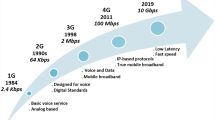
Abstract
Organizations are continually looking for ways to increase the effectiveness of their product and service delivery through supply chain collaborations. Recent technologies (both software and hardware) have been designed to facilitate supply chain collaboration and partnership. Due to the different operational environment throughout the supply chain, the application of these technologies are very often disconnected, causing various operational wastes. We investigate this problem and propose the concept of flexible technology. We use RFID system as an example and investigate the issues related to the electromagnetic regulation in various health care environments. We propose a flexible technology system framework that automatically learns and evolves to accommodate environmental variations throughout the supply chain. Our results show that flexible technology can greatly increase supply chain productivity and collaboration efficacy. In conclusion, we discuss its managerial implications and conditions.
















Similar content being viewed by others
References
Ashar BS, Ferriter A (2007) Radiofrequency identification technology in health care: benefits and potential risks. JAMA 298:2305–2307
Bose I, Lui AKH, Ngai EWT (2011) The impact of RFID adoption on the market value of firms: an empirical analysis. J Organ Comput Electr Commerce 21(4):268–294
Bose I, Leung ACM (2008) Radio frequency identification for customer relationship management. In: Blecker T, Huang G (eds) RFID in operations and supply chain management: research and applications. Erich Schmidt Verlag Publishing, Berlin, pp 273–288
Byrd TA, Turner DE (2000) Measuring the flexibility of information technology infrastructure: exploratory analysis of a construct. J Manag Inf Syst 17(1):167–208
Juels A, Weis S (2005) Authenticating pervasive devices with human protocols. In: Shoup V (ed) Advanced in cryptology—CRYPTO’05, vol 3126. Lecture notes in computer science, pp 293–308, Springer
Meiller Y, Bureau S, Zhou W, Piramuthu S (2011) Adaptive knowledge-based system for health care applications with RFID-generated information. Decis Support Syst 51(1):198–207
Nelson KM, Ghods M (1998) Measuring technology flexibility. Eur J Inf Syst 7(4):232–240
Piramuthu S (2007) Protocols for RFID tag/reader authentication. Decis Support Syst 43(3):897–914
Piramuthu S (2011) RFID mutual authentication protocols. Decis Support Syst 50(2):387–393
Piramuthu S, Wochner S, Grunow M (2014) Should retail stores also RFID-tag ‘cheap’ items? Eur J Oper Res 233(1):281–291
Seidman SJ, Brockman R, Lewis BM, Guag J, Shein MJ, Clement WJ, Kippols J, Digby D, Barber C, Huntwork D (2010) In vitro tests reveal sample radiofrequency identification readers inducing clinically significant electromagnetic interference to implantable pacemakers and implantable cardioverter-defibrillators. HeartRhythm 7(1):99–107
Slack N (2005) The changing nature of operations flexibility. Int J Oper Prod Manag 25(12):1201–1210
Togt R, van Lieshout EJ, Hensbroek R, Beinat E, Binnekade JM, Bakker PJ (2008) Electromagnetic interference from radiofrequency identification inducing potentially hazardous incidents in critical care medical equipment. JAMA 299:2884–2890
Tu Y-J, Zhou W, Piramuthu S (2009) Identifying RFID-embedded objects in pervasive healthcare applications. Decis Support Syst 46(2):586–593
Whang S (2010) Timing of RFID adoption in a supply chain. Manage Sci 56(2):343–355
Zhou W (2009) RFID and item-level information visibility. Eur J Oper Res 198(1):252–258
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhou, W., Piramuthu, S. IoT security perspective of a flexible healthcare supply chain. Inf Technol Manag 19, 141–153 (2018). https://doi.org/10.1007/s10799-017-0279-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10799-017-0279-7