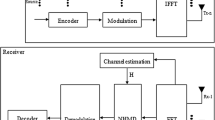
Abstract
In this work, we have proposed an intelligent and secure transceiver design and implemented over RF testbed for future wireless communication. To secure the communication, first of all, physical layer security (PLS) has been proposed for underlay multiple-input multiple-output cognitive radio network (MIMO-CRN) by using a bi-directional zero-forcing beamforming. Secondly, (PLS) has been proposed by using transmit beamforming for non-orthogonal multiple access (NOMA) over multiple cells and in the presence of primary user and secondary users. The proposed model has been extended for MIMO-NOMA over double cell and multiple scenarios. To improve further security an adaptive transceiver has been designed where parameter can be varied as per the system requirement and meantime, an intelligent received is developed in which parameter can be estimated through a blind process. The modulation format is also classified for single carrier, orthogonal frequency division multiplexing (OFDM) and MIMO through a statistical method. Finally, sequence design has been proposed to improve peak average power ratio for OFDM and multicarrier code division multiplexing (MC-CDMA). These sequences can also remove multiuse user interference for CDMA system over asynchronous system by improving the correlation properties within a code.





Similar content being viewed by others
References
Wyner AD (1975) The wiretap channel. Bell Syst Tech J 54:1355–1387
Mukherjee A, Fakoorian SAA, Huang J, Swindlehurst AL (2014) Principles of physical layer security in multiuser wireless networks: a survey. IEEE Commun Surv Tutor 16(3):1550–1573
Shiu YS, Chang SY, Wu HC, Huang SCH, Chen HH (2011) Physical layer security in wireless networks: a tutorial. IEEE Wirel Commun 18(2):66–74
Hua S, Liu H, Zhuo X, Wu M, Panwar SS (2014) Exploiting multiple antennas in cooperative cognitive radio networks. IEEE Trans Veh Technol 63(7):3318–3330
Ding Z, Adachi F, Poor HV (2016) The application of MIMO to non-orthogonal multiple access. IEEE Trans Wirel Commun 15(1):537–552
Zou Y (2017) Physical-layer security for spectrum sharing systems. IEEE Trans Wirel Commun 16(2):1319–1329
Majhi S, Kumar M, Xiang W (2017) Implementation and measurement of blind wireless receiver testbed for single carrier systems. IEEE Trans Instrum Meas 66(8):1965–1975
Cimini L (1985) Analysis and simulation of a digital mobile channel using orthogonal frequency division multiplexing. IEEE Trans Commun 33(7):665–675
Swami A, Sadler BM (2000) Hierarchical digital modulation classification using cumulants. IEEE Trans Commun 48(3):416–429
Kumar M, Majhi S (2017) Joint signal detection and synchronization for OFDM based cognitive radio networks and its implementation. Accepted at Wireless Networks. Springer, Berlin
Kumar S, Majhi S, Chau Y (2018) Multi-user CFOs estimation for SC-FDMA system over frequency selective fading channels. IEEE Access 6:43146–43156
Dobre OA, Abdi A, Bar-Ness Y, Su W (2007) Survey of automatic modulation classification techniques: classical approaches and new trends. IET Commun 1(2):137–156
Dobre OA (2015) Signal identification for emerging intelligent radios: classical problems and new challenges. IEEE Instrum Meas Mag 18(2):11–18
Majhi S, Ho TS (2015) Blind symbol-rate estimation and testbed implementation of linearly modulated signals. IEEE Trans Veh Technol 64(3):954–963
Velazquez-Gutierrez JM, Vargas-Rosales C (2017) Sequence sets in wireless communication systems: a survey. IEEE Commun Surv Tutor 19(2):1225–1248
Chen H-H (2007) The next generation CDMA technologies. Wiley, New York
Kershenbaum A et al (2016) Acoustic sequences in non-human animals: a tutorial review and prospectus. Biol Rev 91(1):13–52
Schroeder M (2009) Number theory in science and communication: with applications in cryptography, physics, digital information, computing, and self-similarity, vol 7. Springer, Heidelberg
Liu Z, Guan YL, Chen HH (2015) Fractional-delay-resilient receiver design for interference-free MC-CDMA communications based on complete complementary codes. IEEE Trans Wirel Commun 14(3):1226–1236
Tang J, Ma Z, Han C (2012) The application of complete complementary codes in MIMO radar. In: Proceedings of the international waveform diversity design conference (WDD), pp 271–276
Liu Z, Guan YL, Parampalli U (2014) New complete complementary codes for peak-to-mean power control in multi-carrier CDMA. IEEE Trans Commun 62(3):1105–1113
Liu Z, Guan YL, Parampalli U (2014) A new construction of zero correlation zone sequences from generalized Reed-Muller codes. In: Proceedings of the IEEE information theory workshop (ITW), pp 591–595
Liu J, Kang G, Lu S, Zhang P (2007) Preamble design based on complete complementary sets for random access in MIMO–OFDM systems. In: Proceedings of the IEEE wireless communications and networking conference, pp 858–862
Majhi S, Nandan N (2018) Secrecy capacity analysis of MIMO system over multiple destinations and multiple eavesdroppers. Accepted for Wireless Personal Communications, Springer
Wang F, Wang X (2010) Fast and robust modulation classification via Kolmogorov–Smirnov test. IEEE Trans Commun 58(8):2324–2332
Nandan N, Majhi S, Wu HC (2018) Secure beamforming for MIMO-NOMA based cognitive radio network. IEEE Commun Lett 22(8):1708–1711
Song X, Babu N, Rave W, Majhi S, Fettweis G (2018) Two-level spatial multiplexing using hybrid beamforming antenna arrays for mm wave communications. IEEE Trans Wirel Commun 17(7):4830–4844
Kumar M, Majhi S (2017) Joint signal detection and synchronization for OFDM based cognitive radio networks and its implementation. Accepted at Wireless Networks, Springer
Majhi S, Gupta R, Xiang W, Glisic S (2017) Hierarchical hypothesis and feature based blind modulation classification for linearly modulated signals. IEEE Trans Veh Technol 66(12):11057–11069
Gupta R, Majhi S, Dobre OA (2018) Design and implementation of a tree-based blind modulation classification for multiple-antenna systems, Accepted at IEEE Transactions on Instrumentation & Measurement
Adhikary AR, Majhi S, Liu Z, Guan YL (2017) New sets of optimal odd-length binary Z-complementary pairs. Accepted at IEEE Transaction on Information Theory
Adhikary AR, Majhi S, Liu Z, Guan YL (2018) New sets of even-length binary Z-complementary pairs with asymptotic ZCZ ratio of 3/4. IEEE Signal Process Lett 25(7):970–973
Das S, Budishin S, Majhi S, Liu Z, Guan YL (2018) A novel multiplier-free generator for complete complementary codes. IEEE Trans Signal Process 66(5):1184–1196
Das S, Majhi S, Liu Z (2018) A novel class of complete complementary codes and their applications for APU matrices. Accepted at IEEE Signal Processing Letters
Sarkar P, Majhi S, Liu Z (2018) Optimal Z-complementary code set from generalized Reed–Muller codes. Accepted at IEEE Transactions on Communication
Adhikary AR, Majhi S (2019) New Constructions of complementary sets of sequences of lengths non-power-of-two. Accepted at IEEE Communications Letters
Das S, Majhi S, Budishin S, Liu Z (2019) A new construction framework for polyphase complete complementary codes with various lengths. Accepted at IEEE Transactions on Signal Processing
Gupta R, Kumar S, Majhi S (2020) Blind modulation classification for asynchronous OFDM systems over unknown signal parameters and channel statistics. Accepted at IEEE Transactions on Vehicular Technology
Kumar S, Chaudhari M, Gupta R, Majhi S (2020) Multiple CFOs estimation and implementation of SC-FDMA uplink system using oversampling and iterative method. Accepted at IEEE Transactions on Vehicular Technology
Sarkar P, Roy A, Majhi S (2020) Construction of Z-complementary code sets with non-power-of-two lengths based on generalized boolean functions. Accepted at IEEE Communication Letters
Acknowledgements
The work of S. Majhi was supported by the Visvesvaraya Young Faculty Research Fellowship, Ministry of Electronics and Information Technology, Government of India, being implemented by the Digital India Corporation.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Majhi, S. Intelligent and secure transceiver design and implementation for future wireless communication. CSIT 8, 157–164 (2020). https://doi.org/10.1007/s40012-020-00288-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40012-020-00288-2