Abstract
In threshold cryptography, private keys are divided into n shares, each one of which is given to a different server in order to avoid single points of failure. In the case of threshold public-key encryption, at least \(t \le n\) servers need to contribute to the decryption process. A threshold primitive is said robust if no coalition of t malicious servers can prevent remaining honest servers from successfully completing private key operations. Non-interactive schemes, considered the most practical ones, allow servers to contribute to decryption without interactions. So far, most non-interactive threshold cryptosystems were only proved secure against static corruptions. In the adaptive corruption scenario (where the adversary can corrupt servers at any time, based on its complete view), all existing robust threshold encryption schemes that also resist chosen-ciphertext attacks till recently require interaction in the decryption phase. A very specific method (in composite order groups) for getting rid of interaction was recently suggested, leaving the question of more generic frameworks and constructions with better security and, in particular, better flexibility (i.e., compatibility with distributed key generation). This paper advances the state of the art and describes a general construction of adaptively secure robust non-interactive threshold cryptosystems with chosen-ciphertext security. We define the novel notion of all-but-one perfectly sound threshold hash proof systems that can be seen as (threshold) hash proof systems with publicly verifiable and simulation-sound proofs. We show that this notion generically implies threshold cryptosystems combining the aforementioned properties. Then, we provide efficient instantiations under well-studied assumptions in bilinear groups (e.g., in such groups of prime order). These instantiations have a tighter security proof in the single-challenge setting and are indeed compatible with distributed key generation protocols.
Similar content being viewed by others
Notes
We assume that tags are non-zero. This can be enforced by having \(\mathsf {Prove}\) and \(\mathsf {Verify}\) output \(\perp \) when \(\mathsf {tag}= 0\).
References
M. Abdalla, F. Ben Hamouda, D. Pointcheval, Disjunctions for hash proof systems: new constructions and applications, in Eurocrypt ’15, LNCS, vol. 9057 (Springer, 2015), pp. 69–100
M. Abe, Robust distributed multiplication with out interaction, in Crypto’99. LNCS, vol. 1666 (1999), pp. 130–147
M. Abe, B. David, M. Kohlweiss, R. Nishimaki, M. Ohkubo, Tagged one-time signatures: tight security and optimal tag size, in K. Kurosawa, G. Hanaoka, editors, PKC 2013 (Springer, 2013)
M. Abe, Y. Cui, H. Imai, E. Kiltz, Efficient hybrid encryption from ID-based encryption. Des. Codes Cryptogr. 54(3), 205–240 (2010)
M. Abe, S. Fehr, Adaptively secure feldman VSS and applications to universally-composable threshold cryptography, in Crypto’04. LNCS, vol. 3152 (2004), pp. 317–334
M. Abe, G. Fuchsbauer, J. Groth, K. Haralambiev, M. Ohkubo, Structure-preserving signatures and commitments to group elements, in T. Rabin, editor, Crypto 2010 (Springer, 2010)
J. Almansa, I. Damgård, J.-B. Nielsen, Simplified threshold RSA with adaptive and proactive security, in Eurocrypt’06. LNCS, vol. 4004 (2006), pp. 593–611
M. Bellare, A. Boldyreva, S. Micali, Public-key encryption in a multi-user setting: security proofs and improvements, Eurocrypt ’00. LNCS, vol. 1807 (Springer, 2000), pp. 259–274
M. Bellare, P. Rogaway, Random oracles are practical: a paradigm for designing efficient protocols, in ACM CCS (1993), pp. 62–73
O. Blazy, G. Fuchsbauer, M. Izabachène, A. Jambert, H. Sibert, D. Vergnaud, Batch Groth–Sahai, in Applied Cryptography and Network Security (ACNS’10). LNCS, vol. 6123 (2010), pp. 218–235
D. Boneh, X. Boyen, Efficient selective-ID secure identity-based encryption without random oracles, in Eurocrypt’04. LNCS, vol. 3027 (2004), pp. 223–238
D. Boneh, X. Boyen, S. Halevi, Chosen ciphertext secure public key threshold encryption without random oracles, in CT-RSA’06. LNCS, vol. 3860 (2006), pp. 226–243
D. Boneh, X. Boyen, H. Shacham, Short group signatures, in Crypto’04. LNCS, vol. 3152 (2004), pp. 41–55
D. Boneh, M. Franklin, Identity-based encryption from the weil pairing. SIAM J. Comput. 32(3), 586–615 (2003). Earlier version in Crypto’01
D. Boneh, E.-J. Goh, K. Nissim, Evaluating 2-DNF formulas on ciphertexts, in Theory of cryptography conference—TCC 2005. LNCS, vol. 3378 (Springer, 2005), pp. 325–341
C. Boyd, Digital multisignatures, in H. J. Beker, F. C. Piper (editors) Cryptography and coding (Oxford University Press, 1989), pp. 241–246.
X. Boyen, Q. Mei, B. Waters, Direct chosen ciphertext security from identity-based techniques, in ACM CCS’05 (2005), pp. 320–329
J. Camenisch, N. Chandran, V. Shoup, A public key encryption scheme secure against key dependent chosen plaintext and adaptive chosen ciphertext attacks, in Eurocrypt’09. LNCS, vol. 5479 (2009), pp. 351–368
J. Camenisch, K. Haralambiev, M. Kohlweiss, J. Lapon, V. Naessens, Structure preserving CCA secure encryption and applications, in Asiacrypt 2011. LNCS, vol. 7073 (2011), pp. 89–106
R. Canetti, R. Gennaro, S. Jarecki, H. Krawczyk, T. Rabin, Adaptive security for threshold cryptosystems, in Crypto’99. LNCS, vol. 1666 (1999), pp. 98–115
R. Canetti, S. Goldwasser, An efficient threshold public key cryptosystem secure against adaptive chosen ciphertext attack, in Eurocrypt’99. LNCS, vol. 1592 (1999), pp. 90–106
R. Canetti, S. Halevi, J. Katz, Chosen-ciphertext security from identity-based encryption, in Eurocrypt’04. LNCS, vol. 3027 (2004), pp. 207–222
R. Cramer, I. Damgård, S. Dziembowski, M. Hirt, T. Rabin, Efficient multi-party computations secure against an adaptive adversary, in Eurocrypt’99. LNCS, vol. 1592 (1999), pp. 311–326
R. Cramer, I. Damgård, Y. Ishai, Share conversion, pseudorandom secret-sharing and applications to secure computation, in TCC’05. LNCS, vol. 3378 (2005), pp. 342–362
R. Cramer, V. Shoup, A practical public key cryptosystem provably secure against adaptive chosen ciphertext attack, in Crypto’98. LNCS, vol. 1462 (1998), pp. 13–25
R. Cramer, V. Shoup, Universal hash proofs and a paradigm for adaptive chosen ciphertext secure public-key encryption, in Eurocrypt’02. LNCS, vol. 2332 (2002), pp. 45–64
I. Damgård, Towards practical public key systems secure against chosen ciphertext attacks, in Crypto’91. LNCS, vol. 576 (1991), pp. 445–456
Y. Dodis, N. Fazio, Public key trace and revoke scheme secure against adaptive chosen ciphertext attack, in PKC’03. LNCS, vol. 293, 2567 (2003), pp. 100–115
Y. Desmedt, Society and group oriented cryptography: a new concept, in Crypto’87. LNCS, vol. 293 (1987), pp. 120–127
Y. Desmedt, Y. Frankel, Threshold cryptosystems, in Crypto’89. LNCS, vol. 435 (1989), pp. 307–315
Y. Dodis, J. Katz, Chosen-ciphertext security of multiple encryption, in TCC’05. LNCS, vol. 3378 (2005), pp. 188–209
P.-A. Fouque, D. Pointcheval, Threshold cryptosystems secure against chosen-ciphertext attacks, in Asiacrypt’01. LNCS, vol. 2248 (2001), pp. 351–368
Y. Frankel, P. MacKenzie, M. Yung, Adaptively-secure distributed public-key systems, in ESA’99. LNCS, vol. 1643 (1999), pp. 4–27
Y. Frankel, P. MacKenzie, M. Yung, Adaptively-secure optimal-resilience proactive RSA, in Asiacrypt’99. LNCS, vol. 1716 (1999), pp. 180–194
D. Freeman, Converting pairing-based cryptosystems from composite-order groups to prime-order groups, in Eurocrypt’10. LNCS, vol. 6110 (2010), pp. 44–61
J. Groth, R. Ostrovsky, A. Sahai, Perfect non-interactive zero knowledge for NP, in Eurocrypt’06, volume 4004 of Lecture Notes in Computer Science (Springer, 2006), pp. 339–358
J. Groth, Simulation-sound NIZK proofs for a practical language and constant size group signatures, in Asiacrypt 2006. LNCS, vol. 4284 (2006), pp. 444–459
J. Groth, Fully anonymous group signatures without random oracles, in Asiacrypt 2007. LNCS, vol. 4833 (Springer, 2007), pp. 164–180
J. Groth, A. Sahai, Efficient non-interactive proof systems for bilinear groups, in Eurocrypt’08. LNCS, vol. 4965 (2008), pp. 415–432
J. Håstad, R. Impagliazzo, L. Levin, M. Luby, A pseudorandom generator from any one-way function. SIAM J. Comput. 28(4), 1364–1396 (1999)
D. Hofheinz, T. Jager, Tightly secure signatures and public-key encryption, in Crypto ’12. LNCS, vol. 7417 (Springer, 2012), pp. 590–607
D. Hofheinz, E. Kiltz, The group of signed quadratic residues and applications, in Crypto’09. LNCS, vol. 5677 (2009), pp. 637–653
S. Jarecki, A. Lysyanskaya, Adaptively secure threshold cryptography: introducing concurrency, removing erasures, in Eurocrypt’00. LNCS, vol. 1807 (2000), pp. 221–242
C. Jutla, A. Roy, Relatively-sound NIZKs and password-based key-exchange, in PKC 2012. LNCS, vol. 7293 (2012), pp. 485–503
C. Jutla, A. Roy, Shorter quasi-adaptive NIZK proofs for linear subspaces, in Asiacrypt 2013. LNCS, vol. 8269 (2013), pp. 1–20
C. Jutla, A. Roy, Switching lemma for bilinear tests and constant-size NIZK proofs for linear subspaces, Crypto ’14. LNCS, vol. 8617 (Springer, 2014), pp. 295–312
E. Kachisa, E. Schaefer, M. Scott, Constructing Brezing-Weng pairing-friendly elliptic curves using elements in the cyclotomic field, in Pairing. LNCS, vol. 5209 (2008), pp. 126–135
J. Katz, V. Vaikuntanathan, Round-optimal password-based authenticated key exchange, in TCC’11. LNCS, vol. 6597 (2011), pp. 293–310
E. Kiltz, Chosen-ciphertext security from tag-based encryption, in TCC’06. LNCS, vol. 3876 (2006), pp. 581–600
E. Kiltz, K. Pietrzak, M. Stam, M. Yung, A new randomness extraction paradigm for hybrid encryption, in Eurocrypt’09. LNCS, vol. 5479 (2009), pp. 590–609
E. Kiltz, H. Wee, Quasi-adaptive NIZK for linear subspaces revisited, in Eurocrypt 2015. LNCS, vol. 9057 (2015), pp. 101–128
T. Kim, R. Barbulescu, Extended tower number field sieve: a new complexity for the medium prime case, in Crypto 2016. LNCS, vol. 9814 (2016), pp. 543–571
A. Lewko, B. Waters, New techniques for dual system encryption and fully secure HIBE with short ciphertexts, in TCC 2010. LNCS, vol. 5978 (2010), pp. 455–479
B. Libert, T. Peters, M. Joye, M. Yung, Non-malleability from malleability: simulation-sound quasi-adaptive NIZK proofs and CCA2-secure encryption from homomorphic signatures, in Eurocrypt 2014. LNCS, vol. 8441 (2014), pp. 514–532
B. Libert, T. Peters, C. Qian, Structure-preserving chosen-ciphertext security with shorter verifiable ciphertexts, PKC 2017. LNCS, vol. 10174 (2017), pp. 247–276
B. Libert, M. Yung, Adaptively secure non-interactive threshold cryptosystems, in ICALP 2011. LNCS, vol. 6756 (2011), pp. 588–600
P. MacKenzie, An efficient two-party public key cryptosystem secure against adaptive chosen ciphertext attack, in PKC’03. LNCS, vol. 2567 (2003), pp. 47–61
P. MacKenzie, M. Reiter, K. Yang, Alternatives to non-malleability: definitions, constructions, and applications, in TCC’04. LNCS, vol. 2951 (Springer, 2004), pp. 171–190
T. Malkin, I. Teranishi, Y. Vahlis, M. Yung, Signatures resilient to continual leakage on memory and computation, in TCC’11. LNCS, vol. 6597 (2011), pp. 89–106
M. Naor, M. Yung, Public-key cryptosystems provably secure against chosen ciphertext attacks, in STOC’90 (ACM Press, 1990)
R. Ostrovsky, M. Yung, How to withstand mobile virus attacks, in \(10^{th}\)ACM Symposium on Principles of Distributed Computing (PODC’91) (1991)
T. Rabin, A simplified approach to threshold and proactive RSA, in Crypto’98. LNCS, vol. 1462 (1998), pp. 89–104
C. Rackoff, D. Simon, Non-interactive zero-knowledge proof of knowledge and chosen ciphertext attack, in Crypto’91. LNCS, vol. 576 (1991), pp. 433–444
A. Sahai, Non-malleable non-interactive zero knowledge and adaptive chosen-ciphertext security, in FOCS’99 (1999), pp. 543–553
M. Scott, Authenticated ID-based key exchange and remote log-in with simple token and PIN number. Cryptology ePrint Archive: Report 2002/164
A. Shamir, Identity-based cryptosystems and signature schemes, in Crypto’84. LNCS, vol. 196 (1984), pp. 47–53
V. Shoup, R. Gennaro, Securing threshold cryptosystems against chosen ciphertext attack. J. Cryptol. 15(2), 75–96 (2002). Earlier version in Eurocrypt’98. LNCS, vol. 1403 (1998), pp. 1–16
Z. Wang, H. Qian, Z. Li, Adaptively secure threshold signature scheme in the standard model. Informatica 20(4), 591–612 (2009)
B. Waters, Efficient identity-based encryption without random oracles, in Eurocrypt’05. LNCS, vol. 3494 (2005)
B. Waters, Dual system encryption: realizing fully secure IBE and HIBE under simple assumptions, in Crypto’09. LNCS, vol. 5677 (2009), pp. 619–636
H. Wee, Efficient chosen-ciphertext security via extractable hash proofs, in Crypto’10. LNCS, vol. 6223 (2010), pp. 314–332
H. Wee, Threshold and revocation cryptosystems via extractable hash proofs, in Eurocrypt’11. LNCS, vol. 6632 (2011), pp. 589–609
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Kenneth G. Paterson
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This is the full version of a paper published in the proceedings of TCC 2012.
Moti Yung: Part of this work was done while this author was with Snapchat.
Appendices
One-Time Signatures
1.1 Definition
A one-time signature scheme is a triple of algorithms \(\varSigma =({\mathsf {Gen}},{\mathsf {Sig}},{\mathsf {Ver}})\) such that, on input of a security parameter \(\lambda \) and (optionally) a set of externally supplied public parameters \({\mathsf {pp}}\), \({\mathcal {G}}\) generates a one-time key pair \(({\mathsf {SSK}},{\mathsf {SVK}}) \leftarrow \varSigma .{\mathcal {G}}(\lambda ,{\mathsf {pp}})\) while, for any message M, \(\varSigma .{\mathsf {Ver}}({\mathsf {SVK}},M,\sigma )\) outputs 1 whenever \(\sigma =\varSigma .{\mathsf {Sig}}({\mathsf {SSK}},M)\) and 0 otherwise.
As in [22, 31], we need strongly unforgeable one-time signatures: no PPT adversary can be able to create a new signature for a previously signed message.
Definition 4
\(\varSigma =({\mathsf {Gen}},{\mathsf {Sig}},{\mathsf {Ver}})\) is a strongly unforgeable one-time signature if the probability
where St denotes the state information maintained by \({\mathcal {F}}\) between stages, is negligible for any PPT forger \({\mathcal {F}}\).
1.2 Groth’s One-Time Signature
For completeness, this section recalls the description of the one-time signature proposed by Groth [37], which was proved strongly unforgeable under the Discrete Logarithm assumption. The description assumes pre-existing public parameters \({\mathsf {pp}}\) consisting of a cyclic group \({\mathbb {G}}\) of prime order \(p>2^\lambda \) with a generator \(g \in {\mathbb {G}}\) and a random member \(H:\{0,1\}^* \rightarrow {\mathbb {Z}}_p\) of collision-resistant hash function family.
-
\({\mathsf {Gen}}(\lambda ,{\mathsf {pp}})\) Given \(\lambda \in {\mathbb {N}}\), a key pair is generated by taking the following steps.
-
1.
Choose
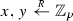 and compute \(f=g^x\), \(h=g^y\).
and compute \(f=g^x\), \(h=g^y\). -
2.
Choose
 and compute \(c= f^r h^s\).
and compute \(c= f^r h^s\).
Output \({\mathsf {SVK}}=(f,h,c) \in {\mathbb {G}}^3\) and \({\mathsf {SSK}}=(x,y,r,s) \in {\mathbb {Z}}_p^4\).
-
1.
-
\({\mathsf {Sig}}({\mathsf {SSK}},M)\) To sign \(M \in \{0,1\}^*\), choose
 and compute $$\begin{aligned} \sigma = \Bigl ( t, \frac{x \cdot (r-t) + y \cdot s - H(M) }{y} \Bigr ) \in {\mathbb {Z}}_p^2. \end{aligned}$$
and compute $$\begin{aligned} \sigma = \Bigl ( t, \frac{x \cdot (r-t) + y \cdot s - H(M) }{y} \Bigr ) \in {\mathbb {Z}}_p^2. \end{aligned}$$ -
\({\mathsf {Ver}}({\mathsf {SVK}},M,\sigma )\) Given a message M and a purported signature \(\sigma =(t,w) \in {\mathbb {Z}}_p^2\), return 1 if
$$\begin{aligned} c= g^{H(M)} \cdot f^t \cdot h^w \end{aligned}$$and 0 otherwise.
Constructing Non-interactive Proofs for Schemes in Prime Order Groups
1.1 Constructing Proof Elements in the DLIN-Based Instantiation
In the following notations, we define a coordinate-wise pairing \(E:{\mathbb {G}}\times {\mathbb {G}}^3 \rightarrow {\mathbb {G}}_T^3\) such that, for any element \(h\in {\mathbb {G}}\) and any vector \(\vec {g}=(g_1,g_2,g_3)\), we have \(E\big (h,\vec {g}\big )=\big (e(h,g_1),e(h,g_2),e(h,g_3)\big )\).
To construct the proof \(\pi _{\mathrm {LIN}}\) that \(\varPhi =(\varPhi _1,\varPhi _2,\varPhi _3)=\big (g_1^{\theta _1},g_2^{\theta _2},g^{\theta _1+\theta _2}\big )\), for some \((\theta _1,\theta _2) \in ({\mathbb {Z}}_p)^2\), the sender first computes commitments \(\vec {C}_{\theta _i}=\vec {g}_{\mathsf {tag}}^{~\theta _i} \cdot \vec {g_1}^{r_i} \cdot \vec {g_2}^{s_i}=\big (g_{\mathsf {tag},1}^{~\theta _i} \cdot g_1^{r_i},~g_{\mathsf {tag},2}^{~\theta _i} \cdot g_2^{s_i},g_{\mathsf {tag},3}^{~\theta _i} \cdot g^{r_i+s_i} \big )\), for each \(i \in \{1,2\}\), with  and where \(\vec {g}_{\mathsf {tag}}=(g_{\mathsf {tag},1},g_{\mathsf {tag},2},g_{\mathsf {tag},3}) \in {\mathbb {G}}^3\). Then, he generates the proof \(\pi _{(\theta _1,\theta _2)}\) as
and where \(\vec {g}_{\mathsf {tag}}=(g_{\mathsf {tag},1},g_{\mathsf {tag},2},g_{\mathsf {tag},3}) \in {\mathbb {G}}^3\). Then, he generates the proof \(\pi _{(\theta _1,\theta _2)}\) as
which satisfies the verification equations
When the above verifications are performed in the naive way, they require to evaluate 30 pairings altogether. However, using randomized batch verification techniques (which, as illustrated in [10], can provide substantial savings in the context of Groth–Sahai proofs), they can be more efficiently processed by computing a product of 12 pairings at the expense of a tiny probability of accepting an invalid ciphertext.
On a CRS \((\vec {g_1},\vec {g_2},\vec {g}_{\mathsf {tag}^\star })\) for the WI setting (i.e., where \(\vec {g}_{\mathsf {tag}^\star }=\vec {g_1}^{\xi _1} \cdot \vec {g_2}^{\xi _2}\) for some \(\xi _1,\xi _2 \in _R {\mathbb {Z}}_p\)), the proof \(\pi _{\mathrm {LIN}}\) can be simulated as follows. First, commitments \(\vec {C}_{\theta _1},\vec {C}_{\theta _2}\) are computed as commitments to 0 (say \(\vec {C}_{\theta _i}=\vec {g_1}^{r_i} \cdot \vec {g_2}^{s_i}\) for each \(i \in \{1,2\}\) with  ). Then, proof elements \(\pi _{(\theta _1,\theta _2)}=(\pi _1,\pi _2,\pi _3,\pi _4,\pi _5,\pi _6)\) satisfying (11) can be obtained as per
). Then, proof elements \(\pi _{(\theta _1,\theta _2)}=(\pi _1,\pi _2,\pi _3,\pi _4,\pi _5,\pi _6)\) satisfying (11) can be obtained as per
1.2 Constructing Proof Elements in the SXDH-Based instantiation
Here, our notations use a coordinate-wise pairing \(E:{\mathbb {G}}\times {\hat{{\mathbb {G}}}}^2 \rightarrow {\mathbb {G}}_T^2\) such that, for any element \(h\in {\mathbb {G}}\) and any vector \(\vec { {g}}=(\hat{g_1},\hat{g_2} ) \in {\hat{{\mathbb {G}}}}^2\), we have \(E\big (h,\vec { {g}}\big )=\big (e(h,\hat{g_1}),e(h,\hat{g_2}) \big )\).
To construct the non-interactive proof \(\pi _{\mathrm {DH}}\) that \((\varPhi _1,\varPhi _2)=(g_1^{\theta },g_2^{\theta })\), for some \(\theta \in _R {\mathbb {Z}}_p\), the sender first computes a commitment \(\vec {C}_{\theta }=\vec {u}_{\mathsf {tag}}^{~\theta } \cdot \vec {u_1}^{r } =\big ({\hat{u}}_{\mathsf {tag},1}^{~\theta } \cdot {\hat{g}}^{r},~{\hat{u}}_{\mathsf {tag},2}^{~\theta } \cdot {\hat{h}}^{r} \big )\), using a randomly drawn  and where \(\vec {u}_{\mathsf {tag}}=({\hat{u}}_{\mathsf {tag},1},{\hat{u}}_{\mathsf {tag},2}) \in {\hat{{\mathbb {G}}}}^2\). Then, he generates the proof \(\pi _{\theta }\) as
and where \(\vec {u}_{\mathsf {tag}}=({\hat{u}}_{\mathsf {tag},1},{\hat{u}}_{\mathsf {tag},2}) \in {\hat{{\mathbb {G}}}}^2\). Then, he generates the proof \(\pi _{\theta }\) as
which satisfies the verification equations
Instead of naively verifying equations (12) separately, the verifier can choose  and test whether
and test whether
which fails with overwhelming probability when one of the two equations (12) is not satisfied. With further optimizations (when coordinate-wise equalities are simultaneously batch-verified), the verifier only needs to compute a product of 6 pairings.
On a CRS \((\vec {u}_{\mathsf {tag}},\vec {u}_1)\) for the perfect WI setting (i.e., where \(\vec {u}_{\mathsf {tag}}=\vec {u}_1^{\rho _u}\) for some \(\rho _u \in _R {\mathbb {Z}}_p\)), a NIZK proof \(\pi _{\mathrm {DH}}\) can be simulated by computing \(\vec {C}_{\theta }\) as a commitment to 0 (say \(\vec {C}_{\theta }=\vec {u}_1^r\) for some  ) and the assignment
) and the assignment
is easily seen to satisfy the verification equations (12).
Rights and permissions
About this article
Cite this article
Libert, B., Yung, M. Adaptively Secure Non-interactive CCA-Secure Threshold Cryptosystems: Generic Framework and Constructions. J Cryptol 33, 1405–1441 (2020). https://doi.org/10.1007/s00145-020-09350-3
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00145-020-09350-3




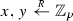 and compute
and compute  and compute
and compute  and compute
and compute