当前位置:
X-MOL 学术
›
Int. J. Commun. Syst.
›
论文详情
Our official English website, www.x-mol.net, welcomes your feedback! (Note: you will need to create a separate account there.)
RPL rank based-attack mitigation scheme in IoT environment
International Journal of Communication Systems ( IF 2.1 ) Pub Date : 2021-07-06 , DOI: 10.1002/dac.4917 Mohammed Amine Boudouaia 1, 2 , Abdelhafıd Abouaissa 2 , Adda Ali‐Pacha 1 , Ayoub Benayache 2 , Pascal Lorenz 2
International Journal of Communication Systems ( IF 2.1 ) Pub Date : 2021-07-06 , DOI: 10.1002/dac.4917 Mohammed Amine Boudouaia 1, 2 , Abdelhafıd Abouaissa 2 , Adda Ali‐Pacha 1 , Ayoub Benayache 2 , Pascal Lorenz 2
Affiliation
|
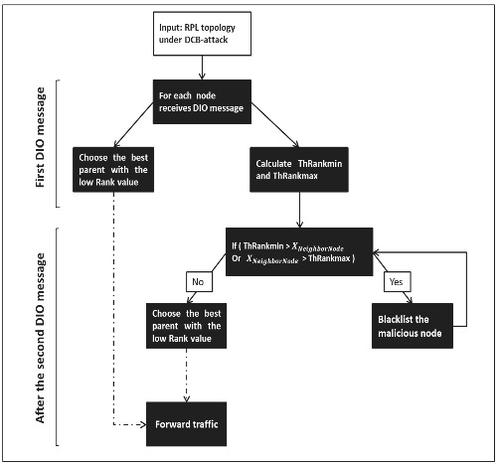
Due to the new technologies of the Internet of Things (IoT), connected objects have become smart interactive devices. However, despite their imminent advantages, whether for the daily life of users or in professional contexts, and the various security solutions proposed in literature in particular, the security of IoT networks is still a paramount issue given to the amount of confidential data that circulates through these technologies. In other words, among the IoT protocols that suffer from security issues, routing protocol for low power and lossy networks (RPL) is considered to be one of the most widely used protocols in the deployment of constrained IoT networks with limited resources (storage and energy constraints for example). On this basis, this article investigates in the first part a security flaw in the RPL protocol by carrying out an attack against the rank value of the RPL in an IoT environment. In the second part, a mitigation scheme to avoid it using a trust threshold is proposed. The malicious behavior of the attack and the effectiveness of the proposed scheme were assessed by detailed simulations using the Cooja simulator, in terms of successful detection rate, average network hops and global energy consumption. To conclude, a fair comparison between the different simulation results has been adopted using the Friedman statistical test, and a discussion has been presented with some future works concerning security against rank attack.
中文翻译:

物联网环境中基于 RPL 等级的攻击缓解方案
由于物联网(IoT)的新技术,连接的对象已成为智能交互设备。然而,尽管它们的优势迫在眉睫,无论是对于用户的日常生活还是在专业环境中,尤其是文献中提出的各种安全解决方案,物联网网络的安全性仍然是一个首要问题,因为通过大量机密数据流通这些技术。换句话说,在存在安全问题的物联网协议中,低功耗和有损网络(RPL)路由协议被认为是在资源(存储和能源)有限的受限物联网网络部署中使用最广泛的协议之一。例如约束)。在此基础上,本文的第一部分通过在物联网环境中对 RPL 的秩值进行攻击来调查 RPL 协议中的安全漏洞。在第二部分中,提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。
更新日期:2021-08-04
中文翻译:

物联网环境中基于 RPL 等级的攻击缓解方案
由于物联网(IoT)的新技术,连接的对象已成为智能交互设备。然而,尽管它们的优势迫在眉睫,无论是对于用户的日常生活还是在专业环境中,尤其是文献中提出的各种安全解决方案,物联网网络的安全性仍然是一个首要问题,因为通过大量机密数据流通这些技术。换句话说,在存在安全问题的物联网协议中,低功耗和有损网络(RPL)路由协议被认为是在资源(存储和能源)有限的受限物联网网络部署中使用最广泛的协议之一。例如约束)。在此基础上,本文的第一部分通过在物联网环境中对 RPL 的秩值进行攻击来调查 RPL 协议中的安全漏洞。在第二部分中,提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。提出了一种使用信任阈值来避免它的缓解方案。攻击的恶意行为和所提出方案的有效性通过使用 Cooja 模拟器的详细模拟在成功检测率、平均网络跳数和全局能量消耗方面进行评估。总而言之,使用弗里德曼统计检验对不同的模拟结果进行了公平的比较,并讨论了一些未来关于对抗秩攻击的安全性的工作。


























 京公网安备 11010802027423号
京公网安备 11010802027423号