Pattern Recognition Letters ( IF 5.1 ) Pub Date : 2021-11-08 , DOI: 10.1016/j.patrec.2021.11.009 M. Vijayakumar 1 , T.S. Shiny Angel 2
|
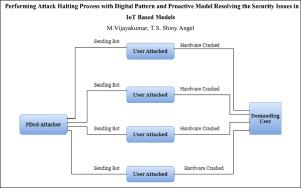
The major development of the Internet of Things (IoT) has improved wireless technology in general and multiple sectors. Hardware security representations are crucial in maintaining the trustworthiness, credibility, and credibility of integrated circuits (ICs) and digital equipment. Phlashing attacks have just been termed Permanent Denial of Service (PDoS) attacks since they behave similarly to a standard DoS attack but still have long-term implications. To prevent a PDoS intrusion that would block all Internet connectivity and related functionalities on a computer. A phlashing is a cyber-attack where an entity intentionally blocks another individual basis team from accessing internet resources also including network communication and financing. This article aims to provide an analysis of cyber-attack avoidance is identified and ceased by worldwide records across the last year to analyze data and developments in cyber-attacks. Attacks can be tracked better as the same form of attack is performed again by using a database containing the attack signatures. Our study revealed, by using the Recurrent Neural Network (RNN) algorithm, that our system could provide adequate detection efficiency while still correcting the detectors whenever an intruder is observed.
中文翻译:

使用数字模式和主动模型执行攻击停止过程解决基于物联网模型中的安全问题
物联网 (IoT) 的重大发展改善了一般和多个领域的无线技术。硬件安全表示对于维护集成电路 (IC) 和数字设备的可信度、可信度和可信度至关重要。Phlashing 攻击刚刚被称为永久拒绝服务 (PDoS) 攻击,因为它们的行为类似于标准的 DoS 攻击,但仍具有长期影响。防止 PDoS 入侵会阻止计算机上的所有 Internet 连接和相关功能。网络攻击是一种网络攻击,其中一个实体故意阻止另一个个人基础团队访问互联网资源,包括网络通信和融资。本文旨在提供对过去一年全球记录中识别和停止网络攻击的分析,以分析网络攻击的数据和发展。由于使用包含攻击特征的数据库再次执行相同形式的攻击,因此可以更好地跟踪攻击。我们的研究表明,通过使用循环神经网络 (RNN) 算法,我们的系统可以提供足够的检测效率,同时在观察到入侵者时仍能纠正检测器。


























 京公网安备 11010802027423号
京公网安备 11010802027423号