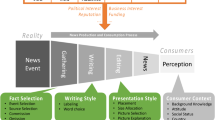
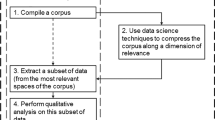
Abstract
Automated social media bots have existed almost as long as the social media environments they inhabit. Their emergence has triggered numerous research efforts to develop increasingly sophisticated means to detect these accounts. These efforts have resulted in a cat and mouse cycle in which detection algorithms evolve trying to keep up with ever evolving bots. As part of this continued evolution, our research proposes a multi-model ‘tool-box’ approach in order to conduct detection at various tiers of data granularity. To support this toolbox approach this research also uses random string detection applied to user names to filter twitter streams for bot accounts and use this as labeled training data for follow on research.

Similar content being viewed by others
References
Ananthalakshmi A (2018) Ahead of Malaysian polls, bots flood twitter with pro-government
Bawaba A (2017) The loop. Thousands of twitter bots are attempting to silence reporting on yemen
Beskow D, Carley KM (2018a) Bot conversations are different: leveraging network metrics for bot detection in twitter. In: 2018 international conference on advances in social networks analysis and mining (ASONAM), pp 176–183. IEEE
Beskow D, Carley KM (2018b) Introducing bothunter: a tiered approach to detection and characterizing automated activity on twitter. In: Halil B, Ayaz H, Chris D, Robert T (eds) International conference on social computing, behavioral-cultural modeling and prediction and behavior representation in modeling and simulation. Springer, Berlin
Beskow D, Carley KM (2018c) Using random string classification to filter and annotate automated accounts. In: Halil B, Ayaz H, Chris D, Robert T (eds) International conference on social computing, behavioral-cultural modeling and prediction and behavior representation in modeling and simulation. Springer, Berlin
Bessi A, Ferrara E (2016) Social bots distort the 2016 US presidential election online discussion
Chu Z, Gianvecchio S, Wang H, Jajodia S (2010) Who is tweeting on twitter: human, bot, or cyborg? In: Proceedings of the 26th annual computer security applications conference, pp 21–30. ACM
Davis CA, Varol O, Ferrara E, Flammini A, Menczer F (2016) Botornot: a system to evaluate social bots. In: Proceedings of the 25th international conference companion on world wide web, pp 273–274. International World Wide Web Conferences Steering Committee
Ferrara E (2017) Measuring social spam and the effect of bots on information diffusion in social media. arXiv:1708.08134
Freeman DM (2013) Using naive bayes to detect spammy names in social networks. In: Proceedings of the 2013 ACM workshop on artificial intelligence and security, pp 3–12. ACM
Freitas C, Benevenuto F, Ghosh S, Veloso A (2015) Reverse engineering socialbot infiltration strategies in twitter. In: Proceedings of the 2015 IEEE/ACM international conference on advances in social networks analysis and mining 2015, pp 25–32. ACM
Glaser A (2017) Russian bots are trying to sow discord on twitter after Charlottesville
Graham T, Ackland R (2016) Do socialbots dream of popping the filter bubble? Socialbots and their friends: digital media and the automation of sociality, p. 187
Howard PN, Kollanyi B (2016) Bots Bence Kollanyi,# strongerin,# brexit: computational propaganda during the uk-eu referendum. Browser download this paper
Krishnamurthy B, Gill P, Arlitt M (2008) A few chirps about twitter. In: Proceedings of the first workshop on Online social networks, pp 19–24. ACM
Lee K, Eoff BD, Caverlee J (2011) A long-term study of content polluters on twitter. In: ICWSM, seven months with the devils
Lumezanu C, Feamster N, Klein H (2012) # bias: measuring the tweeting behavior of propagandists. In: Sixth international AAAI conference on weblogs and social media
Matthew B, Kathleen CM (2016) From tweets to intelligence: understanding the Islamic Jihad supporting community on twitter. In: Social, cultural, and behavioral modeling: 9th international conference, SBP-BRiMS 2016, Washington, DC, USA, June 28–July 1, 2016, Proceedings 9, pp. 346–355. Springer, Berlin
Namazifar M (2015) Detecting randomly generated strings
Neudert LM, Kollanyi B, Howard PN (2017) Junk news and bots during the German federal presidency election: what were German voters sharing over twitter?
Pedregosa F, Varoquaux G, Gramfort A, Michel V, Thirion B, Grisel O, Blondel M, Prettenhofer P, Weiss R, Dubourg V, Vanderplas J, Passos A, Cournapeau D, Brucher M, Perrot M, Duchesnay E (2011) Scikit-learn: machine learning in Python. J Mach Learn Res 12:2825–2830
Raghuram J, Miller DJ, Kesidis G (2014) Unsupervised, low latency anomaly detection of algorithmically generated domain names by generative probabilistic modeling. J Adv Res 5(4):423–433
Shannon CE (1948) A mathematical theory of communication. Bell Syst Tech J 27:379–423
Subrahmanian VS, Azaria A, Durst S, Kagan V, Galstyan A, Lerman K et al. (2016) The darpa twitter bot challenge. Computer 49(6):38–46
Twitter rate limiting. https://developer.twitter.com/en/docs/basics/rate-limiting. Accessed 2 May 2018
Verkamp J-P, Gupta M (2013) Five incidents, one theme: twitter spam as a weapon to drown voices of protest. In: FOCI
Yadav S, Kumar KRA., Reddy AL, Supranamaya R (2010) Detecting algorithmically generated malicious domain names. In: Proceedings of the 10th ACM SIGCOMM conference on Internet measurement, pp 48–61. ACM
Acknowledgements
This work was supported in part by the Office of Naval Research (ONR) Multidisciplinary University Research Initiative Award N000140811186 and Award N000141812108, the Army Research Laboratory Award W911NF1610049, Defense Threat Reductions Agency Award HDTRA11010102, and the Center for Computational Analysis of Social and Organization Systems (CASOS). The views and conclusions contained in this document are those of the authors and should not be interpreted as representing the official policies, either expressed or implied, of the ONR, ARL, DTRA, or the U.S. government.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Beskow, D.M., Carley, K.M. Its all in a name: detecting and labeling bots by their name. Comput Math Organ Theory 25, 24–35 (2019). https://doi.org/10.1007/s10588-018-09290-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10588-018-09290-1