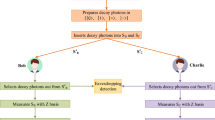
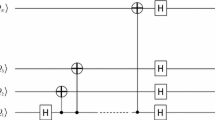
Abstract
Li et al. (Quantum Inf Process 17(10):285, 2018) proposed a limited resource semi-quantum secret sharing protocol, in which the classical participants do not equip any quantum measurement devices. However, this protocol has a security loophole. This study investigates this loophole and indicates that a malicious agent can perform the double-CNOT attack to steal partial information about the secret shadow of the other agent without being detected.
Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612 (1979)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical Bob. Phys. Rev. A 99(14), 140501 (2007)
Li, Z.L., Li, Q., Liu, C.D., Peng, Y., Chan, W.H., Li, L.H.: Limited resource semiquantum secret sharing. Quantum Inf. Process. 17(10), 285 (2018)
Iqbal, H., Krawec, W.O.: Semi-quantum cryptography. Quantum Inf. Process. 19(3), 97 (2020)
Wojcik, A.: Eavesdropping on the ‘ping–pong’ quantum communication protocol. Phys. Rev. Lett. 90(15), 157901 (2003)
Zhang, Z.J., Man, Z.X., Li, Y.: Improving Wójcik’s eavesdropping attack on the ping–pong protocol. Phys. Lett. A 333(1–2), 46 (2004)
Liu, H., Zhang, X.L., Lu, H.: Eavesdropping on the quantum dialogue protocol in lossy channel. Chin. Phys. B 20(7), 070305 (2011)
Gao, F., Wen, Q.Y., Zhu, F.C.: Comment on: ‘Quantum exam’. Phys. Lett. A 360(6), 748 (2007)
Shaari, J.S., Lucamarini, M., Wahiddin, M.R.B.: Deterministic six states protocol for quantum communication. Phys. Lett. A 358(2), 85 (2006)
Faisal, A.A.: El-Orany: Comment on ‘Deterministic six states protocol for quantum communication’. Phys. Lett. A 374(8), 1097 (2010)
Gu, J., Lin, P.H., Hwang, T.: Double C-NOT attack and counterattack on ‘Three-step semi-quantum secure direct communication protocol’. Quantum Inf. Process. 17(7), 182 (2018)
Lin, P.H., Hwang, T., Tsai, C.W.: Double CNOT attack on ‘Quantum key distribution with limited classical Bob’. Int. J. Quantum Inf. 17(02), 1975001 (2019)
Yang, C.W.: Efficient and secure semi-quantum secure direct communication protocol against double CNOT attack. Quantum Inf. Process. 19(50), 108 (2020)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72(1), 012332 (2005)
Bennett, C.H., Brassard, G., Robert, J.M.: Privacy amplification by public discussion. SIAM J. Comput. 17(2), 210 (1988)
Bennett, C.H., Brassard, G., Crepeau, C., Maurer, U.M.: Generalized privacy amplification. IEEE Trans. Inf. Theory 41(6), 1915 (1995)
Acknowledgements
We would like to thank the anonymous reviewers and the editor for their very valuable comments, which greatly enhanced the clarity of this paper. This research was partially supported by the Ministry of Science and Technology, Taiwan, R.O.C. (Grant Nos. MOST 106-2218-E-039-002-MY3, MOST 107-2218-E-143-002-MY2, MOST 107-2627-E-006-001 and MOST 107-2221-E-143-001-MY3), China Medical University, Taiwan (Grant No. CMU108-N-01), and Bureau of Energy, Ministry of Economic Affairs, Taiwan (Grant No. 109-D0101-2).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tsai, CW., Chang, YC., Lai, YH. et al. Cryptanalysis of limited resource semi-quantum secret sharing. Quantum Inf Process 19, 224 (2020). https://doi.org/10.1007/s11128-020-02690-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02690-w