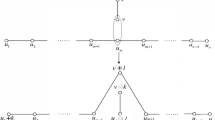
Abstract
Anonymous ranking allows each user to perfectly know the position of his/her private datum in the ascending or descending sequence of all ranking data, while anonymous selection focuses on particular items. Both of them disclose each user’s input and hide the accurate link between users and ranking data. Mature solutions of anonymous ranking and selection are usually crucial components of solving complex problems and are also extensively applied to many fields in daily life, such as auctions and commercial enterprises. In this paper, we propose two protocols of quantum anonymous ranking and selection with verifiability, in which each user can verify whether his/her ranking datum has been modified in a manner without detection and obtain the corresponding output with the property of anonymity. Furthermore, we demonstrate in detail that our protocols achieve security against outside eavesdroppers and inside malicious users under ideal or practical environment assumptions.

Similar content being viewed by others
References
Qiu, M., Luo, S.S., Liu, W., Chen, P.: A solution of secure multi-party multi-data ranking problem based on RSA encryption scheme. Chin. J. Electron. 37(5), 1119–1123 (2009)
Xiao, Q., Luo, S.S., Chen, P., Wu, B.: Research on the problem of secure multi-party ranking under semi-honest model. Chin. J. Electron. 36(4), 709–714 (2008)
Cheng, C., Luo, Y.L., Chen, C.X., Zhao, X.K.: Research on secure multi-party ranking problem and secure selection problem. In: Proceedings of WISM ’10, pp. 79–84, Washington (2010)
Huang, W., Wen, Q.Y., Liu, B., Su, Q., Qin, S.J., Gao, F.: Quantum anonymous ranking. Phys. Rev. A 89(3), 032325 (2014)
Lin, S., Guo, G.D., Huang, F., Liu, X.F.: Quantum anonymous ranking based on the Chinese remainder theorem. Phys. Rev. A 93(1), 012318 (2016)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computer Systems and Signal Processing, p. 17, Bangalore (1984)
Deng, F.G., Long, G.L.: Controlled order rearrangement encryption for quantum key distribution. Phys. Rev. A 68(4), 042315 (2003)
Chen, X.B., Wen, Q.Y., Guo, F.Z., Sun, Y., Xu, G., Zhu, F.C.: Controlled quantum secure direct communication with W state. Int. J. Quant. Inf. 6(4), 899–906 (2008)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 18241829 (1999)
Yang, Y.G., Wen, Q.Y., Zhang, X.: Multiparty simultaneous quantum identity authentication with secret sharing. Sci. China G Phys. Mech. Astron. 51(3), 321327 (2008)
Jia, H.Y., Wen, Q.Y., Gao, F., Qin, S.J., Guo, F.Z.: Dynamic quantum secret sharing. Phys. Lett. A 376(10), 1035–1041 (2012)
Christandl, M., Wehner, S.: Quantum anonymous transmissions. In: ASIACRYPT 2005, pp. 217-235, Berlin (2005)
Wang, T.Y., Wen, Q.Y., Zhu, F.C.: Economical quantum anonymous transmissions. J. Phys. B At. Mol. Opt. Phys. 43(24), 245501 (2010)
Shi, R.H., Su, Q., Guo, Y., Huang, D.: The dining cryptographer problem-based anonymous quantum communication via non-maximally entanglement state analysis. Int. J. Theor. Phys. 376(10), 1035–1041 (2012)
Shi, R.H., Mu, Y., Zhong, H., Cui, J., Zhang, S.: Secure multiparty quantum computation for summation and multiplication. Sci. Rep. 6(1), 19655 (2016)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with \(n\)-level entangled statesg. Quantum Inf. Proc. 13(11), 23752389 (2014)
Wang, Q.L., Yu, C.H., Gao, F., Qi, H.Y., Wen, Q.Y.: Self-tallying quantum anonymous voting. Phys. Rev. A 94(2), 022333 (2016)
Li, D., Yang, Y.G., Bi, J.L., Yuan, J.B., Xu, J.: Controlled alternate quantum walks based quantum hash function. Sci. Rep. 8(1), 225 (2018)
Zhou, Y.Q., Gao, F., Li, D.D., Li, X.H., Wen, Q.Y.: Semi-device-independent randomness expansion with partially free random sources using \(3\rightarrow 1\) quantum random access code. Phys. Rev. A 94(3), 032318 (2016)
Zhang, Z.C., Gao, F., Cao, Y., Qin, S.J., Wen, Q.Y.: Local indistinguishability of orthogonal product states. Phys. Rev. A 93(1), 012314 (2016)
Jiang, D.H., Xu, Y.L., Xu, G.B.: Arbitrary quantum signature based on local indistinguishability of orthogonal product states. Int. J. Theor. Phys. 58(3), 10361045 (2019)
Aaronson, S., Christiano, P.: Quantum money from hidden subspaces. In: Proceedings of STOC 12 Proceedings of the Forty-Fourth Annual ACM Symposium on Theory of Computing, p. 4160, New York (2012)
Moulick, S.R., Panigrahi, P.K.: Quantum cheques. Quantum Inf. Proc. 15, 2475 (2016). https://doi.org/10.1007/s11128-016-1273-4
Gavinsky, D.: Quantum money with classical verification. In: Proceedings of IEEE 27th Conference on Computational Complexity, p. 4252, Porto (2012)
Behera, A., Paul, G.: Quantum to classical one-way function and its applications in quantum money authentication. Quantum Inf. Proc. 17, 200 (2018). https://doi.org/10.1007/s11128-018-1965-z
Cabello, A.: \(N\)-particle \(N\)-level singlet states: some properties and applications. Phys. Rev. Lett. 89(10), 100402 (2002)
Broadbent, A., Tapp, A.: Information-theoretic security without an honest majority. In: ASIACRYPT 2005, pp. 410–426, Heidelberg (2007)
Hevia, A., Micciancio, D.: Simultaneous broadcast revisited. In: Proceedings of the Twenty-Fourth annual ACM Symposium on Principles of Distributed Computing, pp. 324–333, New York (2005)
Wang, Q.L., Yu, C.H., Li, Y.C., He, H., Zhou, Y.Q.: Quantum random draw and application in picking at random problems (in generation)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: A simple participant attack on the Br\(\acute{a}\)dler-Du\(\check{s}\)ek protocol. Quantum Inf. Comput. 7(4), 329–334 (2007)
Acknowledgements
This work was supported by NSFC (Grant No. 61801126), Open project of CAS Key Laboratory of Quantum Information, University of Science and Technology of China (Grant No. KQI201902), Research and Application of Key Technologies for Open Source Software Security Monitoring (Grant No. SGFJXT00YJJS1800074).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, Q., Li, Y., Yu, C. et al. Quantum anonymous ranking and selection with verifiability. Quantum Inf Process 19, 166 (2020). https://doi.org/10.1007/s11128-020-02664-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02664-y