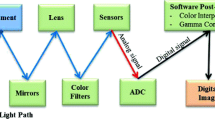
Abstract
Images are acquired and stored digitally these days. Image forensics is a science which is concerned with revealing the underlying facts about an image. The universal approaches provide a general strategy to perform image forensics irrespective of the type of manipulation. Identification of acquisition device is one of the significant universal approach. This review paper aims at analyzing the different types of device identification approaches. All research papers aiming camera and mobile detection using image analysis were acquired and then finally 60 most suitable papers were included. Out of these, 32 states of art papers were critically analyzed and compared. As every research starts with the literature review such analysis is significant. This is the first attempt for source camera and source mobile detection evaluation as per the authors knowledge. The authors have concluded that the Accuracy rate of Lens Aberration based detection techniques deteriorates when the different source camera from same brand were under consideration. The performance of color filter array Based Detection techniques dropped when the post processing operation were used on images. These techniques were vulnerable to high compression rate for JPEG images.




Similar content being viewed by others
References
Avcibas I, Bayram S, Memon N, Ramkumar M, Sankur B (2004) A classifier design for detecting image manipulations. In: 2004 International conference on image processing, vol 4, pp 2645–2648
Avcibas I, Memon N, Sankur B (2003) Steganalysis using image quality metrics. IEEE Trans Image Process 12(2):221–229
Al Banna MH, Haider MA, Al Nahian MJ, Islam MM, Taher KA and Kaiser MS (2019) Camera model identification using deep CNN and transfer learning approach. In: 2019 International conference on robotics, electrical and signal processing techniques (ICREST). IEEE, pp. 626–630
Bayar B and Stamm MC (2018) Towards open set camera model identification using a deep learning framework. In: 2018 IEEE international conference on acoustics, speech and signal processing (ICASSP), 2007–2011
Bayram S, Sencar HT, Memon N, Avcibas I (2005) Source camera identification based on CFA interpolation. In: International conference on image processing, vol 3, pp 69–78
Bayram S, Sencar HT, Memon N (2008) Classification of digital camera-models based on demosaicing artifacts. Digit Investig 5(1):49–59
Bianchi T, Piva A (2012) Image forgery localization via block-grained analysis of JPEG artifacts. Inf Forensics Secur 7(3):1003–1017
Bondi L, Baroffio L, Güera D, Bestagini P, Delp EJ, Tubaro S (2016) First steps toward camera model identification with convolutional neural networks. IEEE Signal Process Lett 24(3):259–263
Bondi L, Güera D, Baroffio L, Bestagini P, Delp EJ, Tubaro S (2017) A preliminary study on convolutional neural networks for camera model identification. Electron Imaging 7:67–76
Bouman KL, Khanna N, Delp EJ (2016) Digital image forensics through the use of noise reference patterns. In: International sustainable remediation forum conference, pp 1–7
Cao H, Kot AC (2009) Accurate detection of demosaicing regularity for digital image forensics. IEEE Trans Inf Forensics Secur 4(4):899–910
Cao H, Kot AC (2010) Mobile camera identification using demosaicing features. In: IEEE international symposium on circuits and systems (ISCAS), pp 1683–1686
Celiktutan O, Avcibas I, Sankur B, Ayerden NP, Capar C (2006) Source cell-phone identification. In: IEEE 14th signal processing and communications applications, pp 1–3. https://doi.org/10.1109/siu.2006.1659882
Choi KS (2006) Source camera identification using footprints from lens aberration. In: Proceedings on digital photography II, no. 852 in 6069: 60,690 J–60,690 J–8
Chang TY, Tai SC, Lin GS (2014) A passive multi-purpose scheme based on periodicity analysis of CFA artifacts for image forensics. J Vis Commun Image Represent 25(6):1289–1298
Chen C, Stamm MC (2015) Camera model identification framework using an ensemble of demosaicing features. In: 2015 IEEE international workshop on information forensics and security (WIFS), pp 1–6
Chen M, Fridrich J, Goljan M, Lukas J (2008) Determining image origin and integrity using sensor noise. IEEE Trans Inf Forensics Secur 3(1):74–90
Chierchia G, Poggi G, Sansone C, Verdoliva L (2014) A Bayesian-MRF approach for PRNU-based image forgery detection. IEEE Trans Inf Forensics Secur 9(4):554–567
Cooper AJ (2013) Improved photo response non-uniformity (PRNU) based source camera identification. Forensic Sci Int 226(1):132–141
Costa FDO, Eckmann M, Scheirer WJ, Rocha A (2012) Open set source camera attribution. In Proceedings of the 25th conference on graphics, patterns and images, pp 71–78
Costa FDO, Silva E, Eckmann M, Scheirer WJ, Rocha A (2014) Open set source camera attribution and device linking. Pattern Recognit Lett 39:92–101
Dirik AE, Sencar HT, Memon N (2008) Digital single lens reflex camera identification from traces of sensor dust. IEEE Trans Inf Forensics Secur 3(3):539–552
Fan N, Jin C, Huang Y (2009) A pixel-based digital photo authentication framework via demosaicking inter-pixel correlation. In: 11th ACM workshop on multimedia and security, New Jersey, USA, pp 125–130
Fan Z, De Queiroz RL (2003) Identification of bitmap compression history: JPEG detection and quantizer estimation. IEEE Trans Image Process 12(2):230–235
Farid H (2006) Digital image ballistics from JPEG quantization. Technical Report TR2006-583, Department of Computer Science, Dartmouth College
Fridrich J (2009) Digital image forensics. IEEE Signal Process Mag 26(2):1–11
Gallagher AC (2005) Detection of linear and cubic interpolation in JPEG compressed images. In: 2nd canadian conference on computer and robot vision, pp 65–72
Gallagher AC, Chen T (2008) Image authentication by detecting traces of demosaicing. In: IEEE conference on computer vision and pattern recognition workshops, pp 1–8
Goljan M, Fridrich J (2012) Sensor-fingerprint based identification of images corrected for lens distortion. Media Watermarking Secur Forensics Int Soc Opt Photon 8303:1–13
Gonzalez W, Woods RE (2004) Eddins digital image processing using MATLAB. Prentice Hall, Upper Saddle River
Gupta S, Kumar M (2019) Forensic document examination system using boosting and bagging methodologies. Soft Comput. https://doi.org/10.1007/s00500-019-04297-5
Ho JS, Au OC, Zhou J, Guo Y (2010) Inter-channel demosaicking traces for digital image forensics. In: 2010 IEEE international conference on multimedia and expo (ICME), pp 1475–1480. https://doi.org/10.1109/icme.2010.5582951
Hu Y, Li CT, Zhou C (2010) Selecting forensic features for robust source camera identification. In: International computer symposium (ICS), 2010, pp 506–511. http://doi.org/10.1109/COMPSYM.2010.5685458
Kang X, Li Y, Qu Z, Huang J (2011) Enhancing source camera identification performance with a camera reference phase sensor pattern noise. IEEE Trans Inf Forensics Secur 7(2):393–402
Kharrazi M, Sencar HT, Memon ND (2004) Blind source camera identification. In: International conference on image processing, pp 709–712
Kirchner M (2010) Efficient estimation of CFA pattern configuration in digital camera images. In: Media forensics and security, pp 754111–754123
Long Y, Huang Y (2006) Image based source camera identification using demosaicking. In: 8th IEEE workshop on multimedia signal processing, pp 419–424
Li CT, Chang C, Li Y (2010) On the reputability of device identification and image integrity verification using sensor pattern noise. In: Weerasinghe D (ed) ISDF2009, LNICST, vol 41, pp 19–25
Li CT, Li Y (2010) Digital camera identification using colour-decoupled photo response non-uniformity noise pattern. In: IEEE international symposium on circuits and systems, pp 3052–3055
Liu BB, Hu Y, Lee HK (2010) Source camera identification from significant noise residual regions. In: 17th IEEE international conference on image processing, pp 1749–1752
Liu Q, Li X, Chen L, Cho H, Cooper AP, Chen Z, Qiao M, Sung AH (2012) Identification of smart phone image source and manipulation. In: Advanced research in applied artificial intelligence, lecture notes in computer science, vol 7345. Springer, Berlin, pp 262–271. https://doi.org/10.1007/978-3-642-31087-428
Lukas J, Fridrich J, Goljan M (2006) Detecting digital image forgeries using sensor pattern noise. In: Security, steganography, and watermarking of multimedia contents, electronic imaging, vol 6072, pp 15–26
Marra F, Poggi G, Sansone C, Verdoliva L (2015) Evaluation of residual-based local features for camera model identification. In: International conference on image analysis and processing, pp 11–18
Marra F, Poggi G, Sansone C, Verdoliva L (2016) Correlation clustering for PRNU-based blind image source identification. In: IEEE international workshop on information forensics and security, pp 1–6
Marra F, Poggi G, Sansone C, Verdoliva L (2017) A study of co-occurrence based local features for camera model identification. Multimed Tools Appl 76(4):4765–4781
McKay C, Swaminathan A, Gou H, Wu M (2008) Image acquisition forensics: forensic analysis to identify imaging source. In 2008 IEEE international conference on acoustics, speech and signal processing, pp 1657–1660
Ozparlak L, Avcibas I (2011) Differentiating between images using wavelet-based transforms: a comparative study. IEEE Trans Forensics Secur 6(4):1418–1431
Piva A (2013) An overview on image forensics. ISRN Signal Process 496701:1–22
Popescu AC, Farid H (2004) Statistical tools for digital forensics. Inf Hiding 3200:395–407
Popescu AC, Farid H (2005) Exposing digital forgeries by detecting traces of resampling. IEEE Trans Signal Process 53(2):758–767
Rabbani M (2002) JPEG2000 Image compression fundamentals, standards and practice. J Electron Imaging 11(2):286–292
Sandoval Orozco AL, Arenas Gonzlez DM, Corripio JR, Villalba LJG, Castro JCH (2014) Source identification for mobile devices, based on wavelet transforms combined with sensor imperfections. Computing 96(9):829–841. https://doi.org/10.1007/s00607-013-0313-5
Sandoval Orozco AL, Corripio JR, Villalba LJG, Castro JCH (2016) Image source acquisition identification of mobile devices based on the use of features. Multimedia Tools Appl 75(12):7087–7111
Swaminathan A, Wu M, Liu KR (2008) Digital image forensics via intrinsic fingerprints. IEEE Trans Inf Forensics Secur 3(1):101–117
Takamatsu J, Matsushita Y, Ogasawara T, Ikeuchi K (2010) Estimating demosaicing algorithms using image noise variance. In: IEEE conference on computer vision and pattern recognition, pp 279–286
Tsai MJ, Lai CL, Liu J (2007) Camera/mobile phone source identification for digital forensics. In: 2007 IEEE international conference on acoustics, speech and signal processing—ICASSP’07, vol 2, pp II-221
Tuama A, Comby F, Chaumont M (2016) Camera model identification with the use of deep convolutional neural networks. In: 2016 IEEE international workshop on information forensics and security (WIFS), pp 1–6
Van LT, Emmanuel S, Kankanhalli M (2007) Identifying source cell phone using chromatic aberration. In: IEEE international conference on multimedia and expo, pp 883–886. https://doi.org/10.1109/ICME.2007.4284792
Wang B, Guo Y, Kong X, Meng F (2009) Source camera identification forensics based on wavelet features. In: International conference on intelligent information hiding and multimedia signal processing, pp 702–705
Wang W, Dong J, Tan T (2009) Effective image splicing detection based on image chroma. In: 16th IEEE international conference on image processing, Cairo, Egypt, pp 1257–1260
Xu B, Wang X, Zhou X, Xi J, Wang S (2016) Source camera identification from image texture features. Neurocomputing 207:131–140
Yang P, Ni R, Zhao Y, Zhao W (2019) Source camera identification based on content-adaptive fusion residual networks. Pattern Recognit Lett 119:195–204
Zeng H (2016) Rebuilding the credibility of sensor-based camera source identification. Multimed Tools Appl 75(21):13871–13882
Zhao X, Stamm MC (2016) Computationally efficient demosaicing filter estimation for forensic camera model identification. In: 2016 IEEE international conference on image processing (ICIP), pp 151–155
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gupta, S., Mohan, N. & Kumar, M. A Study on Source Device Attribution Using Still Images. Arch Computat Methods Eng 28, 2209–2223 (2021). https://doi.org/10.1007/s11831-020-09452-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11831-020-09452-y