Abstract
Interference channel, in which multiple user pairs communicate over shared resources, is a building block of communications networks. Here, the K-user interference channel (IC) aided by J instantaneous relays (IRs), i.e. relays without delay, is considered. For KICJR networks, where \(K>2\) and \(J>1\), the DoF performance and achievable schemes have not been investigated in literature. Here, we devise a novel achievable scheme, called restricted interference alignment (RIA), which restricts the received interference from each source at each destination in a limited sub-space, and then, aligns the restricted interferences. Furthermore, we develop an analytical tool for finding a tight upper bound on DoF of KICJR networks by analyzing the properness of the interference alignment equations. Moreover, we develop linear beamforming design for sources and relays based on the mean square error (MSE) minimization, as an achievable scheme. The performance evaluation results show that the achievable sum DoF by using the proposed RIA scheme and the MSE-based beamforming design match well with the derived upper bounds. Furthermore, the results confirm that the achieved sum DoF using the RIA scheme outperforms the existing achievable schemes. Motivated by these promising results, we further investigate impact of IRs in providing physical layer security, i.e. achieving secure DoF in interference networks. Specifically, we derive a lower bound on the achievable secure DoF by devising an achievable scheme, called transmission in the null space (TNS). This scheme makes the cross channels rank deficient and enables sources to select their transmit filters in the constructed null spaces. Performance evaluation shows that by leveraging IRs, the secure DoF performance of interference networks could be increased significantly. The proposed analytical framework in this work for rank deficiency-powered DoF analysis is expected to also attract attention from other research areas, e.g. beamforming design for millimeter wave communications.
Similar content being viewed by others
1 Introduction
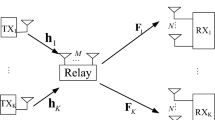
Interference, a consequence of the broadcast nature of wireless channels is a limiting factor for the capacity of wireless networks. The K-user interference channel (IC), in which K pairs communicate over a shared wireless medium, has profound attention for modeling communication in cellular and ad-hoc networks, e.g. the wireless backhauling of base stations (Fig. 1) [1], or BS-assisted device-to-device/vehicle-to-vehicle communications [2]. In this setting, source i transmits data for destination j, but this data is also received by other destinations, and hence, transmission from each user pair results in interference for other user pairs, as depicted in Fig. 2. In lack of information about other users of a K-user IC, interference-avoiding resource access schemes result in an achieved sum data rate equal to the case of one user pair communications. In other words, the pre-log factor of the sum data rate at high signal to noise ratio (SNR), also known as degrees of freedom (DoF),Footnote 1 is 1. When global channel state information (CSI) is available at each transmitter, they can employ an advanced linear precoding technique, called interference alignment (IA), in order to align the interfering signals in time, frequency, or spatial domain [3, 4]. In K-user IC with generic channel coefficients, IA can allocate approximately one-half of the available dimensions to the desired signals (by using infinite time extensions) and the other one to the interfering signals, i.e. asymptotically K / 2 degrees of freedom are achievable [5]. Then, all the interfering sources could be treated as a single interfering source, the degrees of freedom increase linearly with the number of users, and the interference channel becomes noise limited.
For interference channels with generic channel matrices and without time extensions, feasibility of the interference alignment has been investigated in [6]. By deriving the IA equation system and investigating its properness, the authors of [6] found upper bounds on the achievable DoF in the K-user interference channel with finite channel extensions. Later in [7], the general conditions which must be satisfied by any feasible DoF in the K-user interference channel with finite channel extensions were found. Using this condition, it was shown that \(\frac{2K}{K+1}\) degrees of freedom are achievable in the K-user interference channel. Further analyses on the DoF performance of KIC with limited and delayed CSI have been presented in [8,9,10,11]. In lower SNR regimes, when the power of noise is not negligible, the achieved sum rate of an IA-based network could be much less than the theoretical maximum [12]. To address this issue, several solutions, including adaptive power allocation and opportunistic communication, have been introduced in literature [13, 14].
While IA can increase the achievable DoF of the KIC from 1 to \(\frac{2K}{K+1}\) (without time extension), the system is still interference limited and by increasing the number of users K, the achievable DoF approaches 2. Then, many efforts have been carried out to further increase the achievable DoF, i.e. to let the DoF increase linearly with an increase in K. Motivated by the benefits of applying interference alignment for ICs, in [15, 16] interference alignment has been employed for achieving secure DoFFootnote 2 (SDoF) in a K-user IC. The authors of [16] have shown that for a K-user interference channel with confidential messages (KIC-CM), a network in which each undesired destination is a potential eavesdropper, \(\frac{K-2}{2K-2}\) SDoF are achievable by using secrecy and IA precoders. In [17], it has been shown that \(\frac{K(K-1)}{2K-1}\) SDoF are achievable in the K-user interference channel, when each node is equipped with one antenna. Recently in [18], the authors have shown that instead of mitigating interference in interference networks, one may benefit from cognitive interference of other users for masking its confidential messages, and hence, increasing its security. Motivated by the benefits achieved in using relays in wireless communications, the effect of relaying on the achievable DoF in interference networks has been investigated, and it has been shown that in general, relays cannot improve the achievable DoF [19]. However, in some special cases such as networks with cognitive relays, networks without power constraints at the relays, or networks with limited CSI available at transmitters, relaying can increase the achievable DoF [3]. In networks where relays cannot increase the DoF, relaying can simplify the achievable DoF scheme by enabling linear alignment schemes where nonlinear alignments are otherwise needed [3, 20].
Instantaneous memoryless relaying, in which the relay’s retransmitted signal depends on the presently received signals, has been introduced in [21]. In [22], practical motivations for instantaneous relay-aided IC have been presented, and it has been shown that a linear memoryless instantaneous relay (IR) can increase the achievable DoF of 2-user IC by 50%, i.e. 3M / 2 DoF are achievable, where M denotes the number of antennas at each node. These DoF are achieved using a new scheme called aligned interference neutralization (AIN). In the AIN scheme, source nodes select their transmit beamforming matrices to align some of the received signals at the relays to each other. Immediately, the relays scale the received signals and retransmit them such that these signals neutralize some of the interferences which are received directly from the sources. Let us denote by KICJR the K-user IC aided by J linear memoryless instantaneous relays. In [10, 23], the feasibility of interference alignment for 2IC1R with different numbers of antennas at sources, relay, and destinations has been investigated. The authors of [10] have shown that 3M/2 DoF are achievable in 2IC1R, where the number of relay’s antennas is less than M. DoF performance of 2-user interference channel aided by an instantaneous bidirectional relay has been investigated in [24]. In [25], performance of 3IC1R has been investigated.
1.1 Motivation and contribution
One sees while performance of KICJR has been investigated for up to \(K\le\)3 and \(J\le\) 1, the DoF region in the general form, i.e. for any K and J values, has not been investigated before, and is the focus of the present work. Our main aim is shedding light into the bound up to which, adding an extra instantaneous relay can increase the achievable DoF of a K-user IC. As a potential application of this work, one may consider the future 5G wireless networks, in which an ultra-dense access point deployment is envisioned in hot spots [26]. In this case, our proposed scheme can leverage the dormant access points in the service area as helper nodes to increase DoF of communications at the cost of extra energy consumption in the radio access network. Our approaches for dealing with such a complex network consists in providing lower- and upper bounds on the achievable DoF by devising achievable schemes and investigating the properness of interference alignment equation system, respectively. Motivated by the promising results of adding IRs to interference networks, and due to lack of previous art on the potential impact of IRs in providing physical layer security, we further investigate the achievable secure DoF leveraging IRs. We distinguish our work from the state-of-the-art works on SDoF of interference channels by considering a strong security constraint, which requires neutralization of the confidential signals on the air before arriving at the unintended destinations, and hence, we don’t put any constraint on the computation capability of the eavesdroppers. Then, we further shed light into the achievable strongly secure DoF (\({\mathbb {S}}\)DoF) of KICJR-CMFootnote 3 network. Towards this end, we derive a lower bound on the achievable \({\mathbb {S}}\) DoF by devising an achievable scheme called transmission in the null space of the channel (TNS). This scheme makes the cross channels, i.e. channels between unintended pairs, rank deficient leveraging instantaneous relays. Then, it is possible for sources to select their transmit filters in the null spaces of cross channels. We further provide upper bounds on the achievable \({\mathbb {S}}\)DoF by analyzing the necessary conditions for achieving rank deficiency in the cross channels. The performance evaluation results show that by leveraging instantaneous relaying, the \({\mathbb {S}}\)DoF performance of interference networks could be improved significantly.
The major contributions of this work are as follows.
1.1.1 Lower bound on the DoF performance of KICJR network
At first, we present the restricted interference alignment (RIA) scheme as an achievable scheme for interference channels aided by instantaneous relays. We further shed light into the DoF performance of the network by leveraging another achievable scheme, called MSE-based beamforming design.
1.1.2 Upper bound on the DoF performance of KICJR network
We derive upper bounds on the DoF performance of the KICJR by investigating the properness of the interference alignment equations. These bounds are validated by comparing against lower bounds from the RIA scheme and MSE-based beamforming.
1.1.3 Lower bound on the secure DoF performance of KICJR network
We present a \({\mathbb {S}}\)DOF achievable scheme for K-user interference channel aided by instantaneous relays, i.e. the TNS scheme, which outperforms the state-of-the-art \({\mathbb {S}}\)DoF achievable schemes.
1.1.4 Upper bound on the secure DoF performance of KICJR network
We derive upper bounds on the achievable \({\mathbb {S}}\)DoF by investigating the necessary conditions for making the cross channels rank deficient.
1.1.5 Novel analytical framework for rank deficiency analysis of matrices
We present a rigorous novel mathematical analysis on necessary conditions for rank deficiency of matrices. This analysis is expected to be of interest also for researchers in other research areas, e.g. beamforming design for millimeter wave communications.
1.2 Paper organization
The rest of this paper is organized as follows. In the next section, the system model and problem formulation are introduced. In Sect. 3, lower bounds on the achievable DoF using two achievable schemes, i.e. the RIA and MSE-minimization schemes, are presented. In Sect. 4, upper bounds on the DoF performance of the KICJR are presented. In Sect. 5, lower and upper bounds on the achievable secure DoF are presented. Performance evaluation results are presented in Sect. 6. The concluding Remarks are given in Sect. 7.
2 System model and problem formulation
2.1 System model
The K-user interference channel aided by J linear memoryless instantaneous relays is considered in this work (Fig. 1). Denote the set of users by \({\mathcal {K}} \triangleq \lbrace 1, \ldots , K \rbrace\). In this system, source \(S_i, i \in {\mathcal {K}}\) sends its independent message to its paired destination \(D_i\). The relays instantaneously amplify and forward the currently received data symbols from the sources to the destinations.Footnote 4 All nodes in the system have been equipped with M antennas. The channel coefficients between the nth source node and mth destination node, the nth source node and jth relay and the jth relay and mth destination node are denoted by \({\mathbf{{H}}}_{mn}^{ds}\), \({\mathbf{{H}}}_{jn}^{rs}\) and \({\mathbf{{H}}}_{mj}^{dr}\), respectively. Furthermore, all elements of the channel matrices are drawn independently from a Gaussian distribution with unit variance and zero mean.
2.2 Problem formulation
At source \(S_i\), \(i\in {\mathcal {K}}\), message \(W_i\) is split into \(\delta _i\) submessages, where \(\delta _i\) is the DoF for source i and \(\Delta =\sum _{i=1}^{K} \delta _i\) is the sum DoF. Submessage \(W_{i,j}, j \in \lbrace 1, \ldots , \delta _i\}\) is encoded using a Gaussian codebook with codewords of length n denoted as \(x_{i,j}\). Source \(S_i\) sends symbol \(x_{i,j}\) with the \(M \times 1\) beamforming vector \({\mathbf{{v}}}_{i,j}\). Then the transmit beamforming matrix, transmitted data stream, and transmitted signal for source i are as follows:
Now, one can write the received signal at relay j and destination k as
respectively. In this expression, \({\mathbf{{z}}}_j^r\) is the retransmitted signal from relay j, \({\mathbf{{n}}}_k\) is the noise vector at the destination k, and \({\mathbf{{n}}}_j^r\) is the noise vector at the jth relay. The noise vector components are independent random variables which follow a Gaussian complex distribution with zero mean and unit variance. Then, one can write the received signal at destination k as follows:
In this expression, \({\mathbf{{n}}}_k^t\) is the equivalent noise at destination k, \({\mathbf{{W}}}_j\) is the beamforming matrix at relay j, and \({\varvec{\Phi }}_{ki}\) is the equivalent channel matrix between source i and destination k, i.e. sum of direct and relay links. Using a linear receive beamforming matrix \({\mathbf{{R}}}_k\) at destination k, one can write the received data vector at the destination k as:
The DoF tuple (\(\delta _1, \ldots , \delta _K\)) is feasible if the beamforming matrices at users and relays can be designed such that the following conditions are satisfied:
This system of equations aims at aligning all the received interferences at destination k in an \(M-\delta _k\) dimensional subspace and tries to guarantee \(\delta _k\) interference-free dimensions for the desired data streams. Solvability of this interference alignment system of equations, as well as the achievable schemes, is investigated in this work.
3 Lower bound on the achievable DoF: the proposed achievable schemes
In order to shed light into the DoF region of KICJR networks, in the following, we present two achievable schemes. These achievable schemes provide lower bounds on the achievable DoF in a KICJR network.
3.1 The RIA scheme
Interference alignment has been shown to be a promising technique for interference management. In essence, this scheme limits the number of dimensions which are occupied by interfering streams [3]. By deploying instantaneous relays between sources and destinations in an interference channel, destination nodes receive multiple copies of the desired and the interfering signals. Then, one can design the beamforming matrices at the sources and the relays to cancel out as much interfering streams as possible. Here, we present an achievable scheme, called RIA, which benefits from instantaneous relays for decreasing the occupied dimensions by interfering streams at the destinations. In the following, the RIA scheme is presented in three steps: Restricting, Aligning, and Zero forcing.
3.1.1 First step: restricting dimension of received interference from each source at each destination
Denote the DoF of user i by \(\delta _i\). The received interference from source i at destination k is expressed as \({\varvec{\Phi }}_{ki}{} {\mathbf{{V}}}_i\), in which the rank of \({\mathbf{{V}}}_i\) is \(\delta _i\) to guarantee \(\delta _i\) DoF for user i. Then, the maximum number of dimensions which can be occupied by interfering streams at destination i is \(M-\delta _i\). In the first step of the RIA scheme, we decrease the dimension of the received interference from source i at destination k from \(\delta _i\) to \(M-\delta _k\), where \(i, k \in {\mathcal {K}}, i\ne k\). To this end, we need \([\delta _i+\delta _k-M]^+\) alignments for interfering streams of source i at destination k, such that these \(\delta _i\) streams span over \(M-\delta _k\) dimensions, where \([x]^+=\max (x, 0)\).
3.1.2 Second step: aligning the restricted interferences at each destination
Up to now, the available space at destination k has been spanned by \(K-1\) interference subspaces, where each of them has \(M-\delta _k\) dimensions. As the maximum number of dimensions which can be spanned by interference subspaces at destination k is \(M-\delta _k\), these \(K-1\) interference subspaces must be aligned to each other. Denote the (\(M-\delta _k\))-dimensional subspace reserved for interference at destination k by \({\varvec{\Psi }}_k\). Then, the following must hold:
This alignment can be done by adapting the transmit beamforming matrices at the sources, i.e. \({\mathbf{{V}}}_i\), or by adapting the beamforming matrices at the relays which construct the equivalent channel, \({\varvec{\Phi }}_{ki}\).
3.1.3 Third step: zero forcing at destinations
Applying step 1 and 2, the dimension of the received interference at destination k will become at most \(M-\delta _k\). As each destination has been equipped with M antennas, one can use zero-forcing beamforming at destination k to extract \(\delta _k\) desired streams from the \(M-\delta _k\) interfering streams.
One observes that the RIA scheme aims at converting the relay-aided interference channel to a conventional interference channel with low-rank, i.e. rank deficient, cross channels. Using instantaneous relays, the RIA scheme at first decreases the rank of the cross channels as much as possible while keeping the rank of the direct channels unchanged. Then, it applies a conventional interference alignment scheme to the equivalent interference channel.
3.2 The MSE-minimization scheme
In this section, we investigate an iterative algorithm for designing beamforming matrices at source, relay, and destination nodes such that the maximum degrees of freedom can be achieved. In this algorithm, the sum MSE of users is considered as the objective function to be minimized.
3.2.1 MSE-based beamforming algorithm
Using the definitions in Sect. 2, one can define the MSE at destination k as presented at the top of the next page. Also, as the messages from different users are independent from each other and from the noises, one can simplify the expression in (8) as follows:
where
By minimizing the \({\text {MSE}}_k, \forall k\), one may find the optimal set of beamforming matrices, but solving this problem is very hard, if not impossible. We use the sum MSE at the destinations as the objective function to be minimized and develop the optimization problem as follows:
in which, \(P_R^k\) and \(P_R^j\) are the power constraint at source k and relay j respectively. One can see that sum-MSE minimization over each set of beamforming matrices at the sources, relays, and destinations is convex, but it is not jointly convex. Then, an iterative algorithm for beamforming design is developed to minimize the sum MSE of the users. The procedure of this algorithm is as follows: (1) choose two sets of beamforming matrices as constants (e.g. beamforming matrices at the sources and the destinations); (2) derive the optimal filters for the third set (e.g. beamforming matrices at the relays); and (3) update the two constant sets. Then, we repeat this algorithm for the other combinations of beamforming matrices. One can write the Lagrangian function for the optimization problem in (10) as follows:
where \(\lambda _k\) and \(\gamma _j\) are Lagrange multipliers for satisfying the power constraint at source k and relay j. Using the K.K.T.Footnote 5 conditions, the optimal transmit beamforming matrix (the other two set of beamforming matrices are treated as constants) is written as follows:
By considering beamforming matrices at sources and relays as constants, one can optimize the beamforming at the destinations as
Finally the beamforming matrices at the relays are optimized as follows:
In Table 1, the iterative algorithm for the MSE-based beamforming is presented.
3.2.2 Convergence of MSE-based beamforming design
The presented iterative algorithm is guaranteed to converge, because the iterative process between the beamforming matrices is a monotonically decreasing function of the sum-MSE. As the sum-MSE is lower bounded at least by zero, this iterative algorithm always converges. However, the convergence to the global minimum is not guaranteed because the sum-MSE objective function is jointly non-convex over the beamforminng matrices at the sources, relays, and destinations. In numerical results, it is shown that the MSE-based beamforming provides a tight lower bound on the maximum achievable DoF in a KICJR network.
4 Upper bound on the achievable DoF: a rank deficiency analysis
In this section, upper bounds on the maximum achievable DoF in the K-user interference channel aided by J instantaneous relays are presented. These bounds are derived by investigating the solvability of the interference alignment system of equations in (5), (6). In the sequel, we present the prerequisites that will be used in the subsequent sections.
Lemma 1
Denote by\({\varvec{\Phi }}_{ki}\)the equivalent channel between source i and destination k, where\(i, k \in {\mathcal {K}}, i\ne k\). Then\(r_{ki}\triangleq [\delta _k+\delta _i-M]^+\) singular values of\({\varvec{\Phi }}_{ki}\) are zero, where\(\delta _i\) is the DoF for useri.
Proof
For guaranteeing \(\delta _k\) interference-free dimensions at destination k, the interference space from source i at destination k, \({\varvec{\Phi }}_{ki}{} {\mathbf{{V}}}_i\), must span up to \(M-\delta _k\) dimensions. As the rank of the transmit beamforming matrix at source i is \(\delta _i\), the rank of \({\varvec{\Phi }}_{ki}\) must not exceed \(M-\left( \delta _i-(M-\delta _k)\right) =2M-\delta _i-\delta _k\). Then, \([\delta _i+\delta _k-M]^+\) singular values of the equivalent channel matrix between source i and destination k have to be zero. \(\square\)
Lemma 2
Denote by \({\mathbf {C}}\) an \(m \times n\) matrix where its elements are drawn randomly from a continuous probability distribution and its rank is \(\min (m, n)\) with probability one. To reduce the rank of \({\mathbf{C}}\) from \(\min (m, n)\) to d, at least \((m-d)(n-d)\) elements of \({\mathbf{C}}\) are to be designed.
Proof
Denote by \({\mathbf{{c}}}_i\) the ith row of \({\mathbf{C}}\). Then one can derive the necessary conditions for \({\mathbf{C}}\) to have rank d, as follows:
in which \(k_{j,i}\) is a free variable. Using Remark 1, the properness of the polynomial system of equations in (14) is necessary for the solvability of (14). As each of the \(m-d\) equation sets in (14) has n equations (because each row of \({\mathbf{C}}\) consists of n elements), the total number of equations is \(n(m-d)\). Also, by counting the \(k_{i,j}\)s in (14), one can see that the total number of free variables is \(d(m-d)\). Then for solvability of (14), at least \((n-d)(m-d)\) elements of \({\mathbf{C}}\) are subject to change for rank reduction. \(\square\)
4.1 Necessary conditions on a DoF tuple to be feasible
A system of polynomial equations which is improper (overdetermined) may have solutions if some equations are interconnected. In our system, the elements of channel matrices are drawn from a continuous probability distribution, and hence, such a situation rarely occurs. Then, we proceed our analysis on solvability of equation system in (5)-(6) for a given DoF tuple by assuming improperness implies infeasibility, and hence, investigate properness of the equation system. Later in Sect. 6, we will examine tightness of this assumption by comparing it against the lower-bound from the proposed achievable scheme. In the following, we develop the necessary conditions which must be satisfied by any feasible DoF tuple in a KICJR, by analyzing properness of the equation system in (5), (6).
4.1.1 The first necessary condition
The first necessary condition comes from the limited number of dimensions at each user, as follows:
4.1.2 The second necessary condition
Using Lemma 1, all interferences at destination k must be encapsulated in a subspace with \(M-\delta _k\) dimensions. The total number of received signals at destination k is \(\Delta\), where \(\Delta -\delta _k\) of them are interfering signals. The interfering streams can be shown in an M-by-\((\sum _{i\in {\mathcal {K}}, i\ne k}\delta _k)\) matrix as follows:
Then, the rank of \({\mathbf{{X}}}_k\) must be less than or equal to \(M-\delta _k\). Using lemma 2, for decreasing the rank of \({\mathbf{{X}}}_k\) to \(M-\delta _k\), one needs at least
free variables. Then for all destinations together, \((\Delta -M)\Delta\) free variables are required. Now we count the number of free variables in the beamforming matrices at the sources and the relays, to check the properness of the rank reduction problem. The transmit beamforming matrix at source i, \({\mathbf{{V}}}_i\), is an \(M\times \delta _i\) matrix and its rank is \(\delta _i\). Then, \(\delta _i^2\) elements of \({\mathbf{{V}}_i}\) are used for satisfying the rank constraint, and hence, there are \(\delta _i(M-\delta _i)\) free variables at \({\mathbf{{V}}_i}\). Considering the transmit beamforming matrices at all sources, there are \(\sum \nolimits_{i=1}^{K}\delta _i(M-\delta _i)\) free variables at the sources. Also, there are at most \(JM^2\) free variables at the relays. Then, the following condition must be held for properness of rank reduction in \({\mathbf{{X}}}_k\):
4.1.3 The third necessary condition
As mentioned in the above, the rank of \({{\mathbf{{X}}}_k}\) must be less than or equal to \(M-\delta _k\). Then the rank of \({\varvec{\Phi }}_{ki}{} {\mathbf{{V}}}_i\) has to be less than or equal to \(M-\delta _k\), where \(i, k \in {\mathcal {K}}, i\ne k\). Furthermore, as the transmit beamforming matrix at source k is of full rank, the channel matrix \({\varvec{\Phi }}_{ki}\) must be rank deficient, and this can happen by using appropriate beamforming design at the relays. Using lemma 2, for \({\varvec{\Phi }}_{ki}\) to have \(r_{ki}=\left[ \delta _k+\delta _i-M\right] ^+\) zero singular values, we need at least \(r_{ki}^2\) free variables at the relays. By considering all cross channels, \({\varvec{\Phi }}_{ki}, i\ne k\); one can write the third necessary condition on feasible DoF tuples as follows:
4.1.4 The fourth necessary condition
Here, we present a strong necessary condition for the feasibility of a DoF tuple in the KIC1R, and verify its necessity. In other words, this necessary condition does not come just from the properness analysis of the equation system.
Proposition 1
Denote by\({\mathbf{{A}}}\) and\({\mathbf{{B}}}\) two\(M\times M\) full rank matrices. A necessary condition on the existence of matrix\({\mathbf{{W}}}\) which satisfies
is described as\(r_A+r_B \le M\).
Proof
Consider the following system of equations:
where \({\mathbf{{F}}}_1\) and \({\mathbf{{F}}}_2\) have \(M-r_A\) rows and M columns; \({\mathbf{{G}}}_1\) and \({\mathbf{{G}}}_2\) have \(M-r_B\) rows and M columns. The elements of these four matrices and \({\mathbf{{W}}}\) are to be designed such that the equations in (46), (47) could be satisfied. Also, the rank of \({\mathbf{{F}}}_i\) and \({\mathbf{{G}}}_i\) matrices must be \(M-r_A\) and \(M-r_B\), respectively for \(i=1,2\). One can write the difference of (47) and (46) as follows:
As \({\mathbf{{A}}}\) and \({\mathbf{{B}}}\) are full rank matrices, their difference is full rank with probability one. Then, for consistency of (46), (47), the right hand of (48) must be of full rank. But as the ranks of \({\mathbf{{F}}}_{1}^{T}{} {\mathbf{{F}}}_2\) and \({\mathbf{{G}}}_{1}^{T}{} {\mathbf{{G}}}_2\) are \(M-r_A\) and \(M-r_B\), respectively, the rank of their sum is less than or equal to \(\min (2M-r_A-r_B, M)\). Hence, one can derive the necessary condition on the solvability of (46), (47) as follows:
and the proof is completed. \(\square\)
Now, in a KIC1R network, for the channel matrices \({\varvec{\Phi }}_{ki}\) and \({\varvec{\Phi }}_{ik}\) to have \(r_{ki}\) and \(r_{ik}\) zero singular values, the following equations should be held:
in which \({\mathbf{{W}}}_1\) is the beamforming matrix at the relay, and the channel matrices are \(M\times M\) dimensional. The matrices \({\mathbf{{F}}}\) and \({\mathbf{{G}}}\) have \(M-r_{ki}\) rows and M columns, and the matrices \({\mathbf{{Y}}}\) and \({\mathbf{{Z}}}\) have \(M-r_{ik}\) rows and M columns, respectively. We design matrices \({\mathbf{{W}}}_1\), \({\mathbf{{F}}}\), \({\mathbf{{G}}}\), \({\mathbf{{Y}}}\), and \({\mathbf{{Z}}}\) such that the system of equations in (50), (51) is satisfied, and the four latter matrices become full rank. As the elements of the channel matrices are drawn from continuous probability distributions, the channel matrices are full rank with probability one, and they are invertible. Then it is straightforward to rewrite (50), (51) as follows:
in which
Using the condition in (49) for solvability of (25), we conclude that \(r_{ki}+r_{ik} \le M\) must hold, which means:
Now, we can summarize all investigated necessary conditions on feasible DoF tuples as follows:
Proposition 2
The\((\delta _1,\dots ,\delta _k)\)DoF tuple is feasible in the KICJR if it satisfies the following conditions:
4.2 Using upper bounds for DoF performance evaluation
One can leverage the derived necessary conditions in (30)–(33) to analyze the DoF performance of different interference networks. In the following, we analyze the maximum achievable DoF in 2IC1R, KIC0R, and KICK(K-1)R networks.
Proposition 3
The maximum achievable degrees of freedom in a 2IC1R network is \(\left\lfloor 1.5M \right\rfloor .\)
Proof
Based on the necessary condition in (33), the following bound is held in a 2IC1R network: \(\delta _1+\delta _2=\Delta \le \left\lfloor 1.5M \right\rfloor .\) Also, in [22] it has been shown that \(\left\lfloor 1.5M \right\rfloor\) degrees of freedom are achievable in a 2IC1R network using the AIN scheme. Then, the maximum achievable DoF in this network is \(\left\lfloor 1.5M \right\rfloor\). \(\square\)
As the DoF performance of a K-user interference channel is known from [7], one can use the derived bounds for the KICJR in (30)–(33) for the case in which \(J=0\), and compare the results for cross validation, as follows.
Proposition 4
For the\((\delta _1, \dots , \delta _K)\) DoF tuple to be feasible in aKIC0R, the following conditions must be met:
Proof
Here, we prove that the results in (34)–(36) are consistent with the results of [7]. The condition in (34) comes from the limited number of antennas at each node, and is the same as (4) in [7]. The equation in (35) is the extension of (30) when there is no instantaneous relays, and counts the number of equations and unknowns as follows:
By subtracting \(\sum \nolimits_{k=1}^{K}\delta _k^2\) from both sides of (37), we have:
which is in accordance with (6) in [7]. Also, in lemma 1, it has been shown that the equivalent channel matrix \({\varvec{\Phi }}_{ki}\) between source i and destination k, must have \(\left[ \delta _i+\delta _k-M\right] ^+\) zero singular values. The beamforming matrices at the relays make the cross channels rank deficient and provide zero singular values. In a KIC0R network, as there is no instantaneous relays, the number of zero singular values must be zero. Then, the following condition must be held: \(\delta _i+\delta _j \le M\). This conditions is in accordance with (5) in [7], and the proof is completed. \(\square\)
In the following, we investigate the required number of instantaneous relays for achieving the full DoF of the K-user interference channel.
Proposition 5
Consider theK-user IC. Using\(K(K-1)\)instantaneous relays, KM degrees of freedom are achievable.
Proof
As there are \(K\times (K-1)\) interfering channels in a K-user interference channel, the relays must provide M zero singular values at each cross channel matrix. The channel matrices are M-by-M and the only rank zero M-by-M matrix is the all-zero matrix. Then, \(K(K-1)\) linear system of equations must satisfied, where in each of them, there are \(M^2\) zero forcing equations. The system of equations for removing the interfering channel between source i and destination k could be written as
in which, \(f=K(K{\text {-}}1)\). Using the Kronecker product, one can rewrite (38) as:
where \({\mathbf{{w}}}_k=\mathrm{{vec}}({\mathbf{{W}}}_k)\) and \(\mathrm{{vec}}({\mathbf{{A}}})\) is the column vector built from the columns of \({\mathbf {A}}\). Now, we can reshape the \(K\times (K\text {-}1)\) systems of equations, required for removing all the interfering channels, in a matrix form, and rewrite the overall problem as shown on top of the next page, in which \({\mathbf{{h}}}_{ki}^{xy}=\mathrm{{vec}}({\mathbf{{H}}}_{ki}^{xy})\). As the channel matrices are full rank with probability one, and the rank of the Kronecker product of two matrices is equal to the product of their ranks, the coefficient matrix in (40) is of full rank, and the system of equations in (40) has a unique solution. This unique solution gives the beamforming matrices at the relays for removing interfering channels between undesired users, and achieves KM degrees of freedom. \(\square\)
In Sect. 6, we will investigate the DoF performance of the proposed RIA scheme, and will show that the achieved DoF performance by this scheme well matches the derived upper bounds in this section.
5 Physical layer security using instantaneous relays
In this section, we investigate the impact of instantaneous relays in providing physical layer security, i.e. achieving secure DoF in interference networks. Towards this end, we investigate lower and upper bounds on the achievable \({\mathbb {S}}\)DoF in presence and lack of instantaneous relays, and compare them later in Sect. 6.
5.1 Lower bound on the achievable \({\mathbb {S}}\)DoF: the TNS scheme
Here, we investigate the proposed \({\mathbb {S}}\)DoF achieving scheme for the KICJR network. Based on the strong security constraint, described in the previous section, the transmitted signals to all unintended destinations should be removed on the air. This scheme, called TNS, is presented in the following two steps.
5.1.1 Step 1: blocking one unintended destination by transmitting data in the artificial null space of the respective cross channel
In this step, we neutralize the interference from source i, \(\forall i\in {\mathcal {K}}\), at one unintended destination, \(l \in {\mathcal {K}}, l\ne i\). Without loss of generality, let us assume \(l=i+1\) for \(i\in {\mathcal {K}}\setminus K,\) and \(l=1\) for \(i=K\). We design \(r_{li}^2\) elements of the transmit filters at relays such that the null space of \({\varvec{\Phi }}_{li}\) becomes \(\delta _i\) dimensional. In other words, we design the equivalent cross channel \({\varvec{\Phi }}_{li}\) such that it has \(r_{ki}\) rank deficiencies.Footnote 6 This problem could be expressed as follows,
in which, \({\mathbf{{Y}}}_{ki}\) and \({\mathbf{{Z}}}_{ki}\) have \(M-r_{ki}\) rows and M columns, and the equality is achieved by designing \({\mathbf{{Y}}}_{ki}\), \({\mathbf{{Z}}}_{ki}\), and \({\mathbf{{W}}}_{j}\) matrices. Then, the transmit filter at source i is designed to be in the null space of the respective cross channel, i.e. \({\varvec{\Phi }}_{li}\), \(\forall i\in {\mathcal {K}}\). This guarantees that the confidential message of source i will not be received at destination l, and hence, the strong notion of secrecy is satisfied [28]. Up to now, the interference from each source has been removed in one unintended destination. For the 2-user interference channel, the proposed achievable scheme is terminated in the step because there is only one potential eavesdropper in the network. For \(K\ge 3\), we have the following step as well.
5.1.2 Step 2: blocking the \(K-2\) remaining unintended destinations by making the respective cross channels rank deficient
In this step, the interferences from source \(i, \forall i\in {\mathcal {K}}\) at destination \(k, k\in {\mathcal {K}}\setminus \{i,l\}\) are removed. As the transmit filter at source i has been already designed, we leverage the processing filters of relays to design the null space of cross channel \({\varvec{\Phi }}_{ki}, k\in {\mathcal {K}}, k\ne i,k\ne l\), according to the previously designed transmit filter of user i, i.e. \({\mathbf{{V}}}_i\). Then, in destination k, only signals from source k will arrive, and the confidential messages of other sources will be removed on the air, before arriving at the kth destination.
This achievable scheme provides a lower bound on the achievable \({\mathbb {S}}\)DoF in K-user interference channels aided by instantaneous relays. In Sect. 6, we evaluate performance of this achievable scheme, and compare it against the upper bounds derived in the next section.
5.2 Upper bound on the achievable \({\mathbb {S}}\)DoF: the rank deficiency analysis
In this subsection, we aim at investigating achievability of a \({\mathbb {S}}\)DoF tuple of type \((\delta _1,\ldots ,\delta _K)\), where \(\sum _i \delta _i=\Delta\). We further assume here that the ith source, relay, and destination have been equipped with \(M_{s_i}\), \(M_{r_i}\), and \(M_{d_i}\) antennas, respectively. Finding bounds on the achievable \(\Delta\) in a KICJR network is equivalent to investigating solvability of the following equation system:
A system of polynomial equations which is improper (overdetermined) may have solutions if some equations are interconnected. In our system, the elements of channel matrices are drawn from a continuous probability distribution, and hence, such a situation rarely occurs. Then, we proceed the analysis by assuming improperness implies infeasibility, and hence, investigate properness of the equation system. Later in Sect. 6, we will examine tightness of this assumption by comparing it against the lower-bound from the proposed achievable scheme.
5.2.1 Deriving necessary conditions for solvability of Eq. 2
5.2.2 The first necessary condition
Recall the security-preserving equation system for the K-user interference channel in (42). In order to check properness of this equation system, we count the number of equations and unknowns in this equation system. From the right-hand side of (42), one observes that \(M_{d_k}\times \delta _i\) equations should be satisfied. Also, there are \(M_{r_j}^2\) free variables at jth relay (i.e. all of its elements), and \(\delta _i(M_{s_i}-\delta _i)\) free variables at the ith source.Footnote 7 Then the necessary condition on properness of (42) will be as:
In the first necessary condition, we counted the overall numbers of constraints and free variables in the transmit filters of sources and processing filters of relays in order to determine the proneness of the equation system in (42). However, some of the constraints could be only satisfied by leveraging free variables at instantaneous relays. Then, summing up the free variables at sources and relays could result in a loose upper bound. The second and third necessary conditions, which are presented in the sequel, focus on the required rank deficiency constraint in equivalent cross channels (i.e. \({\varvec{\Phi }}_{ki}, i\ne k\)). This constraint could be only satisfied by the free variables at processing filters of relays, which are part of the equivalent channel. Before going into the details of these necessary conditions, we first extend lemma 1 to the asymmetric case in which, source, relay, and destination nodes have been equipped with different number of antennas.
Lemma 3
Denote by\({\varvec{\Phi }}_{ki}\)the equivalent channel between source i and destination k in a KICJR, where\(i, k \in {\mathcal {K}}, i\ne k\). In order to provide\(\delta _i\)\({\mathbb {S}}\)DoF for user i, \({\varvec{\Phi }}_{ki}\) should have\(r_{ki}\triangleq [\delta _i-[M_{s_i}-M_{d_k}]^+]^+\) rank deficiencies, where\([x]^+=\max (x, 0)\).
Proof
For guaranteeing \(\delta _i\)\({\mathbb {S}}\)DoF in source i, the interferences from source i at destination k, \({\varvec{\Phi }}_{ki}{} {\mathbf{{V}}}_i, \forall k\in {\mathcal {K}}, k\ne i\), should be removed. As the rank of transmit filter at source i is \(\delta _i\), then the null space of \({\varvec{\Phi }}_{ki}\) matrix should be at least \(\delta _i\) dimensional. As the null space of a randomly generated matrix is \([M_{s_i}-M_{d_i}]^+\)-dimensional (with probability one), then \({\varvec{\Phi }}_{ki}\) should have \(r_{ki}= [\delta _i-[M_{s_i}-M_{d_k}]^+]^+\) rank deficiencies. \(\square\)
5.2.3 The second necessary condition
Using Lemma 1, the processing filters of relays are to be designed such that the equivalent cross channel matrices, i.e. \({\varvec{\Phi }}_{ki}\), \(i,k \in {\mathcal {K}}\), \(i\ne k\), have \(r_{ki}\) rank deficiencies. Now, we count the number of constraints and free variables in order to find the necessary condition on the achievability of such rank deficiencies. In order to count the number of constraints, we present the following useful lemma. Using lemma 2, decreasing the rank of \({\varvec{\Phi }}_{ki}\) to \(r_{ki}\) requires \(r_{ki}^2\) free variables in processing filters of relays. As there are \(M_{r_j}^2\) free variables in the jth relay, one can drive the second condition on achievability of \({\mathbb {S}}\)DoF as
where \(m=\min (M_{s_i}, M_{d_k})\).
5.2.4 The third necessary condition
The third necessary condition is presented only for the symmetric case, i.e. when all nodes have been equipped with M antennas. By applying the lemma 3 to the KICJR with M antennas at each node, one can write the third necessary condition on the achievability of \({\mathbb {S}}\)DoF as follows:
In the following, we aim at proving that (45) must be held for any feasible \({\mathbb {S}}\)DoF, i.e. it is not just com from properness analysis of (42). Towards this end, we first need some preliminaries,a s presented in the sequel.
Proposition 6
Denote by\({\mathbf{{A}}}\) and\({\mathbf{{B}}}\)two full-rank square matrices with M rows and columns. A necessary condition for existence of a square matrix like\({\mathbf{{W}}}\)with M rows and columns such that\({\mathbf{{A}}}+{\mathbf{{W}}}\) and\({\mathbf{{B}}}+{\mathbf{{W}}}\) have\(r_A\) and\(r_B\) rank deficiencies, is\(r_A+r_B \le M\).
Proof
consider the following equation system:
where \({\mathbf{{F}}}_1\) and \({\mathbf{{F}}}_2\) have \(M-r_A\) rows and M columns; \({\mathbf{{G}}}_1\) and \({\mathbf{{G}}}_2\) have \(M-r_B\) rows and M columns. The elements of these four matrices and \({\mathbf{{W}}}\) should be designed such that the equations in (46), (47) are satisfied. By subtracting (47) from (46), one has
As \({\mathbf{{A}}}\) and \({\mathbf{{B}}}\) are full rank matrices, their subtraction will be of full rank with probability one. Then for consistency of (46), (47), the right-hand side of (48) should be a full rank matrix. But as the ranks of \({\mathbf{{F}}}_{1}^{T}{} {\mathbf{{F}}}_2\) and \({\mathbf{{G}}}_{1}^{T}{} {\mathbf{{G}}}_2\) are \(M-r_A\) and \(M-r_B\), respectively, the rank of their sum will be less than equal to \(\min (2M-r_A-r_B, M)\). Hence, one can write the necessary condition on solvability of (46), (47) as follows,
and the proof is completed. \(\square\)
Now, for \({\varvec{\Phi }}_{ki}\) and \({\varvec{\Phi }}_{ik}\) to have \(r_{ki}\) and \(r_{ik}\) rank deficiencies, the following equations should be satisfied:
in which \({\mathbf{{W}}}_1\) is the processing matrix at relay, and the channel matrices have M rows and columns. The \({\mathbf{{F}}}\) and \({\mathbf{{G}}}\) matrices have \(M-r_{ki}\) rows and M columns, and \({\mathbf{{Y}}}\) and \({\mathbf{{Z}}}\) matrices have \(M-r_{ik}\) rows and M columns. We need to design \({\mathbf{{W}}}_1\), \({\mathbf{{F}}}\), \({\mathbf{{G}}}\), \({\mathbf{{Y}}}\), and \({\mathbf{{Z}}}\) matrices such that the equations in (50), (51) are satisfied. As the elements of channel matrices are drawn from a continuous probability distribution, these matrices are of full rank with probability one, and hence, they will be invertible. By multiplying the invert of channel matrices between relay and sources to the both sides of (50), (51), one can rewrite them as follows:
The \({{\mathbf{{H}}}_{k1}^{dr}}^{-1}{} {\mathbf{{H}}}_{ki}^{ds}{{\mathbf{{H}}}_{1i}^{rs}}^{-1}\) and \({{\mathbf{{H}}}_{i1}^{dr}}^{-1}{} {\mathbf{{H}}}_{ik}^{ds}{{\mathbf{{H}}}_{1k}^{rs}}^{-1}\) matrices have M rows and columns, and they will be of full rank with probability one. Also, \({{\mathbf{{H}}}_{k1}^{dr}}^{-1}{} {\mathbf{{F}}}^T{\mathbf{{G}}}{{\mathbf{{H}}}_{1i}^{rs}}^{-1}\) and \({{\mathbf{{H}}}_{i1}^{dr}}^{-1}{} {\mathbf{{Y}}}^T{\mathbf{{Z}}}{{\mathbf{{H}}}_{1k}^{rs}}^{-1}\) matrices will have \(M-r_{ki}\) and \(M-r_{ik}\) ranks, respectively. Then, one can rewrite the (52), (53) as follows:
in which,
The dimensions of \({\mathbf{{Y}}}_1\) and \({\mathbf{{Y}}}_2\) are the same as \({\mathbf{{F}}}\) and \({\mathbf{{G}}}\), and the dimensions of \({\mathbf{{Z}}}_1\) and \({\mathbf{{Z}}}_2\) are the same as \({\mathbf{{Y}}}\) and \({\mathbf{{Z}}}\). For solvability of (54), one can leverage the results of proposition 1 and conclude that the \(r_{ki}+r_{ik} \le M\) should be hold. We rewrite this necessary condition as follows
and the poof is completed.
5.2.5 The fourth necessary condition
Finally, the limited number of spatial dimensions at each node must be considered. Then, one can derive the fourth necessary condition on feasibility of \({\mathbb {S}}\)DoF as follows:
5.2.6 Utilizing the derived bounds for investigating \({\mathbb {S}}\)DoF performance of wireless networks
The provided necessary conditions in this work could be used in evaluating \({\mathbb {S}}\)DoF performance of different ICs. In the following, we present some results on the K-user IC and the wiretap channel aided by instantaneous relay(s).
Proposition 7
Consider the K-user interference channel, where each node is equipped with M antennas. For achieving KM\({\mathbb {S}}\)DoF, K(K-1) instantaneous relays are needed.
Proof
In Proposition 7, we have proved that using K(K-1) instantaneous relays the cross channels could be blocked, and hence, KM DoF could be achieved. This on the other hand means that the unintended receivers will not receive confidential messages, and hence, \({\mathbb {S}}\)DoF=DoF=KM. \(\square\)
Finally, we consider the point to point data transmission with one eavesdropper, and aided by one instantaneous relay, as depicted in Fig. 3. We further assume that each node has been equipped with M antennas. In the following, we show that using linear transmit/receive filters, M\({\mathbb {S}}\)DoF for this system are achievable. Towards this end, we need to remove the transmitter-eavesdropper channel, and hence, we need to solve the following equation system as \({\mathbf{{H}}}_{11}^{es} + {\mathbf{{H}}}_{11}^{er}{{\mathbf{{W}}}_1}{} {\mathbf{{H}}}_{11}^{rs} = {[0]_{M \times M}}\) where e denotes the eavesdropper. One can rearrange this equation as \({\mathbf{{H}}}_{11}^{er} \otimes {\mathbf{{H}}}_{11}^{rs}\mathrm{{vec}}({{\mathbf{{W}}}_1}) = -{\mathbf{{H}}}_{11}^{es}.\) As the elements of channel matrix are drawn from a continues probability distribution, the channel matrix will be of full rank with probability one, and hence, the equation system has a unique solution. Then, by solving this equation system, we can derive the relay’s processing filter. One must note that full CSI at the relay and no CSI at the transmitter side are required.
6 Performance evaluation
6.1 The DoF performance
In this section, the lower bound on the DoF performance of the KICJR network using the RIA scheme, and the upper bound on the DoF performance using the analysis on the properness of the interference alignment equations are evaluated. For the benchmark, we also present simulation results from MSE-based beamforming design, and analytical results from analysis of the AIN scheme [22], the pure IA scheme [7], and the time division multiple access (TDMA) scheme (in a KIC0R setting). The simulator has been built in Matlab,Footnote 8 and includes a fully-connected homogeneous K-user interference channel, where data transmissions experience Rayleigh fadingFootnote 9 and a distance-dependent path-loss, with a path-loss exponent of 2. In the legend of following figures, the suffix u denotes the upper bound on the maximum achievable DoF in the KICJR, which have been derived from analysis of (30)–(33). For a 3IC1R network, one observes in Fig. 4 that the lower bounds from the MSE-based beamforming and the RIA scheme well match the derived DoF upper bounds. For a 3IC2R network, we observe that the lower bounds from the RIA scheme and the MSE-based beamforming are in close match with the DoF upper bounds, but there is a gap between them, especially when the number of antennas at each node becomes higher than 5. This gap is due to the fact that in this work we have found 4 necessary conditions on solvability of the IA system of equations, while there might also exist other necessary conditions, which have not been discovered here. Then, this gap represents a future direction of research for DoF analysis of interference channels. In both cases, the proposed RIA scheme significantly outperforms the AIN scheme. This gap is mainly due to the fact that the proposed RIA scheme gets the most benefit of instantaneous relays for making the cross channels rank deficient instead of just using them for aligning the interferences. The DoF performances of the 2IC1R and 2IC2R networks have been presented in Fig. 5. One can see that the DoF performances of the RIA, MSE, and AIN schemes in a 2IC1R network are the same and match the upper bounds on the DoF performance. Also, the achieved DoF are in accordance with the proposition 3 in this work, i.e. the maximum achievable DoF in 2IC1R is \(\left\lfloor 3M/2\right\rfloor\). For a 2IC2R network, one can see that the DoF performances from the RIA and the MSE schemes are the same and match quite well the DoF upper bounds, while the DoF performance of the AIN scheme is worse than the maximum achievable DoF in this network. Also, the DoF performance in a 2IC2R network is in accordance with the proposition 7, i.e. the maximum achievable DoF in the 2-user interference channel are achieved using two instantaneous relays. One must note that while the achieved DoF in the interference channel using IA techniques, including our proposed instantaneous relay-aided IA, is high, in practical scenarios with uncontrolled out of clusterFootnote 10 interference, the performance will be highly affected. The level of degradation, and respective compensating schemes are out of the scope of this paper, and the interested reader may refer to [5] for more information.
6.2 The \({\mathbb {S}}\)DoF performance
In this subsection, the \({\mathbb {S}}\)DoF performance of the proposed achievable scheme is compared against the derived upper bounds in Sect. 5.2. Figure 6 shows the upper and lower bounds on the sum \({\mathbb {S}}\)DoF performance for the 2-user interference channel by changing the number of antennas at each node. The 2ICJR-l curves (for \(J=1,2\)) represent the lower bounds, and have been derived by applying the proposed achievable scheme to the system. The 2ICJR-u curves (for J=1,2) represent the upper bounds, and have been derived by considering the necessary conditions in Sect. 5.2. For the benchmark, the SDoF results of artificial noise alignment (ANA) [29] and interference alignment for secrecy (IAS) have been presented [16]. One observes that instantaneous relays can significantly increase the \({\mathbb {S}}\)DoF. Figure 7 shows the upper bounds on \({\mathbb {S}}\)DoF performance of KICJR, for different numbers of instantaneous relays by changing the number of users, i.e. K. In this figure, the KICJR-labeled curves, for different values of J, have been generated using the necessary conditions derived in Sect. 5.2. Also, the SDoF performance of the K-user interference channel, derived from [17], has also been depicted in this figure, denoted by IAS. One observes that using an appropriate number of instantaneous relays in the K-user interference channel, the full \({\mathbb {S}}\)DoF, i.e. KM, could be achieved. It is also interesting to see that for each J value, i.e. number of relays, there is a respective K-user IC in which, the highest sum \({\mathbb {S}}\)DoF is achieved. More investigation of the simulation results and analysis of the K which maximizes the achieved \({\mathbb {S}}\)DoF in an interference network are left for the future works.
7 Conclusions
The DoF performance of the K-user interference channel with J instantaneous relays has been investigated in this work. Previously, it has been shown that one instantaneous relay can increase the DoF of a 2-user interference channel by fifty percent using the AIN scheme. In this work, restricted interference alignment for the KICJR network has been proposed. In this scheme, the interferences from each source are restricted at each destination, and the received restricted interferences at each destination are aligned. We have further presented upper bounds on the DoF performance of the KICJR network by investigating properness of the interference alignment’s system of equations. Numerical and simulation results have confirmed the superior performance of the proposed RIA scheme in comparison with the state-of-the-art achievable schemes. We have further shown that the achieved DoF using RIA is close to the derived upper bounds from the properness of the interference alignment equations and the DoF performance of the MSE-based beamforming design. Furthermore, in order to enable physical layer security, we have presented an \({\mathbb {S}}\)DoF achieving scheme for K-user interference channel with confidential messages by leveraging instantaneous relaying for maching cross channels rank deficient. The achieved \({\mathbb {S}}\)DoF is secure against any cooperation among eavesdroppers. By investigating the necessary conditions for achieving the required rank deficiency in the cross channels, the \({\mathbb {S}}\)DoF performance of this K-user interference channel has been investigated. The performance evaluation results have confirmed that instantaneous relaying can significantly increase the \({\mathbb {S}}\)DoF performance of the system. The proposed analytical framework sheds light into the DoF region of the general KIC network aided by instantaneous relays, which is missing in literature, and could be of interest in other research areas, e.g. the rank deficiency results are of interest in beamforming design for millimeter wave communications.
Notes
DoF of a network approximates the network capacity as C(SNR) = \(\Delta \log\)(SNR) + O(\(\log\)(SNR)), where C and \(\Delta\) represent the capacity and sum DoF respectively. Then, it characterizes the network capacity as a function of interference in the high SNR regime [3].
In this paper, we denote by SDoF the scenario in which the messages of source i are only decodable at destination i. We also denote by strongly secure DoF (\({\mathbb {S}}\)DoF) the scenario in which destination j, for \(j\ne\) i, doesn’t receive any signal from source i.
The K-user interference channel with J instantaneous relays and confidential messages.
Practical motivations for instantaneous relays could be found in [27].
Karush–Kuhn–Tucker.
Denote by \({\mathbf {A}}\) an \(m \times n\) matrix. Matrix \({\mathbf {A}}\) has \(r_A\) rank deficiencies if its rank is \(\min (m, n)-r_A\).
The transmit filter of the ith source should have a rank of \(\delta _i\), and hence, \(\delta _i^2\) elements of transmit filter of source i are not free variables.
The codes are available online in the supporting repository of the paper: www.github.com/AminAzari/DoF-Simulator.
By the homogeneous model, we mean that the communications parameters like transmit power are the same across nodes, and hence, are canceled out in DoF performance analysis in high SNR regime.
A cluster of sources/destinations which make a K-user interference channel.
References
Sahoo, B., Yao, C.-H., & Wei, H.-Y. (2017). Millimeter-wave multi-hop wireless backhauling for 5G cellular networks. In IEEE Vehicular Technology Conference (pp. 1–5).
Asadi, A., Wang, Q., & Mancuso, V. (2014). A survey on device-to-device communication in cellular networks. IEEE Communications Surveys & Tutorials, 16(4), 1801–1819.
Zhao, N., et al. (2016). Interference alignment and its applications: A survey, research issues, and challenges. IEEE Communications Surveys Tutorials, 18(3), 1779.
Cadambe, V., & Jafar, S. (2008). Interference alignment and degrees of freedom of the K-user interference channel. IEEE Transactions on Information Theory, 54(8), 3425–3441.
Ntranos, V., et al. (2015). Cellular interference alignment. IEEE Transactions on Information Theory, 61(3), 1194–1217.
Yetis, C. M., Gou, T., Jafar, S. A., & Kayran, A. H. (2010). On feasibility of interference alignment in MIMO interference networks. IEEE Transactions on Signal Processing, 58(9), 4771–4782.
Razaviyayn, M., et al. (2012). On the degrees of freedom achievable through interference alignment in a MIMO interference channel. IEEE Transactions on Signal Processing, 60(2), 812–821.
Aquilina, P., & Ratnarajah, T. (2017). Linear interference alignment in full-duplex MIMO networks with imperfect CSI. IEEE Transactions on Communications, 65(12), 5226–5243.
Seif, M., Tandon, R., & Li, M. (2018). Secure retrospective interference alignment. arXiv:1801.03494.
Liu, T., Tuninetti, D., & Chung, S.-Y. (2017). On the DoF region of the MIMO gaussian two-user interference channel with an instantaneous relay. IEEE Transactions on Information Theory, 63(7), 4453–4471.
Johnny, M., & Aref, M. R. (2018). Blind interference alignment for the\(k\)-user SISO interference channel using reconfigurable antennas. IEEE Communications Letters, 22(5), 1046–1049.
Zhao, N., Yu, F. R., Li, M., Yan, Q., & Leung, V. C. (2016). Physical layer security issues in interference-alignment-based wireless networks. IEEE Communications Magazine, 54(8), 162–168.
Zhao, N., Yu, F. R., & Leung, V. C. (2015). Opportunistic communications in interference alignment networks with wireless power transfer. IEEE Wireless Communications, 22(1), 88–95.
Zhao, N., Yu, F. R., Sun, H., & Li, M. (2016). Adaptive power allocation schemes for spectrum sharing in interference-alignment-based cognitive radio networks. IEEE Transactions on Vehicular Technology, 65(5), 3700–3714.
Fan, Y., Liao, X., & Vasilakos, A. V. (2017). Physical layer security based on interference alignment in k-user MIMO Y wiretap channels. IEEE Access, 5, 5747–5759.
Koyluoglu, O., et al. (2011). Interference alignment for secrecy. IEEE Transactions on Information Theory, 57(6), 3323–3332.
Xie, J., & Ulukus, S. (2015). Secure degrees of freedom of \(k\)-user gaussian interference channels: A unified view. IEEE Transactions on Information Theory, 61(5), 2647–2661.
Cao, Y., Zhao, N., Yu, F. R., Jin, M., Chen, Y., Tang, J., et al. (2018). Optimization or alignment: Secure primary transmission assisted by secondary networks. IEEE Journal on Selected Areas in Communications, 36(4), 905–917.
Cadambe, V. R., & Jafar, S. A. (2008). Can feedback, cooperation, relays and full duplex operation increase the degrees of freedom of wireless networks? In IEEE International Symposium on Information Theory (pp. 1263–1267).
Al-Shatri, H., et al. (2012). Interference alignment using a MIMO relay and partially-adapted transmit/receive filters. In IEEE Wireless Communications and Networking Conference (pp. 459–464).
El Gamal, A., & Hassanpour, N. (2005). Relay without delay. In International Symposium on Information Theory (pp. 1078–1080).
Lee, N., & Wang, C. (2013). Aligned interference neutralization and the degrees of freedom of the two-user wireless networks with an instantaneous relay. IEEE Transactions on Communications, 61(9), 3611–3619.
Wang, Q., Dong, Y., Zhao, J., Li, N., Qian, J., & Liu, B. (2015). Instantaneous relaying: Feasibility conditions for interference neutralization. IEEE Communications Letters, 19(8), 1370–1373.
Cheng, Z., et al. (2016). The degrees of freedom of full-duplex bidirectional interference networks with and without a MIMO relay. IEEE Transactions on Wireless Communication, 15(4), 2912–2924.
Matthiesen, B., et al. (2015). Instantaneous relaying for the 3-way relaychannel with circular message exchanges. In Asilomar Conference on Signals, Systems and Computers (pp. 475–479).
Ge, X., Tu, S., Mao, G., Wang, C., & Han, T. (2016). 5G ultra-dense cellular networks. IEEE Wireless Communications, 23(1), 72–79.
Lee, N., & Wang, C. (2013). Aligned interference neutralization and the degrees of freedom of the two-user wireless networks with an instantaneous relay. IEEE Transactions on Communications, 61(9), 3611–3619.
Wang, Z., Schaefer, R. F., Skoglund, M., Xiao, M., & Poor, H. V. (2018). Strong secrecy for interference channels based on channel resolvability. IEEE Transactions on Information Theory, 64(7), 5110–5130.
Fakoorian, A., et al. (2010). MIMO interference channel with confidential messages: Game theoretic beamforming designs. In Asilomar Conference on Signals, Systems and Computers (pp. 2099–2103).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Azari, A. On the DoF and secure DoF of K-user MIMO interference channel with instantaneous relays. Wireless Netw 26, 1921–1936 (2020). https://doi.org/10.1007/s11276-018-1875-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-018-1875-0