Abstract
This operations research aims to derive an easy but meaningful method for practitioners to identify key influencers and uncover suppressed narratives within a Twitter topic group. This research employs a new concept called “authentic chatter” (analogous to a grass-roots discourse) in combination with influence metrics, content analysis, and commercial-off-the-shelf social media analysis software (NexaIntelligence). The mixed-method exploits the power of social network analysis to determine a small but prominent group of influencers that provides a manageable dataset for the qualitative review of the content. This paper reviews research on social influence and identifies two local influence theories, “indegree” and “retweet”, ideal for topical discussion. Next it reviews Twitter content analysis research looking at specific details on methods. Findings from this past research guide development of a new methodology. The research concludes that use of a prominent group and filtering for authentic chatter increased the signal to noise ratio highlighting important underlying themes within the topic.



Similar content being viewed by others
Notes
The idea and formal definition of a prominent group is discussed in (Kardara et al. 2015). In brief she states: “the members of a topic community typically differ in the degree of influence they exert over their peers. Some users are rather passive, while others excel in some aspect of the community, affecting the behavior of other members and setting relevant trends. We call influencers or prominent users those members that have established a prominent position inside a community. Collectively, the influential users of a specific community comprise a sub-community that is called prominent group.”
In this case “local influence” means influence that is felt within a particular topic area, or # within Twitter. A person may be considered an expert in that particular domain but not so outside that topic area.
NexaIntelligence by Nexalogy was used in this research.
Note a person who creates a tweet can be referred to as a user, publisher, actor or author within this paper.
LIWC—Linguistic Inquiry and Word Count is a text analysis algorithm that exposes emotional, cognitive, and structural components present in text collections. See http://liwc.wpengine.com/wp-content/uploads/2015/11/LIWC2015_LanguageManual.pdf for more details.
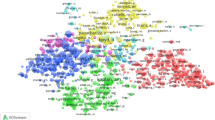
Note the colours with Fig. 1 represent outliers, are produced automatically by the software, but were not used for this research.
References
AlFalahi K, Atif Y, Abraham A (2014) Models of influence in online social networks. Int J Intell Syst 29(2):1–23
Anger I, Kittl C (2011) Measuring influence on Twitter. Paper presented at the proceedings of the 11th international conference on knowledge management and knowledge technologies, Graz, Austria
Ayers J, Leas EC, Allem J-P, Benton A, Dredze M, Althouse BM (2017) Why do people use electronic nicotine delivery systems (electronic cigarettes)? A content analysis of Twitter, 2012-2015. PLoS ONE. https://doi.org/10.1371/journal.pone.0170702
Berzins J (2014) Russia’s new generation warfare in Ukraine: implications for Latvian defense policy. National Defence Academy of Latvia
Bongwon S, Lichan H, Peter P, Ed HC (2010) Want to be Retweeted? Large Scale Analytics on Factors Impacting Retweet in Twitter Network. IEEE Computer Society
Cha M, Haddadi H, Benevenuto F, Gummadi K (2010) Measuring user influence in Twitter: the million follower fallacy. In: ICWSM’10: proceedings of international AAAI conference on weblogs and social
Chase S (2017) Latvian diplomat says NATO deployment may have to stay for 10 years to counter Russia. Ottawa
Chen W, Wang Y, Yang S (2009) Efficient influence maximization in social networks. Paper presented at the proceedings of the 15th ACM SIGKDD international conference on knowledge discovery and data mining, Paris, France
Chen W, Wang C, Wang Y (2010) Scalable influence maximization for prevalent viral marketing in large-scale social networks. Paper presented at the proceedings of the 16th ACM SIGKDD international conference on Knowledge discovery and data mining, Washington, DC, USA
Chew C, Eysenbach G (2010) Pandemics in the age of Twitter: content analysis of Tweets during the 2009 H1N1 outbreak. PLoS ONE 5:e14118
Hansen LK, Arvidsson A, Nielsen FA, Colleoni E, Etter M (2010) Good friends, bad news affect and virality in Twitter. Danish Strategic Research Council
Howard PN, Duffy A, Freelon D, Hussain M, Mari W, Mazaid M (2011) Opening closed regimes what was the role of social media during the Arab spring?. The Project on Information Technology and Political Islam, Washington
Jianshu W, Ee-Peng L, Jing J, Qi H (2010) TwitterRank: finding topic-sensitive influential Twitterers. ACM, New York
Jolicoeur P, Seaboyer A (2014) The evolution of Russian cyber influence activity: a comparison of Russian Cyber Ops in Georgia (2008) and Ukraine (2014). Royal Military College of Canada
Kardara M, Papadakis G, Papaoikonomou A, Tserpes K, Varvarigou T (2015) Large-scale evaluation framework for local influence theories in Twitter. Inf Process Manage 51:226–252. https://doi.org/10.1016/j.ipm.2014.06.002
Lachlan KA, Spence PR, Lin X, Najarian K, Del Greco M (2016) Social media and crisis management: CERC, search strategies, and Twitter content. Comput Hum Behav 54:647–652. https://doi.org/10.1016/j.chb.2015.05.027
LIWC (2018) Home page. https://liwc.wpengine.com/. Accessed 12 Jan 2018
Neuendorf KA (2017) The content analysis guidebook. SAGE, Thousand Oaks
Pal A, Counts S (2011) Identifying topical authorities in microblogs. Paper presented at the proceedings of the fourth ACM international conference on Web search and data mining, Hong Kong, China
Paul C, Matthews M (2016) The Russian “Firehose of Falsehood” Propaganda Model. Rand Corporation, Santa Monica
Pomerantsev P, Weiss M (2014) The menace of unreality: how the Kremlin weaponizes information, culture and money
Quercia D, Ellis J, Capra L, Crowcroft J (2011) In the mood for being influential on Twitter. In: 2011 IEEE third international conference on privacy, security, risk and trust and 2011. IEEE third international conference on social computing, 9-11 Oct. 2011 2011. pp 307-314. https://doi.org/10.1109/passat/socialcom.2011.27
Räbiger S, Spiliopoulou M (2015) A framework for validating the merit of properties that predict the influence of a Twitter user. Expert Syst Appl 42:2824–2834. https://doi.org/10.1016/j.eswa.2014.11.006
Riddell J, Brown A, Kovic I, Jauregui J (2017) Who are the most influential emergency physicians on Twitter? West J Emerg Med 18:281
Riquelme F, González-Cantergiani P (2016) Measuring user influence on Twitter: a survey. Inf Process Manage 52:949–975. https://doi.org/10.1016/j.ipm.2016.04.003
Romero DM, Galuba W, Asur S, Huberman BA (2011) Influence and passivity in social media. Paper presented at the proceedings of the 20th international conference companion on world wide web, Hyderabad, India
Schenk CB, Sicker DC (2011) Finding event-specific influencers in dynamic social networks. In: 2011 IEEE third international conference on privacy, security, risk and trust and 2011. IEEE third international conference on social computing, 9-11 Oct. 2011. pp 501–504. https://doi.org/10.1109/passat/socialcom.2011.100
Scripps J, Tan P-N, Esfahanian A-H (2009) Measuring the effects of preprocessing decisions and network forces in dynamic network analysis. Paper presented at the proceedings of the 15th ACM SIGKDD international conference on Knowledge discovery and data mining, Paris, France
Shane S (2017) The fake Americans Russia created to influence the election. New York
Small TA (2011) What the hashtag? Inform Commun Soc 14:872–895. https://doi.org/10.1080/1369118X.2011.554572
Starbird K (2017) Examining the alternative media ecosystem through the production of alternative narratives of mass shooting events on Twitter. Paper presented at the ICWSM 2017
Sun J, Tang J (2011) A survey of models and algorithms for social influence analysis. Social network data analysis. Springer, New York, pp 177–214
Sun J, Tang J (2013) Models and algorithms for social influence analysis. Paper presented at the proceedings of the sixth ACM international conference on web search and data mining, Rome, Italy
Timberg C (2016) Russian propaganda effort helped spread ‘fake news’ during election, experts say
Wikipedia (2018) Social influence. https://en.wikipedia.org/wiki/Social_influence. Accessed 28 Feb 2018
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Forrester, B. Authentic chatter. Comput Math Organ Theory 26, 382–411 (2020). https://doi.org/10.1007/s10588-019-09299-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10588-019-09299-0