Abstract
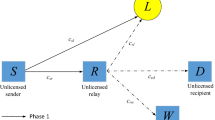
Covert wireless communication ensures information security by hiding the existence of the information transmission itself. Available works mainly focused on the covert throughput study of one-hop wireless communications, while the performance limit of covert throughput in important two-way two-hop scenarios remains largely unknown. As the most significant contribution, this paper, for the first time, investigates such performance limit in a system where two sources wish to covertly exchange information through a relay against the detection of a warden, i.e., a malicious node that attempts to detect the existence of communication between the two sources. As the second contribution, this paper considers various scenarios regarding the warden’s prior knowledge about the relay, the sources/relay’s prior knowledge about the warden, as well as different relaying patterns, and then proposes a covertness strategy to resist the warden’s detection for each scenario. As the last contribution, we derive the scaling law result for the covert throughput of the system for each scenario, i.e., the maximum number of bits that the two sources can exchange subject to a constraint on the detection probability of the warden. The results in this paper indicate that the covert throughput of the concerned system follows the well-known square root scaling law, which is independent of the relaying patterns, detection schemes, covertness strategies, and prior knowledges of the sources/relay and warden.


Similar content being viewed by others
References
Tse, D., & Viswanath, P. (2005). Fundamentals of wireless communication. Cambridge: Cambridge University Press.
Bloch, M., & Barros, J. (2011). Physical-layer security: From information theory to security engineering. Cambridge: Cambridge University Press.
Bash, B. A., Goeckel, D., Towsley, D., & Guha, S. (2015). Hiding information in noise: Fundamental limits of covert wireless communication. IEEE Communications Magazine, 53(12), 26–31.
Che, P. H., Bakshi, M., & Jaggi, S. (2013). Reliable deniable communication: Hiding messages in noise. In 2013 IEEE international symposium on information theory proceedings (ISIT) (pp. 2945–2949). IEEE.
Bloch, M. R. (2016). Covert communication over noisy channels: A resolvability perspective. IEEE Transactions on Information Theory, 62(5), 2334–2354.
Sarangapani, J. (2017). Wireless ad hoc and sensor networks: Protocols, performance, and control. Boca Raton: CRC Press.
Rashid, B., & Rehmani, M. H. (2016). Applications of wireless sensor networks for urban areas: A survey. Journal of Network and Computer Applications, 60, 192–219.
Narayanan, S. (2006). Two-hop forwarding in wireless networks. Ph.D. dissertation, Polytechnic University.
Louie, R. H., Li, Y., & Vucetic, B. (2010). Practical physical layer network coding for two-way relay channels: Performance analysis and comparison. IEEE Transactions on Wireless Communications, 9(2), 764–777.
Bash, B. A., Goeckel, D., & Towsley, D. (2012). Square root law for communication with low probability of detection on AWGN channels. In 2012 IEEE international symposium on information theory proceedings (ISIT) (pp. 448–452). IEEE.
Zhang, R., Song, L., Han, Z., & Jiao, B. (2012). Physical layer security for two-way untrusted relaying with friendly jammers. IEEE Transactions on Vehicular Technology, 61(8), 3693–3704.
Simon, M. K., Omura, J. K., Scholtz, R. A., & Levitt, B. K. (1994). Spread spectrum communications handbook. New York: McGraw-Hill.
Bash, B. A., Goeckel, D., & Towsley, D. (2013). Limits of reliable communication with low probability of detection on AWGN channels. IEEE Journal on Selected Areas in Communications, 31(9), 1921–1930.
Haeupler, B., Kamath, P., & Velingker, A. (2015). Communication with partial noiseless feedback. In Approximation, randomization, and combinatorial optimization. Algorithms and techniques (APPROX/RANDOM 2015). Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik.
Wang, G., Qin, Y., & Chang, C. (2017). Communication with partial noisy feedback. In 2017 IEEE symposium on computers and communications (ISCC) (pp. 602–607). IEEE.
Efremenko, K., Gelles, R., & Haeupler, B. (2016). Maximal noise in interactive communication over erasure channels and channels with feedback. IEEE Transactions on Information Theory, 62(8), 4575–4588.
Che, P. H., Bakshi, M., Chan, C., & Jaggi, S. ( 2014). Reliable, deniable and hidable communication. In Information theory and applications workshop (ITA), 2014 (pp. 1–10). IEEE.
Che, P. H., Bakshi, M., Chan, C., & Jaggi, S. (2014). Reliable deniable communication with channel uncertainty. In 2014 IEEE information theory workshop (ITW 2014) (pp. 30–34). IEEE.
Bloch, M. (2015). A channel resolvability perspective on stealth communications. In 2015 IEEE international symposium on information theory (ISIT) (pp. 2535–2539). IEEE.
Wang, L., Wornell, G. W., & Zheng, L. (2016). Fundamental limits of communication with low probability of detection. IEEE Transactions on Information Theory, 62(6), 3493–3503.
Bash, B. A., Goeckel, D., & Towsley, D. (2014). LPD communication when the warden does not know when. In 2014 IEEE international symposium on information theory (ISIT) (pp. 606–610). IEEE.
Goeckel, D., Bash, B., Guha, S., & Towsley, D. (2016). Covert communications when the warden does not know the background noise power. IEEE Communications Letters, 20(2), 236–239.
Sobers, T. V., Bash, B. A., Guha, S., Towsley, D., & Goeckel, D. (2017). Covert communication in the presence of an uninformed jammer. IEEE Transactions on Wireless Communications, 16(9), 6193–6206.
Soltani, R., Goeckel, D., Towsley, D., Bash, B., & Guha, S. (2017). Covert wireless communication with artificial noise generation. arXiv preprint arXiv:1709.07096.
Yan, S., He, B., Zhou, X., Cong, Y., & Swindlehurst, A. L. (2019). Delay-intolerant covert communications with either fixed or random transmit power. IEEE Transactions on Information Forensics and Security, 14(1), 129–140.
Bash, B. A., Goeckel, D., & Towsley, D. (2016). Covert communication gains from adversary’s ignorance of transmission time. IEEE Transactions on Wireless Communications, 15(12), 8394–8405.
Shahzad, K., Zhou, X., & Yan, S. (2017). Covert communication in fading channels under channel uncertainty. arXiv preprint arXiv:1703.02169.
Lee, S.-H., Wang, L., Khisti, A., & Wornell, G. W. (2018). Covert communication with channel-state information at the transmitter. IEEE Transactions on Information Forensics and Security, 13(9), 2310–2319.
Forouzesh, M., Azmi, P., Mokari, N., & Goeckel, D. (2019). Robust power allocation in covert communication: Imperfect CDI. arXiv preprint arXiv:1901.04914.
He, B., Yan, S., Zhou, X., & Lau, V. K. (2017). On covert communication with noise uncertainty. IEEE Communications Letters, 21(4), 941–944.
Lee, S., Baxley, R. J., Weitnauer, M. A., & Walkenhorst, B. (2015). Achieving undetectable communication. IEEE Journal of Selected Topics in Signal Processing, 9(7), 1195–1205.
Hu, J. Yan, S. Zhou, X. Shu, F. & Li, J. (2018). Covert wireless communications with channel inversion power control in Rayleigh fading. arXiv preprint arXiv:1803.07812.
Zhang, Y., Shen, Y., & Jiang, X. (2019). Friendship-based cooperative jamming for secure communication in Poisson networks. Wireless Networks, 25(7), 4077–4095.
Shahzad, K., Zhou, X., Yan, S., Hu, J., Shu, F., & Li, J. (2018). Achieving covert wireless communications using a full-duplex receiver. IEEE Transactions on Wireless Communications, 17(12), 8517–8530.
Wu, H., Liao, X., Dang, Y., Shen, Y., & Jiang, X. (2017). Limits of covert communication on two-hop AWGN channels. In 2017 international conference on networking and network applications (NaNA) (pp. 42–47). IEEE.
Sheikholeslami, A., Ghaderi, M., Towsley, D., Bash, B. A., Guha, S., & Goeckel, D. (2018). Multi-hop routing in covert wireless networks. IEEE Transactions on Wireless Communications, 17, 3656–3669.
Liu, Z., Liu, J., Zeng, Y., Ma, Z., Ma, J., & Huang, Q. (2019). Challenges in covert wireless communications with active warden on AWGN channels. arXiv preprint arXiv:1901.03185.
Lehmann, E. L., & Romano, J. P. (2006). Testing statistical hypotheses. Berlin: Springer.
Cover, T. M., & Thomas, J. A. (2012). Elements of information theory. Hoboken: Wiley.
Lang, S. (2013). Undergraduate analysis. Berlin: Springer.
Kullback, S. (1997). Information theory and statistics. North Chelmsford: Courier Corporation.
Filler, T., Ker, A. D., & Fridrich, J. (2009). The square root law of steganographic capacity for Markov covers. In Media forensics and security (Vol. 7254, p. 725408). International Society for Optics and Photonics.
Madhow, U. (2008). Fundamentals of digital communication. Cambridge: Cambridge University Press.
Rankov, B., & Wittneben, A. (2006). Achievable rate regions for the two-way relay channel. In 2006 IEEE international symposium on information theory (pp. 1668–1672). IEEE.
Cormen, T. H. (2009). Introduction to algorithms. Cambridge: MIT Press.
Acknowledgements
This work is supported in part by Japan Society for the Promotion of Science (JSPS) Grant No. 18H03235, Japan JSPS KAKENHI under Grant 19K14983, China NSFC (61972308, 61571352, U1736216, U1536202), China the Project of Hainan Province Key Research and Development Program “The study of Data Mining and Analysis Technologies for Network Security Management on Key Information Infrastructure in Big Data Environment” (No. ZDYF2019202), and China Fundamental Research Funds for the Central Universities (GK201903087). Finally, our deepest gratitude goes to the reviewers and the editor for their careful work and thoughtful suggestions that have helped improve this paper substantially.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wu, H., Zhang, Y., Liao, X. et al. On covert throughput performance of two-way relay covert wireless communications. Wireless Netw 26, 3275–3289 (2020). https://doi.org/10.1007/s11276-020-02256-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-020-02256-9