Abstract
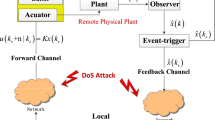
This paper addresses the problem of event-triggered attack-tolerant tracking control for a networked nonlinear system under spasmodic denial-of-service (DoS) attacks. Compared with some existing results, the exact duration of DoS attacks is not required while only assuming attainable bounds of attack frequency and duration. First, a new event-triggered attack-tolerant fuzzy tracking controller is proposed, to reduce the amount of sensor data transmissions over the sensor-to-controller (S-C) channel while counteracting unknown DoS attacks. Second, for the purpose of performance analysis and synthesis, a unified event-triggered Takagi-Sugeno (T-S) fuzzy switched model is established, which accounts for a suitable attackresilient event-triggered communication scheme and unknown DoS jamming signals. Third, using piecewise Lyapunov-Krasovskii functional (PLKF) analysis technique, a new criterion is derived to ensure exponential stability of the resulting switched tracking error system while achieving a weighted H1 performance level. Additionally, the relationship among the parameters of a DoS attack signal, the triggering parameters, the fuzzy controller gains, the sampling period, and the decay rate can be quantitatively characterized. Moreover, the triggering matrix parameter and fuzzy controller gains are obtained by finding a feasible solution to a set of linear matrix inequalities (LMIs). Finally, numerical verification is performed to demonstrate the effectiveness of the proposed control design method.
Similar content being viewed by others
References
Zhang X M, Han Q-L, Yu X H. Survey on recent advances in networked control systems. IEEE Trans Ind Inf, 2016, 12: 1740–1752
Qiu J B, Gao H J, Ding S X. Recent advances on fuzzy-model-based nonlinear networked control systems: a survey. IEEE Trans Ind Electron, 2016, 63: 1207–1217
Ding D R, Han Q-L, Wang Z D, et al. A survey on model-based distributed control and filtering for industrial cyber-physical systems. IEEE Trans Ind Inf, 2019, 15: 2483–2499
Cheng P, Shi L, Sinopoli B. Guest editorial special issue on secure control of cyber-physical systems. IEEE Trans Control Netw Syst, 2017, 4: 1–3
Ding D R, Han Q-L, Xiang Y, et al. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing, 2018, 275: 1674–1683
Wang D, Wang Z D, Shen B, et al. Recent advances on filtering and control for cyber-physical systems under security and resource constraints. J Franklin Institute, 2016, 353: 2451–2466
Xiao S, Han Q-L, Ge X H, et al. Secure distributed finite-time filtering for positive systems over sensor networks under deception attacks. IEEE Trans Cybern, 2019. doi: 10.1109/TCYB.2019.2900478
Ge X H, Han Q-L, Zhong M, et al. Distributed Krein space-based attack detection over sensor networks under deception attacks. Automatica, 2019, 109: 108557
Peng C, Sun H T, Yang M J, et al. A survey on security communication and control for smart grids under malicious cyber attacks. IEEE Trans Syst Man Cybern Syst, 2019, 49: 1554–1569
Lu A Y, Yang G H. Event-triggered secure observer-based control for cyber-physical systems under adversarial attacks. Inf Sci, 2017, 420: 96–109
An L W, Yang G H. Improved adaptive resilient control against sensor and actuator attacks. Inf Sci, 2018, 423: 145–156
He W L, Gao X Y, Zhong W M, et al. Secure impulsive synchronization control of multiagent systems under deception attacks. Inf Sci, 2018, 459: 354–368
Mo Y L, Chabukswar R, Sinopoli B. Detecting integrity attacks on SCADA systems. IEEE Trans Contr Syst Technol, 2014, 22: 1396–1407
Amin S, Cardenas A A, Sastry S. Safe and secure networked control systems under denial-of-service attacks. In: Proceedings of the International Workshop on Hybrid Systems: Computation and Control, 2009. 5469: 31–45
Xu W Y, Ma K, Trappe W, et al. Jamming sensor networks: attack and defense strategies. IEEE Netw, 2006, 20: 41–47
Zhang H, Cheng P, Shi L, et al. Optimal denial-of-service attack scheduling with energy constraint. IEEE Trans Automat Contr, 2015, 60: 3023–3028
Zhang H, Cheng P, Shi L, et al. Optimal DoS attack scheduling in wireless networked control system. IEEE Trans Contr Syst Technol, 2016, 24: 843–852
An L W, Yang G H. Decentralized adaptive fuzzy secure control for nonlinear uncertain interconnected systems against intermittent DoS attacks. IEEE Trans Cybern, 2019, 49: 827–838
Yang H J, Shi M, Xia Y Q, et al. Security research on wireless networked control systems subject to jamming attacks. IEEE Trans Cybern, 2019, 49: 2022–2031
Yan H C, Wang J N, Zhang H, et al. Event-based security control for stochastic networked systems subject to attacks. IEEE Trans Syst Man Cybern Syst, 2019. doi: 10.1109/TSMC.2018.2856819
Li Y Z, Shi L, Cheng P, et al. Jamming attacks on remote state estimation in cyber-physical systems: a game-theoretic approach. IEEE Trans Automat Contr, 2015, 60: 2831–2836
Yuan Y, Yuan H H, Guo L, et al. Resilient control of networked control system under DoS attacks: a unified game approach. IEEE Trans Ind Inf, 2016, 12: 1786–1794
Liu S C, Liu P X, Saddik A E. A stochastic game approach to the security issue of networked control systems under jamming attacks. J Franklin Institute, 2014, 351: 4570–4583
Yue D, Tian E G, Han Q-L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans Automat Contr, 2013, 58: 475–481
Heemels W P M H, Donkers M C F, Teel A R. Periodic event-triggered control for linear systems. IEEE Trans Automat Contr, 2013, 58: 847–861
Ge X H, Han Q-L, Wang Z. A threshold-parameter-dependent approach to designing distributed event-triggered H1 consensus filters over sensor networks. IEEE Trans Cybern, 2019, 49: 1148–1159
Ge X H, Han Q-L, Wang Z. A dynamic event-triggered transmission scheme for distributed set-membership estimation over wireless sensor networks. IEEE Trans Cybern, 2019, 49: 171–183
Ding L, Han Q-L, Ge X H, et al. An overview of recent advances in event-triggered consensus of multiagent systems. IEEE Trans Cybern, 2018, 48: 1110–1123
Ge X H, Han Q-L, Zhang X-M, et al. Distributed event-triggered estimation over sensor networks: a survey. IEEE Trans Cybern, 2019. doi: 10.1109/TCYB.2019.2917179
Ding L, Han Q-L, Zhang X-M. Distributed secondary control for active power sharing and frequency regulation in islanded microgrids using an event-triggered communication mechanism. IEEE Trans Ind Inf, 2019, 15: 3910–3922
de Persis C, Tesi P. Input-to-state stabilizing control under denial-of-service. IEEE Trans Automat Contr, 2015, 60: 2930–2944
Foroush H S, Mart´ınez S. On triggering control of single-input linear systems under pulse-width modulated DoS signals. SIAM J Control Opt, 2016, 54: 3084–3105
Feng S, Tesi P. Resilient control under Denial-of-Service: robust design. Automatica, 2017, 79: 42–51
Dolk V S, Tesi P, de Persis C, et al. Event-triggered control systems under denial-of-service attacks. IEEE Trans Control Netw Syst, 2017, 4: 93–105
Cetinkaya A, Ishii H, Hayakawa T. Networked control under random and malicious packet losses. IEEE Trans Automat Contr, 2017, 62: 2434–2449
Lu A Y, Yang G H. Input-to-state stabilizing control for cyber-physical systems with multiple transmission channels under denial of service. IEEE Trans Automat Contr, 2018, 63: 1813–1820
Sun Y C, Yang G H. Periodic event-triggered resilient control for cyber-physical systems under denial-of-service attacks. J Franklin Institute, 2018, 355: 5613–5631
Peng C, Li J C, Fei M R. Resilient event-triggering H1 load frequency control for multi-area power systems with energy-limited DoS attacks. IEEE Trans Power Syst, 2017, 32: 4110–4118
Hu S L, Yue D, Xie X P, et al. Resilient event-triggered controller synthesis of networked control systems under periodic DoS jamming attacks. IEEE Trans Cybern, 2019, 49: 4271–4281
Chen X L, Wang Y G, Hu S L. Event-based robust stabilization of uncertain networked control systems under quantization and denial-of-service attacks. Inf Sci, 2018, 459: 369–386
Liu J L, Wei L L, Xie X P, et al. Quantized stabilization for T-S fuzzy systems with hybrid-triggered mechanism and stochastic cyber-attacks. IEEE Trans Fuzzy Syst, 2018, 26: 3820–3834
Hu S L, Han Y X, Chen X L, et al. Event-triggered H1 filtering over wireless sensor networks under unknown periodic DoS jamming attacks. In: Proceedings of the 30th Chinese Control and Decision Conference, Shenyang, 2018. 1433–1438
Gao H J, Chen T W. Network-based H1 output tracking control. IEEE Trans Automat Contr, 2008, 53: 655–667
Hu S L, Zhang Y N, Du Z P. Network-based H1 tracking control with event-triggering sampling scheme. IET Control Theor Appl, 2012, 6: 533–544
Zhang D W, Han Q-L, Jia X C. Network-based output tracking control for T-S fuzzy systems using an event-triggered communication scheme. Fuzzy Sets Syst, 2015, 273: 26–48
Gu Z, Yue D, Liu J L, et al. H1 tracking control of nonlinear networked systems with a novel adaptive event-triggered communication scheme. J Franklin Institute, 2017, 354: 3540–3553
Yan H C, Hu C Y, Zhang H, et al. H1 output tracking control for networked systems with adaptively adjusted event-triggered scheme. IEEE Trans Syst Man Cybern Syst, 2019, 49: 2050–2058
Chen X L, Hu S L. Event-based output tracking control for networked T-S fuzzy systems under non-periodic DoS jamming attacks, In: Proceedings of the 2018 Australian & New Zealand Control Conference (ANZCC), Melbourne, 2018. 69–74
Takagi T, Sugeno M. Fuzzy identification of systems and its applications to modeling and control. IEEE Trans Syst Man Cybern, 1985, 15: 116–132
de Persis C, Tesi P. Resilient control under denial-of-service. IFAC Proc Volumes, 2014, 47: 134–139
Lam H K, Narimani M. Stability analysis and performance design for fuzzy-model-based control system under imperfect premise matching. IEEE Trans Fuzzy Syst, 2009, 17: 949–961
Peng C, Wu M, Xie X P, et al. Event-triggered predictive control for networked nonlinear systems with imperfect premise matching. IEEE Trans Fuzzy Syst, 2018, 26: 2797–2806
Gu Z, Yue D, Tian E G. On designing of an adaptive event-triggered communication scheme for nonlinear networked interconnected control systems. Inf Sci, 2018, 422: 257–270
Zhang X M, Han Q-L, Zeng Z G. Hierarchical type stability criteria for delayed neural networks via canonical Bessel- Legendre inequalities. IEEE Trans Cybern, 2018, 48: 1660–1671
Tseng C S, Chen B S, Uang H J. Fuzzy tracking control design for nonlinear dynamic systems via T-S fuzzy model. IEEE Trans Fuzzy Syst, 2001, 9: 381–392
Acknowledgements
This work was supported by National Natural Science Foundation of China (Grant No. 61771256).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chen, X., Wang, Y. Event-triggered attack-tolerant tracking control design for networked nonlinear control systems under DoS jamming attacks. Sci. China Inf. Sci. 63, 150207 (2020). https://doi.org/10.1007/s11432-019-2691-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-019-2691-4