Abstract
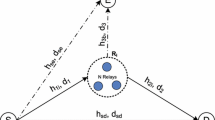
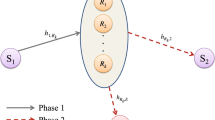
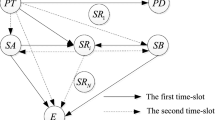
The use of wireless transmission networks in various environments has become widespread. One of the main challenges in wireless networks is that the wireless transmission is highly vulnerable to eavesdropping attacks. In this paper, an amplify-and-forward cooperative relaying wireless system with relay selection is considered to improve the physical layer (PHY) security of the wireless system in the presence of multiple eavesdroppers, under two cases, namely, perfect channel state information (CSI) and outdated CSI cases. To evaluate the PHY security of the system, we derive closed-form expressions for the PHY security performance metrics, including the probability of non-zero secrecy capacity, the average secrecy capacity, and the secrecy outage probability. Then using those expressions, we obtain several numerical results under system parameters. The results show that relay selection provides significant improvement in the PHY security of the system. Moreover, it is observed that, when the CSI used to select the best relay is outdated, the PHY secrecy performance is relatively inferior compared to that of the perfect CSI case. Finally, the obtained mathematical expressions are also validated using Monte-Carlo simulation.


















Similar content being viewed by others
References
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell system technical journal, 28(4), 656–715.
Wyner, A. D. (1975). The wire-tap channel. Bell system technical journal, 54(8), 1355–1387.
Leung-Yan-Cheong, S., & Hellman, M. (1978). The gaussian wire-tap channel. Information Theory, IEEE Transactions on, 24(451–456), 08.
Zou, Y., Zhu, J., Wang, X., & Leung, V. C. M. (2015). Improving physical-layer security in wireless communications using diversity techniques. IEEE Network, 29(1), 42–48.
Zou, Y., Zhu, J., Wang, X., & Hanzo, L. (2016). A survey on wireless security: Technical challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), 1727–1765.
Rawat, D. B., White, T., Parwez, M. S., Bajracharya, C., & Song, M. (2017). Evaluating secrecy outage of physical layer security in large-scale mimo wireless communications for cyber-physical systems. IEEE Internet of Things Journal, 4(6), 1987–1993.
He, B., Ni, Q., Chen, J., Yang, L., & Lv, L. (2018). User-pair selection in multiuser cooperative networks with an untrusted relay. IEEE Transactions on Vehicular Technology, 68(1), 869–882.
Harrison, W. K., Almeida, J., Bloch, M. R., McLaughlin, S. W., & Barros, J. (2013). Coding for secrecy: An overview of error-control coding techniques for physical-layer security. IEEE Signal Processing Magazine, 30(5), 41–50.
Zhao, R., Lin, H., He, Y.-C., Chen, D.-H., Huang, Y., & Yang, L. (2017). Secrecy performance of transmit antenna selection for mimo relay systems with outdated csi. IEEE Transactions on Communications, 66(2), 546–559.
Huang, Y., Al-Qahtani, F. S., Duong, T. Q., & Wang, J. (2015). Secure transmission in MIMO wiretap channels using general-order transmit antenna selection with outdated CSI. IEEE Transactions on Communications, 63(8), 2959–2971.
Melki, R., Noura, H. N., Mansour, M. M., & Chehab, A. (2020). Physical layer security schemes for MIMO systems: an overview. Wireless Networks, 26(3), 2089–2111.
BaghaeiPouri, A., & Torabi, M. (2019). Secrecy performance analysis of CIOD-OFDM systems over wireless fading channels. Wireless Networks, 1–14.
BaghaeiPouri, A., & Torabi, M. (2019). OFDM/OQAM transmission with improved physical layer security. Physical Communication, 36, 100787.
Mukherjee, A., Fakoorian, S. A. A., Huang, J., & Swindlehurst, A. L. (2014). Principles of physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys & Tutorials, 16(3), 1550–1573.
BaghaeiPouri, A., & Torabi, M. (2020). Physical layer security in space-time block codes from coordinate interleaved orthogonal design. IET Communications, 14(12), 2007–2017.
BaghaeiPouri, A., & Torabi, M. (2020). Analysis of secrecy outage performance of TAS-CIOD systems over wireless Rayleigh fading channels. Physical Communication, 101–129.
Barros, J., & Rodrigues, M. R. (2006). Secrecy capacity of wireless channels. In IEEE International Symposium on Information Theory, (pp. 356–360), IEEE.
Wang, P., Yu, G., & Zhang, Z. (2007). On the secrecy capacity of fading wireless channel with multiple eavesdroppers. In IEEE International Symposium on Information Theory, (pp. 1301–1305), IEEE.
Torabi, M., Ajib, W., & Haccoun, D. (2009). Performance analysis of amplify-and-forward cooperative networks with relay selection over rayleigh fading channels. In 69th IEEE Vehicular Technology Conference, VTC-Spring, (pp. 1–5), IEEE.
Torabi, M., & Haccoun, D. (2011). Capacity of amplify-and-forward selective relaying with adaptive transmission under outdated channel information. IEEE Transactions on Vehicular Technology, 60(5), 2416–2422.
Sarker, D. K., Sarkar, M. Z. I., & Anower, M. S. (2018). Secure wireless multicasting through AF-cooperative networks with best-relay selection over generalized fading channels. Wireless Networks, 1–14.
Bletsas, A., Khisti, A., Reed, D. P., & Lippman, A. (2006). A simple cooperative diversity method based on network path selection. IEEE journal on Selected Areas in Communications, 24(3), 659–672.
Zhao, Y., Adve, R., & Lim, T. J. (2006). Symbol error rate of selection amplify-and-forward relay systems. IEEE Communications Letters, 10(11), 757–759.
Ferdinand, N. S., da Costa, D. B., & Latva-aho, M. (2013). Effects of outdated csi on the secrecy performance of miso wiretap channels with transmit antenna selection. IEEE Communications Letters, 17(5), 864–867.
Fan, L., Lei, X., Yang, N., Duong, T. Q., & Karagiannidis, G. K. (2017). Secrecy cooperative networks with outdated relay selection over correlated fading channels. IEEE Transactions on Vehicular Technology, 66(8), 7599–7603.
Torabi, M., & Haccoun, D. (2010). Capacity analysis of opportunistic relaying in cooperative systems with outdated channel information. IEEE Communications Letters, 14(12), 1137–1139.
Kumar, R., & Chauhan, S. S. (2020). Physical layer security for space-time-block-coded MIMO system in Rician fading in the presence of imperfect feedback. Wireless Networks, 1–9.
Torabi, M., Frigon, J.-F., & Haccoun, D. (2016). Impact of spatial correlation on the BER performance of cooperative wireless relay networks with OSTBC. IET Commun., 10(8), 975–979.
Anghel, P., & Kaveh, M. (2004). Exact symbol error probability of a cooperative network in a Rayleigh-fading environment., 3, 1416–1421.
Yan, Z., Ouyang, B., Zhang, X., & Liu, H. -L. (2019). Secrecy Outage Performance of Opportunistic Relay Selection with Limited CSI Feedback. IEEE Wireless Communications Letters.
David, N. H. (2003). Order statistics (3rd ed.). New Jersey: Wiley.
Suraweera, H. A., Smith, P. J., & Shafi, M. (2010). Capacity limits and performance analysis of cognitive radio with imperfect channel knowledge. IEEE Transactions on Vehicular Technology, 59(4), 1811–1822.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Torabi, M., Parkouk, S. & Shokrollahi, S. Secrecy performance analysis of amplify-and-forward cooperative network with relay selection in the presence of multiple eavesdroppers. Wireless Netw 27, 2977–2990 (2021). https://doi.org/10.1007/s11276-021-02611-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02611-4