Abstract
The green communication for 5th generation Internet of Things base on the energy collecting and security issues is studied in this paper. The transceiver and power splitting factor are optimized aiming at minimizing the transmitting power at the source node subject to the security performance and energy collection. Since the optimization problem is a nonconvex function, an iteration optimization algorithm is proposed to divide the objective optimization function into two subproblems, namely, a joint transmitter and PS factor optimization subproblem and a minimum mean-square error-based receiving filter optimization subproblem. Furthermore, since the transmitter and PS combining optimization subproblem is still a nonconvex function, the semidefinite relaxation technique is used to transform it into a convex function. The feasibility of the optimization problem and the convergency of the iteration algorithm are proved in theory, and the simulation results show the availability of the proposed scheme.
Similar content being viewed by others
1 Introduction
Internet of Things (IoT) is expected to improve human life due to it can connect various objects to provide information and control the monitored objects at any time and space [1]. However, IoT devices have to face the energy limitation problem due to resource constraints. In recent years, simultaneous wireless information and power transfer (SWIPT) based on radio frequency (RF) is regarded as a promising energy collection scheme [2]. It is a prospective energy replenishment method for the sensors in IoT with insufficient battery capacity. Due to the ways of energy collection, there are two work modes, namely, time splitting mode and power splitting (PS) mode. In the PS mode, the receiver divides the received RF signals into two parts: one is for energy collection, and the other is for information processing.
The 5G IoT communication systems provide users with high data transmission, wide network coverage, multiple devices access, and low data delay, which bring more severe challenges to the secure transmission [3]. A large number of sensitive and confidential information, such as medical records, financial data, military information, and so on, is transmitted on wireless channels. Once the security of these sensitive information is destroyed, it will bring a huge threat to people’s privacy, social economy, and even national security. How to ensure the secure transmission of information is an important prerequisite for future wireless network applications.
As it was shown in information theory and cryptography, the secure transmission in wireless communications system can be guaranteed by applying the physical layer security (PLS) technologies instead of public key cryptography. In contrast to the traditional cryptographic systems, PLS technologies take advantage of the difference between the main channel capacity and the eavesdroppers channel capacity to ensure the security transmission of the data [4,5,6]. Cooperative communication and beamforming are common effective methods to improve secure performance. Cooperative diversity against channel fading can be provided by relaying. Beamforming is a signal pre-processing technique based on the antenna array. By designing the coefficients of the antenna array, an appropriate precoding matrix can be achieved to improve the receiving quality of the legal receiver [7].
Authors in [8] studied the PLS techniques in a multiuser IoT with untrusted relay. Three different scheduling schemes were proposed to reduce the complexity of scheduling algorithm. The secure relay communications in IoT with unknown number and locations eavesdroppers were investigated in [9]. Both single-antenna and multiple antennas scenarios were considered for improving the secrecy outage probability by designing the optimal power allocation and codeword rate. A secure transmission in IoT relay system with multiple eavesdroppers was considered in [10]. The authors assumed that the multiple eavesdroppers can cooperate to form joint receiving beamforming, a secure transmission scheme based on nonorthogonal multiple access is proposed. Mean-square error (MSE)-based transceiver optimization schemes have been studied a lot in different application scenarios to improve the performance of the systems [11,12,13]. The optimal design for transceiver in amplify-and-forward (AF) multiple-input multiple-output (MIMO) relay communication system was studied in [14]. The aim was to minimize the MSEs at the receivers subject to transmitting power constraints. An iterative transceiver design was proposed by exploiting the optimal structure of the transmitter, relay, and receiver matrices. Authors in [15] studied the transceiver design of a MIMO relay system based on the MSE. They studied the transceiver design in nonregenerative MIMO relay systems and developed an iterative scheme to jointly design the matrices of transceiver and relay node to minimize the maximal MSE of the signal estimation. Authors in [16] provided a minimum mean-square error (MMSE)-based transceiver design with low calculating complexity for MIMO AF relaying system. The authors in [17] investigated the minimization of the total transmitting power of the base station and the relay station problem under both signal-to-interference-plus-noise ratio and energy collecting constraints in a SWIPT multiuser multiple-input single-output relay system. They proposed an iterative algorithm based on alternating optimization and with guaranteed convergence to optimize the transceiver coefficients. In order to reduce the computational complexity, a novel design scheme based on switched relaying was also proposed.
The studies mentioned above usually consider the system model working in half-duplex. Since full-duplex transmission can receive and transmit signals at the same time, which the spectrum efficiency is twice that of half-duplex transmission. It is regarded as a key technology in 5G communication system. The transmitter design in an AF MIMO full-duplex relay network with quality of service constraints was studied in [18]. The joint optimization of the precoding matrix of the source node and the relay node was realized by two iteration algorithms to minimize the transmit power. In [19], the authors studied a SWIPT AF full-duplex relay network. Based on the MMSE criterion, the authors formulated the precoder optimization problem of the transceiver under the transmitting power and the user’s energy collection constraints. But it did not optimize the energy harvesting factor, which will affect the energy collection constraint. Moreover, none of the papers mentioned above have considered the security capacity of the system which is an important performance index, when constructing a transmitting power minimizing problem. Because reducing the transmitting power will affect the performance of the main channel, resulting in the decrease of the system security performance.
PS factor is the power splitting factor which is a key index to balance the energy collection and the information transmitting. If too much energy is collected, the data packets that the destination node received will be fewer which results in a decreased achievable capacity; the probability of eavesdropping will increase; if less energy is collected, the destination node cannot work normally and continuously. Therefore, there must be a reasonable PS factor to make the system perform well.
Thus, the transceiver and power splitting factor combining optimal scheme based on secure transmission and energy collection (EC) constraints for the MIMO SWIPT IoT with full-duplex relay is studied in this paper. The present work aims to jointly optimize the transceiver and the energy collection factor to minimize the transmitting power; meanwhile, the constraints of secure capacity (SC), MSE, and EC are satisfied. Furthermore, the formulated optimization problem is nonconvex and cannot be solved directly; thus, an iteration optimization algorithm is proposed to divide the objective optimization function into two subproblems, namely, a transmitter and PS factor subproblem and a MMSE subproblem of the receiving filter. Since the transmitter and PS factor subproblem is still a nonconvex function, the semidefinite relaxation (SDR) technique is used to transform it into a convex function.
The main innovations of this paper are summarized as follows:
- 1.
The transceiver optimal design for the SWIPT IoT is extended from the half-duplex to MIMO full-duplex model.
- 2.
In addition to MSE of received signal, the security performance and energy collecting constraints are also considered when formulating the optimization problem.
- 3.
In order to minimize the transmitting power of the source node, the transceiver and the PS factor are combining optimized subject to EC, MSE, and SC.
- 4.
An iteration algorithm is proposed to solve the problem by iteratively optimizing the transmitter and PS factor subproblem and a MMSE receiving filter subproblem. Furthermore, the feasibility of the formulated problem and the convergency of the iteration algorithm are analyzed theoretically.
- 5.
Since the subproblem of transmitter and PS factor optimization is still a nonconvex function, the SDR technique is used to transform it into a convex problem that can be effectively solved.
2 System model
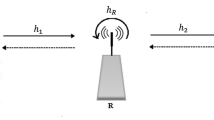
It is assumed that there is a source sensor node S, a decode-forward (DF) full-duplex relay sensor node R, a destination sensor node D, and an eavesdropping sensor node E in the IoT relay system. And all the nodes are equipped with multiple antennas. There are direct links between S and R, S and E, R and D, and R and E. The channel coefficients can be defined as hsr, hse, hrd, and hre. The residual self-interference (SI) of full-duplex which defined as hsi is considered due to the major SI is suppressed by SI cancellation technology (Fig. 1).
System model of IoT sensors relay network. The blue node represents the source sensor node S; the grey node represents DF full-duplex relay sensor node R; the green node represents the destination sensor node D; the red node represents the eavesdropping sensor node E.hsr, hse, hrd, and hre represent the links between S and R, S and E, R and D, and R and E. hsi represents residual self-interference of full-duplex
‖A‖ is expressed as the Euclidean norm of A; hH represents the conjugate transpose operation of matrix h. Tr(A) represents the trace of a matrix A; G(μ, δ2) represents a complex Gaussian distribution with mean μ and variance δ2. Assuming all the channels experience Rayleigh fading, \( {\mathbf{h}}_{sr}\in {\mathbf{R}}^{M_1\times M} \), hse ∈ RN × M, \( {\mathbf{h}}_{re}\in {\mathbf{R}}^{N\times {M}_2} \), and \( {\mathbf{h}}_{rd}\in {\mathbf{R}}^{N\times {M}_2} \). M is the antenna number of the source node; M1 is the antenna number of the full-duplex relay node that receives information; M2 is the antenna number of the full-duplex relay node that transmits data packets; N is the antenna number of the destination node and eavesdropping node. The channel noises at nodes R, E, and D are denoted as \( {n}_r(t)\sim G\left(0,{\delta}_r^2\right) \), \( {n}_e(t)\sim G\left(0,{\delta}_e^2\right) \), and \( {n}_d(t)\sim G\left(0,{\delta}_d^2\right) \), respectively. The channel state information (CSI) of all the links is assumed to be perfectly got by applying channel estimation algorithms, such as a pilot-based channel estimation algorithm. And all the channel coefficients are obeying the independent and identically Rayleigh distribution.
At the time slot t, the source node S transmits data xs(t) to the relay node R. Generally, it is assumed that \( E\left({x}_s(t){x}_s^H(t)\right)=\mathbf{I} \). I denotes an identity matrix. Let Q ∈ RM × T denotes the precoding matrix of the source node S, and T is the data streams. The transmitting power of source node S can be calculated as Ps = ‖Q‖2. Here, one time slot delay is taken into consideration for decoding and self-interference suppression in the relay node, as it is more practical. Thus, the received signal is given by as follows:
It is assumed that the precoder of the relay node is the same as that of the source node. The limited energy destination sensor node D is supplied by SWIPT, and it works in PS mode for energy collecting and information receiving. Thus, the received information data at destination node D is presented as follows:
where ρ represents the PS factor. The harvested energy at the destination node D is defined as follows:
The eavesdropping node E can receive information data in both time slot t and t − 1, the received information data at node E is presented as follows:
3 Method introductions
The aim is to achieve green communication subject to the constraints of SC, MSE, and EC by combining optimizing the transceiver and PS factor to minimize the transmitting power at the source node.
3.1 Formulation of the optimization function
According to Eqs. (1) and (2), the corresponding achievable capacity Cr and Cd at nodes R and D are as follows:
The eavesdropping ability of node E is expressed as eavesdropping capacity Ce. Since the source-eavesdropper and relay-eavesdropper channels form an inter-symbol interference (ISI) channel [20], in order to get Ce, we assume that one transmission block contains K data packets, and the eavesdropper gathers the received K-packets for processing. Thus, Eq. (4) can be rewritten in matrix form as follows:
where
The eavesdropper’s achievable capacity can be expressed as follows:
By performing the eigen-decomposition processing on HHH, Eq. (12) can be rewritten as follows:
θk is standing for the kth eigenvalue of HHH. According to the expression of eigenvalue of Toeplitz matrix in [21], θk can be represented as follows:
By substituting Eq. (14) into Eq. (13), the eavesdropping achievable rates can be obtained as follows:
Assuming that K is large in this paper, Ce is rewritten as follows:
One of the key performance measures of physical layer security is the security capacity, which is defined as the channel capacity difference between the legitimate receiver and the eavesdroppers. The link between source node S and legitimate receiver D is consisted of two parts due to the system model, namely, the link from S to R and the link from R toD. Therefore, the achievable capacity of the main channel is the lesser one. The security capacity Cs of the system can be expressed as follows:
As can be seen from the above expression of security capacity, when the ‖Q‖2 decreases, the security capacity of the system will also decreases. Thus, when minimizing the transmission power, namely, decreasing the value of ‖Q‖2, it is necessary to consider the system’s security capacity as one of the design constraints; otherwise, the system will face the risk of eavesdropping.
Furthermore, let F ∈ RN × T represents the receiving filter. Then, the detected signal of the destination node expressed as follows:
The corresponding MSE of received data is
Thus, the optimization problem proposed in this paper can be defined as follows:
By substituting formulas (3), (17), and (19) into (20), formula (21) can be obtained as follows:
η, ε, and μ are the constraints of SC, MSE, and EC separately. By solving the above formula, we can get the optimal values of Q, ρ, and F which can minimize the transmission power and while satisfying the MSE, EC, and SC constraints.
3.2 Viability analysis
Before finding out the solution of formula (21), the viability of the optimization problem is analyzed. First, only considering about the MSE constraint, the optimization function can be presented as follows:
If ignoring the variable ρ, Eq. (22) can be rewritten as follows:
It is easily to find that formula (23) is the traditional MSE-based transceiver optimization problem aimed at minimizing the transmit power; this has been widely investigated [14,15,16,17,18]. Therefore, formula (23) must be viable, and we assume that (Q, F ) is its solution.
Let Q = Q/ρ and F = ρF, and then substitute (Q/ρ, ρF, ρ) into the MSE formula as follows:
It can be seen that (Q/ρ, ρF, ρ) is also a solution that can satisfy formula (22). Moreover, substitute the solution (Q/ρ, ρF, ρ) into the formulas of energy collection and security capacity, the formulas (25) and (26) can be get.
As seen from formulas (25) and (26), there must exist a sufficiently small ρ, where 0 < ρ < 1, the constraints of \( {P}_r^{EC} \) and Cs are satisfied. Thus, (Q/ρ, ρF, ρ) can be the solution of formula (21), and then the optimization problem is proved viable.
3.3 Iteration algorithm
Since the formulated optimization problem is a nonconvex function that cannot be solved directly, in this section, an iteration algorithm is proposed to solve the function by iteratively optimizing the precoder of the transmitter together with the PS factor and the filter of the receiver.
It can be seen from problem (21) that with a fixed precoder and a power splitting factor, the transmit power remains unchanged. Furthermore, the EC and the SC are independent of the receiving filters, and only MSE is related to the filter F. Thus, the optimization problem can be divided into two subproblems: the transmitter and PS factor joint optimization subproblem and the receiver optimization subproblem.
First, we fix the receiving filter F, and the optimization problem (21) degrade into a function only about, and by solving the joint transmitting precoder and power splitting factor optimal design subproblem, the corresponding Q and ρ can be obtained.
Then, calculate the value of F, the receiving filter can be optimized by minimizing the MSE. The optimization subproblem is presented as follows:
The optimal value of F can be obtained from formula (27), which is the well-known linear MMSE receiver, as follows:
Substituting the Q and ρ obtained before, the optimal value of F can be obtained.
In summary, an iteration optimization algorithm is formed by optimizing the transmitting precoder and PS factor subproblem and the receiving filter optimization subproblem. This process can be summarized by the following steps and is shown in Fig. 2.
- 1.
Initialize F and substitute it into the optimization problem (21); then, the function turns into a nonconvex function about variables Q and ρ.
- 2.
Solve the transmitter and PS factor joint optimization subproblem, and the corresponding optimal values of Q and ρ can be obtained.
- 3.
Substitute the Q and ρ obtained in step (2) into formula (28) to optimize the receiver filter F.
- 4.
Repeat steps 2 and 3 until convergency or the maximum number of iterations is obtained.
3.4 Subproblem solution
As indicated by the above iteration algorithm, first, we should solve the transmitter and PS factor joint optimization subproblem. It can be seen that the subproblem is still a nonconvex function, and it is difficult to find a closed-form solution. To find the suboptimal solution, the SDR is employed. By using SDR, the nonconvex subproblem is relaxed to a semidefinite programming (SDP) function, which can be solved availably.
First, with fixed F, the aim is to get the optimal values of Q and ρ by solve formula (29):
Three variables, A, B, and X, are introduced to use this SDR technique. Let \( {\delta}_d^2/{\rho}^2=A \), μ/(1 − ρ) = B, and X = QQH, and further relax them as \( {\delta}_d^2/{\rho}^2\le A \), μ/(1 − ρ) ≤ B, and QQH ≤ X. Therefore, formula (29) can be rewritten as formula (30):
The problem (30) is a convex SDP function with variable Q, positive semidefinite Hermitian symmetric variable X, and nonnegative variables ρ, A, and B; this problem can be solved efficiently by adopting the solving convex toolbox Yalmip. It can be seen that the value of the optimal function (30) is a lower bound of that of the nonconvex function (29). The optimal solutions Q and ρ of the SDR problem (30) are equivalent to those of problem (29) since the same objective function is minimized over a large set.
After substituting the Q and ρ obtained by formula (30) into formula (28), the optimized F can be obtained. Then, execute the process repeatedly until convergence or the maximum number of iterations is reached.
3.5 Convergence analysis
In order to further illustrate the feasibility of the proposed iteration algorithm, the convergence of the iteration algorithm is analyzed theoretically as follows.
It is assumed that n = 0, 1, 2⋯presents the iteration number of the algorithm, where n = 0 is the initializing step. Let MSE[Q(n), ρ(n); F(n − 1)] and MSE[Q(n), ρ(n); F(n)], respectively, represent the MSE achieved after steps (2) and (3) of the algorithm, and P(n) = Tr[Q(n)Q(n)H] presents the obtained optimal value of the function at the nth iteration.
At the first step, initialize the receiver as F(0), a solution {Q(1), ρ(1)} is obtained after completing step (2) and MSE[Q(1), ρ(1); F(0)] ≤ ε. After step (3), the receiver F(1) is optimized under the obtained {Q(1), ρ(1)}. However, the MSE will not increase in this step, which gives MSE[Q(1), ρ(1); F(1)] ≤ MSE[Q(1), ρ(1); F(0)] ≤ ε. The transmitter and PS factor are invariant when renewing F, and thus the harvested energy and security capacity remain unchanged.
At the second iteration, through the fixed receiver F(1), {Q(2), ρ(2)} is optimized after step (2). {Q(1), ρ(1), F(1)} is a solution of problem (21), and steps (2) and (3) aim to minimize the transmitting power, which will make P(2) ≤ P(1).
Analogously, {Q(n), ρ(n), F(n)} is also a solution of problem (21) after the nth iteration. The transmitting power decreases with the increase in iterations, namely, P(n) ≤ P(n − 1). This proves that the convergency of the iteration algorithm.
4 Simulation results
In this section, the proposed combining optimization design scheme of the transceiver and PS factor in the MIMO full-duplex relay network powered by SWIPT is verified by simulation. The simulation parameters of the system are set as follows: M = M1 = M2 = 4, N = 4, T = 2, \( {\delta}_e^2={\delta}_d^2={\delta}_r^2=-20 dB \), and the residual self-interference ‖hsi‖2 = 0.1. All the channel coefficients generated in the simulation obey the Rayleigh distribution. The MSE, EC, and SC thresholds are set to be ε = 0.1, μ = 20 dBm, and η = 4. Two thousand times of Monte-Carlo simulation are acted to achieve the simulation results.
Figure 3 shows that as the number of the iterations increase, the optimized transmitting power decreases, and finally convergence at maximum number of iterations. It further verifies that the proposed algorithm is convergent and viable. Similarly, the PS factor decreases as the number of iterations increases as it is shown in Fig. 4. In Fig. 5, the security capacity decreases with the increase in iteration numbers. With the operation of iterative algorithm, the transmitting power decreases; the security capacity of system reduces correspondingly and then convergence at maximum number of iterations.
To better evaluate the performance of the optimal design scheme, other two similar schemes are introduced for comparison. One is the traditional MSE-based precoder optimal design (MSED) which is proposed in [18], and the other is a precoder design considering both MSE and EC constraints (MHED) which is proposed in [19]. The design scheme proposed in this paper defined as secure transmission-based joint PS factor and transceiver scheme (SPSD).
Figures 6, 7, 8, and 9 compare the transmit power, security capacity, the harvested energy, and MSE, respectively, obtained by the MSED, MHED, and SPSD optimization schemes. As shown in the Fig. 6, the transmit power achieved by MSED is lowest, followed by that of MHED; the transmit power achieved by SPSD is maximal; however, there is little difference between the values after optimization.
The transmitting power achieved by the three optimization schemes. The black histogram represents the transmitting power achieved by MSED, which is the scheme proposed in reference 18; the red histogram represents the transmitting power achieved by MHED which is the scheme proposed in reference 19; the blue histogram represents the transmitting power achieved by SPSD the optimization scheme proposed by this paper
The harvested energy achieved by two optimization schemes. The blue histograms represent the harvested energy achieved by MHED and SPSD, when energy collection constraints \( {P}_1^{EC}=20\kern0.3em \mathrm{dBm} \). The orange histogram represents the harvested energy achieved by MHED and SPSD, when energy collection constraints \( {P}_2^{EC}=30\kern0.3em \mathrm{dBm} \)
The variance of the MSE achieved by the three schemes under the constraints of ε = 0.01 and ε = 0.1. y-axis represents the MSE; x-axis represents the number of iterations. There are two subgraphs in the figure. The upper one represents the MSE achieved by the MSED, MHED, and SPSD under the MSE constraint of ε = 0.01; the bottom one represents the MSE achieved by the MSED, MHED, and SPSD under the MSE constraint of ε = 0.1. The black solid line represents MSED; the green line represents MHED; the red dotted line represents SPSD
Figure 7 shows that the both security capacities achieved by MSED and MHED are lower than that of SPSD, which means that the information data transmitted in by these schemes will be more probably eavesdropped. Figure 8 shows that both of the MSED and SPSD can satisfy the given energy constraints \( {P}_1^{EC}=20\kern0.3em \mathrm{dBm} \) and \( {P}_2^{EC}=30\kern0.3em \mathrm{dBm} \). Figure 9 illustrates that all the three optimization schemes can satisfy the MSE constraints under the conditions of ε = 0.01 and ε = 0.1.
5 Discussions
As can be seen from the experiment results, the optimization design proposed in this paper can performance green communication while satisfying the secure and energy collection requiring of the system. The secure performance achieved by the proposed paper is better comparing with other recommendations. It should be noted that the formulated optimization problem is a non-convex function which cannot get the global optimal value. So SDR is used to translate it into SDP function to get suboptimal value. In addition, the perfect channel status information is assumed. In the future, the imperfect situation will be studied.
6 Conclusions
The transceiver and PS factor design scheme based on secure transmission and energy collection constraints has been considered in the SWIPT-powered 5G IoT relay system with full-duplex relay. An optimization function has been formulated to minimize the transmitting power at the source sensor node subject to the system security capacity, MSE, and energy collection. Since the optimization problem is a nonconvex function, an iterative optimization has been proposed to divide the objective optimization function into two subproblems, namely, a transmitter and PS factor optimization subproblem and a MMSE subproblem of the receiving filter. In addition, the feasibility of the optimization function and the convergency of the iteration algorithm have been theoretically analyzed. Since the transmitter and PS factor optimization subproblem is still a nonconvex function, the SDR has been used to transform it into a convex function that can be easily solved. Finally, simulation results have demonstrated the availability of the proposed design.
Availability of data and materials
Not applicable.
Abbreviations
- 5G:
-
5th generation
- IoT:
-
Internet of Things
- PS:
-
power splitting
- RF:
-
radio frequency
- MSE:
-
mean-square error
- MMSE:
-
minimum mean-square error
- MIMO:
-
multiple-input multiple-output
- AF:
-
amplify-and-forward
- PLS:
-
physical layer security
- EC:
-
energy collection
- SC:
-
secure capacity
- SDR:
-
semidefinite relaxation
- MSED:
-
the optimization scheme which is proposed in reference 18
- MHED:
-
which is proposed in reference 19
- SPSD:
-
the optimization scheme proposed by this paper
- SDP:
-
semidefinite programming
References
F. Meneghello, M. Calore, D. Zucchetto, et al., IoT: Internet of Threats ? A Survey of Practical Security Vulnerabilities in Real IoT Devices. IEEE Internet Things J. 6(5), 8182–8201 (2019)
I. Krikidis, S. Timotheou, S.G. Nikolaou, Simultaneous wireless information and power transfer in modern communication systems. IEEE Commun. Mag. 52(11), 104–110 (2014)
Y.P. Wu, A. Khisti, C.S. Xiao, et al., A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE Journal on selected areas in communications. 36(4), 679–695 (2018)
D. Wang, B. Bai, W.B. Zhao, et al., A Survey of Optimization Approaches for Wireless Physical Layer Security. IEEE Communications Surveys & Tutorials 21(2), 1878–1911 (2019)
F. Jameel, S. Wyne, G. Kaddoum, A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Communications Surveys & Tutorials. 21(3), 2734–2771 (2019)
M. Zhang, J.H. Zheng, Y. He, Secure transmission scheme for SWIPT-powered full-duplex relay system with multi-antenna based on energy cooperation and cooperative jamming. Telecommun. Syst. (2019). https://doi.org/10.1007/s11235-019-00642-z
X.M. Chen, D.W.K. Ng, W.H. Gerstacker, et al., A Survey on Multiple-Antenna Techniques for Physical Layer Security. IEEE Communications Surveys & Tutorials 19(2), 1027–1053 (2017)
D.C. Chen, W.W. Yang, J.W. Hu, et al., Energy-Efficient Secure Transmission Design for the Internet of Things With an Untrusted Relay. IEEE Access. 6, 11862–11870 (2018)
Q. Xu, P.Y. Ren, H.B. Song, et al., Security Enhancement for IoT Communications Exposed to Eavesdroppers With Uncertain Locations. IEEE Access. 4, 2840–2853 (2016)
P.M. Huang, Y.Q. Hao, T.J. Lv, Secure Beamforming Design in Relay-Assisted Internet of Things. IEEE Internet Things J. 6(4), 6453–6464 (2019)
X. Xie, H. Yang, A.V. Vasilakos, Robust Transceiver Design Based on Interference Alignment for Multi-User Multi Cell MIMO Networks With Channel Uncertainty. IEEE Access 5, 5121–5134 (2017)
H. Yang, C. Chen, W. Zhong, et al., Joint Precoder and Equalizer Design for Multi-User Multi-Cell MIMO VLC Systems. IEEE Trans. Veh. Technol. 67(12), 11354–11364 (2018)
A. Gebhard, O. Lang, M. Lunglmayr, et al., A Robust Nonlinear RLS Type Adaptive Filter for Second-Order-Intermodulation Distortion Cancellation in FDD LTE and 5G Direct Conversion Transceivers. IEEE Transactions on Microwave Theory and Techniques 67, 5 (2019)
K.X. Nguyen, Y. Rong, S. Nordholm, MMSE-Based Transceiver Design Algorithms for Interference MIMO Relay Systems. IEEE Trans. Wirel. Commun. 14(11), 6414–6424 (2015)
L. Gopal, Y. Rong, Z.Q. Zang, Robust MMSE Transceiver Design for Nonregenerative Multicasting MIMO Relay Systems. IEEE Trans. Veh. Technol. 66(10), 8979–8989 (2017)
H.B. Kong, H.M. Shin, T. Oh, Joint MMSE Transceiver Designs for MIMO AF Relaying Systems With Direct Link. IEEE Trans. Wirel. Commun. 16(6), 3547–3560 (2017)
Y.L. Cai, M.M. Zhao, Q.J. Shi, et al., Joint Transceiver Design Algorithms for Multiuser MISO Relay Systems With Energy Harvesting. IEEE Trans. Commun. 64(10), 4147–4164 (2016)
J.L. Yang, Z. He, Q.Y. Rong, Transceiver Optimization for Two-Hop MIMO Relay Systems With Direct Link and MSE Constraints. IEEE Access 5, 24203–24213 (2017)
Z.G. Wen, X.Q. Liu, R. Wang, Joint Source and Relay Beamforming Design for Full-Duplex MIMO AF Relay SWIPT Systems. IEEE Commun. Lett. 20(2), 320–323 (2018)
N. Vucic, H. Boche, S. Shi, Robust transceiver optimization in downlink multiuser MIMO systems. IEEE Trans. Signal Process. 57(9), 3576–3587 (2009)
S. Noschese, L. Pasquini, L. Reichel, Tridiagonal Toeplitz matrices: Properties and novel applications. Numer. Linear Algebra. 20(2), 302–326 (2013)
Funding
This work is supported by the National Science and Technology Major Project of China under Grant No. 2018ZX03001026-002, the Doctoral Candidate Innovative Talent Project of CQUPT under Grant No. BYJS201807, and the Science Technology Project of Chongqing Education Commission under Grant No. KJQN201800618.
Author information
Authors and Affiliations
Contributions
MZ was in charge of the major theoretical analysis, algorithm design, experimental simulation, and paper writing. QH had contributions to paper writing. JHZ and MK had contributions to theoretical analysis and gave suggestions of the organization. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Zhang, M., Zheng, J., Huang, Q. et al. Green communication for MIMO SWIPT-powered 5G Internet of Things with full-duplex relay base on secure transmission and energy collection constraints. J Wireless Com Network 2020, 119 (2020). https://doi.org/10.1186/s13638-020-01732-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-020-01732-2