribution law for random sequence, which indicates insufficient complexity of test sequence |
NOTE ABOUT THE APPLICABILITY OF ASSOCIATIVE STEGANOGRAPHY FOR TEXTUAL CHARACTERISTICS OF OBJECTS PROTECTION
Associative steganography is quite acceptable for the protection of text characteristics of various objects: rocket mines; oil wells; mineral deposits; shore shelf contents; medical records of patients; personal data, for example, information on the availability of particular property, etc.
The infological database schema for such associative protection application is shown in Figure 5.
Here:
—Type— relation containing information about all thematic layers represented by a pair of hidden codes: Type code (for example, mine)—Layer code (specific mine). For each type, the code of the layer is chosen randomly on the full set of codes of a given width.
—[Type]_[Theme] (the name is composite, contains open codes of type and layer)—set of relations, each of which describes separate thematic layer (list of cluster names representing many characteristics of this object).
—[Type]_[Theme]_[Cluster] (the name is composite, contains open codes of type, layer and cluster names)—set of relations, each of which represents one of the characteristics of this object.—Data on the attributes marked with an asterisk are stored in masked form.
Line number code (Local_Y*) | Character code (Symbol_num*) | Position code in line (Local_X*) |
Let any textual characteristic occupy no more than one typewritten page. Then:
—The number of lines of the message—no more than 30.
—The number of characters per line—no more than 60.
With \(k=3,n=60\), the maximum response volume for any requested characteristic is \(3\times 3\times(9\times 60{-}12)\times 1.8\times 10^{3}=8.5536\times 10^{6}\) bits \({\approx}1\)MB, which is acceptable. Earlier estimates of the durability and noise immunity of associative protection remain valid for stegotexts. Sequence of characters representing the requested textual characteristic can be interpreted as a linear cartographic object, which allows the development of a full-featured DBMS of cartographic scenes with associative protection [16] and with the necessary adaptation to a new application to be used.
Rights and permissions
About this article
Cite this article
Vershinin, I.S., Gibadullin, R.F., Pystogov, S.V. et al. Associative Steganography. Durability of Associative Protection of Information. Lobachevskii J Math 41, 440–450 (2020). https://doi.org/10.1134/S1995080220030191
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1134/S1995080220030191