Abstract
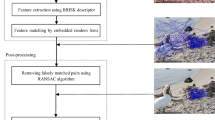
Copy-move is one of the most common image forgeries, wherein one or more region are copied and pasted within the same image. The motivations of such forgery include hiding an element in the image or emphasizing a particular object. Copy-move image forgery is more challenging to detect than other types, such as splicing and retouching. Keypoint based copy-move forgery detection extracts image keypoints and uses local visual features to identify duplicated regions, which exhibits remarkable performance with respect to memory requirement and robustness against various attacks. However, these approaches fail to handle the cases when copy-move forgeries only involve small or smooth regions, where the number of keypoints is very limited. Also, they generally have higher time costs owing to complex feature descriptor and more error matching points. To tackle these challenges, we propose a fast and effective copy-move forgery detection method through adaptive keypoint extraction and processing, introducing fast robust invariant feature, and filtering out the wrong pairs. Firstly, the uniform distribution keypoints are extracted adaptively from the forged image by employing the fast approximated LoG filter and performing the uniformity processing. Then, the image keypoints are described using fast robust invariant feature and matched through the Rg2NN algorithm. Finally, the falsely matched pairs are removed by employing the segmentation based candidate clustering, and the duplicated regions are localized using optimized mean-residual normalized production correlation. We conduct extensive experiments to evaluate the performance of the proposed scheme, in which encouraging results validate the effectiveness of the proposed technique, in comparison with the state-of-the-art approaches recently proposed in the literature.



















Similar content being viewed by others
References
Achanta, R., Shaji, A., Smith, K., et al. (2012). SLIC superpixels compared to state-of-the-art superpixel methods. IEEE Transactions on Pattern Analysis and Machine Intelligence,34(11), 2274–2282.
Alahmadi, A., Hussain, M., Aboalsamh, H., et al. (2017). Passive detection of image forgery using DCT and local binary pattern. Signal, Image and Video Processing,11(1), 81–88.
Amerini, I., Ballan, L., Caldelli, R., et al. (2013). Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Processing: Image Communication,28(6), 659–669.
Aymaz, S., Aymaz, Ş., & Ulutaş, G. (2016). Detection of copy move forgery using Legendre moments. In 2016 24th signal processing and communication application conference (SIU) (pp. 1125–1128). IEEE.
Cao, Y., Gao, T., Fan, L., et al. (2012). A robust detection algorithm for copy-move forgery in digital images. Forensic Science International,214(1–3), 33–43.
Christlein, V., Riess, C., Jordan, J., et al. (2012). An evaluation of popular copy-move forgery detection approaches. IEEE Transactions on Information Forensics and Security,7(6), 1841–1854.
Cozzolino, D., Poggi, G., & Verdoliva, L. (2014). Copy-move forgery detection based on patchmatch. In 2014 IEEE international conference on image processing (ICIP) (pp. 5312–5316). IEEE.
Cozzolino, D., Poggi, G., & Verdoliva, L. (2015). Efficient dense-field copy–move forgery detection. IEEE Transactions on Information Forensics and Security,10(11), 2284–2297.
Dixit, R., Naskar, R., & Mishra, S. (2017). Blur-invariant copy-move forgery detection technique with improved detection accuracy utilising SWT-SVD. IET Image Processing,11(5), 301–309.
Huang, D. Y., Huang, C. N., Hu, W. C., et al. (2015). Robustness of copy-move forgery detection under high JPEG compression artifacts. Multimedia Tools and Applications,76, 1–22.
Isaac, M. M., & Wilscy, M. (2015). Copy-Move forgery detection based on Harris Corner points and BRISK. In Proceedings of the third international symposium on women in computing and informatics (pp. 394–399). ACM.
Jia, S., Xu, Z., Wang, H., Feng, C., & Wang, T. (2018). Coarse-to-fine copy-move forgery detection for video forensics. IEEE Access,6, 25323–25335.
Jin, G., & Wan, X. (2017). An improved method for SIFT-based copy–move forgery detection using non-maximum value suppression and optimized J-Linkage. Signal Processing: Image Communication,57, 113–125.
Lee, J. C., Chang, C. P., & Chen, W. K. (2015). Detection of copy–move image forgery using histogram of orientated gradients. Information Sciences,321, 250–262.
Li, C., Yu, F., Lin, Z., et al. (2016). A novel fast target tracking based on video image. In 2016 35th Chinese control conference (CCC) (pp. 10264–10268). IEEE.
Lin, C., Li, Y., Xu, G., et al. (2017). Optimizing ZNCC calculation in binocular stereo matching. Signal Processing: Image Communication,52, 64–73.
Pan, X., & Lyu, S. (2010). Region duplication detection using image feature matching. IEEE Transactions on Information Forensics and Security,5(4), 857–867.
Pun, C. M., Yuan, X. C., & Bi, X. L. (2015). Image forgery detection using adaptive oversegmentation and feature point matching. IEEE Transactions on Information Forensics and Security,10(8), 1705–1716.
Ryu, S. J., Lee, M. J., & Lee, H. K. (2010). Detection of copy-rotate-move forgery using Zernike moments. In International workshop on information hiding (pp. 51–65). Berlin, Heidelberg: Springer.
Shah, T. J., & Banday, M. T. (2017). Copy-move forgery detection using hybrid transform and K-means clustering technique. In 2017 3rd international conference on applied and theoretical computing and communication technology (iCATccT) (pp. 79-83). IEEE.
Shahroudnejad, A., & Rahmati, M. (2016). Copy-move forgery detection in digital images using affine-SIFT. In International conference of signal processing and intelligent systems (ICSPIS) (pp. 1–5). IEEE.
Shivakumar, B. L., & Baboo, S. S. (2011). Detection of region duplication forgery in digital images using SURF. International Journal of Computer Science Issues (IJCSI),8(4), 199.
Silva, E., Carvalho, T., Ferreira, A., et al. (2015). Going deeper into copy-move forgery detection: Exploring image telltales via multi-scale analysis and voting processes. Journal of Visual Communication and Image Representation,29, 16–32.
Soni, B., Das, P. K., & Thounaojam, D. M. (2018). CMFD: A detailed review of block based and key feature based techniques in image copy-move forgery detection. IET Image Processing,12(2), 167–178.
Teerakanok, S., & Uehara, T. (2018). Copy-move forgery detection using GLCM-based rotation-invariant feature: A preliminary research. In 2018 IEEE 42nd annual computer software and applications conference (COMPSAC) (Vol. 2, pp. 365–369). IEEE.
Thirunavukkarasu, V., Kumar, J. S., Chae, G. S., et al. (2018). Non-intrusive forensic detection method using DSWT with reduced feature set for copy-move image tampering. Wireless Personal Communications,98(4), 3039–3057.
Üstübioğlu, B., Ayas, S., Doğan, H., et al. (2015). Image forgery detection based on colour SIFT. In Signal processing & communications applications conference. IEEE.
Wang, Z., Fan, B., & Wu, F. (2013) FRIF: Fast robust invariant feature. In British machine vision conference.
Wang, X. Y., Jiao, L. X., Wang, X. B., et al. (2018a). A new keypoint-based copy-move forgery detection for color image. Applied Intelligence,48(10), 3630–3652.
Wang, X. Y., Li, S., Liu, Y. N., et al. (2017a). A new keypoint-based copy-move forgery detection for small smooth regions. Multimedia Tools and Applications,76(22), 23353–23382.
Wang, X. Y., Liu, Y. N., Xu, H., et al. (2018b). Robust copy-move forgery detection using quaternion exponent moments. Pattern Analysis and Applications,21(2), 451–467.
Wang, Y., Tian, L., & Li, C. (2017b). LBP-SVD based copy move forgery detection algorithm. In 2017 IEEE international symposium on multimedia (ISM) (pp. 553–556). IEEE.
Warif, N. B. A., Wahab, A. W. A., Idris, M. Y. I., et al. (2017). SIFT-symmetry: a robust detection method for copy-move forgery with reflection attack. Journal of Visual Communication and Image Representation,46, 219–232.
Wo, Y., Yang, K., Han, G., et al. (2017). Copy–move forgery detection based on multi-radius PCET. IET Image Processing,11(2), 99–108.
Yan, L., Liu, N., Zhang, B., et al. (2015). Image multiple copy-move forgery detection algorithm based on reversed-generalized 2 nearest-neighbor. Journal of Electronics & Information Technology,37(7), 1667–1673.
Yang, F., Li, J., Lu, W., et al. (2017). Copy-move forgery detection based on hybrid features. Engineering Applications of Artificial Intelligence,59, 73–83.
Yang, B., Sun, X., Guo, H., et al. (2018). A copy-move forgery detection method based on CMFD-SIFT. Multimedia Tools and Applications,77(1), 837–855.
Zandi, M., Mahmoudi-Aznaveh, A., & Talebpour, A. (2016). Iterative copy-move forgery detection based on a new interest point detector. IEEE Transactions on Information Forensics and Security,11(11), 2499–2512.
Zheng, J., Liu, Y., Ren, J., et al. (2016). Fusion of block and keypoints based approaches for effective copy-move image forgery detection. Multidimensional Systems and Signal Processing,27(4), 989–1005.
Zhu, Y., Shen, X., & Chen, H. (2016). Copy-move forgery detection based on scaled ORB. Multimedia Tools and Applications,75(6), 3221–3233.
Zong, T., Xiang, Y., Natgunanathan, I., et al. (2015). Robust histogram shape-based method for image watermarking. IEEE Transactions on Circuits and Systems for Video Technology,25(5), 717–729.
Acknowledgments
This work was supported partially by the National Natural Science Foundation of China (Nos. 61472171, 61701212), China Postdoctoral Science Foundation (Nos. 2017M621135, 2018T110220), Key Scientific Research Project of Liaoning Provincial Education Department (LZ2019001), Natural Science Foundation of Liaoning Province (2019-ZD-0468), and High-level Innovation Talents Foundation of Dalian (No. 2017RQ055).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, XY., Wang, C., Wang, L. et al. A fast and high accurate image copy-move forgery detection approach. Multidim Syst Sign Process 31, 857–883 (2020). https://doi.org/10.1007/s11045-019-00688-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11045-019-00688-x