Abstract
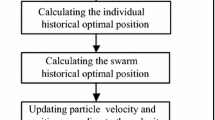
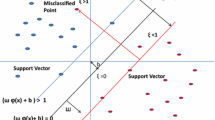
Support vector machine (SVM) is a renowned machine learning technique, which has been successfully applied to solve many practical pattern classification problems. One of the difficulties in successful implementation of SVM is its different parameters (i.e., kernel parameter(s), penalty parameter (C) and the features available in the dataset), which should be well adjusted during the training process. In this paper, a new approach called smart adaptive particle swarm optimization–support vector machine (SAPSO–SVM) is developed to adapt the parameters of optimization algorithm (i.e., inertia weight and acceleration coefficients) to the latest changes in the search space, so that each particle explicitly explores the search space based on the latest changes made to Personal best, Global best and other particle locations. In this algorithm, using the changes in Personal best and Global best at each stage of execution, the new evolution factor values are designated and the interference of the intervals of inertia weight is eradicated. Then, the states of each particle (i.e., convergence, exploitation, exploration, jumping-out) at each stage of administration, based on the interval weights, are specified accurately. By fine tuning the parameters of SAPSO, this algorithm can acquire the best optimal responses for SVM parameters. The results obtained from the SAPSO–SVM method demonstrate the superiority of this method in four different measures (i.e., sensitivity, specificity, precision, accuracy) in comparison with the other three similar ones. Finally, the top 20 features of Android botnets are somehow introduced by the proposed approach and three other approaches; firstly, these features are not encrypted by Android botnets, and secondly, are selected based on the best results.



Similar content being viewed by others
References
Kennedy J (2010) Particle swarm optimization. In: Sammut C, Webb GI (eds) Encyclopedia of machine learning. Springer, Boston, pp 760–766
Zhan Z, Zhang J, Li Y, Chung HS (2009) Adaptive particle swarm optimization. IEEE Trans Syst Man Cybern Part B Cybern 39(6):1362–1381
Taherkhani M, Safabakhsh R (2016) A novel stability-based adaptive inertia weight for particle swarm optimization. Appl Soft Comput 38:281–295
Khare A, Rangnekar S (2013) A review of particle swarm optimization and its applications in solar photovoltaic system. Appl Soft Comput 13(5):2997–3006
Chauhan P, Deep K, Pant M (2013) Novel inertia weight strategies for particle swarm optimization. Memet Comput 5(3):229–251
Kennedy J, Eberhart RC (1997) A discrete binary version of the particle swarm algorithm. In: 1997 IEEE International Conference on Systems, Man, and Cybernetics. Computational Cybernetics and Simulation, vol 5, pp 4104–4108
Moodi M, Ghazvini M (2018) A new method for assigning appropriate labels to create a 28 standard android botnet dataset (28-SABD). J Ambient Intell Humaniz Comput 10:4579–4593
Sharafaldin I, Lashkari AH, Ghorbani AA (2018) Toward generating a new intrusion detection dataset and intrusion traffic characterization. In: Information Systems Security and Privacy: ICISSP
Mas’ud MZ, Sahib S, Abdollah MF, Selamat SR, Yusof R (2014) Analysis of features selection and machine learning classifier in android malware detection. In: 2014 International Conference on Information Science and Applications (ICISA), pp 1–5
Shanthi K, Seenivasan D (2015) Detection of botnet by analyzing network traffic flow characteristics using open source tools. In: 2015 IEEE 9th International Conference on Intelligent Systems and Control (ISCO), pp 1–5. IEEE
Lu W, Rammidi G, Ghorbani AA (2011) Clustering botnet communication traffic based on n-gram feature selection. Comput Commun 34(3):502–514
Gu G, Perdisci R, Zhang J, Lee W (2008) BotMiner: clustering analysis of network traffic for protocol-and structure-independent botnet detection. USENIX Secur Symp 5(2):139–154
Chen C-M, Lin H-C (2015) Detecting botnet by anomalous traffic. J Inf Secur Appl 21(Supplement C):42–51
Karim A, Salleh R, Khan MK (2016) SMARTbot: a behavioral analysis framework augmented with machine learning to identify mobile botnet applications. PLoS ONE 11(3):e0150077
Meng X, Spanoudakis G (2016) MBotCS: a mobile botnet detection system based on machine learning. In: Lambrinoudakis C, Gabillon A (eds) Risks and Security of Internet and Systems: 10th International Conference, CRiSIS 2015, Mytilene, Lesbos Island, Greece, July 20–22, 2015, Revised Selected Papers. Springer, Cham, pp 274–291
Hijawi W, Alqatawna J, Faris H (2017) Toward a detection framework for android botnet. In: 2017 International Conference on New Trends in Computing Sciences (ICTCS), pp 197–202
Canbek G, Sagiroglu S, Temizel TT (2018) New techniques in profiling big datasets for machine learning with a concise review of android mobile malware datasets. In: 2018 International Congress on Big Data, Deep Learning and Fighting Cyber Terrorism (IBIGDELFT), pp 117–121
Chang C-C, Lin C-J (2011) LIBSVM: a library for support vector machines. ACM Trans Intell Syst Technol 2(3):1–27
Boser BE, Guyon IM, Vapnik VN (1992) A training algorithm for optimal margin classifiers. In: Proceedings of the Fifth Annual Workshop on Computational Learning Theory, Pittsburgh, Pennsylvania, USA
Cortes C, Vapnik V (1995) Support-vector networks. Mach Learn 20(3):273–297
Tianping C, Hong C (1995) Approximation capability to functions of several variables, nonlinear functionals, and operators by radial basis function neural networks. IEEE Trans Neural Netw 6(4):904–910
García Nieto PJ, García-Gonzalo E, Alonso Fernández JR, Díaz Muñiz C (2017) A hybrid wavelet kernel SVM-based method using artificial bee colony algorithm for predicting the cyanotoxin content from experimental cyanobacteria concentrations in the Trasona reservoir (Northern Spain). J Comput Appl Math 309(Supplement C):587–602
Huang C-L, Dun J-F (2008) A distributed PSO–SVM hybrid system with feature selection and parameter optimization. Appl Soft Comput 8(4):1381–1391
Clerc M, Kennedy J (2002) The particle swarm-explosion, stability, and convergence in a multidimensional complex space. IEEE Trans Evol Comput 6(1):58–73
Wang Y, Li B, Weise T, Wang J, Yuan B, Tian Q (2011) Self-adaptive learning based particle swarm optimization. Inf Sci 181(20):4515–4538
Zuo X, Zhang G, Tan W (2014) Self-adaptive learning PSO-based deadline constrained task scheduling for hybrid IaaS cloud. IEEE Trans Autom Sci Eng 11(2):564–573
Boussaïd I, Lepagnot J, Siarry P (2013) A survey on optimization metaheuristics. Inf Sci 237:82–117
Boussaïd I, Lepagnot J, Siarry P (2013) A survey on optimization metaheuristics. Inf Sci 237(Supplement C):82–117
Nickabadi A, Ebadzadeh MM, Safabakhsh R (2011) A novel particle swarm optimization algorithm with adaptive inertia weight. Appl Soft Comput 11(4):3658–3670
Anwar S, Zolkipli MF, Inayat Z, Odili J, Ali M, Zain JM (2018) Android botnets: a serious threat to android devices. Pertanika J Sci Technol 26(1):37–70
Abdul Kadir AF, Stakhanova N, Ghorbani AA (2015) Android botnets: what URLs are telling us. In: Qiu M, Xu S, Yung M, Zhang H (eds) Network and System Security: Proceedings of 9th International Conference, NSS 2015, New York, NY, USA, November 3–5, 2015. Springer, Cham, pp 78–91
Kirubavathi G, Anitha R (2018) Structural analysis and detection of android botnets using machine learning techniques. Int J Inf Secur 17(2):153–167
Alothman B, Rattadilok P (2017) Android botnet detection: an integrated source code mining approach. In: 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), pp 111–115
Karim A, Salleh R, Shah SAA (2015) DeDroid: a mobile botnet detection approach based on static analysis. In: 2015 IEEE 12th International Conference on Ubiquitous Intelligence and Computing and 2015 IEEE 12th International Conference on Autonomic and Trusted Computing and 2015 IEEE 15th International Conference on Scalable Computing and Communications and its Associated Workshops (UIC-ATC-ScalCom), 2015, pp 1327–1332
Arshad S, Shah MA, Khan A, Ahmed M (2016) Android malware detection and protection: a survey. Int J Adv Comput Sci Appl 7:463–475
Hojjatinia S, Hamzenejadi S, Mohseni H (2019) Android botnet detection using convolutional neural networks. arXiv preprint arXiv:1911.12457
He P, Gan G (2020) Android malicious app detection based on CNN deep learning algorithm. IOP Conf Ser Earth Environ Sci 428:012061
Agarwal S, Rajesh R, Ranjan P (2017) FRBPSO: a fuzzy rule based binary PSO for feature selection. Proc Natl Acad Sci India Sect A Phys Sci 87(2):221–233
Jin B, Tang YC, Zhang Y-Q (2007) Support vector machines with genetic fuzzy feature transformation for biomedical data classification. Inf Sci 177(2):476–489
SABD (2018). http://mobilebotnet.ir/. Published 24 Nov 2018
Ghazvini M, Monadjemi SA, Movahhedinia N, Jamshidi K (2009) Defect detection of tiles using 2D-wavelet transform and statistical features
Lashkari AH, Draper-Gil G, Mamun MSI, Ghorbani AA (2017) Characterization of Tor traffic using time based features. In: ICISSP, 2017, pp 253–262
Gil GD, Lashkari AH, Mamun M, Ghorbani AA (2016) Characterization of encrypted and VPN traffic using time-related features. In: Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP 2016), 2016, pp 407–414
Acknowledgements
The authors are grateful to Dr. Gholamreza Nakhaeizadeh (APL-Professor of Economics and Econometrics, Karlsruhe Institute of Technology, Germany) and Dr. Mohammad GhasemiGol (Assistant Professor, University of Birjand, Iran) for their valuable contributions in this study. Authors also kindly appreciate Birjand University of Technology for their kind help to conduct the study experiments in the university research laboratory.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Moodi, M., Ghazvini, M., Moodi, H. et al. A smart adaptive particle swarm optimization–support vector machine: android botnet detection application. J Supercomput 76, 9854–9881 (2020). https://doi.org/10.1007/s11227-020-03233-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03233-x