Abstract
We introduce a novel lower bound technique for distributed graph algorithms under bandwidth limitations. We define the notion of fooling views and exemplify its strength by proving two new lower bounds for triangle membership in the Congest \((B)\) model:
-
1.
Any 1-round algorithm requires \(B\ge c\varDelta \log n\) for a constant \(c>0\).
-
2.
If \(B=1\), even in constant-degree graphs any algorithm must take \(\varOmega (\log ^* n)\) rounds.
The implication of the former is the first proven separation between the Local and the Congest models for deterministic triangle membership. The latter result is the first non-trivial lower bound on the number of rounds required, even for triangle detection, under limited bandwidth. All previous known techniques are provably incapable of giving these bounds. We hope that our approach may pave the way for proving lower bounds for additional problems in various settings of distributed computing for which previous techniques do not suffice.


Similar content being viewed by others
Notes
Congest \((B)\) stands for the synchronous model with a bandwidth of B bits. In particular, the standard Local and Congest models correspond to Congest \((\infty )\) and Congest \((\log {n})\), respectively.
Throughout this paper \(\varDelta \) denotes the maximum degree of the graph.
In the triangle membership problem, every node must indicate whether it participates in a triangle.
While this reduction increases the ID space by r, it remains polynomial in n, because we know that \(r<n\).
Locally Checkable Labeling (LCL) problems are problems in which the legality of the output can be verified by looking at the output of the immediate neighborhood (e.g., coloring).
For simplifying the exposition, we will assume that nodes send B bits in each round and cannot send less bits or remain silent. It is easy to verify that this only affects the constants in our asymptotic notation.
In fact, one can show that there are many such nodes as \(w^*\), but we do not use this in this section.
Throughout the paper, we denote by \({{\dot{\cup }}}\) a disjoint union.
Observe that the order of the triple doesn’t matter. We still choose the notation (u, w, x) instead of \(\{u,w,x\}\) as it helps us to refer to nodes from specific sets in the proofs. That is, in the proofs later when we denote (u, w, x) we mean \(u\in A_1\), \(w\in A_2\), \(x\in A_3\).
We say that an event occurs with high probability if it occurs with probability \(1-\frac{1}{n^c}\), for some constant \(c\ge 1\).
References
Abboud, A., Backurs, A., Williams, V.V.: If the current clique algorithms are optimal, so is Valiant’s parser. In: FOCS, pp. 98–117 (2015)
Abboud, A., Censor-Hillel, K., Khoury, S., Lenzen, C.: Fooling views: a new lower bound technique for distributed computations under congestion (2017). arxiv:1711.01623
Abboud, A., Williams, V.V.: Popular conjectures imply strong lower bounds for dynamic problems. In: FOCS, pp. 434–443 (2014)
Abboud, A., Williams, V.V., Yu, H.: Matching triangles and basing hardness on an extremely popular conjecture. In: STOC, pp. 41–50 (2015)
Afrati, F.N., Fotakis, D., Ullman, J.D.: Enumerating subgraph instances using map-reduce. In: ICDE, pp. 62–73. IEEE (2013)
Alon, N., Babai, L., Itai, A.: A fast and simple randomized parallel algorithm for the maximal independent set problem. J. Algorithms 7(4), 567–583 (1986)
Alon, N., Yuster, R., Zwick, U.: Color-coding. J. ACM 42(4), 844–856 (1995)
Awerbuch, B., Goldreich, O., Peleg, D., Vainish, R.: A trade-off between information and communication in broadcast protocols. J. ACM 37(2), 238–256 (1990)
Bansal, N., Williams, R.: Regularity lemmas and combinatorial algorithms. Theory Comput. 8(1), 69–94 (2012)
Bar-Noy, A., Naor, J., Naor, M.: One-bit algorithms. Distrib. Comput. 4, 3–8 (1990)
Baruch, M., Fraigniaud, P., Patt-Shamir, B.: Randomized proof-labeling schemes. In: Proceedings of the 2015 ACM Symposium on Principles of Distributed Computing (PODC), pp. 315–324 (2015)
Belovs, A.: Span programs for functions with constant-sized 1-certificates. In: STOC, pp. 77–84. ACM (2012)
Björklund, A., Pagh, R., Williams, V.V., Zwick, U.: Listing triangles. In: International Colloquium on Automata, Languages, and Programming, pp. 223–234. Springer (2014)
Brandt, S., Fischer, O., Hirvonen, J., Keller, B., Lempiäinen, T., Rybicki, J., Suomela, J., Uitto, J.: A lower bound for the distributed lovász local lemma. In: STOC, pp. 479–488 (2016)
Buhrman, H., Durr, C., Heiligman, M., Hoyer, P., Magniez, F., Santha, M., De Wolf, R.: Quantum algorithms for element distinctness. In: CCC, pp. 131–137. IEEE (2001)
Censor-Hillel, K., Fischer, E., Schwartzman, G., Vasudev, Y.: Fast distributed algorithms for testing graph properties. In: DISC, pp. 43–56. Springer (2016)
Censor-Hillel, K., Kaski, P., Korhonen, J.H., Lenzen, C., Paz, A., Suomela, J.: Algebraic methods in the congested clique. In: PODC, pp. 143–152. ACM (2015)
Censor-Hillel, K., Kavitha, T., Paz, A., Yehudayoff, A.: Distributed construction of purely additive spanners. In: DISC, pp. 129–142 (2016)
Censor-Hillel, K., Khoury, S., Paz, A.: Quadratic and near-quadratic lower bounds for the CONGEST model. In: DISC, pp. 10:1–10:16 (2017)
Chan, T.M.: Speeding up the four Russians algorithm by about one more logarithmic factor. In: SODA, pp. 212–217 (2015)
Chang, Y.-J., Pettie, S., Zhang, H.: Distributed triangle detection via expander decomposition. In: SODA, pp. 821–840 (2019)
Chang, Y.-J., Saranurak, T.: Improved distributed expander decomposition and nearly optimal triangle enumeration. In: PODC, pp. 66–73 (2019)
Czumaj, A., Lingas, A.: Finding a heaviest vertex-weighted triangle is not harder than matrix multiplication. SIAM J. Comput. 39(2), 431–444 (2009)
Dolev, D., Lenzen, C., Peled, S.: “tri, tri again”: finding triangles and small subgraphs in a distributed setting. In: DISC, pp. 195–209. Springer (2012)
Drucker, A., Kuhn, F., Oshman, R.: On the power of the congested clique model. In: Proceedings of the ACM Symposium on Principles of Distributed Computing (PODC), pp. 367–376 (2014)
Elkin, M.: A simple deterministic distributed MST algorithm, with near-optimal time and message complexities. In: PODC, pp. 157–163. ACM (2017)
Erdös, P.: On extremal problems of graphs and generalized graphs. Isr. J. Math. 2(3), 183–190 (1964)
Fischer, O., Gonen, T., Kuhn, F., Oshman, R.: Possibilities and impossibilities for distributed subgraph detection. In: SPAA, pp. 153–162 (2018)
Fraigniaud, P., Rapaport, I., Salo, V., Todinca, I.: Distributed testing of excluded subgraphs. In: DISC, pp. 342–356. Springer (2016)
Frischknecht, S., Holzer, S., Wattenhofer, R.: Networks cannot compute their diameter in sublinear time. In: SODA, pp. 1150–1162 (2012)
Håstad, J., Wigderson, A.: The randomized communication complexity of set disjointness. Theory Comput. 3(1), 211–219 (2007)
Henzinger, M., Krinninger, S., Nanongkai, D., Saranurak, T.: Unifying and strengthening hardness for dynamic problems via the online matrix-vector multiplication conjecture. In: STOC, pp. 21–30. ACM (2015)
Itai, A., Rodeh, M.: Finding a minimum circuit in a graph. SIAM J. Comput. 7(4), 413–423 (1978)
Izumi, T., Le Gall, F.: Triangle finding and listing in CONGEST networks. In: Proceedings of the ACM Symposium on Principles of Distributed Computing, (PODC), pp. 381–389 (2017)
Jukna, S.: Extremal Combinatorics–with Applications in Computer Science. Texts in Theoretical Computer Science. An EATCS Series. Springer, Berlin (2001)
Kari, J., Matamala, M., Rapaport, I., Salo, V.: Solving the induced subgraph problem in the randomized multiparty simultaneous messages model. In: SIROCCO, pp. 370–384. Springer (2015)
King, V., Kutten, S., Thorup, M.: Construction and impromptu repair of an MST in a distributed network with o(m) communication. In: PODC, pp. 71–80. ACM (2015)
Kolountzakis, M.N., Miller, G.L., Peng, R., Tsourakakis, C.E.: Efficient triangle counting in large graphs via degree-based vertex partitioning. Internet Math. 8(1–2), 161–185 (2012)
Kothapalli, K., Scheideler, C., Onus, M., Schindelhauer, C.: Distributed coloring in \(\tilde{O}(\sqrt{\log {n}})\) bit rounds. In: IPDPS (2006)
Kuhn, F., Moscibroda, T., Wattenhofer, R.: Local computation: lower and upper bounds. J. ACM 63(2), 17 (2016)
Kushilevitz, E., Nisan, N.: Communication Complexity. Cambridge University Press, Cambridge (1997)
Le Gall, F.: Improved quantum algorithm for triangle finding via combinatorial arguments. In: FOCS, pp. 216–225. IEEE (2014)
Le Gall, F.: Powers of tensors and fast matrix multiplication. In: Proceedings of the 39th International Symposium on Symbolic and Algebraic Computation, pp. 296–303. ACM (2014)
Le Gall, F., Nakajima, S.: Multiparty quantum communication complexity of triangle finding. In: TQC (to appear) (2017)
Le Gall, F., Nakajima, S.: Quantum algorithm for triangle finding in sparse graphs. Algorithmica 79(3), 941–959 (2017)
Lee, T., Magniez, F., Santha, M.: Improved quantum query algorithms for triangle finding and associativity testing. In: SODA, pp. 1486–1502. SIAM (2013)
Lenzen, C., Patt-Shamir, B.: Improved distributed steiner forest construction. In: PODC, pp. 262–271 (2014)
Linial, N.: Distributive graph algorithms global solutions from local data. In: Proceedings of the 28th Annual Symposium on Foundations of Computer Science, FOCS, pp. 331–335 (1987)
Linial, N.: Locality in distributed graph algorithms. SIAM J. Comput. 21(1), 193–201 (1992)
Luby, M.: A simple parallel algorithm for the maximal independent set problem. SIAM J. Comput. 15(4), 1036–1053 (1986)
Magniez, F., Santha, M., Szegedy, M.: Quantum algorithms for the triangle problem. SIAM J. Comput. 37(2), 413–424 (2007)
Métivier, Y., Robson, J.M., Saheb-Djahromi, N., Zemmari, A.: An optimal bit complexity randomized distributed MIS algorithm. Distrib. Comput. 23(5–6), 331–340 (2011)
Nanongkai, D., Sarma, A.D., Pandurangan, G.: A tight unconditional lower bound on distributed randomwalk computation. In: PODC, pp. 257–266. ACM (2011)
Naor, M.: A lower bound on probabilistic algorithms for distributive ring coloring. SIAM J. Discrete Math. 4(3), 409–412 (1991)
Naor, M., Stockmeyer, L.J.: What can be computed locally? SIAM J. Comput. 24(6), 1259–1277 (1995)
Pai, S., Pandurangan, G., Pemmaraju, S.V., Riaz, T., Robinson, P.: Symmetry breaking in the congest model: time- and message-efficient algorithms for ruling sets. In: DISC 2017 (2017). arXiv:1705.07861
Pai, S., Pandurangan, G., Pemmaraju, S.V., Riaz, T., Robinson, P.: Symmetry breaking in the congest model: time-and message-efficient algorithms for ruling sets. In: PODC (to appear) (2017)
Pandurangan, G., Robinson, P., Scquizzato, M.: Tight bounds for distributed graph computations (2016). arxiv:1602.08481
Pandurangan, G., Robinson, P., Scquizzato, M.: A time- and message-optimal distributed algorithm for minimum spanning trees. In: STOC, pp. 743–756. ACM (2017)
Peleg, D.: Distributed Computing: A Locality-Sensitive Approach. Society for Industrial and Applied Mathematics, Philadelphia (2000)
Peleg, D., Rubinovich, V.: A near-tight lower bound on the time complexity of distributed minimum-weight spanning tree construction. SIAM J. Comput. 30(5), 1427–1442 (2000)
Razborov, A.A.: On the distributional complexity of disjointness. Theor. Comput. Sci. 106(2), 385–390 (1992)
Sarma, A.D., Afrati, F.N., Salihoglu, S., Ullman, J.D.: Upper and lower bounds on the cost of a map-reduce computation. In: VLDB, vol. 6:4, pp. 277–288. VLDB Endowment (2013)
Sarma, A.D., Holzer, S., Kor, L., Korman, A., Nanongkai, D., Pandurangan, G., Peleg, D., Wattenhofer, R.: Distributed verification and hardness of distributed approximation. SIAM J. Comput. 41(5), 1235–1265 (2012)
Schank, T., Wagner, D.: Finding, counting and listing all triangles in large graphs, an experimental study. In: WEA, pp. 606–609. Springer (2005)
Szegedy, M.: On the quantum query complexity of detecting triangles in graphs (2003). arxiv:quant-ph/0310107
Williams, V.V.: Multiplying matrices faster than Coppersmith-Winograd. In: STOC, pp. 887–898. ACM (2012)
Williams, V.V.: Hardness of easy problems: basing hardness on popular conjectures such as the strong exponential time hypothesis (invited talk). In: LIPIcs-Leibniz International Proceedings in Informatics, vol. 43 (2015)
Williams, V.V., Williams, R.: Subcubic equivalences between path, matrix and triangle problems. In: FOCS, pp. 645–654 (2010)
Yu, H.: An improved combinatorial algorithm for Boolean matrix multiplication. In: ICALP, pp. 1094–1105. Springer (2015)
Acknowledgements
We are grateful to Michal Dory, Eyal Kushilevitz, and Merav Parter for stimulating discussions. We are also grateful to Ivan Rapaport, Eric Remila, and Nicolas Schabanel, a point that was made by them helped in significantly simplifying Sect. 3.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This research has received funding from the European Union’s Horizon 2020 research and innovation programme under Grant Agreement No. 755839. This research is also supported in part by the Israel Science Foundation (Grant 1696/14)
Appendix A: k-cycle membership for \(k \ge 4\)
Appendix A: k-cycle membership for \(k \ge 4\)
An immediate question is whether we can get lower bounds on the bandwidth for additional round-optimal algorithms. We show here how to generalize our lower bound technique to apply for detecting membership in larger cycles. However, curiously, as we show in Sect. A.1 for the sake of comparison, for cycles that are larger than 3, the standard approach of reductions from 2-party communication complexity problems allows for stronger lower bounds.
An optimal-round algorithm for solving k-cycle membership completes within exactly \(\lfloor (k-1)/2\rfloor \) rounds, by a simple (standard) indistinguishability argument (this is even with unlimited bandwidth). This is because after t rounds of communication a node may have information only about nodes at distance at most \(t+1\) from it. Therefore, after \(\lfloor (k-1)/2\rfloor -1\) rounds of communication, a node cannot distinguish whether it participates in a k-cycle or not.
To see how we generalize our technique, observe first that the lower bound given in Theorem 2 holds even when a specific node u is given as input to all the nodes, and only u needs to solve the triangle membership problem. This is helpful in extending our lower bound to the case of k-cycles when \(k \ge 4\), and hence we define this problem formally.
Definition 8
(Fixed-Node Triangle Membership) In the Fixed-Node Triangle Membership problem, all nodes are given the identity of a specific node u, and node u needs to detect whether it is a part of a triangle.
The proof of Theorem 2 actually proves the following theorem.
Theorem 5
The fixed-node triangle membership problem cannot be solved by a single-round algorithm in the Congest \((B)\) model unless \(B \ge \log ((\frac{n-2}{2(\varDelta -1)})^{\varDelta -1})\).
We formally extend the membership problem to larger cycles, as follows.
Definition 9
(k-Cycle Membership) In the k-Cycle Membership problem, each node needs to detect whether it is a part of a k-cycle.
Now, Theorem 5 can be used to prove the following.
Theorem 6
Let \(k\in O(n^{1-\epsilon })\), for some constant \(0<\epsilon <1\). The k-cycle membership problem cannot be solved by an optimal \(\lfloor (k-1)/2\rfloor \)-round algorithm in the Congest \((B)\) model unless \(B \ge c\log ((\frac{n-2}{2(\varDelta -1)})^{\varDelta -1})\), for some constant \(c\ge 0\).
We prove Theorem 6 by showing a reduction from the fixed-node triangle membership problem, given in Definition 8. That is, we show that an algorithm for solving the k-cycle membership problem can be used to solve the fixed-node triangle membership problem.
Proof of Theorem 6
First, we show how to construct an appropriate instance for the k-cycle membership problem, given an instance for the fixed-node triangle membership problem. We start with describing the construction for an odd value of k, and then show how to tweak it to handle even values of k as well.
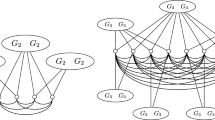
Let \((G=(V,E),u)\) be an instance of the fixed-node triangle membership problem where \(|V|={\widetilde{n}}\), and let E(u) be the set of edges incident to the node u. For an odd k, we define an instance of the k-cycle membership problem, \(G'=(V',E')\), where \(|V'|=n\), as follows. We replace each edge \(\{u,v\}\in E(u)\) with a path \(P_{uv}\) of length \((k-3)/2+1\) going through \((k-3)/2\) new nodes \(uv_1,\dots , uv_{(k-3)/2}\) and containing the edges \(\{u,uv_1\}, \{uv_1,uv_2\}, {\dots }, \{uv_{(k{-}3)/2{-}1},uv_{(k{-}3)/2}\},\{uv_{(k{-}3)/2},v\}\). For example, for \(k=7\), we replace each edge \(\{u,v\}\) by a path of three edges \(\{u,uv_1\},\{uv_1,uv_2\}, \{uv_2,v\}\), going through two new intermediate nodes \(uv_1\) and \(uv_2\) (see Fig. 3).
The following observation follows directly from the construction above.
Observation 3
For an odd k, the node u participates in a k-cycle in \(G'\) if and only if it participates in a triangle in G.
Since an algorithm may use the IDs of the nodes, we need to also assign unique IDs to nodes in \(G'\). We can do this in any consistent arbitrary manner, say, by assigning \(ID_{G'}(x)=ID_{G}(x)\) if \(x \in V\), and \(ID(uv_{i}) = ID(v)\circ bin(i)\) for nodes in \(V'\setminus V\), where bin(i) is the binary representation of i. Notice that \(\varDelta (G')=\varDelta (G)\).
Next, assume towards a contradiction, that there is an algorithm \(A'\) that solves the k-cycle membership problem in an optimal number of \((k-1)/2\) rounds in the Congest \((B)\) model with \(B < \log ((\frac{{\widetilde{n}}-2}{2e(\varDelta -1)})^{\varDelta -1})\). We show an algorithm A that solves the fixed-node triangle membership problem on \((G=(V,E),u)\) in a single round of the Congest \((B)\) model with \(B < \log ((\frac{{\widetilde{n}}-2}{2e(\varDelta -1)})^{\varDelta -1})\). As this contradicts Theorem 5, and \(n<k{\widetilde{n}}\), this completes the proof for all values of k in \(O(n^{1-\epsilon })\) for any constant \(0<\epsilon < 1\).
We construct A such that nodes in G simulate the nodes in \(G'\) running algorithm \(A'\), as follows. In A, each node in V, sends to its neighbors in G the message it sends in the first round of \(A'\) on \(G'\). If \(v \in V\) is a neighbor of u in G, then it sends to u the message it sends to \(uv_{(k-3)/2}\) in \(A'\). Then, for each of its neighbors v, the node u has all the messages that the node \(uv_{(k-3)/2}\) receives in the first round of \(A'\). Now, by backwards induction, for each i, \(1\le i \le (k-3)/2\), by local simulation at the node u, it knows the view of the node \(uv_{i}\) at the end of the first \((k-3)/2-i+1\) rounds of \(A'\). This implies that u knows the message sent to it by \(uv_{1}\) in round \((k-3)/2+1=(k-1)/2\) of \(A'\). Since in \((k-1)/2\) rounds of \(A'\) the node u knows whether it is in a k-cycle in \(G'\), by Observation 3, it thus knows in a single round whether it is in a triangle in G.
To handle even values of k, we construct \(G'\) in a similar manner by replacing each edge \((u,v) \in E(u)\) by a path of \((k-4)/2\) nodes. In addition, each edge \((v,w) \in E\setminus E(u)\), is replaced by a path of length two, which contains the additional node vw. Similarly to Observation 3, the node u participates in a k-cycle in \(G'\) if and only if it participates in a triangle in G. As in the case for odd k, given an algorithm \(A'\) for k-cycle membership in \(G'\), the simulation of \((k-4)/2+1=(k-2)/2=\lfloor (k-1)/2\rfloor \) rounds of it in G requires only a single round of communication. Therefore, the reduction carries over for even values of k as well. Observe that here \(n<k{\widetilde{n}}+{\widetilde{n}}^2\), therefore, as in the case of odd k, we achieve the same asymptotic lower bound as in the triangle membership problem, for any value of k in \(O(n^{1-\epsilon })\). \(\square \)
1.1 Appendix A.1: k-cycle membership for \(k \ge 4\) using communication complexity
Here we show a lower bound on the bandwidth needed for any optimal-round algorithm for solving k-cycle membership for \(k \ge 4\) by using the standard framework of reduction from a 2-party communication complexity problem. For simplicity, we will show this for even values of k, but a similar construction works for odd values as well. For \(k>4\), the bound is larger compared with our proof in the previous section.
Theorem 7
The k-cycle membership problem cannot be solved by a deterministic optimal-round algorithm in the Congest \((B)\) model unless \(B \ge \varOmega (\varDelta ^{\frac{k-4}{2}+1}\log (n))\), and it cannot be solved by a randomized optimal-round algorithm, which succeeds with high probability,Footnote 11 in the Congest \((B)\) model unless \(B \ge \varOmega (\varDelta ^{\frac{k-4}{2}+1})\), for any integers \(n,\varDelta ,k\) such that
for some constant \(0<\epsilon <1.\)
In order to prove Theorem 7, we show a reduction from the 2-party communication complexity problem \(DISJ_{K,S}\).
A 2-party communication complexity problem [41] consists of a function \(f:\left\{ 0,1 \right\} ^K\times \left\{ 0,1 \right\} ^K\rightarrow \left\{ {{\,\mathrm{{\scriptstyle {TRUE}}}\,}},{{\,\mathrm{{\scriptstyle {FALSE}}}\,}} \right\} \), and two strings, \(x,y\in \left\{ 0,1 \right\} ^K\), that are given as inputs for two players, Alice and Bob, respectively. The players exchange bits of communication in order to compute f(x, y), according to a protocol \(\pi \). The communication complexity \(CC(\pi )\) of a protocol \(\pi \) for computing f is the maximal number of bits, taken over all input pairs (x, y), exchanged between Alice and Bob. The communication complexity CC(f) of f is the minimum, taken over all protocols \(\pi \) that compute f, of \(CC(\pi )\).
In the S-Disjointness problem (\(DISJ_{K,S}\)), each of the players Alice and Bob receives a K-bit input string containing exactly S ones, and the function f is \(DISJ_{K,S}(x,y)\), whose output is \({{\,\mathrm{{\scriptstyle {FALSE}}}\,}}\) if there is an index \(i\in \{0,\ldots ,K-1\}\) such that \(x_i=y_i=1\), and \({{\,\mathrm{{\scriptstyle {TRUE}}}\,}}\) otherwise. Observe that for \(S>\frac{K}{2}\), the function is constant. For \(S\le \frac{K}{2}\) the deterministic communication complexity of \(DISJ_{K,S}\) is known to be \(\varOmega (\log \left( {\begin{array}{c}K\\ S\end{array}}\right) )\) [35, 41]Footnote 12, while its randomized communication complexity is known to be \(\varOmega (S)\) [31, 62]. For the reduction, we adapt the formalization of Family of Lower Bound Graphs given in [19] to our setting.
Definition 10
(Definition 1 (simplified) of [19]: Family of Lower Bound Graphs) Fix an integer K, a function \(f:\left\{ 0,1 \right\} ^K\times \left\{ 0,1 \right\} ^K\rightarrow \left\{ {{\,\mathrm{{\scriptstyle {TRUE}}}\,}},{{\,\mathrm{{\scriptstyle {FALSE}}}\,}} \right\} \). The family of graphs \(\{G_{x,y}=(V,E_{x,y})\mid x,y\in \left\{ 0,1 \right\} ^K\}\), is said to be a family of lower bound graphs w.r.t. f and k-cycle membership if the following properties hold:
-
(1)
The set of nodes V is the same for all graphs, and we denote by \(V=\{u\}{{\dot{\cup }}} V_A{{\dot{\cup }}} V_B{{\dot{\cup }}} {\widetilde{V}}\) a fixed partition of it;
-
(2)
Only the existence of edges in \(V_A\times {\widetilde{V}}\) may depend on x;
-
(3)
Only the existence of edges in \(V_B\times {\widetilde{V}}\) may depend on y;
-
(4)
The node u participates in a k-cycle in \(G_{x,y}\) iff \(f(x,y)={{\,\mathrm{{\scriptstyle {FALSE}}}\,}}\).
Observe that given a family of lower bound graphs \(\{G_{x,y}=(V,E_{x,y})\mid x,y\in \left\{ 0,1 \right\} ^K\}\) w.r.t. to \(DISJ_{K,S}\) and k-cycle membership, if Alice and Bob can simulate an algorithm for k-cycle membership on u, then by checking the output of u at the end of the algorithm they can solve \(DISJ_{K,S}(x,y)\).
The proof of Theorem 7 is organized as follows. First, we construct a family of lower bound graphs, and next, we show that given an algorithm ALG for k-cycle membership with messages of size B, Alice and Bob can simulate ALG on \(G_{x,y}\) by exchanging only O(B) bits.
We now construct the following family of lower bound graphs, by describing a fixed graph construction \(G=(V,E)\), which we then generalize to a family of graphs \(\{G_{x,y}\}\), which we show to be a family lower bound graphs w.r.t. to \(DISJ_{K,S}\) and k-cycle membership.
The fixed graph construction The fixed graph construction consists of a tree T and a path P of size \(n-|T|\). The tree T is a tree in which the root node of T, denoted by u, is connected to two nodes w and v, such that each of w and v is a root of a \((\varDelta -1)\)-regular tree of depth \(\frac{k-4}{2}\). Denote by leaves(w) and leaves(v) the set of leaves of the tree rooted at w and the set of leaves of the tree rooted at v, respectively. We define \(V_A\) and \(V_B\) to be leaves(w) and leaves(v) respectively.
Adding edges corresponding to the inputs Each of the players Alice and Bob receives as the input a set of nodes in P of size \((\varDelta -1)^{\frac{k-4}{2}+1}\). Alice connects the nodes in her input to the \((\varDelta -1)^{\frac{k-4}{2}}\) leaves of the tree rooted at v, such that each leaf is connected to \(\varDelta -1\) nodes in P. Similarly, Bob connects the nodes in his input to the \((\varDelta -1)^{\frac{k-4}{2}}\) leaves of the tree rooted at w, such that each leaf in connected to \(\varDelta -1\) nodes in P. The following observation follows directly from the construction.
Observation 4
The node u participates in a cycle of length k in \(G_{x,y}\) if and only if the two sets of Alice and Bob are not disjoint.
Therefore, given an algorithm ALG for k-cycle membership, if Alice and Bob can simulate ALG on u then they can solve S-Disjointness, where \(S=(\varDelta -1)^{\frac{k-4}{2}+1}\) and the size of the input stings is
Observe that for
for some constant \(0<\epsilon < 1\), it holds that \(K=\varTheta (n)\), and \(\log \left( {\begin{array}{c}K\\ S\end{array}}\right) =\varOmega (\varDelta ^{\frac{k-4}{2}+1}\log (n))\). It remains to show that given an algorithm for k-cycle membership with messages of size B, Alice and Bob can simulate ALG on u by exchanging only O(B) bits.
Theorem 7
Let ALG be a (\(k/2-1\))-round algorithm for solving the k-cycle membership problem. Let
be the two sets of messages sent from v and w to u during the \(k/2-1\) rounds, where, e.g., \(m^i_{v\rightarrow u}\) is the message sent from v to u in round i.
The crucial observation is that Alice and Bob can simulate the nodes v, w, and u during the first \(k/2-2\) rounds without any communication, because the \(k/2-2\) neighborhoods of these nodes are fixed. Therefore, in order for the players to compute the output of u after \(k/2-1\) rounds, it suffices for Alice to send to Bob the message \(m^{k/2-1}_{v\rightarrow u}\), and for Bob to send to Alice the message \(m^{k/2-1}_{w\rightarrow u}\).
By Observation 4, this implies that 2B bits suffice for the players to correctly compute \(DISJ_{K,S}\). Therefore, by the lower bounds on \(DISJ_{K,S}\), any deterministic optimal-round algorithm for k-cycle membership requires messages of size \(\varOmega (\log \left( {\begin{array}{c}K\\ S\end{array}}\right) )=\varOmega (\varDelta ^{\frac{k-4}{2}+1}\log (n))\), and any randomized optimal-round algorithm which succeeds with high probability requires \(\varOmega (S)=\varOmega (\varDelta ^{\frac{k-4}{2}+1})\), for any integers \(n,\varDelta ,k\) such that
for some constant \(0<\epsilon < 1\). \(\square \)
We mention that one can use the set-disjointness function instead of \(DISJ_{K,S}\) to obtain a lower bound of \((\varDelta -1)^{\frac{k-4}{2}}\), by simply connecting each leaf to a single node on the path, based on the inputs. However, this gives a rather strong bound on \(\varDelta \) with respect to n because then the number of leaves must be also linear in n. Such a bound for \(\varDelta \) does not occur in our given construction.
Rights and permissions
About this article
Cite this article
Abboud, A., Censor-Hillel, K., Khoury, S. et al. Fooling views: a new lower bound technique for distributed computations under congestion. Distrib. Comput. 33, 545–559 (2020). https://doi.org/10.1007/s00446-020-00373-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00446-020-00373-4